
What a difference a year makes in the threat environment.
In January 2017, Rig Exploit Kit (EK) was still in the middle of a strong run. But when April 2017 came, Rig started a very marked decline.
You can see this in the chart below:
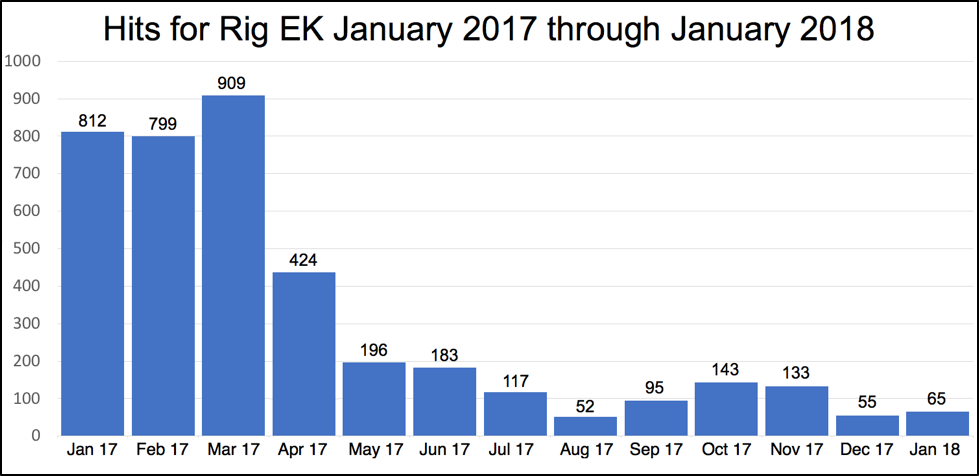
Figure 1: Hits for Rig EK from January 2017 through January 2018
We first noted the trend in our June 2017 research blog “Decline in Rig Exploit Kit”. And now in our most recent research blog “Rig EK one year later: From Ransomware to Coin Miners and Information Stealers” we can see the decline in April wasn’t an anomaly: it was the start of a precipitous decline that may mark the fall of Rig EK and exploit kits altogether as you can see.
As with the rise and fall of other threat trends, there are many likely reasons for this. As Unit 42 researcher Brad Duncan noted in June 2017 and January 2018, likely reasons for the decline of Rig EK include a declining browser target base, lack of new exploits, efforts to fight domain shadowing, criminal arrests, and on-going work by vendors to harden browsers.
But the decline and (hopeful) fall of Rig and other exploit kits isn’t the only story here. The sudden rise of coinmining in response to the surging value of cryptocurrencies comes into this story as well.
This is because while Rig is down (and declining) it’s not totally out yet. And we’re seeing what remains of Rig EK shift nearly wholesale from ransomware to information stealers and coinminers.
The shift to information stealers isn’t new: in many ways this is “back to the future” for Rig and EKs generally: they were in use before the surge in ransomware starting in 2013 and distributed information stealers and banking trojans in those early days.
But the adoption of coinmining is a new thing for Rig and EKs. Given the trends we’ve seen generally with the sudden surge in coinmining tactics and techniques it’s not surprising. As shown below, the volume of coinmining increase nearly 2,800% in a year.
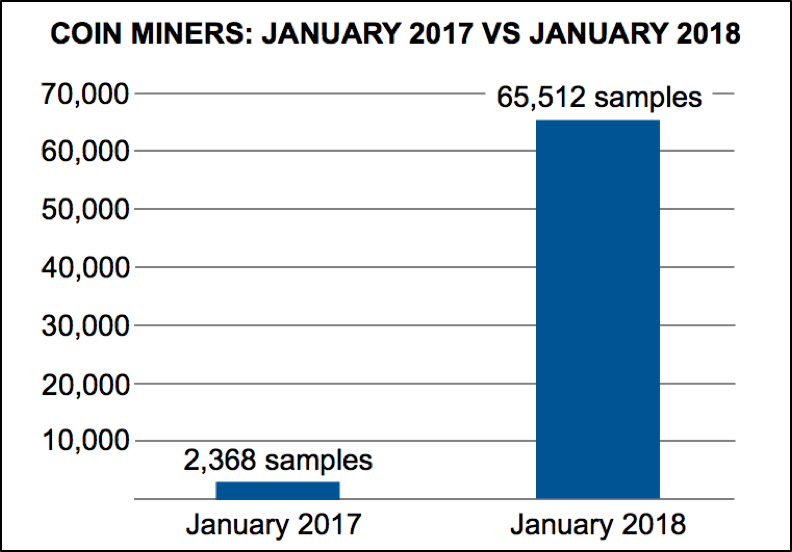
Figure 2: Coin miner samples in January 2017 versus January 2018.
The criminals behind Rig and other EKs have always been focused on maximizing the financial return on their investment in using their wares. And so, we can look at this shift away from ransomware back to information stealers and ahead to coinmining as a possible sign that the era of ransomware is passing at last.
We can’t say why this shift is happening. It could be there is a shift from ransomware due to a declining return on investment because people no longer willing to pay ransom in the wake of WannaCry/ WanaCrypt0r, and Petya/NotPetya. Or there could be a network effect at work and attackers are focusing on coinmining and away from ransomware because others are doing the same.
Whatever the reasons, though, the latest trends in a declining Rig EK give us a possible indicator of the overall future threat landscape. That ransomware is finally on its way out, and that coinmining is taking its mantle as the primary focus for cybercriminals, and thus the threat we should all give primary focus for our prevention efforts.
Get updates from
Palo Alto
Networks!
Sign up to receive the latest news, cyber threat intelligence and research from us
By submitting this form, you agree to our Terms of Use and acknowledge our Privacy Statement.
