The Third Generation of XDR Has Arrived!
Announcing Cortex XDR 3.0, the third-generation XDR platform that allows security teams to identify and investigate attacks across all endpoint, network, cloud and identity sources from a single console.
When we launched Cortex XDR in 2019, it was the first XDR product in the industry. We wanted to provide a modern cloud-based platform leveraging the latest in machine learning, analytics and automation to fight the many cyber attacks businesses face every day. We were driven by the principle that you can identify and stop the most sophisticated cyber attacks if and only if you can integrate the right set of security data sources and analyze them in real-time. Since Cortex XDR’s inception, our approach has continually proven itself to be the most effective means of preventing and detecting sophisticated cyber attacks, like SolarStorm and those emulated by the MITRE ATT&CK Evaluations.
Today, we released Cortex XDR 3.0, taking a significant step in our mission to know about and stop all cybersecurity attacks. XDR 3.0 extends the key tenets of our XDR platform to cloud environments, ensuring SOC teams can run prevention, detection and response on their cloud assets. The new platform also integrates a rich set of identity data sources and built-in analytics to address a variety of identity-based threats.
Importantly, the third generation of XDR will provide utmost flexibility to security teams by allowing them to ingest data from any third-party source and correlate with other native data sources for richer, deeper investigations.
And that’s not all! We are also very excited to bring security teams a set of forensic investigation capabilities as an add-on module to XDR 3.0. This offering makes generally available the advanced tools we have been using within Palo Alto Networks’ Unit 42 Security Consulting Group.
