State and local government agencies have technical infrastructure that spans from regular business networks, to service provider offerings, to public safety and other critical services. It’s no secret that applying security frameworks to this existing infrastructure can be difficult. We rarely have the opportunity to build out organization-wide greenfield security deployments for the systems we support and often have to support existing legacy solutions. When greenfield projects do come along, we tend to focus on applying our security frameworks with controls that are unique to that deployment. This results in a story that we are all familiar with – nonintegrated, siloed security solutions with various maturity levels. Granted, there are tools out there that can help security operations teams tie these various siloes together; however, integrations can be limited. The tools themselves might rely on legacy approaches, and by the time information is correlated and analyzed, threat actors have already taken actions on their objectives. What should state and local governments do to remedy this? Defining a clear security strategy and establishing a consistent security policy is a must.
Your Cybersecurity Strategy
If asked to paint a picture of an organization’s optimal security solution, the first question would be, “Which wall do you want the picture on?” This is akin to setting the direction and vision for your cybersecurity strategy. Whether you choose to align yourself with NIST, CIS, ISO or any of the other frameworks, this direction will dictate what the “picture” looks like. Frameworks help provide guidance as a means to an end, and the structure for implementing security controls in the environment. Furthermore, it’s important to consider compliance requirements within your frameworks. CJIS, IRS, HIPAA and other compliance needs may take the whole-wall mural down to multiple framed portraits.
Setting this vision and direction seems like a simple ask, and for anyone that’s been in the space for a while, it may seem trivial. However, with the cybersecurity landscape changing daily, regular review of security visions and frameworks is crucial to a mature security posture. A focused and consistent approach also has the benefits of allowing for easier auditing, simpler documentation and more thorough implementation.
Structured Segmentation
Applying a security framework to an organization comes with the reality that one team is not likely to do everything involved. Design and implementation are usually separate from policies and procedures. Operationalizing daily maintenance (getting a packet from point A to point B) is usually done by a separate team than the one verifying that the packet is legitimate and aligns to policy (separation of network, security, cloud, DevOps, etc.). This is something we work through in other parts of our IT business.
