
This post is also available in: 日本語 (Japanese)
On August 15, Trend Micro published a blog post detailing a high-risk vulnerability in the VBScript Engine of Microsoft Internet Explorer being exploited in-the-wild (CVE-2018-8373). This vulnerability still affects endpoints running the latest versions of Internet Explorer and Windows which do not have the relevant patches applied.
The exploit was served on a malicious web host: hxxp://windows-updater[.]net/realmuto/wood.php?who=1?????? which was linked to the DarkHotel APT campaign by Qihoo 360, and this actor also exploited another VBScript vulnerability earlier this year (CVE-2018-8174). The preliminary payload was also analyzed thoroughly by Qihoo 360, and is dubbed zlib1.dll.
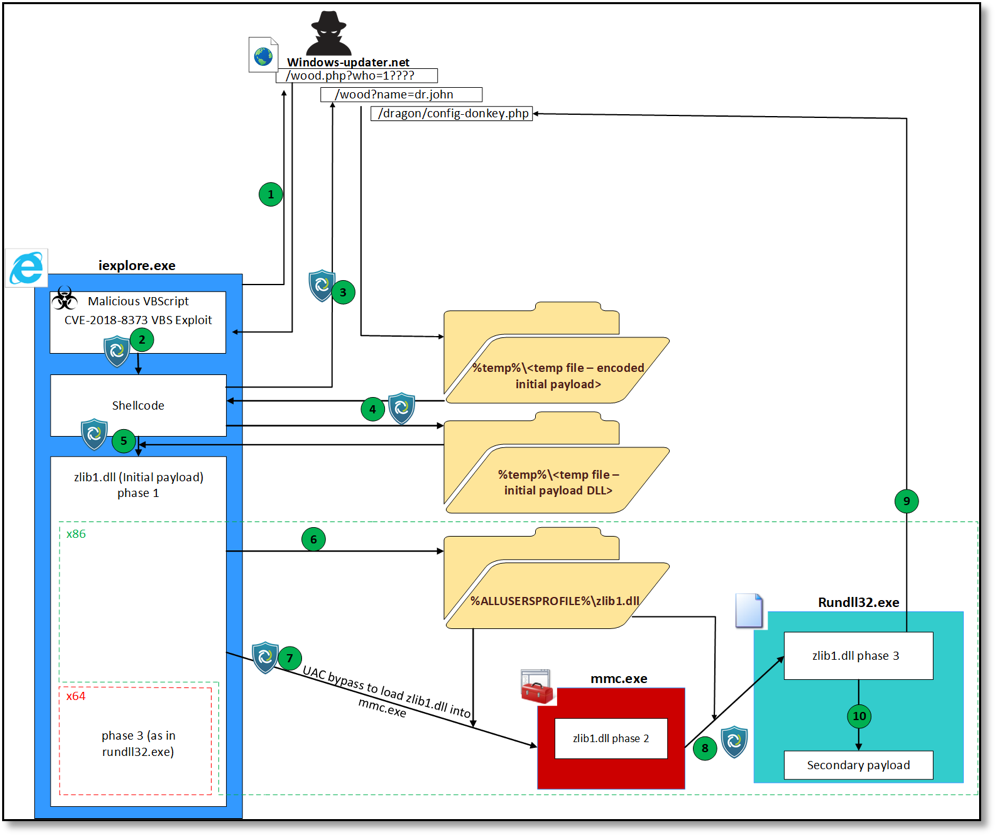
Figure 1. The attack flow as observed in the malicious sample
In Figure 1 we show the attack flow as observed in the malicious sample. First, the victim browses to the exploit URL in the malicious web host (1). The returned webpage contains malicious VBScript which exploits a UAF in vbscript.dll. This exploit implements a RW primitive, uses it to locate and leak the addresses of exported functions, creates a fake CONTEXT structure, and then uses NtContinue to jump to VirtualProtect on the shellcode and directly return to it afterwards (2). The exploitation phase is thoroughly analyzed in Trend Micro’s post.
The shellcode then proceeds to download an initial payload (DLL) from the same malicious web host (hxxp://windows-updater[.]net/realmuto/wood.php?var=xxx&name=dr.john&q=yyy&d=z) to a temporary file (3), decode it to another temporary file (4) and load it using LoadLibrary (5).
On x86 systems, this payload drops itself to %ALLUSERSPROFILE%\zlib1.dll (6), implements a UAC-bypass using mmc.exe (7) and then re-runs itself using rundll32.exe (8). On x64 systems, it runs its main logic directly from iexplore.exe.
The main logic of the initial payload sends the infected computer configuration and downloads a secondary payload from the same host: hxxp://windows-updater[.]net/dragon/config-donkey.php?inst=xxx&name=yyy (9), decodes it and reflectively loads it (10).
We were not able to retrieve samples of the secondary payload for further analysis.
How Traps Prevents this Threat
Palo Alto Networks Traps advanced endpoint protection offers multiple layers of malware and exploit prevention to protect against such complex threats.
Traps prevents a few different and independent techniques of the described exploit using its anti-exploit capabilities. In addition, Traps malware examination flow and local analysis via machine learning, and WildFire integration also prevents the malicious payload from executing at different phases of the attack. In Figure 1 we have marked with the Traps logo different points in the exploitation flow in which Traps would have prevented the attack flow from going forward.
Moreover, even older versions of Traps released years ago would have prevented this exploit from running without applying any special configuration or policy updates.
AutoFocus customers can track this actor via the DarkHotel tag.
Get updates from
Palo Alto
Networks!
Sign up to receive the latest news, cyber threat intelligence and research from us
By submitting this form, you agree to our Terms of Use and acknowledge our Privacy Statement.