Read on for more details!
New Capabilities in XDR 3.0
Cortex XDR Extends Native Analytics to Cloud Data, Enabling SOC Teams to Prevent, Detect and Respond to Threats Across Hybrid and Multi-Cloud Environments
SOC threat monitoring teams rely on threat detection and response platforms for holistic visibility and investigations, but are often left in the dark when it comes to cloud security. Cortex XDR 3.0 integrates cloud telemetry (including host data, traffic logs, audit logs and data from the Palo Alto Networks Prisma Cloud solution) with non-cloud endpoint, network and identity data, delivering organization-wide threat detection and response. We’ve added dozens of cloud-specific detection rules targeting common cloud-threat vectors, like cloud escape and cloud-jacking.
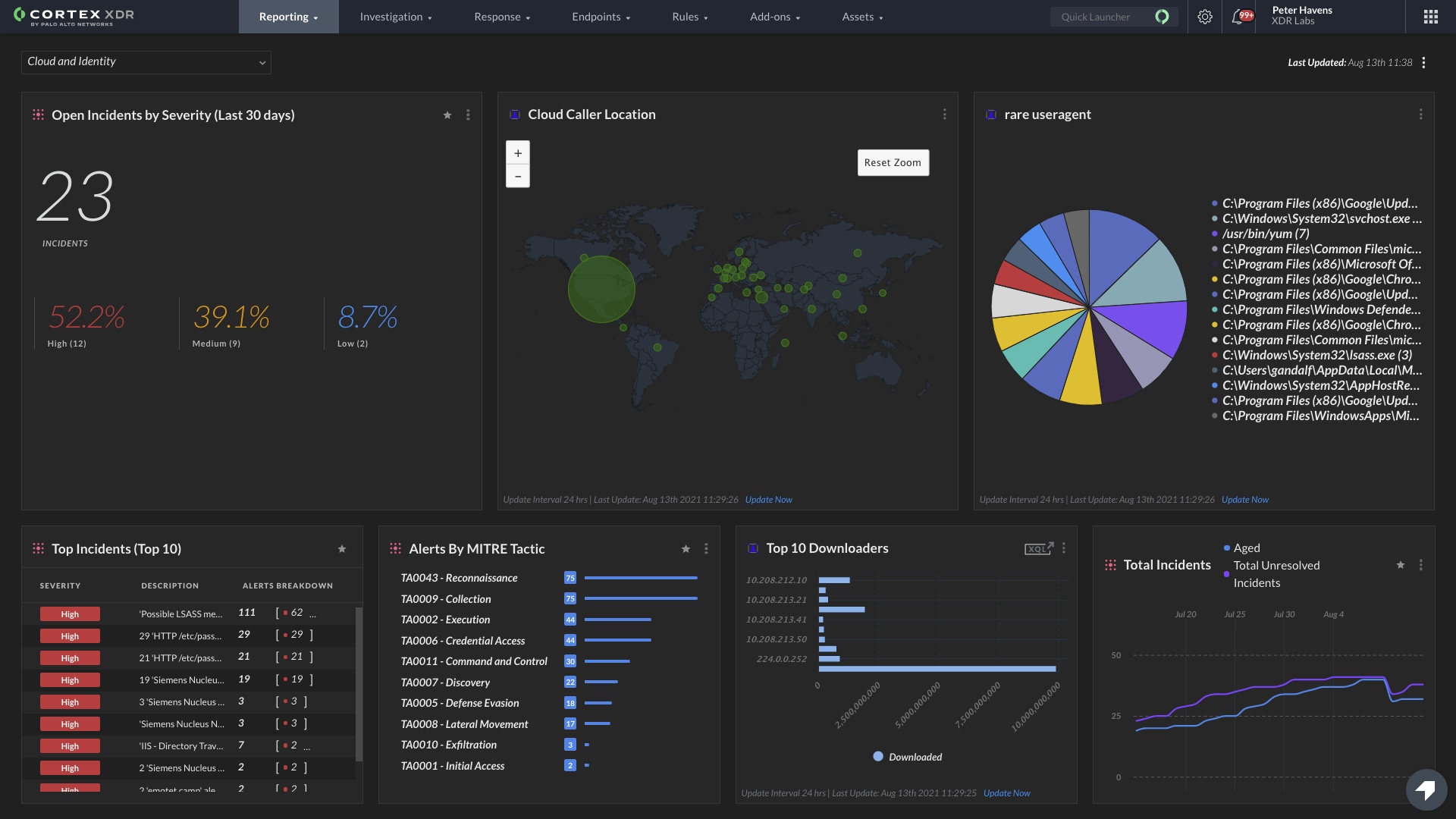
XDR 3.0 also delivers endpoint detection and response (EDR)-level protection for cloud assets, including Windows and Linux virtual machines and Kubernetes containers.
These new cloud capabilities in Cortex XDR 3.0 complement our industry-leading Prisma Cloud solution. Together, they address the unique requirements of both cloud security teams requiring DevOps speed and SOC analysts requiring visibility across their entire enterprise.
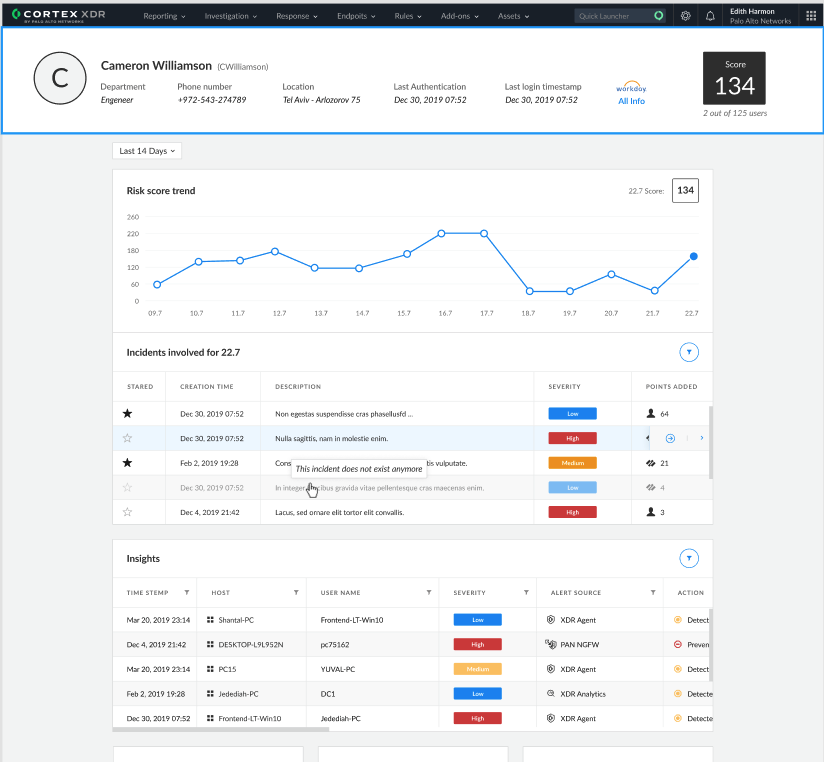
Cortex XDR Expands UEBA Capabilities with Deeper Identity Analytics to Combat Malicious User Activity
Almost all cyber attacks involve compromised identities, which is why analyzing user authentication and access is critical to stopping attacks early in their lifecycle. With Cortex XDR 3.0, we are leveraging ML-based threat detectors against an extensive set of identity data sources, including