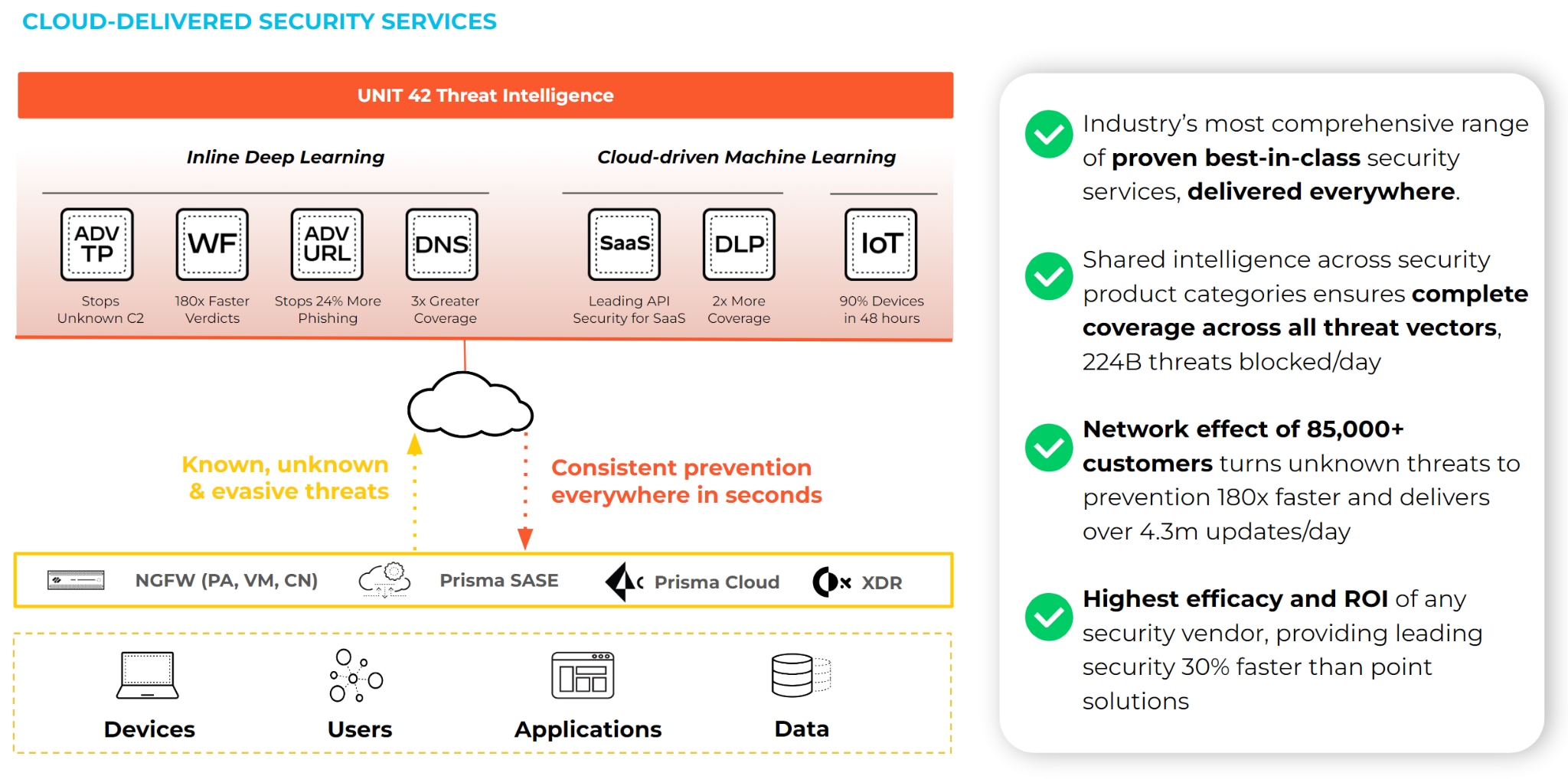
Collaboration, identity, networking, operating systems and other key aspects of running the IT business are usually standardized but enhanced with key native integrations. This should be our approach to cybersecurity, as well. The previously segmented security market now has options for standardizing and providing consistent security across cloud, endpoint, network and operations. Organizations that have taken this approach are seeing serious improvements, as well. In working with state and local government and education customers, we’ve found many improvements:
- A consistent, standardized approach to security is up to 50% more efficient than a siloed, multivendor approach.
- Because of this efficiency, they are also seeing a 45% decrease in the likelihood of a breach supported by an up to 80% reduction in alerts. Automation and native integrations allow for a more effective and mature security posture.
- Application and adhesion to security frameworks are simpler with management through fewer tools. Consistency across applications, operating systems and deployment locations (cloud versus on-premises) allows for easier auditing.
- Consistency allows for automation and native integrations to enable a 24x7x365 security operations center (SOC) with the support of a 9–5, Monday-to-Friday workforce.
What Does Consistency Look Like?
The ability to apply a consistent security policy for on-premises, work-from-home, cloud native and SASE-enabled workloads (or any other workload where data is moving from one point to another) is something that few companies can offer. Additionally, the ability to take the intelligence gathered from moving data and apply it to the integrity of the workloads housing that data (on-premises or in the cloud) takes consistency another step further. Correlate that business, threat and IT intelligence together into a security operations platform, and you now have a consistent approach to pushing packets and maintaining workload integrity, securing data within your organization.
Building upon industry-leading security technologies in conjunction with strong technology partnerships, Palo Alto Networks can help you consolidate your approach to security while maintaining crucial IT business continuity. For more information, visit our state and local government website, or contact your Palo Alto Networks representative.