Flexibility Meets Security with Custom Compliance Checks for Cloud VMs
A recent global survey from 2020 shows that virtual machines (VMs) are the most widely-used cloud infrastructure technologies, accounting for 30% of all cloud workloads. Far from being overshadowed by containers, hosts continue to be integral to cloud native development, underscoring the need for robust and flexible host protection, including compliance.
Prisma Cloud has built-in support for hundreds of distinct compliance checks, that cover images, containers, hosts, clusters and clouds. The checks are based on industry standards (such as CIS benchmarks), vendor and community recommendations, as well as our own set of recommendations.
Although we provide this wide range of compliance checks, users often want to write their own checks or use a new compliance standard which we do not yet support out-of-the-box. That's why, as part of our most recent release, Prisma Cloud now enables users to create their own custom compliance checks for cloud VMs (hosts), the same way they already do for containers.
Simple, Consistent and Powerful Checks For Hosts
As with container images, custom compliance checks for hosts are supported through shell scripts. Each custom check is tied to a single shell script that performs all required actions and provides an exit code, with 0 indicating success and 1 indicating failure.
Users can create custom checks that work across both container images and hosts without having to rewrite them or learn a new method to create checks just for hosts. Scripts are executed in the default shell unless otherwise specified. To use a different shell, customers can add a directive to the relevant shell, for example:
Security Considerations