Active Directory, Identity and Access Management products (including Okta, Ping and Azure AD), human resources (HR) platforms (like Workday) and SASE gateways. Our HR integration with Workday is particularly important — XDR 3.0 adds valuable context to identity-related investigations including a user’s department, manager, phone number, hire date and other details tied into broader multi-dataset incident and causality views.
Cortex XDR’s Third-Party Data Engine Now Delivers the Ability to Ingest, Normalize, Correlate, Query and Analyze Data from Virtually Any Source
When it comes to investigations, the more context, the better. Many customers’ logging efforts run into scalability and efficiency issues, and SOC analysts often need to look into multiple consoles for an investigation to span their various security data. XDR 3.0 offers new functionality for users to:
- Ingest and normalize any data source, including databases, files, FTP, CSV, Syslog, Windows Event Collection (WEC) and more.
- Allow any data to be correlated with threat activity and tagged with MITRE ATT&CK TTPs to help provide a more detailed picture of adversarial movement.
- Facilitate ad-hoc searching across all third-party data sources using XDR’s native query language (XQL), designed and optimized specifically for investigations and threat hunting.
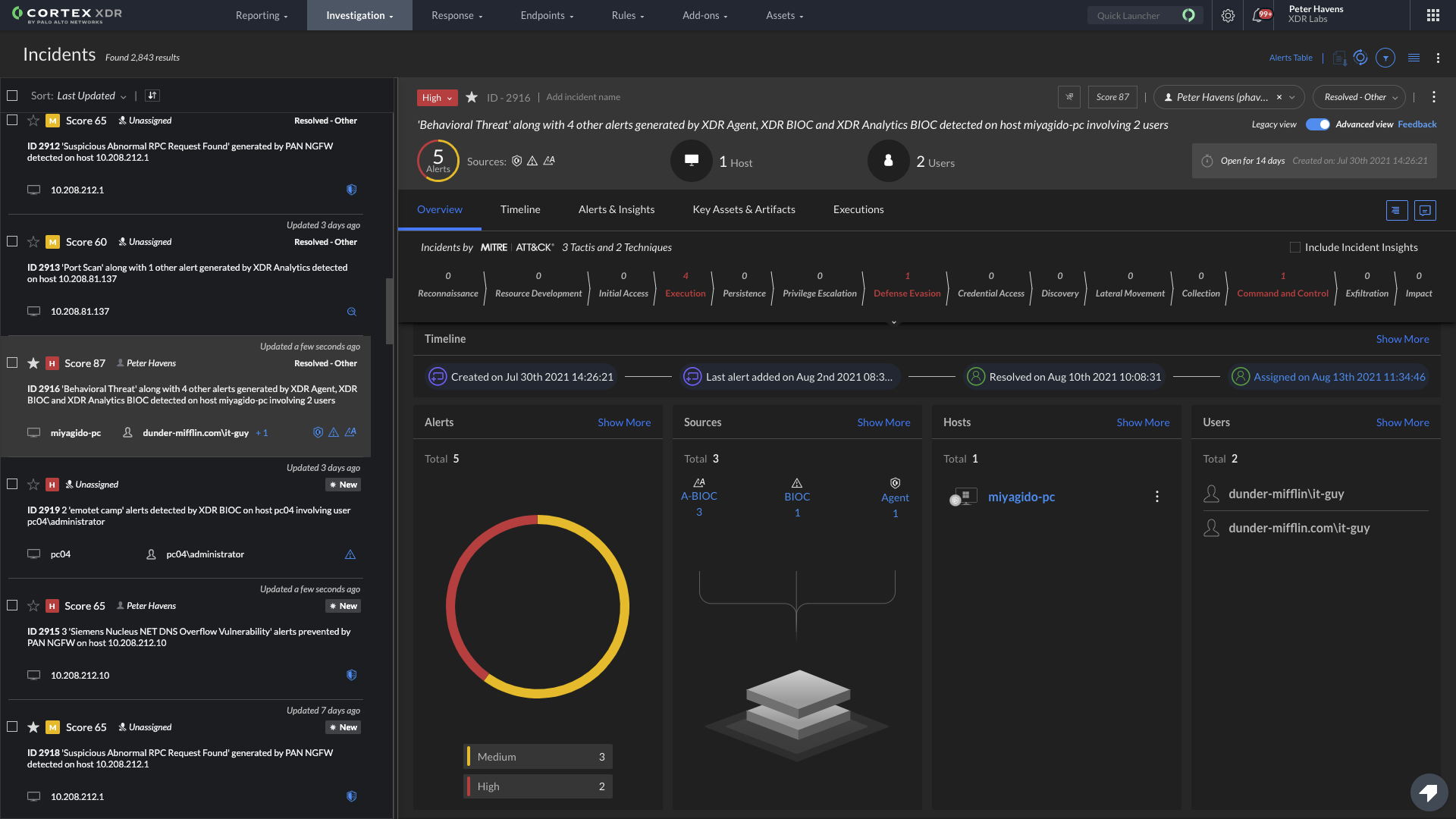
Built-In Forensics Module Brings Native Forensics Capabilities Used by Palo Alto Networks Unit 42 Elite Incident Responders to Customers and Partners
