The Prisma Cloud Intelligence Stream is a real-time feed that contains vulnerability data and threat intelligence from our Unit 42 threat research team, commercial providers and the open source community. It is continuously updated as new threats emerge, helping to ensure that your environment is automatically monitored for the latest risks. The latest updates to Prisma Cloud help improve how teams implement this threat intelligence in isolated environments.
Updating Vulnerability and Threat Intelligence Data
The Prisma Cloud team continuously researches and then compiles vulnerability and threat updates into the Intelligence Stream. This data is updated several times per day and is posted at intelligence.twistlock.com. The Prisma Cloud Compute Console, with internet connectivity, will automatically establish an authenticated, TLS-secured connection and continuously listen for new intelligence updates. When an update is posted, the Console downloads and ingests the update, then immediately begins monitoring your environment for the new threats and vulnerabilities, in addition to existing ones.
Prisma Cloud Enterprise Edition
With Prisma Cloud Enterprise Edition, the Console is delivered via software-as-a-service (SaaS), meaning we manage it for the end-user. Thus, Intelligence Stream data is fed into Prisma Cloud without any user configuration requirements.
Prisma Cloud Compute Edition
With Prisma Cloud Compute Edition, users manage the Console themselves. With internet access, the Intelligence Stream will be updated at regular intervals, just like Enterprise Edition.
But, not every deployment of Prisma Cloud Compute Edition has the luxury of internet access. In fact, many customers choose to operate Compute Edition in highly regulated or air-gapped environments. Prisma Cloud has always supported our customers' ability to manually download updates from the Intelligence Stream, “sneakernet” the tar.gz file to the isolated environment and then manually update the isolated Console’s Intelligence Stream data.
The latest release of Compute Edition, v20_12_531, has improved Intelligence Stream features to support automated deployment of updates to threat intelligence in isolated environments. These enhancements allow isolated environments to scale as if they were internet connected, but can help improve automated distribution of threat intelligence within any environment.
Flexible Options for Updating Threat Intelligence in Isolated Environments
Prisma Cloud ships with a command-line configuration and control tool called twistcli, which supports Linux, macOS, and Windows. The twistcli tool is used to authenticate a connection to intelligence.twistlock.com, in order to download the latest Intelligence Stream updates.
There are several options for implementing Intelligence Stream updates within isolated environments:
- Basic: Use twistcli to manually download the Intelligence Stream update and manually upload into the isolated Consoles.
- HTTP/S: Use twistcli to manually download the Intelligence Stream update, host on an HTTP/S server and configure the isolated Consoles to pull the update.
- Relay: Use a “relay” Console as the Intelligence Stream update source for isolated Consoles. Use twistcli to manually download the Intelligence Stream update and import into the relay Console or allow the relay Console to automatically pull updates from intelligence.twistlock.com. Then configure isolated Consoles to pull the update from the relay Console.
- Projects: In a Projects deployment, the Central Console performs the Intelligence Stream update and then distributes the update to the Supervisor Consoles. Use twistcli to manually download the Intelligence Stream update or allow the Central Console to automatically pull updates from intelligence.twistlock.com.
Every release of Prisma Cloud contains a local, up-to-date Intelligence Stream at the time of shipping. The Intelligence Stream update contains threat data gathered since the current release.
How to Perform the HTTP/S Update
In this example, we will demonstrate hosting the Intelligence Stream update on a Microsoft Internet Information Services (IIS) website that is TLS and basic authentication protected.
Step 1
Copy the download command for twistcli from the Console. Go to Manage > System > Downloads > twistcli tool > Windows platform and click "Copy."
