Palo Alto Networks Cortex CloudTM dramatically reduces the time to detect and respond to threats by correlating signals, elevating actual risk and automating well-scoped actions so low-value noise stays out of the queue.
An alert arrives late in the day and disappears into the swell of notifications. Cloud environments move faster than teams can triage. Siloed tools disrupt visibility and multiply manual work, driving alert overload. The State of Cloud-Native Security Report in fact reports that 91% of security professionals attribute disparate tools to blind spots. Analysts can’t reconstruct context before attackers advance.
The Journey of a Missed Alert: From Noise to Exploitation
Trace what happens when signal turns into noise. A vulnerability scanner flags an exposed S3 bucket. An identity tool flags an unused principal with excessive permissions. Each alert looks low or medium priority in isolation. A team buried in notifications moves on.
Attackers, on the other hand, connect the pieces. They use the overprivileged identity to gain a foothold, pivot across the environment, and reach a sensitive database. Detection existed, but correlation didn’t. The stack failed to relate the exposed bucket to the permissive identity or to quantify the real, exploitable risk.
The Platform Advantage: A Unified Data Layer with Smart Automation
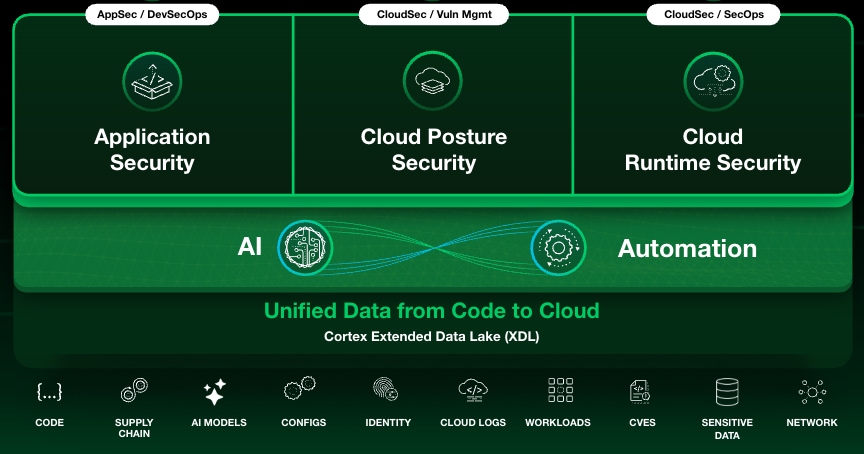
Cortex Cloud replaces fragmented tools with a single CNAPP built on an AI-powered data layer. The platform correlates signals, enriches them with runtime and asset context, and automates the right action so teams move from triage to outcome.
The Initial Alert
Traditional tools treat the exposed bucket and the overpermissive identity as separate, low-priority items. Cortex Cloud correlates them immediately, raises the risk based on the combined context, and sends one alert with the complete attack path.

A Manual Response
Legacy stacks demand handoffs and human confirmation. Cortex Cloud applies prebuilt response actions to revoke excessive permissions and close the path, preventing exploitation before a person needs to step in.
Guided Response When Judgment Matters
If a case requires human judgment, guided playbooks streamline the fix. Policy rules filter low-value noise so analysts focus on the highest-impact work.
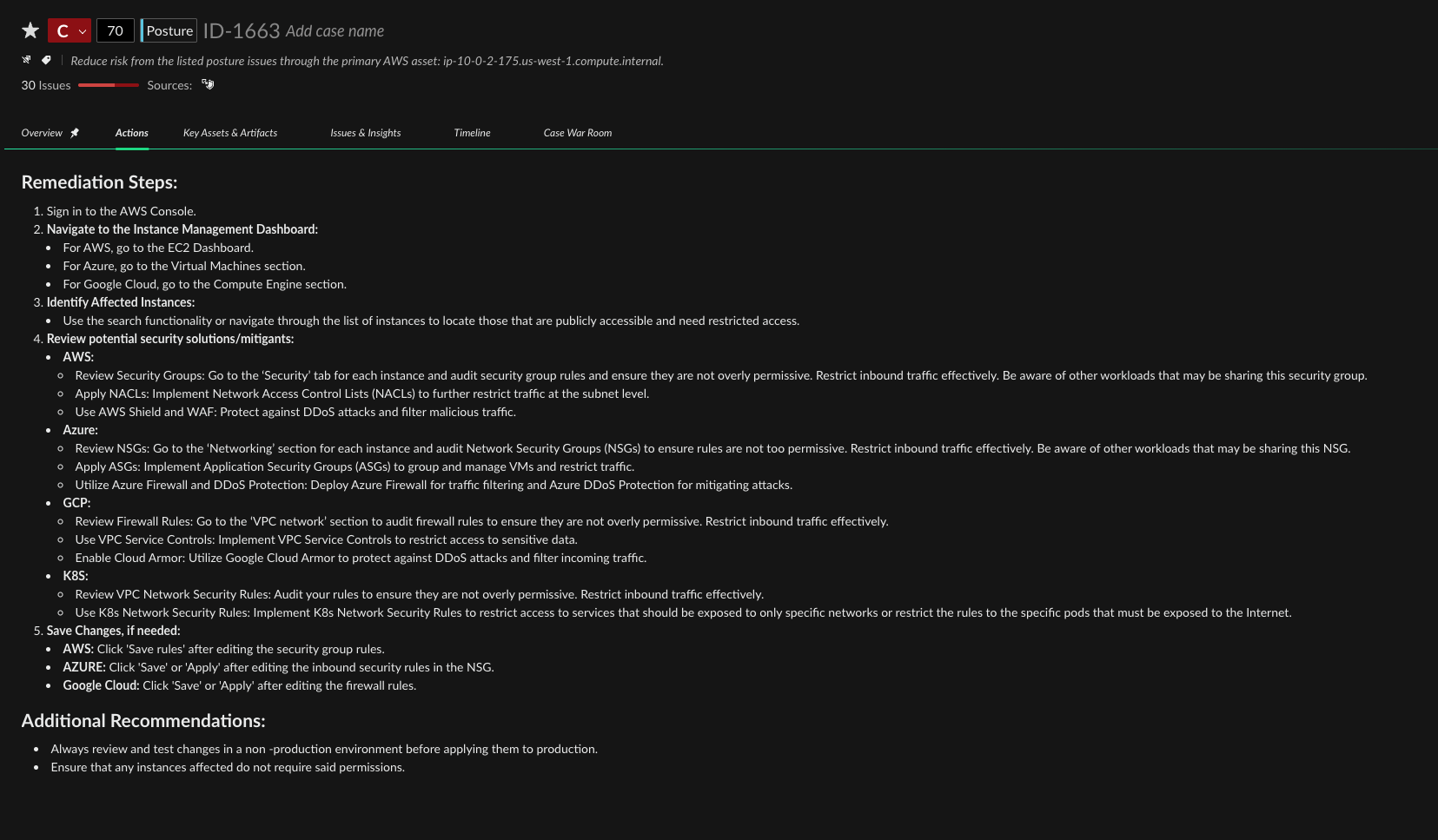
Operationalizing Autoremediation
Leaders need to see how automation stays safe, when to let it act, and how to prove it works in production.
Built-In Safety Guardrails for Autoremediation
Autoremediation operates under explicit control. Policy scope confines actions to named assets and accounts, never the entire estate. Before any change, the system confirms ownership and honors the change window. Dry-run and canary paths prove intent and only then does enforcement proceed. Continuous health checks watch for regressions and trigger rollback when needed. When risk crosses a defined threshold, the change moves to an approver.
