[](https://www.paloaltonetworks.com/cortex?ts=markdown)  [](https://www.paloaltonetworks.com/cortex?ts=markdown) 
* [](https://www.paloaltonetworks.com/cortex?ts=markdown)
* [Industry Validation](https://www.paloaltonetworks.com/cortex/whycortex?ts=markdown)
* Products
 Products
Products
* [AI-Driven SOC](https://www.paloaltonetworks.com/cortex?ts=markdown)
* [Cortex XSIAM](https://www.paloaltonetworks.com/cortex/cortex-xsiam?ts=markdown)
* [Cortex XDR](https://www.paloaltonetworks.com/cortex/cortex-xdr?ts=markdown)
* [Cortex AgentiX](https://www.paloaltonetworks.com/cortex/agentix?ts=markdown)
* [Cortex XSOAR](https://www.paloaltonetworks.com/cortex/cortex-xsoar?ts=markdown)
* [Cortex Exposure Management](https://www.paloaltonetworks.com/cortex/exposure-management?ts=markdown)
* [Cortex Xpanse](https://www.paloaltonetworks.com/cortex/cortex-xpanse?ts=markdown)
* [Cortex Advanced Email Security](https://www.paloaltonetworks.com/cortex/advanced-email-security?ts=markdown)
* [Managed Detection \& Response](https://www.paloaltonetworks.com/cortex/managed-detection-and-response?ts=markdown)
* [Managed XSIAM](https://www.paloaltonetworks.com/cortex/managed-xsiam?ts=markdown)
* [Cloud Security](https://www.paloaltonetworks.com/cortex/cloud?ts=markdown)
* [Cortex Cloud](https://www.paloaltonetworks.com/cortex/cloud?ts=markdown)
* [Application Security](https://www.paloaltonetworks.com/cortex/cloud/application-security?ts=markdown)
* [Cloud Posture Security](https://www.paloaltonetworks.com/cortex/cloud/cloud-posture-security?ts=markdown)
* [Cloud Runtime Security](https://www.paloaltonetworks.com/cortex/cloud/runtime-security?ts=markdown)
[
The Forrester Total Economic Impact^™^ of Cortex XSIAM
257% 3-year ROI and \<6-month payback for SOC transformation.
Get the facts](https://start.paloaltonetworks.com/forrester-total-economic-impact-xsiam)
* Solutions
 Solutions
[Threat Prevention, Detection \& Response](https://www.paloaltonetworks.com/cortex/detection-and-response?ts=markdown)
* [Cloud Detection and Response](https://www.paloaltonetworks.com/cortex/cloud-detection-and-response?ts=markdown)
* [Security Information and Event Management](https://www.paloaltonetworks.com/cortex/modernize-siem?ts=markdown)
* [Endpoint Protection](https://www.paloaltonetworks.com/cortex/endpoint-protection?ts=markdown)
* [Endpoint Detection and Response](https://www.paloaltonetworks.com/cortex/endpoint-detection-and-response?ts=markdown)
* [Extended Detection \& Response](https://www.paloaltonetworks.com/cortex/detection-and-response?ts=markdown)
* [Managed Detection \& Response](https://www.paloaltonetworks.com/cortex/managed-detection-and-response?ts=markdown)
* [Managed Threat Hunting](https://www.paloaltonetworks.com/cortex/managed-threat-hunting?ts=markdown)
* [Ransomware Protection](https://www.paloaltonetworks.com/cortex/ransomware-protection?ts=markdown)
* [Digital Forensics](https://www.paloaltonetworks.com/cortex/digital-forensics?ts=markdown)
[Security Automation](https://www.paloaltonetworks.com/cortex/security-operations-automation?ts=markdown)
* [Network Security Automation](https://www.paloaltonetworks.com/cortex/network-security-automation?ts=markdown)
* [Incident Case Management](https://www.paloaltonetworks.com/cortex/incident-case-management?ts=markdown)
* [Security Operations Workflow Automation](https://www.paloaltonetworks.com/cortex/security-operations-automation?ts=markdown)
* [Threat Intel Management](https://www.paloaltonetworks.com/cortex/threat-intel-management?ts=markdown)
* [Extended Data Lake (XDL)](https://www.paloaltonetworks.com/cortex/cortex-xdl?ts=markdown)
* [Agentic Assistant](https://www.paloaltonetworks.com/cortex/cortex-agentic-assistant?ts=markdown)
