Managing User Identity in a Cloud-First World
Since the start of the pandemic, companies have become more determined to enhance operational efficiencies and rapidly move to the cloud. Whether to replace legacy systems or to adopt new digital transformation initiatives, traditional IT solutions are being redeployed in the cloud.
At the same time, the way we interact with people and how we work has drastically changed since 2020. Organizations around the globe have had to establish a new normal, and companies are adopting cloud-based tools and applications that enable employees to stay productive during the pandemic, regardless of where they are located.
Remote working is the new normal and remote users should have secure access to all apps, have a great user experience and enjoy uncompromising performance. To make this a reality, an all-encompassing Zero Trust approach to network security is critical for safeguarding productivity in the new reality of remote, mobile and hybrid work. To achieve Zero Trust, organizations need to be able to easily and consistently secure users across the branch, data center, public clouds, and remote workforce.
Traditional Security Tools Fail Zero Trust
According to a recent ESG report, “Trends in IAM: Cloud-driven Identities," 87% of organizations are migrating to or are already using cloud-based identity sources in addition to their on-prem repositories. However, unifying identity is challenging which makes Zero Trust difficult to achieve. Security teams are struggling to consistently verify users and enforce identity-based security at all times for three primary reasons:
- User information is distributed between multiple identity providers resulting in increased operational complexity;
- Authentication with cloud identity providers typically requires a laborious authentication setup, with unique configuration requirements for each security device with every identity provider; and
- Lack of visibility into user activity and consistent application of identity controls across the network results in gaps that can weaken an organization's security posture.
Existing solutions are designed for a single source of identity, either on-prem or cloud identity stores, leading to inconsistent security across the infrastructure. Moreover, every identity store and any changes by them have to be manually added and managed on the firewalls. Moving from on-prem to cloud or other identity sources can take months or years.
How do you consistently identify your users when the identity is fragmented in so many different identity stores?
Continuing our six-part Tech Deep Dive Miniseries, Episode 6 covers how our newly enhanced Cloud Identity Engine can help security teams simplify Zero Trust with easy-to-deploy user identity and access across all locations.
If you missed our previous episodes, you can check them out now:
Episode 1: Industry Firsts in Campus and Data Center Security, 3x Faster with ML-Powered NGFW
Episode 2: Evolution of IPS to Advanced Threat Prevention
Episode 3: Innovations in Web Security to Stop Evasive Threats
Episode 4: Smart and Easy IoT Security for Zero Trust
Episode 5: What is AIOps, Optimizing Your NGFW in a Snap
Making Zero Trust a Reality with an Enhanced Cloud Identity Engine
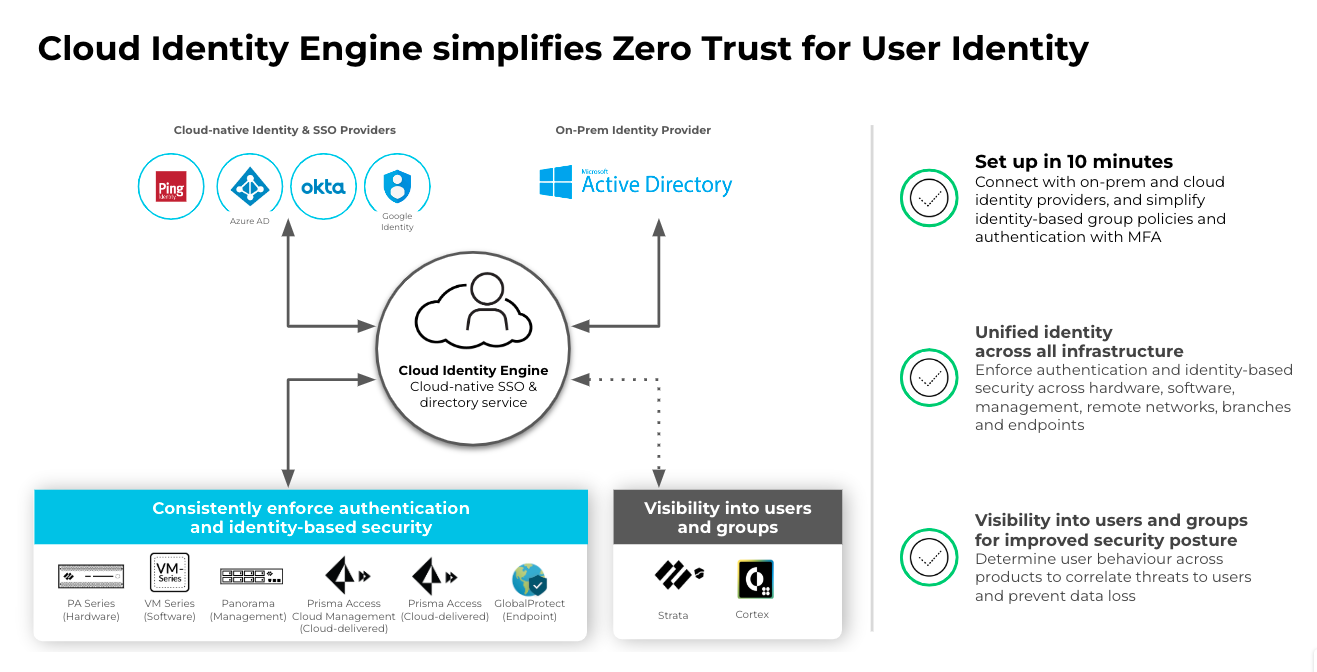
Identity-based security controls are a foundational requirement to achieve Zero Trust. With Nebula (PAN-OS 10.2), the latest upgrade of our industry-leading PAN-OS software, we have continued to build on our identity-based security innovations with an enhanced version of Cloud Identity Engine. With the new Cloud Identity Engine in PAN-OS 10.2, customers can get:
- Simplified identity-based group policies with support for additional cloud based identity providers, including Okta and Google Cloud directories. Ensure privacy of personal data by selectively distributing employee’s data based on company policy with SCIM granular access control.
- Simplified cloud authentication set up and management with Cloud IAM vendors. With the release of Nebula, security teams can connect users easily when authenticating with multiple authentication types – SAML 2.0 Idps (Microsoft AD, Azure AD, Okta, Ping, Google Identity) and cert-based authentication – across enterprise networks, e.g., in merger and acquisition situations.
- Unified identity across infrastructure. Enforce authentication and identity-based security across hardware (PA-series), software (VM-series), management (Panorama), Cloud Management, remote networks (Prisma Access), branches (Prisma Access), and endpoints (GlobalProtect).
- Extending visibility into users and groups for security and health monitoring services to determine user behavior across the network, correlate threats, and prevent data loss (e.g., SaaS Inline, Device Insights, ADEM, CDL, Explore, Visualization and Reporting).
To learn more about Cloud Identity Engine, be sure to register for Episode 6 in our Tech Deep Dive Miniseries, Managing User Identity in a Cloud-First World or download our Cloud Identity Engine Solution Brief.
If you missed our previous blogs, check out what’s new with our NGFWs and security infrastructure; learn about the latest in Intrusion Prevention; learn how our Advanced URL Filtering and DNS Security solutions can protect customers in real time; learn how you can reduce the unseen and unmitigated 30% of risk across your enterprise by implementing Zero Trust for IoT devices; and learn how AIOPs for NGFW can proactively strengthen your security posture and prevent firewall disruptions.
Related Blogs
Subscribe to Network Security Blogs!
By submitting this form, you agree to our Terms of Use and acknowledge our Privacy Statement. Please look for a confirmation email from us. If you don't receive it in the next 10 minutes, please check your spam folder.