A few weeks ago I was fortunate enough to attend REcon in Montreal, Canada. This conference focuses on reverse engineering and exploitation techniques and has been going on for roughly a decade. In this post, I’ll recap some of the presentations witnessed during the conference and provide a general overview of the conference itself.
Despite its long run, REcon is still fairly unknown in the broader information security community. It’s a three day, single track conference covering topics ranging from exploitation, software reverse engineering, malware analysis, and hardware reverse engineering, to name a few.
The conference is generally limited to a few hundred attendees, which produces a very relaxed atmosphere. No jostling to try and get into a talk that you waited 45 minutes in line to see, and no need to compromise between attending talk ‘A’, talk ‘B’, or talk ‘C’, which all happen to be taking place at the same time in different tracks. The talks themselves often verge on the more technical side, with really interesting work being discussed and presented.
Figure 1. REcon Logo
Because of the smaller crowd and intimate atmosphere at REcon, I’ve yet to attend this conference without meeting at least a dozen new and interesting people. This year was no different. People are generally very friendly and it’s not surprising to find yourself chatting with folks at the hotel bar or joining a group of people you just met for dinner over in Chinatown.
During the three days of talks at REcon, a number of great talks were presented. Here are some of the REcon talks I found most interesting:
Totally Spies
Joan Calvet, Marion Marschalek, Paul Rascagnères
As the first official talk of REcon, this presentation did not disappoint. Joan, Marion, and Paul delivered a wonderful talk revolving around their research into the ‘AnimalFarm’ malware group. Those familiar with my background know that a talk such as this is something right up my alley. The malware group itself is comprised of a number of different individual malware families, such as Babar, NBOT, Bunny, Casper, and Dino. Additionally, AnimalFarm spans a number of years (2009-2014). The presentation was broken up into discussion of individual malware families, and the presenters did a great job discussing some of the more technical curiosities present in each. They also did a wonderful job of pointing out the similarities across all of the discussed samples, which allowed them to group these families together. Overall, this presentation provided an overview of this lesser known group of malware and shed light on various indicators and characteristics present in each malware family.
Radare2, building a new IDA
Jeffrey Crowell, Julien Voisin
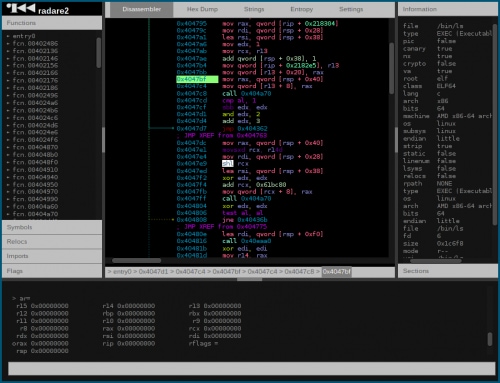
This presentation was only given a 30 minutes slot. This was somewhat disappointing as I would have loved to see Jeffrey and Julien talk more about Radare2, a fascinating tool. Radare2 is an open-source project that provides a portable reverse engineering framework. As the title of the presentation implies, the main developers aim to provide an alternative, free framework that reverse engineers can use in their daily work. I did not previously play with Radare2; I had only heard about it in passing from some of my friends and colleagues, but I never took the plunge. After seeing this presentation, I’d highly encourage readers to check out the project. Not only does Radare2 work on a number of platforms (Windows, Linux, OSX, Android, BSD, etc.), but it also supports a wide range of file types (MZ, ELF, Mach-O, Java, firmware, etc.). Radare2 has tons of functionality and I could certainly see it being a great tool to add to any reverse engineer’s tool bag.
Figure 2. Radare2 WebUI
That being said, there are a couple of limitations: namely, the lack of a proper GUI and a steep learning curve. In typical REcon form, this presentation was great to watch and Jeffrey and Julien did a great job of getting people excited about Radare2
0x3E9 Ways to DIE
Yaniv Balmas
This talk focused on a new IDA plugin written by Yaniv Balmas. The plugin, named ‘DIE’ or Dynamic IDA Enrichment, aims to enrich a reverse engineer’s IDA experience by supplementing static analysis with data generated dynamically during runtime.

Figure 3. DIE Logo
Specifically, Yaniv’s plugin looks at function arguments and return variables and performs analysis to infer their variable types. This data is stored in a separate database where it can be queried at the analyst’s discretion. A number of great live demonstrations were performed on stage, and this plugin looks like it could be very useful when performing analysis on a file in IDA Pro. For those interested, the plugin can be found here. Additionally, I should point out that Yaniv used a Hitchhiker’s Guide to the Galazy theme, so perhaps I’m a bit partial towards this presentation, being member of the Unit 42 threat intelligence team.
The M/o/Vfuscator
Christopher Domas
This would probably win the award for “scariest session”, if only because Christopher performed some extraordinary background work for this presentation. It’s clear that Christopher is a smart person, and when he discovered that the x86 ‘mov’ instruction was ‘Turing Complete’, he decided to work towards writing an obfuscator. Any x86 instruction can be replaced using a series of ‘mov’ instructions. Christopher replicated control flow and operations including branching, assembly math, and comparisons using nothing but ‘mov’ instructions. I say this is the scariest presentation because I imagined seeing a malware sample in the wild using this obfuscation technique. To say reversing such a sample would be a challenge would be possibly the biggest understatement of the century. The following image demonstrates both what a non-obfuscated sample looks like (first two images), as well as what it looks like after obfuscation (third image).
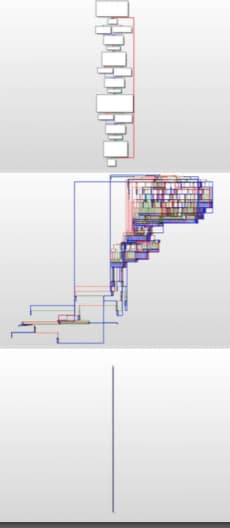
Figure 4. M/o/Vfuscator in Action (Credit: Twitter)
For those interested in some proof of concept code written by Christopher, his GitHub project can be found here. The presentation was wonderfully given, as Christopher went through the process of demonstrating the above technique. The groans of dismay from the audience during his live demos were bittersweet, as we both sat in awe over what we’d seen and dreaded seeing it outside of the safety of the REcon presentation.
Conclusion
There are a number of amazing presentations given at REcon. So many so that we weren’t able to cover everything. As an attendee, there is ample opportunity to learn more about some of the latest malware threats, as seen in the Totally Spies!. It allows us to not only become more familiar with the latest threats, but also helps us identify variations of them going forward.
If malware is not your primary area of interest, perhaps learning about some brand new or lesser-known tools may be of some use. As we saw in the Radare2 and 0x3E9 Ways to DIE, there’s a number of amazing tools being released and discussed during this conference. These tools not only aid a reverse engineer in performing his or her job, but also do so quickly and efficiently.
Finally, we saw some truly innovative research being discussed in M/o/Vfuscator, as the presenter provided a radically new way of obfuscating code. This will likely have an impact on both the malware community as well as those dealing with software protections. As such, the earlier we can become familiar with the techniques discussed, the better prepared we will be in the event it surfaces in the wild.
I can’t say enough good things about REcon. I have only been to the conference a couple of times, but each has been a positive experience. I truly believe that the people really make this conference, and I often find myself astonished at a room full of such amazingly intelligence people gathered together. If you’re interested in exploitation, reverse engineering, or just have that a natural curiosity, I’d highly encourage you to check out this conference next year.