[External Attack Surface Protection](https://www.paloaltonetworks.com/cortex/cortex-xpanse/attack-surface-management?ts=markdown)
* [Attack Surface Management](https://www.paloaltonetworks.com/cortex/cortex-xpanse/attack-surface-management?ts=markdown)
* [Unmanaged Cloud Security](https://www.paloaltonetworks.com/cortex/cortex-xpanse/unmanaged-cloud-asset-management?ts=markdown)
* [Third-Party Security](https://www.paloaltonetworks.com/cortex/cortex-xpanse/attack-surface-management-for-third-party-and-supply-chain-security?ts=markdown)
* [Compliance Management](https://www.paloaltonetworks.com/cortex/cortex-xpanse/compliance-management?ts=markdown)
* [Internet Operations Management](https://www.paloaltonetworks.com/cortex/cortex-xpanse/internet-operations-management?ts=markdown)
* [Remote Network Security](https://www.paloaltonetworks.com/cortex/cortex-xpanse/asm-for-remote-workers?ts=markdown)
[Cloud Security](https://www.paloaltonetworks.com/cortex/cloud?ts=markdown)
* [Application Security](https://www.paloaltonetworks.com/cortex/cloud/application-security?ts=markdown)
* [Cloud Runtime Security](https://www.paloaltonetworks.com/cortex/cloud/runtime-security?ts=markdown)
* [Cloud Posture Security](https://www.paloaltonetworks.com/cortex/cloud/cloud-posture-security?ts=markdown)
[
Tested. Reviewed. Proven
See Industry Validation](https://www.paloaltonetworks.com/cortex/cortex-xdr-industry-validation?ts=markdown)
* [Blog](https://www.paloaltonetworks.com/blog/security-operations/?ts=markdown)
* Resources
 Resources
Resources
* [White Papers](https://www.paloaltonetworks.com/resources?q=cortex&_charset_=UTF-8&fq=RC_TYPE_DFACET%3Apan%253Aresource-center%252Frc-type%252Fwhitepaper&ts=markdown)
* [Cortex Partners](https://cortex.marketplace.pan.dev/marketplace/)
* [Customer Stories](https://www.paloaltonetworks.com/cortex/customer-stories?ts=markdown)
* [Cortex vs. The Competition](https://www.paloaltonetworks.com/cortex/cortex-vs-the-competition?ts=markdown)
* [Cortex XSOAR Marketplace](https://xsoar.pan.dev/marketplace)
* [Events](https://www.paloaltonetworks.com/resources/cortex-events?ts=markdown)
* [Datasheets](https://www.paloaltonetworks.com/resources?q=Cortex&_charset_=UTF-8&fq=RC_TYPE_DFACET%3Apan%253Aresource-center%252Frc-type%252Fdatasheet&ts=markdown)
* [Research Reports](https://www.paloaltonetworks.com/resources?q=cortex&_charset_=UTF-8&fq=RC_TYPE_DFACET%3Apan%253Aresource-center%252Frc-type%252Fresearch&ts=markdown)
* [Videos](https://www.paloaltonetworks.com/resources?q=cortex&_charset_=UTF-8&fq=RC_TYPE_DFACET%3Apan%253Aresource-center%252Frc-type%252Fvideo&ts=markdown)
* [Cortex XDR Resource Center](https://www.paloaltonetworks.com/cortex/cortex-xdr-resource-center?ts=markdown)
[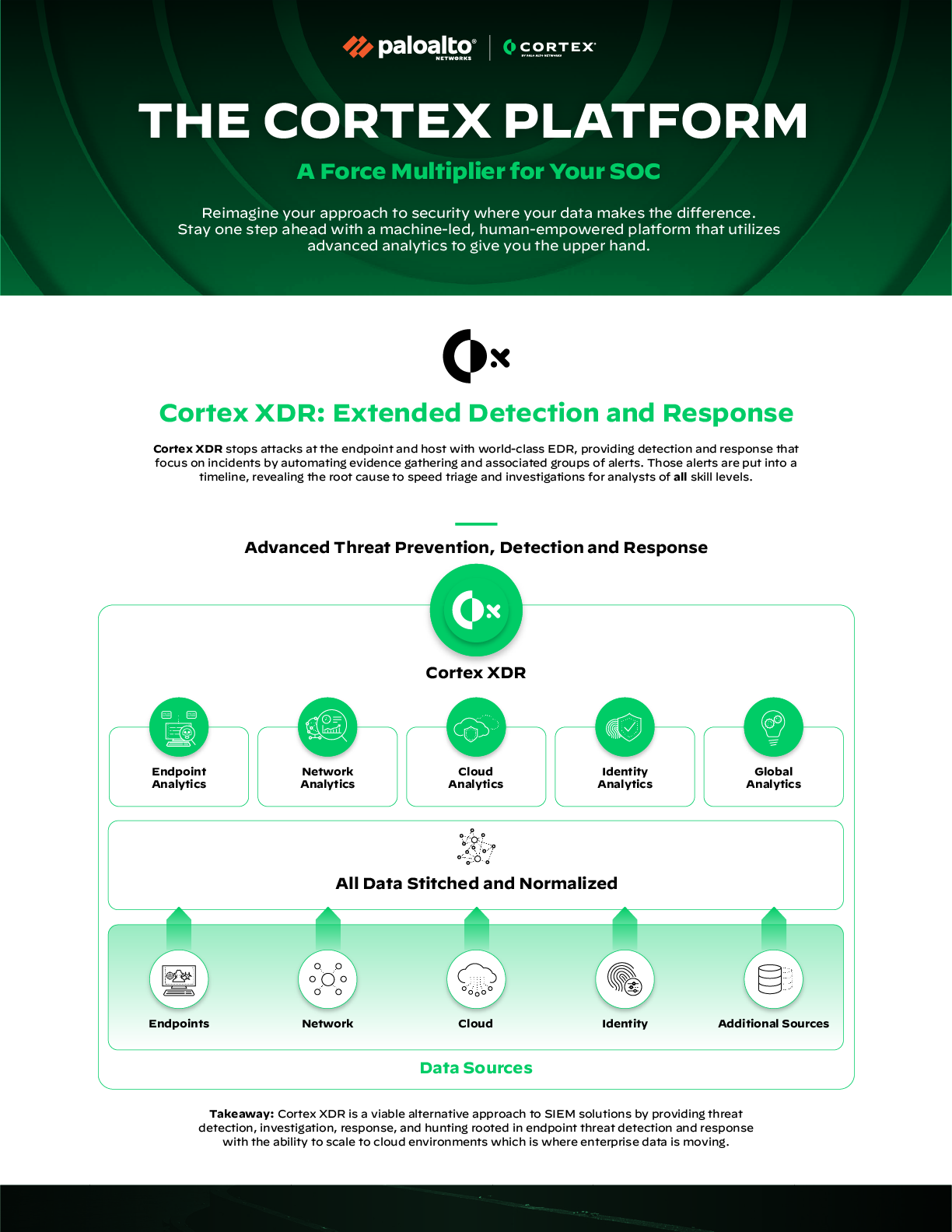
DIGITAL ASSET
THE CORTEX PLATFORM](https://www.paloaltonetworks.com/resources/infographics/soc-transformation-infographic?ts=markdown)
[
WHITEPAPER
Cortex XSIAM Solution Brief](https://www.paloaltonetworks.com/resources/techbriefs/cortex-xsiam?ts=markdown)
[
REPORT
Unlock customized recommendations for transforming your SecOps.](https://www.paloaltonetworks.com/cortex/secops-readiness-report?ts=markdown)
* Get In Touch
 Get In Touch
Get in Touch
* [Request a Demo](https://www.paloaltonetworks.com/cortex/request-demo?ts=markdown)
* [Contact us](https://www.paloaltonetworks.com/company/contact-sales?ts=markdown)
* [Attend a Workshop](https://www.paloaltonetworks.com/cortex/cortex-xdr/hands-on-workshop?ts=markdown)
* [Find a Partner](https://technologypartners.paloaltonetworks.com/English/directory)
* [Join our Community](https://live.paloaltonetworks.com/)
[
SecOps analyst: A day in the life.
