
A new Thanos ransomware strain is trying and failing to deliver the ransom note onto compromised systems by overwriting the computers' Windows master boot record (MBR).
The new Windows MBR locker module has been discovered by security researchers at Palo Alto Networks' Unit 42 while analyzing two attacks were Thanos ransomware affiliates successfully encrypted devices of state-controlled organizations from the Middle East and North Africa during early July 2020.
"Overwriting the MBR is a more destructive approach to ransomware than usual," Unit 42 threat intelligence analyst Robert Falcone said. "Victims would have to expend more effort to recover their files – even if they paid the ransom."
"Fortunately, in this case, the code responsible for overwriting the MBR caused an exception because the ransom message contained invalid characters, which left the MBR intact and allowed the system to boot correctly."
Similar behavior was previously exhibited by Petya ransomware in 2016 when it was seen replacing infected devices' MBR to display a ransom note lock screen, as well as using a fake CHKDSK prompt to encrypt the Master File Table (MFT) in the background, rendering all files inaccessible.
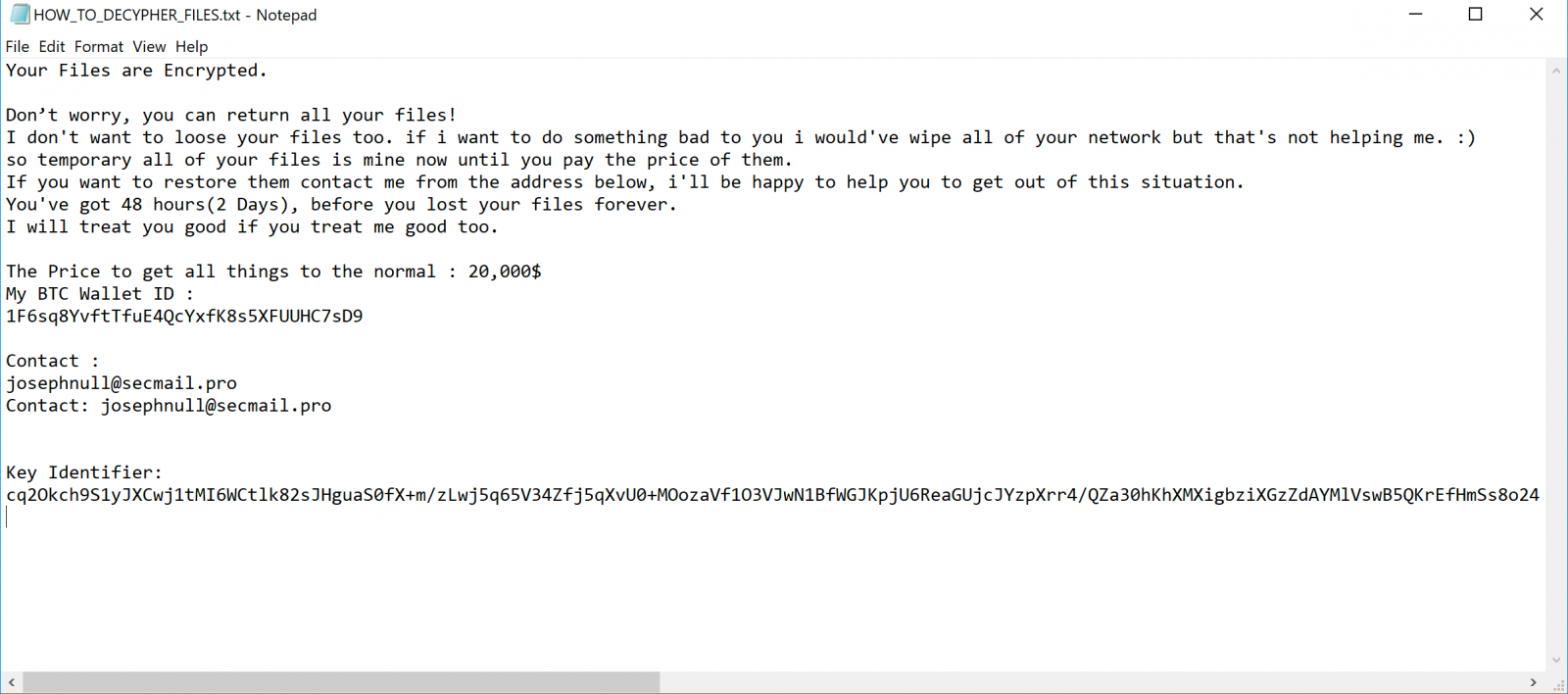
Even though they failed to overwrite the compromised computers' MBRs, the Thanos operators still dropped ransom note they regular way by creating HOW_TO_DECIPHER_FILES.txt text files and asking the victims to pay $20,000 to recover their data.
