Since 2006, when AWS launched its Elastic Compute Cloud (EC2), the term “cloud” has rapidly become part of the business lexicon. Yet despite 13 years elapsing, companies continue to struggle when it comes to security and compliance in public cloud platforms including Azure, Google, AWS and Alibaba. Why do cloud security and compliance seem so hard? Exploring that question will show why organizations need to build holistic cloud security programs.
Innovation Fosters Complexity
If there is one thing that the cloud providers have done extremely well, it is innovate. Unfortunately, the torrent of features they’ve produced, often released on a near-daily basis, has led to exponentially more complexity. Complexity, it has been often stated, is the enemy of security.
Consider that, in one quarter alone, AWS released 497 new services and features. The exact number isn’t important, but rather that, with each new feature, complexity grows, as does the potential attack surface. This rapid pace of innovation fosters complexity in the cloud more so than on-prem. Consider the feature release cycle in a typical on-prem data center vs. Google, Azure and AWS. New capabilities such as Cloud Text-to-Speech, ML inference chips, or Stream Analytics for internet of things (IoT) devices are not typically being released regularly, if at all.
Developers and businesses alike will always want to use the latest and greatest, and they should. While many organizations have yet to harness the full power of public cloud, with each added feature, their security teams’ perceived ability to secure infrastructure as a service (IaaS) and platform as a service (PaaS) clouds shrinks. This is just one reason cloud security and compliance seem out of reach for many organizations.
Fluidity in the Shared Responsibility Model
The cloud providers have gone to great lengths to educate consumers on the delicate line between what they own and secure vs. the consumer. There are a million-plus different visualizations of the shared responsibility model, but Figure 1 below makes things very clear.
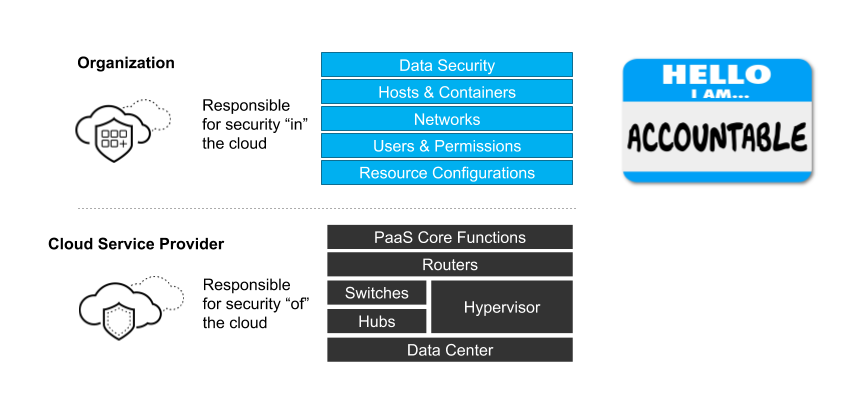
While most security teams I speak with understand this model conceptually, they struggle with it in practice. As an illustration, according to Unit 42, 32% of organizations are still publicly exposing at least one cloud storage service in a way they likely did not intend. While this number is down considerably from an earlier report (58% in May of 2018), it clearly demonstrates that, despite strenuous efforts on the part of cloud providers, there is still much work to be done.
Compliance Mandates Continually Evolving
GDPR went into effect May of 2018. It was followed by the California Consumer Privacy Act (CCPA), which went into full force on January 1, 2020. These mandates are perhaps the most impactful in recent years, but there are literally dozens of others that likely apply for global companies. When combined with the rapid pace of innovation in public cloud environments and the transient nature of cloud systems, organizations are left with a constantly moving target. I have seen many organizations attempt to track cloud compliance with spreadsheets. Despite the best of intentions, this is a losing battle, as cloud environments commonly undergo hundreds of changes per day. Unit 42 cloud research identified that 32% of organizations fail GDPR requirements. While the numbers may seem bleak, you don’t have to be part of the negative statistics if you have a solid cloud security strategy in place.
Strategy Before Tactics
Far too many security teams fall into the trap of adopting a myriad of security point products with the hope they will solve their cloud security and compliance challenges. Certainly, tools are part of the solution. However, before adding yet another tool to the already overcrowded security arsenal, security teams need to first determine if they have a cloud security strategy in place.
In order to tackle these challenges, you’ll need to implement The Big Cloud 5: a 5-step framework for cloud security success realization. When implemented and resourced appropriately, it will help organizations of all sizes form the bedrock of a holistic cloud security and compliance program.