Start product tour](https://www.paloaltonetworks.com/resources/infographics/xsoar-product-tour?ts=markdown)
*
* [Request a Demo](https://www.paloaltonetworks.com/cortex/request-demo?ts=markdown)
 
[](https://www.paloaltonetworks.com/cortex?ts=markdown)
Search
All
* [Tech Docs]()
Close search modal
1. [Cyberpedia](https://www.paloaltonetworks.com/cyberpedia?ts=markdown)
2. [Threats](https://www.paloaltonetworks.com/cyberpedia/threat?ts=markdown)
3. [Cyberthreat Intelligence](https://www.paloaltonetworks.com/cyberpedia/what-is-cyberthreat-intelligence-cti?ts=markdown)
4. [What is a Threat Intelligence Platform (TIP)?](https://www.paloaltonetworks.com/cyberpedia/what-is-a-threat-intelligence-platform?ts=markdown)
Table of Contents
* [What Is Cyber Threat Intelligence (CTI)?](https://www.paloaltonetworks.com/cyberpedia/what-is-cyberthreat-intelligence-cti?ts=markdown)
* [What Data Is Considered Threat Intelligence?](https://www.paloaltonetworks.com/cyberpedia/what-is-cyberthreat-intelligence-cti#considered?ts=markdown)
* [Sources of Threat Intelligence](https://www.paloaltonetworks.com/cyberpedia/what-is-cyberthreat-intelligence-cti#sources?ts=markdown)
* [Tools and Services in Threat Intelligence](https://www.paloaltonetworks.com/cyberpedia/what-is-cyberthreat-intelligence-cti#tools?ts=markdown)
* [Practical Implementation of Threat Intelligence](https://www.paloaltonetworks.com/cyberpedia/what-is-cyberthreat-intelligence-cti#implementation?ts=markdown)
* [The Threat Intelligence Lifecycle: An Overview](https://www.paloaltonetworks.com/cyberpedia/what-is-cyberthreat-intelligence-cti#lifecycle?ts=markdown)
* [Building an Effective Threat Intelligence Program](https://www.paloaltonetworks.com/cyberpedia/what-is-cyberthreat-intelligence-cti#program?ts=markdown)
* [Threat Intelligence FAQs](https://www.paloaltonetworks.com/cyberpedia/what-is-cyberthreat-intelligence-cti#faq?ts=markdown)
* [Threat Intelligence Use Cases and Examples](https://www.paloaltonetworks.com/cyberpedia/threat-intelligence-use-cases-and-examples?ts=markdown)
* [What Are the 4 Types of Threat Intelligence?](https://www.paloaltonetworks.com/cyberpedia/threat-intelligence-use-cases-and-examples#types?ts=markdown)
* [Top 4 Use Cases for a Threat Intel Platform (TIP)](https://www.paloaltonetworks.com/cyberpedia/threat-intelligence-use-cases-and-examples#use-cases?ts=markdown)
* [Specific Examples of Threat Intelligence Use Cases](https://www.paloaltonetworks.com/cyberpedia/threat-intelligence-use-cases-and-examples#examples?ts=markdown)
* [MITRE ATT\&CK as a Threat Intelligence Use Case](https://www.paloaltonetworks.com/cyberpedia/threat-intelligence-use-cases-and-examples#mitre?ts=markdown)
* [Threat Intelligence Use Cases FAQs](https://www.paloaltonetworks.com/cyberpedia/threat-intelligence-use-cases-and-examples#faq?ts=markdown)
* [What is the Threat Intelligence Lifecycle?](https://www.paloaltonetworks.com/cyberpedia/what-is-the-threat-intelligence-life-cycle?ts=markdown)
* [Why is the Threat Intelligence Lifecycle Important?](https://www.paloaltonetworks.com/cyberpedia/what-is-the-threat-intelligence-life-cycle#why?ts=markdown)
* [The 6 Stages of the Threat Intelligence Lifecycle](https://www.paloaltonetworks.com/cyberpedia/what-is-the-threat-intelligence-life-cycle#lifecycle?ts=markdown)
* [Benefits of the Threat Intelligence Lifecycle Framework](https://www.paloaltonetworks.com/cyberpedia/what-is-the-threat-intelligence-life-cycle#benefits?ts=markdown)
* [Threat Intelligence Lifecycle FAQs](https://www.paloaltonetworks.com/cyberpedia/what-is-the-threat-intelligence-life-cycle#faqs?ts=markdown)
* What is a Threat Intelligence Platform (TIP)?