With this new capability, Prisma Cloud customers can use the same scripts for both hosts and container images and can run the compliance checks with unrestricted privileges. While we wanted to carry this consistent experience across all functionality for container images and hosts, there was a key security factor we had to prioritize for one area.
For containers, our unified agent framework, Defender, runs compliance checks inside a restricted, sandboxed container instantiated from the image being scanned, thus avoiding the unnecessary risk associated with running arbitrary code. The same method could not be used for hosts, as it is not ideal to create a new host in a customer environment just for the purpose of running a compliance check.
Instead, we gave customers the freedom to decide which hosts need this capability and only enable it on those hosts. This means that custom compliance checks are turned off by default for both existing host Defenders as well as new installations, unless explicitly enabled on particular hosts. This gives customers the assurance that their hosts cannot be exploited remotely, as only authorized users who have access to those hosts can enable custom checks on them.
How To Use Custom Compliance Checks For Hosts
Custom compliance checks for hosts can be configured via the following steps:
Step 1
Enable custom compliance checks for hosts via Manage > Defenders > Advanced settings.
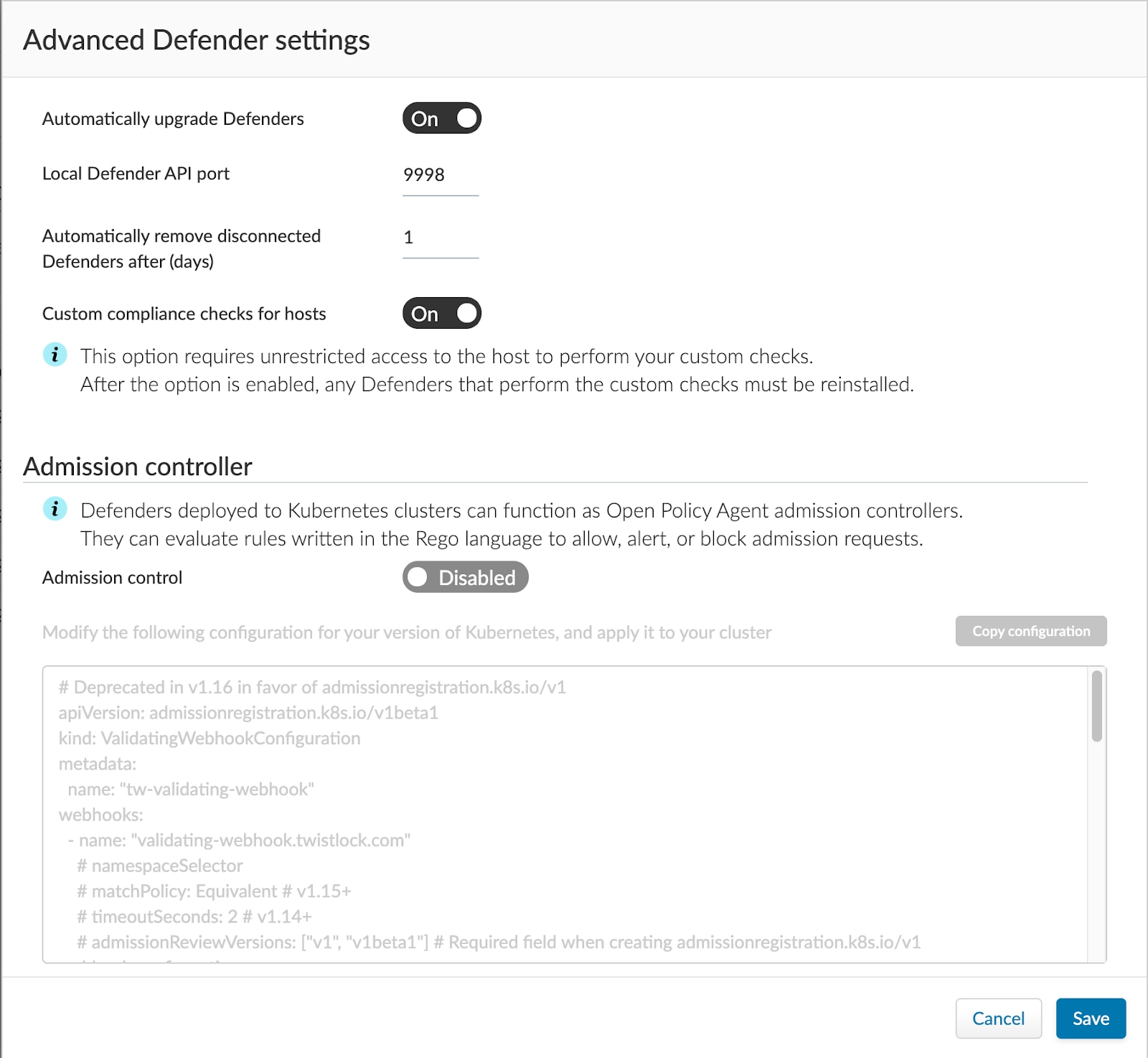
Step 2
Deploy Defenders that require custom compliance checks or redeploy existing defenders for hosts that require custom compliance checks. (Learn about Defenders in our documentation).
Step 3
To write a new custom compliance check, click on “Add check” via Defend > Compliance > Custom. You can also use an existing check as seen in the screenshot below.
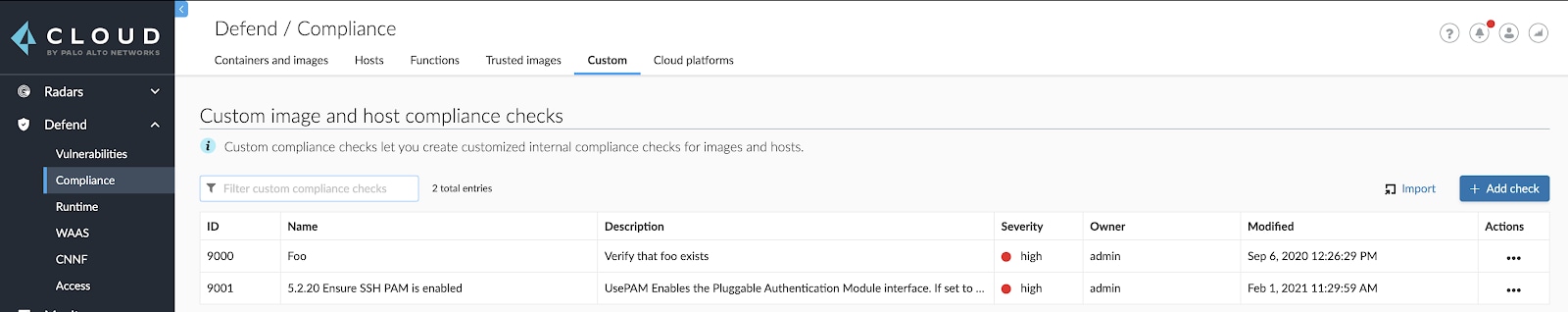
Step 4
Update the compliance policy for hosts to run your target checks via Defend > Compliance > Hosts.
