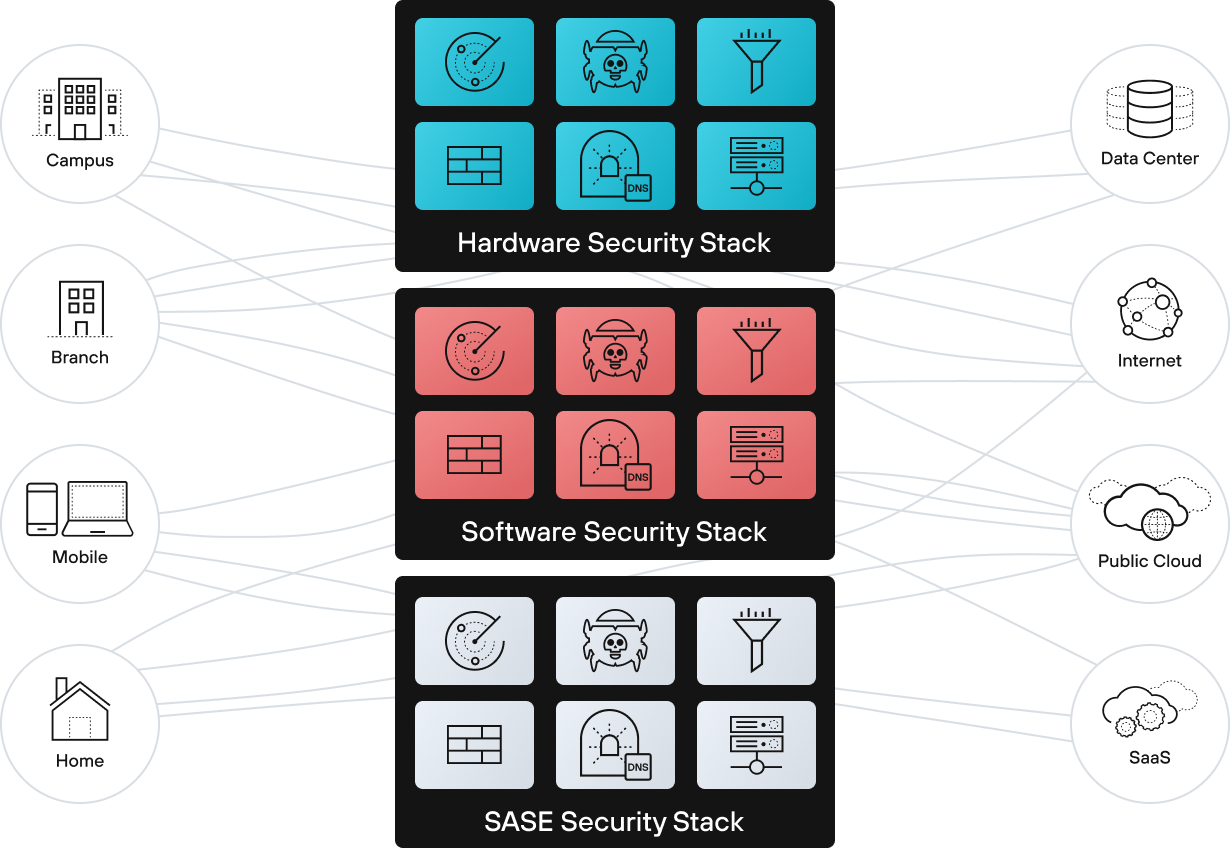
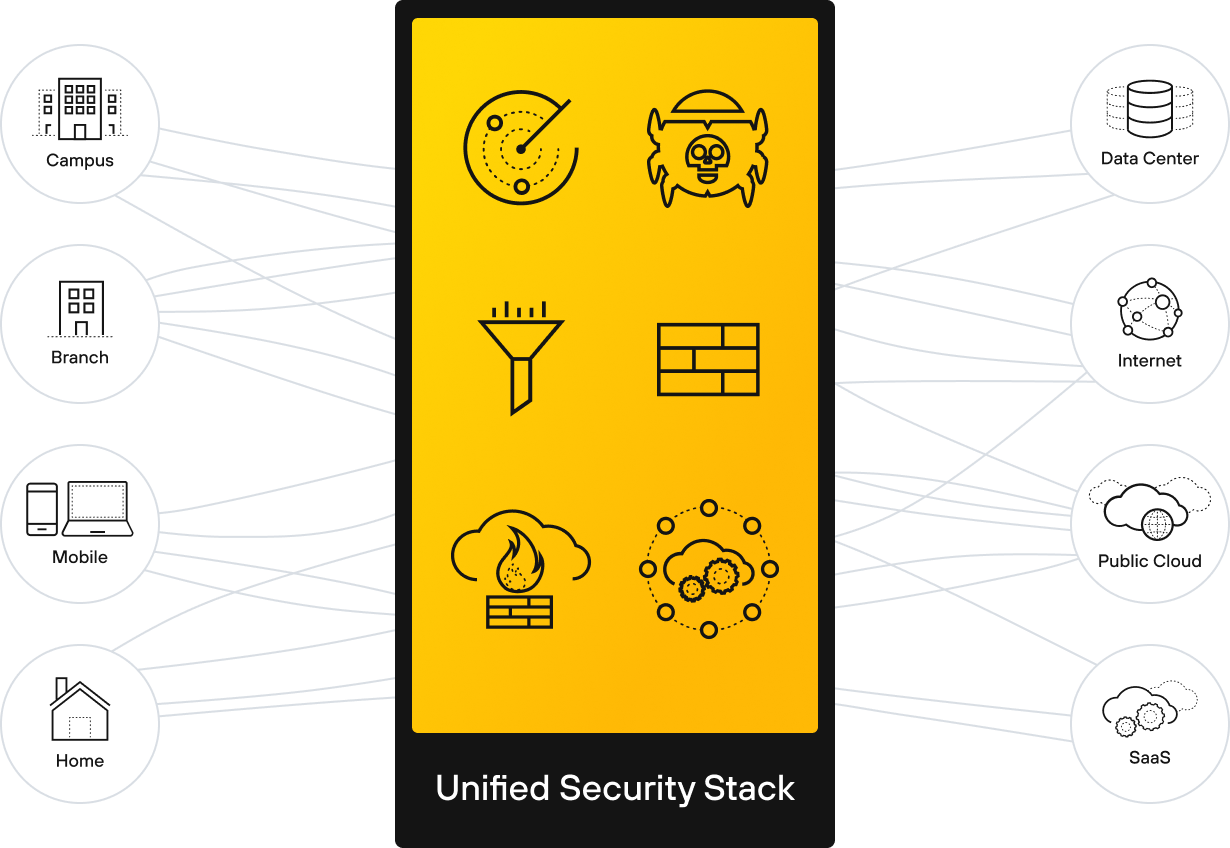
Secure whatever, whenever, wherever.
Palo Alto Networks securely enables digital transformation with a Zero Trust, AI-driven approach to network security that detects and prevents sophisticated attacks and automates manual security operations - all while delivering simplicity and agility.



About our platform in the IDC report.
INDUSTRY RECOGNITION
See what industry analysts and experts have to say.
Forrester Zero Trust Platforms Report Reveals Palo Alto Networks a Zero Trust Platform Leader
Palo Alto Networks the Only Vendor to Be Recognized as a Leader in SD-WAN, SSE and Single-Vendor SASE
Palo Alto Networks has been named a Leader in The Forrester Wave™: Enterprise Firewalls
Palo Alto Networks the Only Vendor to Be Recognized as a Leader in Both SSE and SD-WAN
Discover why Palo Alto Networks is a NESaaS Leader
Palo Alto Networks Named a Leader in the Gartner® Magic Quadrant™ for Network Firewalls for 11th Straight Year
Forrester Consulting study shows 163% ROI for Palo Alto Networks Software Firewalls