* [The Value of a Threat Intelligence Platform](https://www.paloaltonetworks.com/cyberpedia/what-is-a-threat-intelligence-platform#value?ts=markdown)
* [How Threat Intelligence Works](https://www.paloaltonetworks.com/cyberpedia/what-is-a-threat-intelligence-platform#intelligence?ts=markdown)
* [Types and Examples of Threat Intelligence](https://www.paloaltonetworks.com/cyberpedia/what-is-a-threat-intelligence-platform#examples?ts=markdown)
* [Why Do Organizations Need a Threat Intelligence Platform (TIP)?](https://www.paloaltonetworks.com/cyberpedia/what-is-a-threat-intelligence-platform#organizations?ts=markdown)
* [Key Characteristics of a Threat Intelligence Platform](https://www.paloaltonetworks.com/cyberpedia/what-is-a-threat-intelligence-platform#characteristics?ts=markdown)
* [Types of Threat Intelligence Data](https://www.paloaltonetworks.com/cyberpedia/what-is-a-threat-intelligence-platform#threat?ts=markdown)
* [Implementation of a Threat Intelligence Platform](https://www.paloaltonetworks.com/cyberpedia/what-is-a-threat-intelligence-platform#platform?ts=markdown)
* [Threat Intelligence Platforms FAQs](https://www.paloaltonetworks.com/cyberpedia/what-is-a-threat-intelligence-platform#faqs?ts=markdown)
* [What Are Unknown Cyberthreats?](https://www.paloaltonetworks.com/cyberpedia/what-are-unknown-cyberthreats?ts=markdown)
* [How Unknown Cyberthreats Are Redefining Cloud Security](https://www.paloaltonetworks.com/cyberpedia/what-are-unknown-cyberthreats#how?ts=markdown)
* [Why Unknown Threats Matter](https://www.paloaltonetworks.com/cyberpedia/what-are-unknown-cyberthreats#why?ts=markdown)
* [Types of Unknown Cyberthreats](https://www.paloaltonetworks.com/cyberpedia/what-are-unknown-cyberthreats#types?ts=markdown)
* [Advanced Defense Strategies for Modern Threats](https://www.paloaltonetworks.com/cyberpedia/what-are-unknown-cyberthreats#advanced?ts=markdown)
* [Resilient Cloud Security Starts with Visibility and Adaptation](https://www.paloaltonetworks.com/cyberpedia/what-are-unknown-cyberthreats#resilient?ts=markdown)
* [Unknown Cyberthreats FAQs](https://www.paloaltonetworks.com/cyberpedia/what-are-unknown-cyberthreats#faqs?ts=markdown)
* [What Are Cyberthreat Intelligence Tools?](https://www.paloaltonetworks.com/cyberpedia/cyber-threat-intelligence-tools?ts=markdown)
* [Types of Threat Intelligence Tools](https://www.paloaltonetworks.com/cyberpedia/cyber-threat-intelligence-tools#types?ts=markdown)
* [How Threat Intelligence Tools Work](https://www.paloaltonetworks.com/cyberpedia/cyber-threat-intelligence-tools#tools?ts=markdown)
* [Key Functions of Threat Intelligence Tools](https://www.paloaltonetworks.com/cyberpedia/cyber-threat-intelligence-tools#key?ts=markdown)
* [What is a Threat Intelligence Platform (TIP)?](https://www.paloaltonetworks.com/cyberpedia/cyber-threat-intelligence-tools#platform?ts=markdown)
* [Best Practices for Implementing Threat Intelligence Tools](https://www.paloaltonetworks.com/cyberpedia/cyber-threat-intelligence-tools#practices?ts=markdown)
* [Emerging Trends in Threat Intelligence](https://www.paloaltonetworks.com/cyberpedia/cyber-threat-intelligence-tools#trends?ts=markdown)
* [Threat Intelligence Tools FAQs](https://www.paloaltonetworks.com/cyberpedia/cyber-threat-intelligence-tools#faqs?ts=markdown)
* [What are the Types of Cyberthreat Intelligence (CTI)?](https://www.paloaltonetworks.com/cyberpedia/types-of-cyberthreat-intelligence?ts=markdown)
* [What is Cyberthreat Intelligence?](https://www.paloaltonetworks.com/cyberpedia/types-of-cyberthreat-intelligence#cyberthreat?ts=markdown)
* [What is Strategic Threat Intelligence?](https://www.paloaltonetworks.com/cyberpedia/types-of-cyberthreat-intelligence#strategic?ts=markdown)
* [What is Tactical Threat Intelligence?](https://www.paloaltonetworks.com/cyberpedia/types-of-cyberthreat-intelligence#tactical?ts=markdown)
* [What is Operational Threat Intelligence?](https://www.paloaltonetworks.com/cyberpedia/types-of-cyberthreat-intelligence#operational?ts=markdown)
* [Application of Cyberthreat Intelligence](https://www.paloaltonetworks.com/cyberpedia/types-of-cyberthreat-intelligence#application?ts=markdown)
* [Challenges in Cyberthreat Intelligence](https://www.paloaltonetworks.com/cyberpedia/types-of-cyberthreat-intelligence#challenges?ts=markdown)
* [Cyberthreat Intelligence FAQs](https://www.paloaltonetworks.com/cyberpedia/types-of-cyberthreat-intelligence#faqs?ts=markdown)
# What is a Threat Intelligence Platform (TIP)?
4 min. read
Table of Contents
* * [The Value of a Threat Intelligence Platform](https://www.paloaltonetworks.com/cyberpedia/what-is-a-threat-intelligence-platform#value?ts=markdown)
* [How Threat Intelligence Works](https://www.paloaltonetworks.com/cyberpedia/what-is-a-threat-intelligence-platform#intelligence?ts=markdown)
* [Types and Examples of Threat Intelligence](https://www.paloaltonetworks.com/cyberpedia/what-is-a-threat-intelligence-platform#examples?ts=markdown)
* [Why Do Organizations Need a Threat Intelligence Platform (TIP)?](https://www.paloaltonetworks.com/cyberpedia/what-is-a-threat-intelligence-platform#organizations?ts=markdown)
* [Key Characteristics of a Threat Intelligence Platform](https://www.paloaltonetworks.com/cyberpedia/what-is-a-threat-intelligence-platform#characteristics?ts=markdown)
* [Types of Threat Intelligence Data](https://www.paloaltonetworks.com/cyberpedia/what-is-a-threat-intelligence-platform#threat?ts=markdown)
* [Implementation of a Threat Intelligence Platform](https://www.paloaltonetworks.com/cyberpedia/what-is-a-threat-intelligence-platform#platform?ts=markdown)
* [Threat Intelligence Platforms FAQs](https://www.paloaltonetworks.com/cyberpedia/what-is-a-threat-intelligence-platform#faqs?ts=markdown)
1. The Value of a Threat Intelligence Platform
* * [The Value of a Threat Intelligence Platform](https://www.paloaltonetworks.com/cyberpedia/what-is-a-threat-intelligence-platform#value?ts=markdown)
* [How Threat Intelligence Works](https://www.paloaltonetworks.com/cyberpedia/what-is-a-threat-intelligence-platform#intelligence?ts=markdown)
* [Types and Examples of Threat Intelligence](https://www.paloaltonetworks.com/cyberpedia/what-is-a-threat-intelligence-platform#examples?ts=markdown)
* [Why Do Organizations Need a Threat Intelligence Platform (TIP)?](https://www.paloaltonetworks.com/cyberpedia/what-is-a-threat-intelligence-platform#organizations?ts=markdown)
* [Key Characteristics of a Threat Intelligence Platform](https://www.paloaltonetworks.com/cyberpedia/what-is-a-threat-intelligence-platform#characteristics?ts=markdown)
* [Types of Threat Intelligence Data](https://www.paloaltonetworks.com/cyberpedia/what-is-a-threat-intelligence-platform#threat?ts=markdown)
* [Implementation of a Threat Intelligence Platform](https://www.paloaltonetworks.com/cyberpedia/what-is-a-threat-intelligence-platform#platform?ts=markdown)
* [Threat Intelligence Platforms FAQs](https://www.paloaltonetworks.com/cyberpedia/what-is-a-threat-intelligence-platform#faqs?ts=markdown)
A threat intelligence platform (TIP) is an essential tool in modern organizations' cybersecurity arsenal. It provides crucial capabilities for understanding, anticipating, and responding to cyberthreats in a timely and effective manner. TIPs have become essential organizational tools in the ever-evolving cybersecurity landscape.