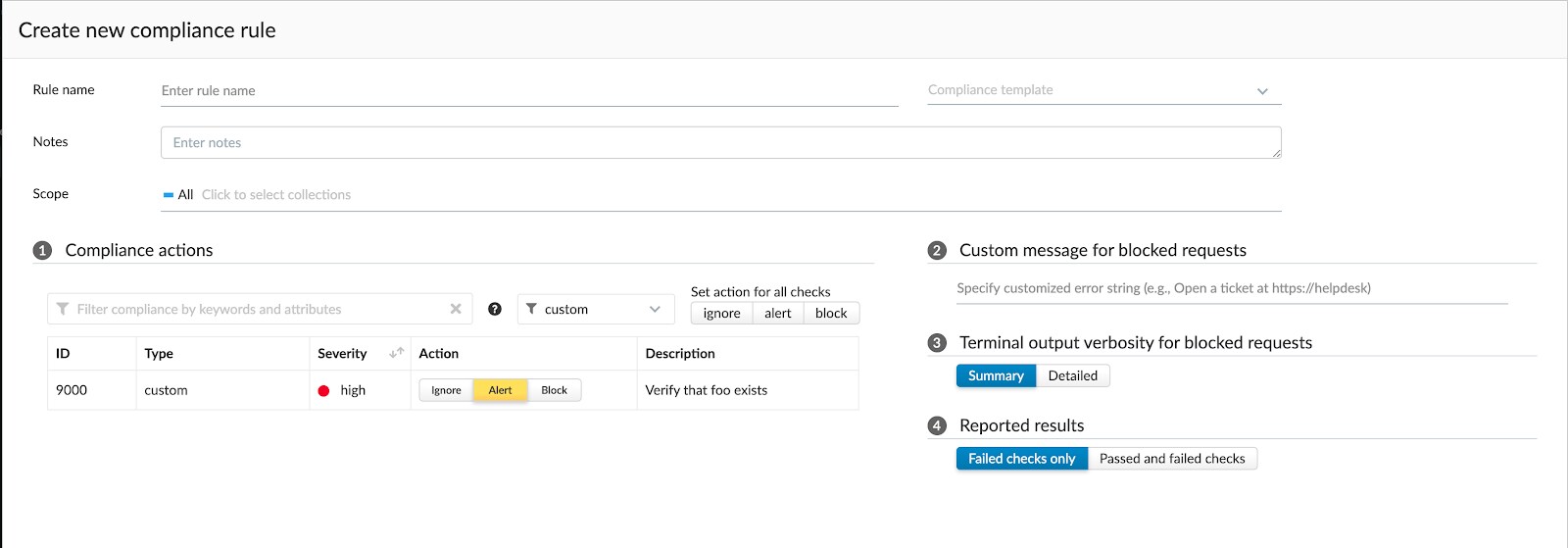
Step 5
View reports for custom compliance checks like any other compliance check, via Monitor > Compliance.