The ability to perform forensic analysis in-house is critical to fully understand the attack and speed remediation. The XDR Forensics Module eliminates the need for deploying, managing and integrating a separate forensics toolkit for collecting and analyzing historical artifacts from endpoints. XDR 3.0 collects program execution, file access, browsing activity, event logs, network sessions and other forensic artifacts, and integrates them into the XDR user interface. The Forensics Module also facilitates data collection for offline endpoints, which is important because network isolation is often one of the first response actions to an attack.
Committed to Creating a Safer, More Secure Future
With these innovations, XDR continues to redefine how security operations teams address complex modern threats and drive greater efficiencies. By tackling the system integration problem of gathering, integrating and analyzing data (and coupling that with the ability to kick off highly optimized and automated workflows), XDR helps solve the challenges of detection, investigation and response at scale in a consolidated manner.
Learn more by registering for our “Next Has Arrived” launch event in September to hear about this monumental release:
- A fireside chat from the attacker’s view — Hear the adversary perspective from Chris Tarbell, former FBI team member who brought down Silk Road, and Hector Monsegur, former “Black Hat” who led the hacker collective Anonymous/LulzSec.
- An industry panel discussing the defender’s view — Hear what tools, processes and strategies defenders are prioritizing.
- An overview and demo of Cortex XDR 3.0 — See the new capabilities first-hand and discover how our third-generation XDR innovations equip defenders to level the playing field.
Related Blogs
Subscribe to the Newsletter!
By submitting this form, you agree to our Terms of Use and acknowledge our Privacy Statement. Please look for a confirmation email from us. If you don't receive it in the next 10 minutes, please check your spam folder.