A TIP provides security teams with information on known malware and other threats, powering efficient and accurate threat identification, investigation and response. It enables threat analysts to spend their time analyzing data and investigating potential security threats rather than collecting and managing data.
Moreover, a TIP allows security and threat intelligence teams to easily share threat intelligence data with other stakeholders and security systems. A TIP can be deployed as a software-as-a-service (SaaS) or an on-premises solution.

## The Value of a Threat Intelligence Platform
Threat intelligence platforms offer immense value by enhancing the capabilities of security operations centers (SOCs). They aggregate threat data from various sources and transform it into actionable insights.
By comparison, a TIP helps security and threat intelligence teams:
* Automate, streamline and simplify the process of researching, collecting, aggregating, and organizing threat intelligence data and normalizing, de-duping, and enriching that data.
* Monitor and quickly detect, validate, and respond to potential security threats in real time.
* Get vital information such as background and details about current and future security risks, threats, attacks, and vulnerabilities, as well as information on threat adversaries and their tactics, techniques, and procedures (TTPs).
* Set up security incident escalation and response processes.
* Share threat intelligence data with other stakeholders via dashboards, alerts, reports, etc.
* Continually feed the most up-to-date threat intelligence data to security systems, such as security information and event management (SIEM) solutions, endpoints, firewalls, application programming interfaces (APIs), intrusion prevention systems (IPSs), and others.
 The lifecycle of threat intelligence platform
## How Threat Intelligence Works
Threat intelligence in cybersecurity is a comprehensive and dynamic method that involves several stages, each crucial to developing an effective defense mechanism against cyberthreats. It starts with gathering data and extends to actionable responses, impacting how security operations centers (SOCs) operate.
### Data Collection
Threat intelligence begins with collecting data from a wide range of sources. These include open-source intelligence (OSINT), such as publicly available information on the Internet, forums, social media, and specialized cybersecurity reports. Internal sources such as server logs, network traffic data, and past incident reports are also crucial.
Subscription-based intelligence feeds provide another layer of data, offering insights from industry experts, research organizations, and government agencies.
### Data Analysis
The collected data is then analyzed to identify patterns (pattern recognition). This involves looking for commonalities in cyberattacks, such as similar methods used by threat actors or recurring system vulnerabilities.
Identifying anomalies is critical in threat intelligence. Anomalies might indicate a deviation from the norm, such as unusual network traffic, which could signify a security breach. Understanding the context of the data is crucial. This involves distinguishing between false positives and genuine threats and understanding the implications of a threat in the organization's specific context.
### Conversion to Actionable Intelligence
The analyzed data is then converted into actionable intelligence. This means distilling the vast data into insights relevant to the organization's security posture. This intelligence aids in strategic planning, helping organizations understand their threat landscape and prepare accordingly.
### Real-time Processing and Response
Real-time processing of threat data enables SOCs to identify emerging threats quickly. The faster a threat is specified, the quicker it is addressed.
### Automated Responses
In many cases, threat intelligence platforms can automate responses to certain types of threats, such as isolating affected systems or updating firewalls to block malicious IPs. The intelligence also informs incident response strategies, guiding how to mitigate and recover from attacks.
### Continuous Improvement
Threat intelligence is not a one-time activity but a continuous process. The insights gained from analyzing threats refine security strategies and improve defense mechanisms.
Threat intelligence is a cyclic and evolving process crucial in the cybersecurity ecosystem. It forms the cornerstone of proactive cyber defense strategies by providing SOCs with the ability to anticipate, identify, and respond to cyberthreats promptly and informally.
## Types and Examples of Threat Intelligence
Threat intelligence is a multifaceted domain comprising various types that cater to different cybersecurity needs. Each type plays a unique role in providing a comprehensive view of the cyberthreat landscape.
### Strategic Intelligence
Strategic intelligence offers a high-level view of the cybersecurity landscape, focusing on long-term trends and insights. This type of intelligence is crucial for decision-makers and policy developers, providing them with a broader understanding of threats, potential risks, and their impact on business or national security. Examples include:
* Global cyberthreat reports detail trends in cybercrime, nation-state activities, and advancements in cyber capabilities.
* Analysis of cybersecurity legislation and policy changes and their implications.
* Long-term risk assessments for industries or organizations.
### Tactical Intelligence
Tactical intelligence delves into threat actors' tactics, techniques, and procedures (TTPs). It's instrumental for security operations center (SOC) teams and incident responders to understand how attackers operate and their strategies. Examples include:
* Detailed analysis of attack patterns and methodologies used in recent cyberattacks.
* Information about specific hacking groups and their preferred methods, such as certain phishing attacks or exploits.
* Best practices and defensive strategies to counter specific TTPs.
### Operational Intelligence
Operational intelligence is concerned with specific, ongoing or imminent threats and attacks. This intelligence is highly actionable and often time-sensitive, designed to assist SOC teams in responding to active threats. Examples include:
* Real-time alerts about ongoing cyberattack campaigns.
* Information about newly discovered vulnerabilities being actively exploited in the wild.
* Incident reports and breakdowns of recent data breaches or security incidents.
### Technical Intelligence
Technical intelligence focuses on the technical details of threats, such as indicators of compromise (IoCs), malware signatures, and IP addresses. IT and security teams use this type of intelligence to set up defenses and respond to specific technical threats. Examples include:
* Hash values of malware files, malicious domain names, or IP addresses associated with threat actors.
* Analysis of malware behavior, its infection vectors, and remediation steps.
* Updates and signatures for antivirus and intrusion prevention systems to detect and block known threats.
### Practical Applications
* Tactical intelligence might include details about a new phishing technique, while technical intelligence would provide IoCs like malicious URLs or email addresses used in the campaign.
* Malware Analysis: Reports on new malware variants, including their behavior, attack vectors, and impact, would fall under technical intelligence, with operational intelligence focusing on current active campaigns using that malware.