The researchers think that the attackers gained access to the targets' networks before the ransomware payloads were deployed since they were able to find valid credentials within the samples recovered after the attack.
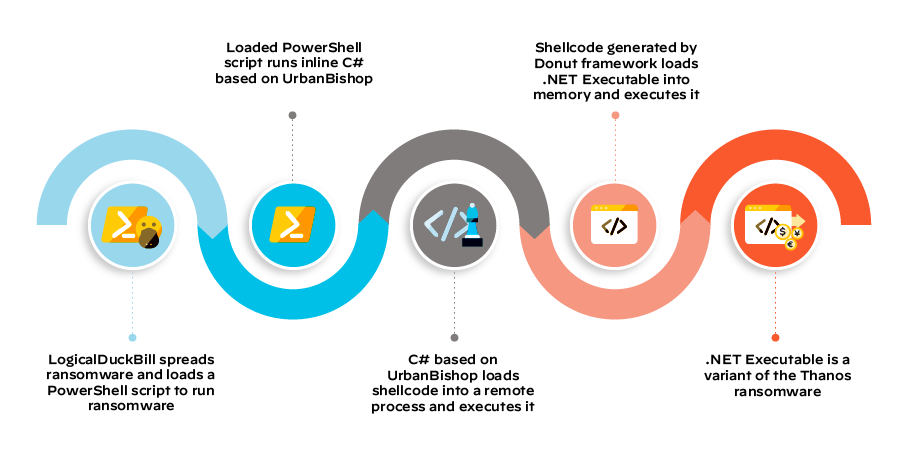
The threat actors also used a layer-based approach to deliver the payloads, with custom PowerShell scripts, inline C# code, and shellcode being used to deliver the ransomware locally and to other systems on the victims' networks using the stolen credentials mentioned above.
While the two state-run entities from the Middle East and North Africa had their systems encrypted using Thanos ransomware payloads, Unit 42 has no info if the attackers were paid for their "efforts."
Thanos ransomware is a Ransomware-as-a-Service (RaaS) operation advertised on several Russian-speaking hacker forums since February 2020 that enables affiliates to create custom ransomware payloads with the help of a builder provided by the developer.
Some Thanos samples have been previously tagged as Hakbit ransomware because of the different encryption extensions used by this RaaS' affiliates, but Recorded Future's Insikt Group says that they're the same malware based on core functionality, code similarity, and string reuse.v
Thanos is also the first to use the RIPlace anti-ransomware evasion technique together with numerous other quite advanced features designed to make it a serious threat as it can steal files and auto-spread between Windows devices using the PSExec program bundled with the SharpExec offensive security toolkit.
Three months ago, in June 2020, Thanos affiliates have failed to persuade multiple European companies from Austria, Switzerland, and Germany to pay €250 worth of bitcoins ransoms after encrypting their systems.


Comments
JohnC_21 - 3 years ago
I have to assume this would not work on a GPT disk as it only has a protected MBR.
GT500 - 3 years ago
It's been 4 years since Petya already?