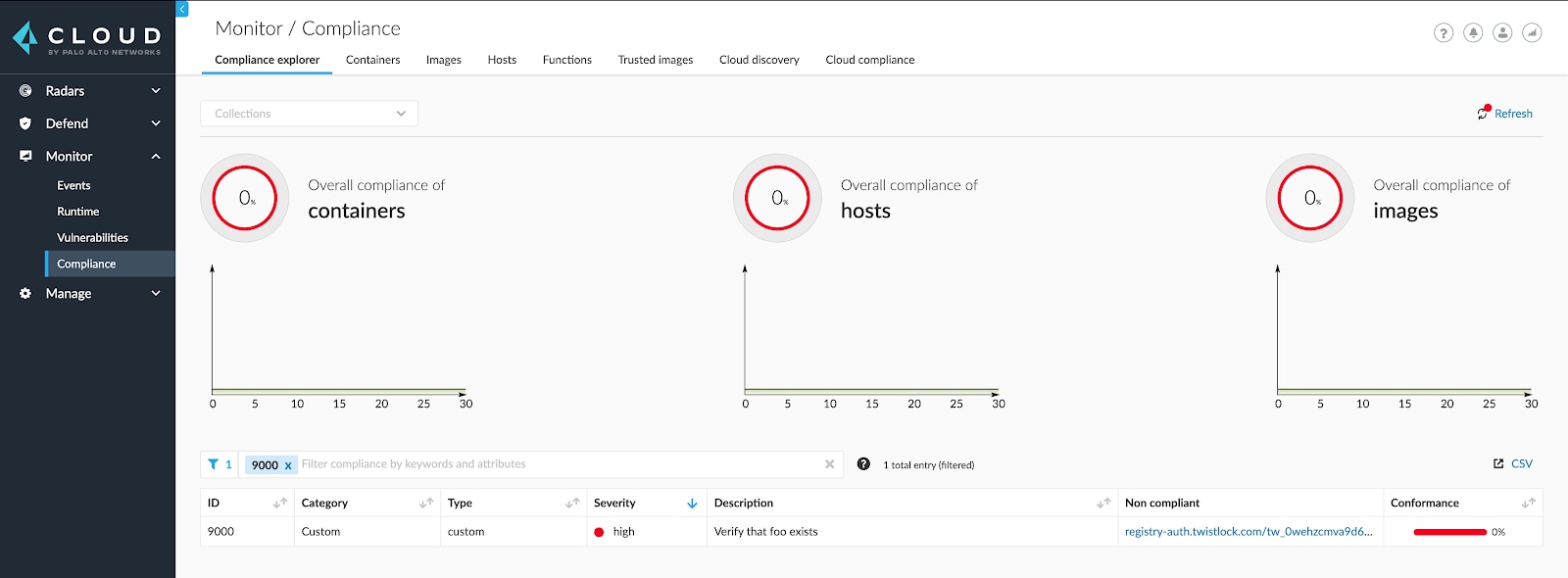
Custom policies are included in Compliance Explorer next to the other compliance policies for your environment. This dashboard ensures that security and compliance teams have comprehensive and up-to-date views of cloud native compliance.
For additional information on custom compliance checks for hosts, refer to the Prisma Cloud Compute admin guide.