* Emerging Hacking Trends: Strategic intelligence helps organizations understand the broader implications of these trends on their long-term security posture. In contrast, tactical intelligence focuses on how these trends could be applied in attacks against them.
These types of threat intelligence collectively empower organizations to understand and respond to cyberthreats on multiple levels. Strategic intelligence helps in long-term planning and policy development, tactical and operational intelligence in day-to-day security operations, and technical intelligence in dealing with specific threats and incidents.
## Why Do Organizations Need a Threat Intelligence Platform (TIP)?
Since threat intelligence data frequently comes from hundreds of sources, manually aggregating this information is time-consuming. This means a technical platform is necessary to handle this task in an automated, intelligent way rather than relying exclusively on human analysts.
In the past, security and threat intelligence teams used multiple tools and processes to manually gather and review threat intelligence data from a variety of sources, identify and respond to potential security threats, and share threat intelligence with other stakeholders (usually through email, spreadsheets or an online portal).
Increasingly, this approach no longer works because:
* Companies collect massive amounts of data in various formats such as STIX/TAXII, JSON, XML, PDF, CSV, email, etc.
* Each year, the number and type of security threats (from malicious actors, malware, phishing, botnets, denial-of-service (DDoS) attacks, ransomware, etc.) continue to increase in scope and sophistication.
* Millions of potential threat indicators are spun up every day.
* Companies must respond to potential security threats much quicker than before to prevent widespread damage.
Security and threat intelligence teams are often inundated with noise and false positives. As a result, it becomes challenging for them to determine which data is the most relevant and valuable to their company. It's also difficult for them to distinguish between real and fake threats.
As a result, they have to spend more time and effort focusing on the threats that pose a genuine risk to their organization.
## Key Characteristics of a Threat Intelligence Platform
Threat intelligence platforms (TIPs) provide a multi-layered approach to understanding and fighting cyberthreats. They analyze and contextualize threat information and integrate it with security operations centers (SOCs) to detect and mitigate cyber risks effectively.
These platforms' automation and response capabilities streamline the process, allowing for a more robust defense against potential cyberattacks.
Key characteristics of TIPs include:
* Data Aggregation and Integration: TIPs gather data from multiple sources, including open-source intelligence, feeds from private vendors, industry reports, incident logs, and more. This aggregation is crucial for developing a broad view of the threat landscape.
* Data Analysis: Beyond mere data collection, TIPs analyze this information to identify patterns, anomalies, and indicators of compromise (IoCs). This analysis turns raw data into actionable intelligence.
* Real-time Monitoring and Alerts: One critical function of a TIP is monitoring for threats in real time, providing timely alerts to potential security incidents, which is crucial for swift incident response.
* Contextualization of Threat Data: TIPs often provide context around the threat data, helping security teams understand the relevance of each piece of intelligence to their specific environment.
* Sharing and Dissemination: Effective TIPs facilitate intelligence sharing across different departments within an organization and, in some cases, with external entities to ensure a coordinated response to threats.
* Integration with security operations center (SOC): TIPs often integrate with an organization's SOC, providing critical inputs for security analysts and aiding in decision-making processes.
* Automation and Response: Advanced TIPs incorporate automation capabilities, enabling quicker responses to identified threats and reducing security teams' manual workload.
## Types of Threat Intelligence Data
The following types of data are integral to their threat intelligence platforms. They ensure that organizations are reactive in dealing with threats as they occur and proactive in anticipating and preparing for potential future threats. This comprehensive approach is crucial for maintaining a robust cybersecurity posture in an ever-evolving digital landscape.
By leveraging these data types, threat intelligence platforms enable organizations to stay ahead in the cybersecurity arms race, ensuring a more secure and resilient digital environment.
* Indicators of Compromise (IoCs):
* Definition: IoCs are data points that suggest a network or system may have been breached. They serve as the red flags or footprints left behind by attackers.
* Examples: Common IoCs include unusual outbound network traffic, anomalies in privileged user account activity, geolocation irregularities, suspicious registry or system file changes, IP addresses, URLs, and malware hashes.
* Use: IoCs are used to detect and investigate breaches quickly. Security teams use them to scan logs and other data sources to identify malicious activity.
* Tactical Data:
* Definition: This type of intelligence focuses on threat actors' specific methods. It details attack vectors, including the tools, techniques, and procedures (TTPs) attackers use.
* Importance: Understanding tactical data helps configure security systems (like firewalls and intrusion detection systems) to defend against specific attack methods.
* Application: Security professionals use tactical data to understand and anticipate attackers' techniques, allowing them to strengthen their defenses against these methods.
* Strategic Intelligence:
* Overview: Strategic intelligence provides a high-level view of the global cybersecurity landscape. It involves analyzing long-term trends, motives, and implications of cyberthreats.
* Content: This can include insights into the geopolitical aspects of cyberthreats, emerging cyberthreat trends, changes in cyber laws, and evolving tactics of cybercriminals.
* Purpose: It aids decision-makers in formulating long-term security strategies and policies. By understanding broader trends, organizations can anticipate and prepare for future threats.
## Implementation of a Threat Intelligence Platform
Implementing a threat intelligence platform is a strategic process involving several key steps, each crucial for ensuring the platform's effectiveness and alignment with an organization's specific security needs.
1. Assessing Specific Intelligence Needs: Identify Objectives: Organizations must first understand their unique threat landscape and security objectives. This involves identifying the threats most relevant to the organization, the assets most at risk, and the potential impact of different threat scenarios. The focus should be on detecting, identifying, and investigating potential security threats, attacks, and malicious threat actors.
2. Choosing the Right Platform: Selecting a threat intelligence platform that complements and integrates seamlessly with the existing security infrastructure is vital. The platform should be capable of aggregating and analyzing data in formats compatible with the organization's existing systems. The platform should be able to handle a variety of data formats and integrate with existing security systems like SIEM, firewalls, and intrusion prevention systems.
3. Training Personnel: It is crucial to train security personnel in the technical aspects of the platform and in interpreting and acting on the intelligence provided. This involves comprehending the context of threats and how to prioritize them. It is important to regularly provide threat-related information to various teams within an organization, suggesting a multi-disciplinary approach to threat intelligence.