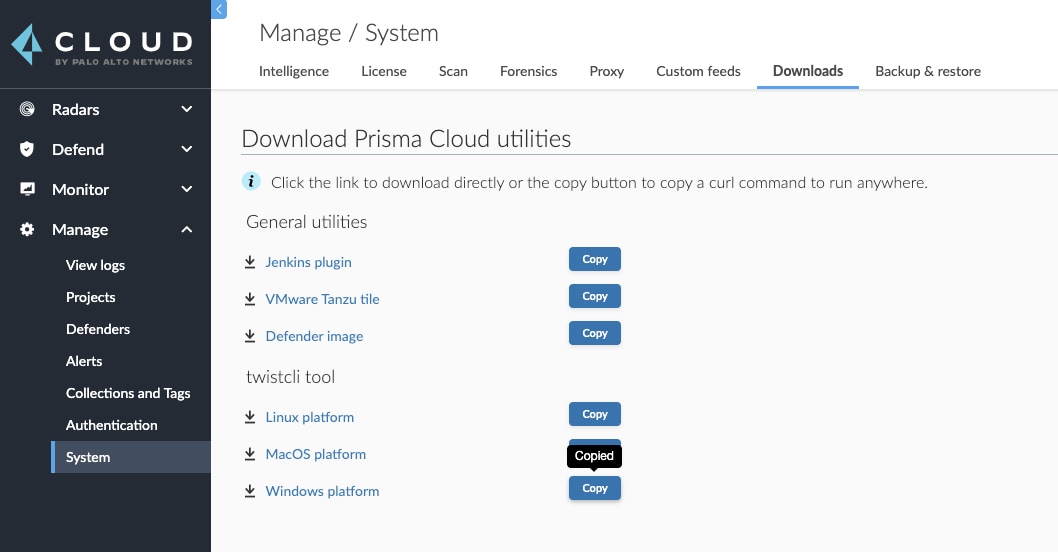
Step 2
On the IIS server, execute the copied command within a command shell. This will call your Console’s API and download the twistcli.exe application locally.
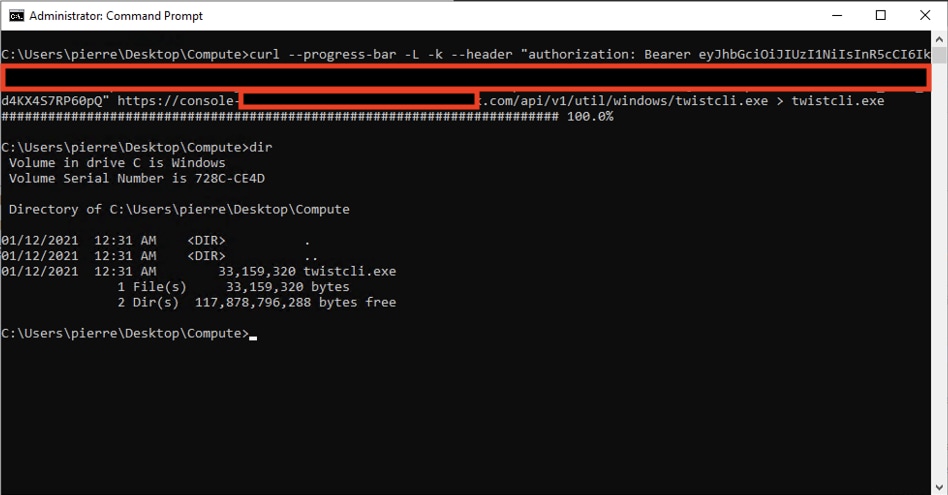
Step 3
Execute the following command to download the latest Intelligence Stream update from intelligence.twistlock.com: twistcli.exe intelligence download ––token <license_access_token>. The ––token argument is your license’s access token, which can be found in the Console at Manage > System > Intelligence.
The downloaded feeds will be compressed into a file named twistlock_feed_xxx.tar.gz. Move this file to the IIS server’s virtual directory that will serve the file to the requesting Consoles. Note: when I move the file I rename it to a common name, intelstream_central_update.tar.gz.
