This post is also available in: 日本語 (Japanese)
By Matthew Chiodi, Chief Security Officer, Public Cloud
It’s time for organizations to face the challenges of cloud security with the mindset of a U.S. Navy SEAL special operations force. The majority of cloud breaches are the result of misconfigurations, not due to elite hackers identifying sophisticated ways of evading carefully constructed protections. Applying a disciplined and proactive military-style approach can help identify and eliminate such gaping security holes, stopping attacks before they happen.
Former U.S. Navy SEAL officers Jocko Willink and Leif Babin describe a principle they call Default: Aggressive, a “confident, independent and proactive default approach to real-time challenges.” Unit 42, the Palo Alto Networks global threat intelligence team, recently reported that 65% of publicly disclosed cloud security incidents are the result of misconfigurations. Here’s how organizations can address these issues by taking a Default: Aggressive stance with their cloud configurations.
Plan Like a SEAL and Expect the Worst
Earlier this year we released our Big Cloud 5 security framework, which includes five practical steps for getting cloud security right. The second step in the process is to automatically prevent the most serious cloud misconfigurations. Just as guardrails along a highway prevent vehicles from running off the road into dangerous territory, proactive security measures can discourage users from straying into misconfigurations that expose an organization to unnecessary risk. This step is significant because it encourages security teams to transform their thought processes from defensive to proactive.
Organizations can avoid opening themselves up to cloud security incidents by automatically identifying “anti-patterns” – negative, preventable situations – and then remediating them automatically as well. Through the Default: Aggressive approach to cloud security, organizations can protect themselves responsibly, and dramatically decrease the share of cloud security incidents that can be attributed to misconfigurations. But what does this actually look like in practice?
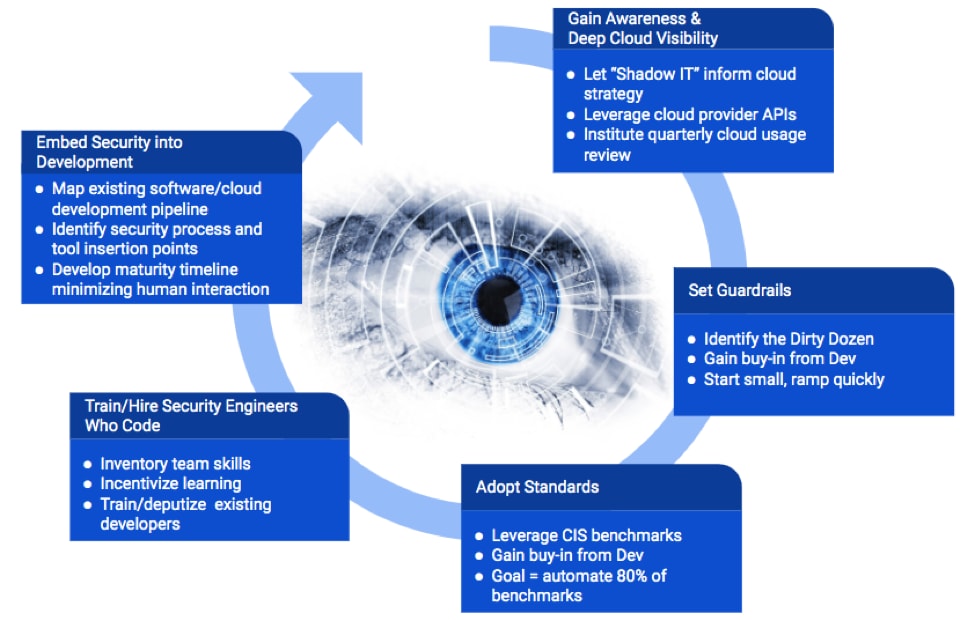
Proactive = Doing the Small Things Right
One way to accomplish Default: Aggressive cloud security is through infrastructure as code (IaC), automating the process of managing an application’s underlying tech stack rather than approaching the same task through often error-prone, manual configuration. If your organization is using cloud, IaC is a must. IaC may be trending as a buzzword, but that’s for good reason. It offers powerful security and quality benefits.
First, it forces organizations to document, in code, what a cloud environment will look like and minimizes how many human hands are manually clicking around creating new systems and networks. Second, it allows cloud configurations to be scanned for security issues prior to deployment. While an organizational move to IaC can’t be achieved overnight, its benefits far outweigh the risks of manually operating cloud environments.
The Default: Aggressive mindset means not waiting for threats before taking action. Organizations can make the decision to move away from reactive production security scanning to building security quality into the entire software development lifecycle. In his 1986 book, “Out of the Crisis,” W. Edwards Deming, the godfather of total quality management, wrote, “Cease dependence on inspection to achieve quality. Eliminate the need for massive inspection by building quality into the product in the first place.” This attitude embodies the core of Default: Aggressive security. By moving security to the earliest possible point in the development process, an organization also fulfills another modern principle: shift-left security.
Default: Aggressive cloud security also calls for strenuously enforcing automated software quality guardrails. Practically speaking, this means starting with a minimum viable product (MVP) shortlist of misconfigurations to eliminate. Examples include configurations such as firewall rules that allow traffic from the entire internet (0.0.0.0/0) on FTP, MongoDB, MySQL, Oracle, Postgres, RDP and SSH ports. Also include in your initial list things like databases not being encrypted, storage buckets being open to the public, or identity and access management policies that allow assuming role permissions across all services. Configurations like this should likely never exist in your cloud environments.
Default: Aggressive Security Wins
Navy SEALs methodically plan out missions, attempting to account for as many variables as possible. How we approach cloud security should be no different. Default: Aggressive security allows us to automate away problems that trip up many cloud consumers. A great place to start implementing the mindset is Unit 42’s recent cloud risk report. Use this research to help form the basis of anti-patterns to proactively defend against. Doing so will put you ahead of the vast majority of your peers, demonstrably reduce your organization's share of cloud incidents, and place you in an elite category – just like a SEAL.