4. Integrating the Platform: The threat intelligence platform should be integrated with existing security tools and protocols. This includes setting up workflows for the automated response and ensuring that the platform enhances, rather than complicates, the existing security operations. Best Practices include integrating threat intelligence platforms into broader security operations, including planning, monitoring, feedback, response, and remediation processes. The integration should also support automated enforcement and threat intelligence sharing across teams.
5. Continuous Evaluation and Improvement: The threat landscape is constantly evolving, and so should the approach to threat intelligence. This means regularly evaluating and updating the threat intelligence platform to ensure it remains effective against new and emerging threats. The importance of staying ahead of threat actors through modernizing security systems and automating security processes, which involves continuous learning and adaptation, cannot be overstated.
## Threat Intelligence Platforms FAQs
### What is an Indicator of Compromise (IoC)?
An indicator of compromise (IoC) is evidence that a cyberthreat has potentially compromised your system or network. Examples include unusual outbound network traffic, suspicious IP addresses, URLs, or malware hashes.
### How Can Organizations Implement Threat Intelligence?
To implement threat intelligence, organizations need first to identify their specific security needs, choose a compatible threat intelligence platform, train personnel on interpreting and using the intelligence, and integrate the platform with their existing security infrastructure.
### Can Threat Intelligence Prevent Cyber Attacks?
While threat intelligence cannot entirely prevent cyberattacks, it plays a crucial role in mitigating them. By providing timely and actionable insights, threat intelligence enables organizations to detect potential threats early and respond quickly to minimize damage.
### What is the Difference Between Threat Intelligence and Threat Data?
Threat data is raw data related to threats, such as logs or hacker forum information. Threat intelligence, conversely, is refined and analyzed data that provides context and actionable information derived from threat data.
### How Do Organizations Share Threat Intelligence?
Organizations often share threat intelligence through information-sharing platforms, industry groups, and partnerships. Sharing intelligence helps in understanding and mitigating threats more effectively across different sectors.
Related content
[What is the MITRE ATT\&CK Matrix?
The MITRE ATT\&CK (Adversarial Tactics, Techniques and Common Knowledge) Matrix is a framework for understanding and categorizing the various tactics, techniques and procedures (TTP...](https://www.paloaltonetworks.com/cyberpedia/what-is-mitre-attack-matrix?ts=markdown)
[MITRE Engenuity ATT\&CK Evaluations Dashboard
Explore the evaluations in our interactive dashboard](https://app.powerbi.com/view?r=eyJrIjoiNWRhYzY1YjItOTAxZC00MGM5LThlNzYtOTYxNzViYzM1ZGY2IiwidCI6IjgyOTNjZmRmLThjMjQtNDY1NS1hMzA3LWVhMjFjZDNiMjJmZiIsImMiOjF9)
[Cortex MITRE webpage
Learn how Cortex XDR performed in the MITRE Engenuity ATT\&CK Evaluations](https://www.paloaltonetworks.com/cortex/cortex-xdr/mitre?ts=markdown)
[The Essential Guide to the 2023 MITRE Engenuity ATT\&CK Evaluations
The MITRE ATT\&CK Evaluations offer unbiased and invaluable insights into each participating vendor's performance. The results are a real-world litmus test for how well these soluti...](https://start.paloaltonetworks.com/essential-guide-MITRE-R5)
  [](mailto:?subject=What%20is%20a%20Threat%20Intelligence%20Platform%20%28TIP%29%3F&body=Explore%20the%20essentials%20of%20Threat%20Intelligence%20Platforms%2C%20key%20features%2C%20and%20their%20role%20in%20cybersecurity.%20Learn%20how%20they%20safeguard%20digital%20assets.%20at%20https%3A//www.paloaltonetworks.com/cyberpedia/what-is-a-threat-intelligence-platform)
Back to Top
[Previous](https://www.paloaltonetworks.com/cyberpedia/what-is-the-threat-intelligence-life-cycle?ts=markdown) What is the Threat Intelligence Lifecycle?
[Next](https://www.paloaltonetworks.com/cyberpedia/what-are-unknown-cyberthreats?ts=markdown) What Are Unknown Cyberthreats?
{#footer}
## Products and Services
* [AI-Powered Network Security Platform](https://www.paloaltonetworks.com/network-security?ts=markdown)
* [Secure AI by Design](https://www.paloaltonetworks.com/precision-ai-security/secure-ai-by-design?ts=markdown)
* [Prisma AIRS](https://www.paloaltonetworks.com/prisma/prisma-ai-runtime-security?ts=markdown)
* [AI Access Security](https://www.paloaltonetworks.com/sase/ai-access-security?ts=markdown)
* [Cloud Delivered Security Services](https://www.paloaltonetworks.com/network-security/security-subscriptions?ts=markdown)
* [Advanced Threat Prevention](https://www.paloaltonetworks.com/network-security/advanced-threat-prevention?ts=markdown)
* [Advanced URL Filtering](https://www.paloaltonetworks.com/network-security/advanced-url-filtering?ts=markdown)
* [Advanced WildFire](https://www.paloaltonetworks.com/network-security/advanced-wildfire?ts=markdown)
* [Advanced DNS Security](https://www.paloaltonetworks.com/network-security/advanced-dns-security?ts=markdown)
* [Enterprise Data Loss Prevention](https://www.paloaltonetworks.com/sase/enterprise-data-loss-prevention?ts=markdown)
* [Enterprise IoT Security](https://www.paloaltonetworks.com/network-security/enterprise-device-security?ts=markdown)
* [Medical IoT Security](https://www.paloaltonetworks.com/network-security/medical-device-security?ts=markdown)
* [Industrial OT Security](https://www.paloaltonetworks.com/network-security/medical-device-security?ts=markdown)