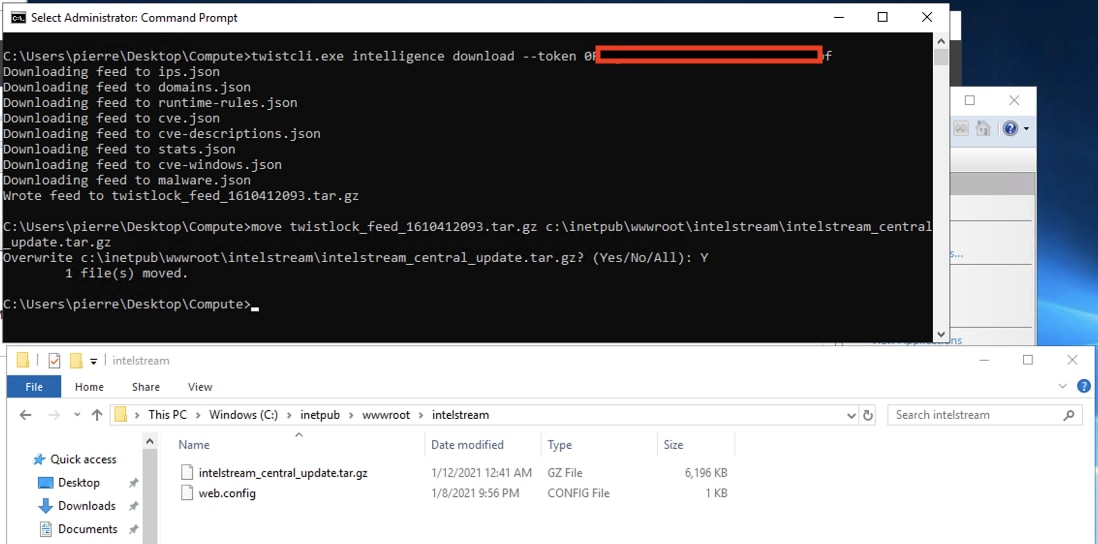
Step 4
Configure the isolated Consoles to pull the Intelligence Stream updates from the IIS server. Navigate to Manage > System > Intelligence. Then select "On" for Update the Intelligence Stream from a custom location.
- Address is the full URL to the Intelligence Stream update file, for example: https://intelstream.authnfox.com/intelstream_central_update.tar.gz
- Credential (optional) is the basic credential that has the rights to authenticate to the IIS endpoint.
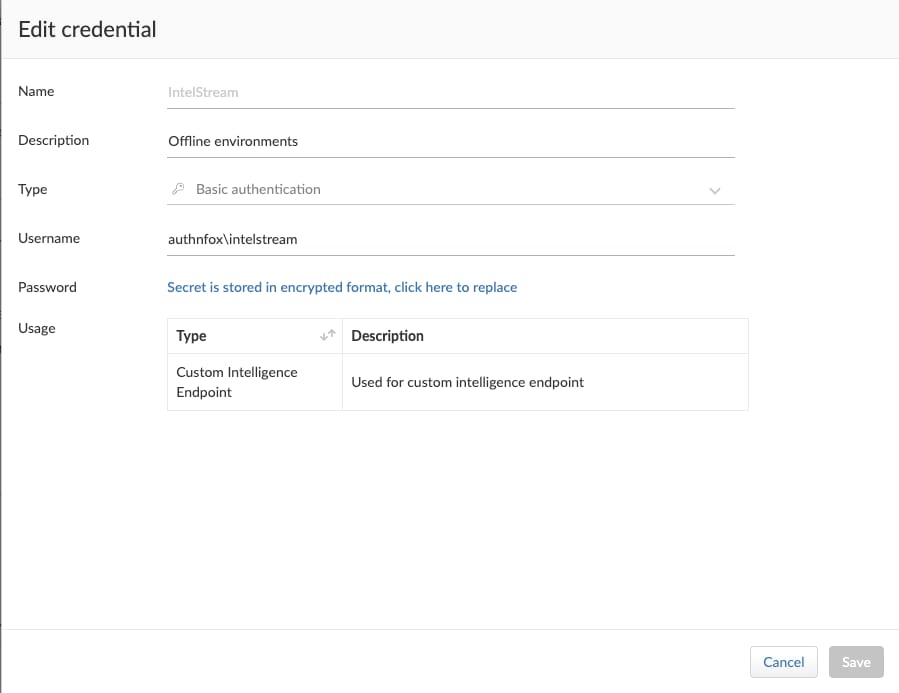
- Enter a CA certificate for the Console to trust (optional). Enter the issuing certificate authority (CA) for the IIS site’s TLS certificate (base64). The Console will validate the IIS site’s TLS certificate when connecting to the site.
