On the 15th of December, after much debate, what was first proposed back in 2012 will finally be established: the European Union has come to agreement on the General Data Protection Regulation (GDPR), which updates and replaces Europe’s Data Protection Directive – rules that were first defined in 1995 (directive 95/46/EC).
As business and cybersecurity leaders, what’s critical is the way in which we choose to interpret and respond to these changes that are now defined.
Why reform the Data Protection laws?
Since 1998, when the Data Protection Directive was originally implemented, the scale and scope of information stored online has significantly changed, so it makes sense to review the requirements to protect citizens’ privacy when online.
It is also a chance to make the regulation more manageable for businesses to follow; for example, it aims to reduce the audit burden and simplify application by harmonization across member countries. Previously each country had interpreted the directive in its own way, creating 28 flavors of the rules.
The new GDPR has garnered significant attention as it has been negotiated. One provision that has created much debate is the planned requirement for companies holding EU citizens’ data to have to notify their national regulator of any significant breach of personal data “without undue delay and, where feasible, not later than 72 hours after having become aware of it”.
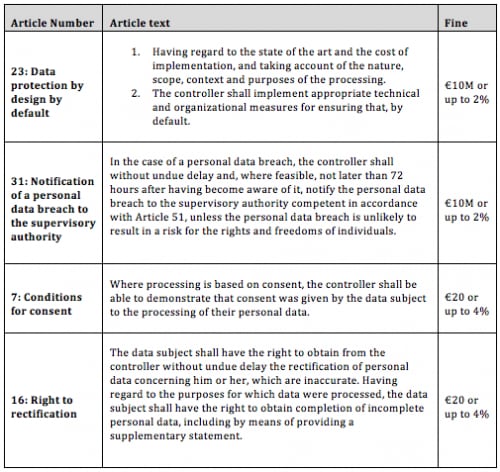
Seen through numerous research reports, it often takes months to identify and respond to breaches today. The introduction of common GDPR penalties (capped at €10M–20M or 2%–4% of total worldwide annual turnover dependent on the type and level of infringement related to breaches, such as failure to notify) has made this a focal point as, commonly, the penalties and breach notification make headlines. For many the fear of brand impact and potential fines grabs the attention of most businesses. However the scope of fines is broader, as shown in the examples in the table, below (please note: this is not exhaustive or complete list):
Specifically in regard to breach notification, these penalties are not aimed to kick a business when it’s down, rather encourage businesses to notify in the defined time scales and ensure they have the appropriate “regard for the state of the art” controls in place to prevent such incidents from occurring.
The GDPR states that companies must implement appropriate technical and organizational measures with regard to the “state of the art”, that can ensure a level of security appropriate to risk. Fines aligned to articles in the revision, I would suggest, aim to be the motivator for businesses to raise the bar on good cybersecurity application. As citizens we expect businesses to comply to keep our data safe.
Your core decision?
It would be easy to review the above and consider your focus must now be on incident response; that typically means either building or growing the staff and capabilities you have in order to both discover and do the forensic analysis on a cyber incident.
The challenge here is threefold: firstly it does not address the cause of the breach problem; secondly it’s dependent on a skilled staff, which is a limited resource; thirdly it’s costly both in terms of the money and people required if you keep needing to respond.
As mentioned the regulation reform highlights the need for “regard for the state of the art”; my encouragement would be that this is where you should focus. If you have better protection so preventing incidents, you take away the heavy response requirements.
So why are we seeing more and more breaches in recent times?
Cybersecurity today is as complex as the IT that it’s protecting, with multiple components that must function together to identify and block the attacker. The challenge is that it’s based on legacy underpinnings.
Consider the city of London, which is believed to have been founded in 43 A.D. The transport infrastructure put in by the Romans soon after, which is still the foundation of much of the city’s key roads, simply struggle to stand up to today’s demands. If London traffic is typically a jam, consider some modern cities that have far more effective systems build leveraging modern state-of-the-art concepts, such as driverless cars, alternative transport, and traffic management systems to mention but a few.
In much the same way, we have put in security products based on their own capabilities; yet, today we have so many, the demands they each add independently stretch IT teams; then add the multiplier effect of getting them to work together. Quite literally we leverage some great technologies, but the underlying infrastructure is lacking and manual, so we are slow to find today’s complex attacks that require gathering data from across multiple solutions. The key point here is that “state of the art” means leveraging both the technical capabilities available today and the processes that allow people to function efficiently. The overall capabilities cannot be constrained by legacy components.
Considerations as you start to plan to comply with the GDPR
Obviously there are some key aspects, such as ensuring you understand the details and the timelines of the regulation, and its adoption, as they are published. But as you start to consider your strategy around achieving state of the art, or at least regard for it, ask yourself the following questions:
- Is your cyber strategy and underlying infrastructure as old as the Data Protection Directive?
Cyber and the security available to enable it evolve at a tremendous pace. When did you last step back and consider just what is possible in terms of good, state-of-the-art cybersecurity best practices? Then define the transformation plan to move your business to this. For most the legacy challenge is the shackles that holds us back. If you were to build a cybersecurity strategy from scratch today, I suspect there would be some significant changes from what you have in place currently.
- How do you measure “state-of-the-art cybersecurity”?
Today the most common measure I see used is: did we find it, which, given enough tools and resources we can always achieve; however most don’t have unlimited access to either. Considering that the volume of threats seems only likely to increase, so will the scale of information we need to protect; we need to become increasingly efficient. As such we need a measure that looks at efficiency, which for me would be: How long does it take to detect? This is a measure we can monitor reactively but also proactively test. I would challenge that, when you fall below what you consider your acceptable timeframe, your security is no longer state- of-the-art, and you should be reviewing what and how you adapt/evolve to return to your defined measure.
- What is the acceptable workload for any security solution (operational efficacy and efficiency)?
To work at digital speed, you need solutions that are operationally efficient. You must consider what is an acceptable level of human interaction for any solution. Typically the lower the efficacy and/or the greater the human interaction the more you move from an automated to a manual solution. Today’s threats typically require correlation across multiple solutions to accurately detect; so, when considering the workload, you must also consider both the individual overhead and additional overhead needed to aggregate/correlate into a single platform.
All of these should start to identify just what the gap is today in your organization, allowing you to define the transformation plan to meet the requirements set out in the regulation reform.
Summary
Over the coming months, there will be a huge amount of discussion around the reform of data protection in the EU. The GDPR enters into force once published in the Official Journal of the European Union – a step that still needs to occur and will apply two years from that date. Thus, it is likely to be fully in effect in early 2018. Until now most held back from action, as the scope was not finalized.
Now you have a clear understanding of the expectations as you move from awareness to action.
In one respect this allows you to gain additional support from the business, as the new regulation is a very clear business mandate and driver; yet how we turn this into action, I would suggest, is open to interpretation. You can focus in on the notification requirement; or you can focus in on the underlying principle behind the reform, which was to raise the bar on cybersecurity, pulling capabilities closer to the state of the art that would better protect citizens’ data and prevent breaches from occurring. Nirvana would be that we never have to notify; the more we can move to an automated state-of-the-art approach that scales to current and future IT requirements, the closer we will get.