When to Automate Vs. Route to a Human
Automate when detection confidence is high and the blast radius stays small. Escalate when data sensitivity rises or dependencies are complex. The boundary is defined by signals — detection confidence, runtime health, recent change activity, ownership clarity and correlation strength. Write those thresholds into policy so decisions remain consistent and auditable.
Concrete Playbooks the Reader Can Picture
Consider a few examples: A public storage exposure calls for making the bucket private, attaching a least-privilege policy and notifying the owner. An overprivileged IAM role merits removing unused permissions, rotating keys and opening a case for role redesign. Suspicious container behavior triggers pod quarantine, blocks the image digest from deployment and creates a ticket with evidence.
How to Measure Success
Measure before you enable automation. Capture alert volume, open-to-close time, reopen rate, rollback rate and the share of low-value noise removed. Track automation’s contribution—the portion of incidents closed without human effort, median autoremediation time and mean time to human involvement. Report week over week for the initial scope and broaden coverage as confidence grows.
Governance and Audit
Policies live in version control with review. Every action writes an immutable audit record with actor, scope, evidence and outcome. Separate policy authorship, approval and execution to keep roles clean. Let exceptions expire by default and require renewal.
Integration with the Investigation Workflow
Every automated action attaches to a case built on an incident-grade object. Signals from code, cloud, identity and runtime map to the same assets and principals, so context holds. With ownership, recent changes and next steps in one place, analysts act without hunting. Effective fixes then move into policy to prevent repeats.
Less Noise, Tangible Business Impact
Automated remediation delivers field-proven gains. Teams that adopt a platform approach cut noise, move faster, and redirect effort to higher-value work.
- Significant alert reduction: Up to 92% fewer alerts through automated remediation.
- Faster response: Mean time to respond drops from days to hours.
- Higher ROI: Freed analyst time converts to a measurable return on security investment.
Empowering Your Team
Cortex Cloud automates routine fixes so analysts concentrate on complex, high-impact threats. The operating model shifts from reactive alert triage to proactive risk reduction, improving resilience without adding headcount.
Take the Next Step
See the platform in action. Request a demo to watch Cortex Cloud’s autoremediation reduce noise and accelerate outcomes.