* [SaaS Security](https://www.paloaltonetworks.com/sase/saas-security?ts=markdown)
* [Next-Generation Firewalls](https://www.paloaltonetworks.com/network-security/next-generation-firewall?ts=markdown)
* [Hardware Firewalls](https://www.paloaltonetworks.com/network-security/hardware-firewall-innovations?ts=markdown)
* [Software Firewalls](https://www.paloaltonetworks.com/network-security/software-firewalls?ts=markdown)
* [Strata Cloud Manager](https://www.paloaltonetworks.com/network-security/strata-cloud-manager?ts=markdown)
* [SD-WAN for NGFW](https://www.paloaltonetworks.com/network-security/sd-wan-subscription?ts=markdown)
* [PAN-OS](https://www.paloaltonetworks.com/network-security/pan-os?ts=markdown)
* [Panorama](https://www.paloaltonetworks.com/network-security/panorama?ts=markdown)
* [Secure Access Service Edge](https://www.paloaltonetworks.com/sase?ts=markdown)
* [Prisma SASE](https://www.paloaltonetworks.com/sase?ts=markdown)
* [Application Acceleration](https://www.paloaltonetworks.com/sase/app-acceleration?ts=markdown)
* [Autonomous Digital Experience Management](https://www.paloaltonetworks.com/sase/adem?ts=markdown)
* [Enterprise DLP](https://www.paloaltonetworks.com/sase/enterprise-data-loss-prevention?ts=markdown)
* [Prisma Access](https://www.paloaltonetworks.com/sase/access?ts=markdown)
* [Prisma Browser](https://www.paloaltonetworks.com/sase/prisma-browser?ts=markdown)
* [Prisma SD-WAN](https://www.paloaltonetworks.com/sase/sd-wan?ts=markdown)
* [Remote Browser Isolation](https://www.paloaltonetworks.com/sase/remote-browser-isolation?ts=markdown)
* [SaaS Security](https://www.paloaltonetworks.com/sase/saas-security?ts=markdown)
* [AI-Driven Security Operations Platform](https://www.paloaltonetworks.com/cortex?ts=markdown)
* [Cloud Security](https://www.paloaltonetworks.com/cortex/cloud?ts=markdown)
* [Cortex Cloud](https://www.paloaltonetworks.com/cortex/cloud?ts=markdown)
* [Application Security](https://www.paloaltonetworks.com/cortex/cloud/application-security?ts=markdown)
* [Cloud Posture Security](https://www.paloaltonetworks.com/cortex/cloud/cloud-posture-security?ts=markdown)
* [Cloud Runtime Security](https://www.paloaltonetworks.com/cortex/cloud/runtime-security?ts=markdown)
* [Prisma Cloud](https://www.paloaltonetworks.com/prisma/cloud?ts=markdown)
* [AI-Driven SOC](https://www.paloaltonetworks.com/cortex?ts=markdown)
* [Cortex XSIAM](https://www.paloaltonetworks.com/cortex/cortex-xsiam?ts=markdown)
* [Cortex XDR](https://www.paloaltonetworks.com/cortex/cortex-xdr?ts=markdown)
* [Cortex XSOAR](https://www.paloaltonetworks.com/cortex/cortex-xsoar?ts=markdown)
* [Cortex Xpanse](https://www.paloaltonetworks.com/cortex/cortex-xpanse?ts=markdown)
* [Unit 42 Managed Detection \& Response](https://www.paloaltonetworks.com/cortex/managed-detection-and-response?ts=markdown)
* [Managed XSIAM](https://www.paloaltonetworks.com/cortex/managed-xsiam?ts=markdown)
* [Threat Intel and Incident Response Services](https://www.paloaltonetworks.com/unit42?ts=markdown)
* [Proactive Assessments](https://www.paloaltonetworks.com/unit42/assess?ts=markdown)
* [Incident Response](https://www.paloaltonetworks.com/unit42/respond?ts=markdown)
* [Transform Your Security Strategy](https://www.paloaltonetworks.com/unit42/transform?ts=markdown)
* [Discover Threat Intelligence](https://www.paloaltonetworks.com/unit42/threat-intelligence-partners?ts=markdown)
## Company
* [About Us](https://www.paloaltonetworks.com/about-us?ts=markdown)
* [Careers](https://jobs.paloaltonetworks.com/en/)
* [Contact Us](https://www.paloaltonetworks.com/company/contact-sales?ts=markdown)
* [Corporate Responsibility](https://www.paloaltonetworks.com/about-us/corporate-responsibility?ts=markdown)
* [Customers](https://www.paloaltonetworks.com/customers?ts=markdown)
* [Investor Relations](https://investors.paloaltonetworks.com/)
* [Location](https://www.paloaltonetworks.com/about-us/locations?ts=markdown)
* [Newsroom](https://www.paloaltonetworks.com/company/newsroom?ts=markdown)
## Popular Links
* [Blog](https://www.paloaltonetworks.com/blog/?ts=markdown)
* [Communities](https://www.paloaltonetworks.com/communities?ts=markdown)
* [Content Library](https://www.paloaltonetworks.com/resources?ts=markdown)
* [Cyberpedia](https://www.paloaltonetworks.com/cyberpedia?ts=markdown)
* [Event Center](https://events.paloaltonetworks.com/)
* [Manage Email Preferences](https://start.paloaltonetworks.com/preference-center)
* [Products A-Z](https://www.paloaltonetworks.com/products/products-a-z?ts=markdown)
* [Product Certifications](https://www.paloaltonetworks.com/legal-notices/trust-center/compliance?ts=markdown)
* [Report a Vulnerability](https://www.paloaltonetworks.com/security-disclosure?ts=markdown)
* [Sitemap](https://www.paloaltonetworks.com/sitemap?ts=markdown)
* [Tech Docs](https://docs.paloaltonetworks.com/)
* [Unit 42](https://unit42.paloaltonetworks.com/)
* [Do Not Sell or Share My Personal Information](https://panwedd.exterro.net/portal/dsar.htm?target=panwedd)

* [Privacy](https://www.paloaltonetworks.com/legal-notices/privacy?ts=markdown)
* [Trust Center](https://www.paloaltonetworks.com/legal-notices/trust-center?ts=markdown)
* [Terms of Use](https://www.paloaltonetworks.com/legal-notices/terms-of-use?ts=markdown)
* [Documents](https://www.paloaltonetworks.com/legal?ts=markdown)
Copyright © 2025 Palo Alto Networks. All Rights Reserved
* [](https://www.youtube.com/user/paloaltonetworks)
* [](https://www.paloaltonetworks.com/podcasts/threat-vector?ts=markdown)
* [](https://www.facebook.com/PaloAltoNetworks/)
* [](https://www.linkedin.com/company/palo-alto-networks)
* [](https://twitter.com/PaloAltoNtwks)
* EN
Select your language