A Real-World Example
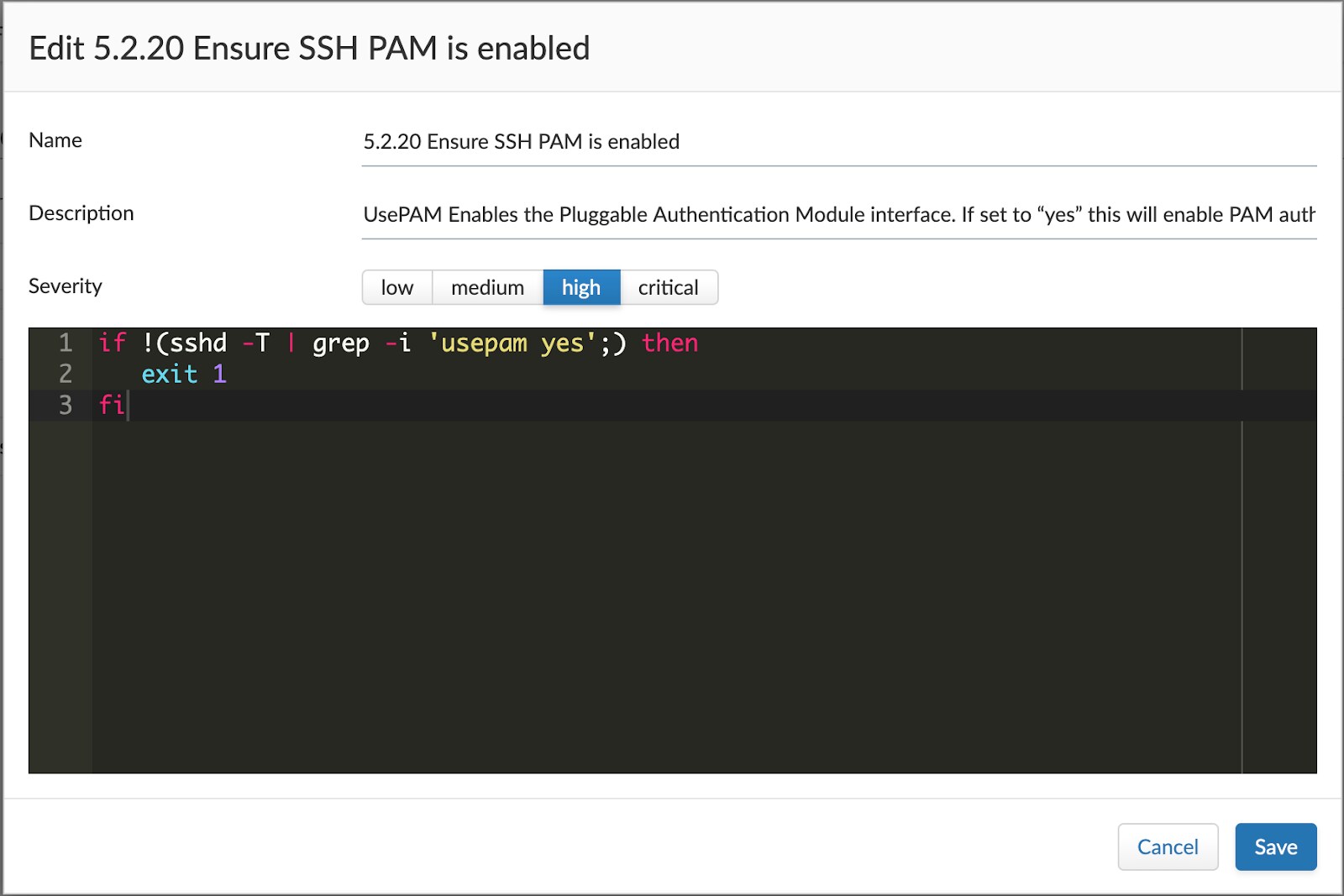
A customer wanted to use the CIS Linux Benchmark 2.0 for their environment. While we are planning to introduce support in a future release, the customer was interested in applying at least some of the checks immediately. Using custom compliance checks for hosts, the customer was able to create similar checks based on the benchmark, and fulfill their immediate needs.