- Click “Save”
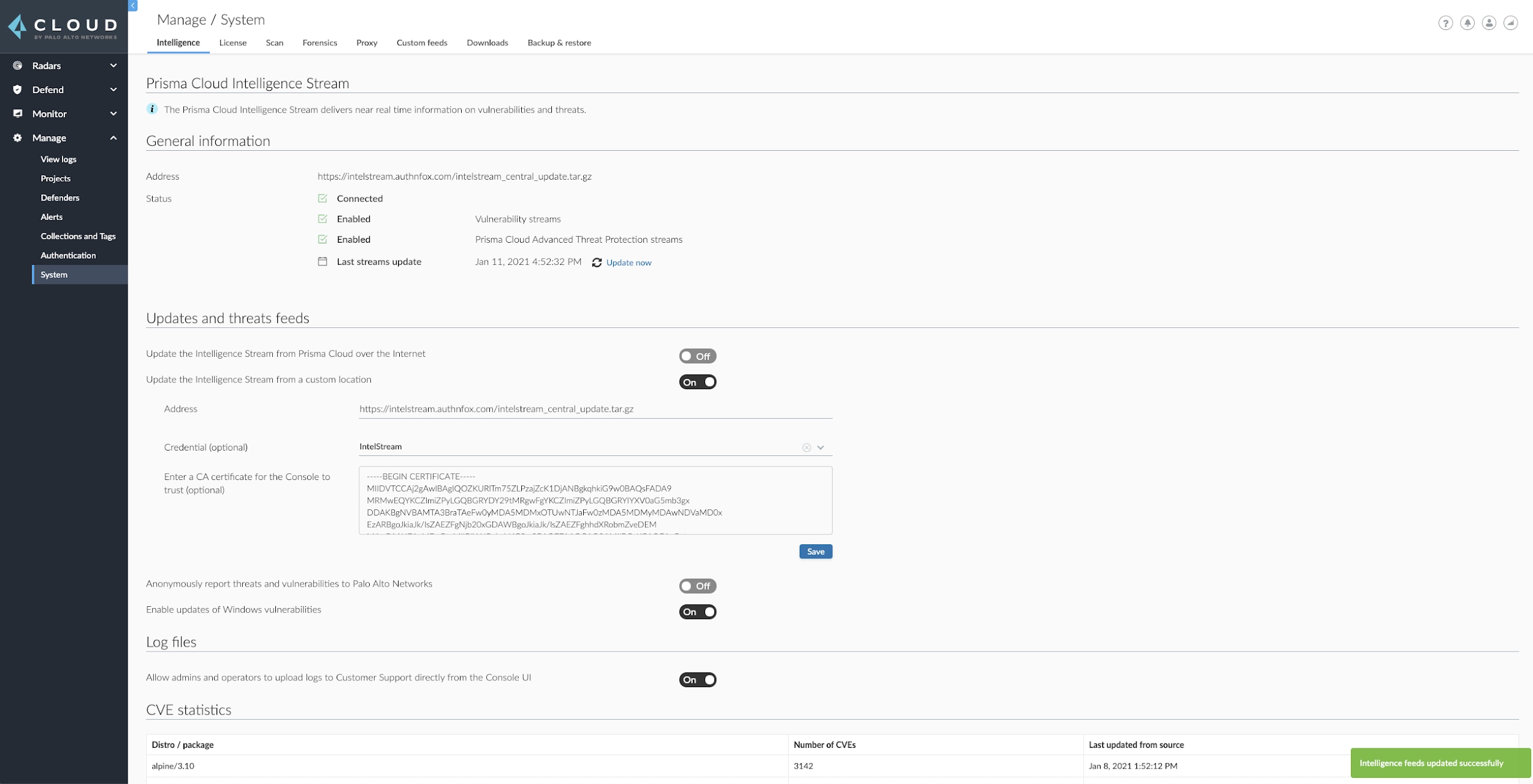
The Console will now pull the Intelligence Stream update, displaying the status in the lower-right corner and in the “Last streams update” field. The Console will automatically check for updates every 24 hours. If the Console is unable to pull an update, it will re-attempt every hour until the update is successfully received.
Conclusion
These new Intelligence Stream capabilities demonstrate our continued commitment to solving challenges for customers that require Cloud Workload Protection within their isolated environments.
For more detailed information about managing threat intelligence in isolated environments, check out the official Prisma Cloud TechDocs.