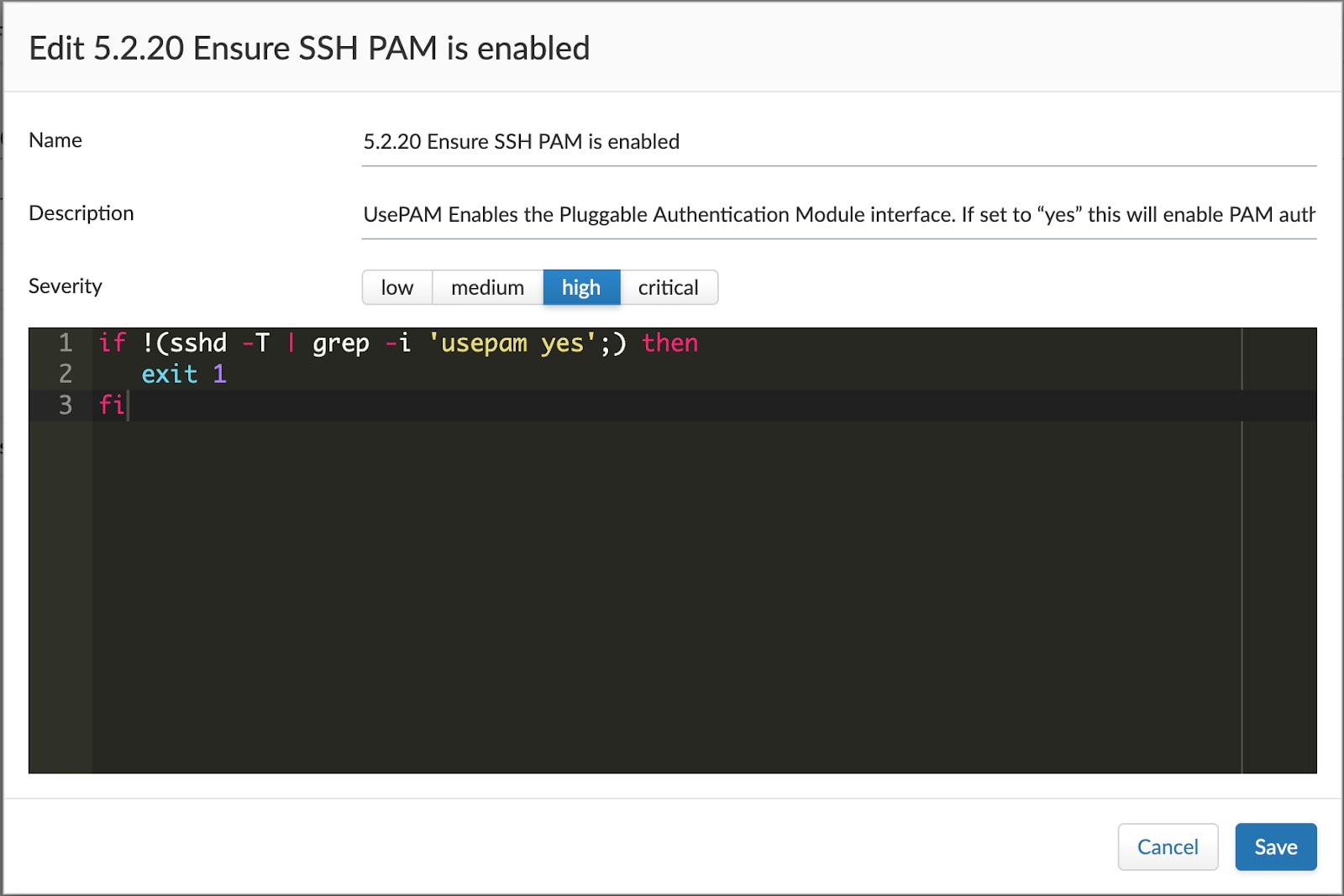
An example of one of the custom checks based on Linux CIS 2.0 can be seen below:
Conclusion
These new flexible capabilities continue to build on our ever-expanding set of robust protections for hosts. With these custom compliance checks, Prisma Cloud helps customers meet their compliance needs, whether it is to address an emerging public benchmark or to satisfy an internal requirement.
For more information on host security, please visit the host security webpage or watch this demo. You can also check out our virtual event focused on host security and best practices for securing VMs, a part of our Power of the Platform series.
Related Blogs
Subscribe to Cloud Native Security Blogs!
By submitting this form, you agree to our Terms of Use and acknowledge our Privacy Statement. Please look for a confirmation email from us. If you don't receive it in the next 10 minutes, please check your spam folder.