Moving to the cloud has offered organizations endless opportunities for improving computing and networking management. Now they can effortlessly scale their data centers up and down, optimize costs, swiftly configure networks, and gain full flexibility when it’s time to make architectural changes or introduce new technologies, such as AI capabilities, to a product.
However, these opportunities come with a cost. The move to the cloud unlocks agility and scale but leaves identity and access management in chaos. The growing number and types of identities – including human, nonhuman and AI agents as well as the endless ways they access environments – poses significant risks for organizations with a cloud presence.
In this blog post, we will explore the differences between on-premises and cloud permissions management. We will also examine the main challenges organizations face when trying to maintain the principle of least privilege in their cloud environments and discuss what can be done to improve your identity and access posture.
Main Characteristics of On-Premises Environments
On-premises environments are mainly characterized by being fully managed, controlled and owned by the organization running them. This means that every resource needs to be purchased, installed, connected to the network, and managed by a dedicated person within the organization. This has many financial, organizational and operational implications, particularly for identity and access management. While monitoring and approving every change helps keep things under control, these processes tend to slow down the organization's ability to adjust and scale according to ever-changing needs.
Identity and access management are static and centralized. A main variable indicating the complexity level of your identity estate is the quantity of resources in your environment. On-premises setups are relatively static. Tight mechanisms set to control the purchase, movement and administration of all compute resources make it easy to keep track of inventory: You know what resources you have, where they are, what they’re connected to, who is responsible for them, and who can access them.
Control Comes at the Expense of Agility
The process of growing an on-premises data center involves purchasing new servers, configuring them, and connecting them to the network. This means that significant changes are infrequent and are monitored by relevant organizational functions. With an on-premises environment, security personnel can be rest assured that no major changes will occur without their knowledge. They have the ability to keep track of all compute-related inventory and can manually approve or reject the addition of any compute resource to the data center.
New technologies aren’t often introduced: New technologies are introduced only from within. Similar to adding a new resource to the data center, the addition of new technology to the organizational stack requires an approval process and can take time to implement.
The number of identities and devices is manageable: On-premises environments are built around a defined perimeter and a limited set of users, applications and devices. The inventory changes infrequently – usually when new hardware is purchased or when employees join or leave the company. External devices can be easily controlled using permissions and networking guardrails.
Access is limited from the outside: Access from an external source (like a SaaS provider) is heavily controlled and continuously monitored by a range of tools, including firewalls, WAFs, network segregation and DMZs. When enabling access from an external source, it’s easy to define who can access the environment, where they can (and cannot) come from, what exactly they can access, and what they can do with such access. This enables a safe connection to the outside world, ensuring that you let in and out only what is supposed to enter and exit.
Keeping a tight grip on the organization's data and compute resources and maintaining a controlled process when introducing new technology enable you to control access and minimize the risk of unnecessary or unwanted granted permissions. At the same time, these mechanisms and guardrails slow down the organization’s ability to advance and expand when necessary.
A simple permissions model comes at the expense of granularity: In general, three permissions can be granted in managed, on-premises environments that are controlled by an active directory: read, write and full access. While extremely simple, this permissions model is overly permissive by design. Utilizing a packaged-deal permission set means that every granted permission includes a set of actions that the identity can carry out without requiring all granted permissions. For example, when granting write permissions on a file, an identity can change the file data or metadata, copy or move it, or even delete the file, while the only required task may be to change the file’s name.
While on-premises identity and access management is a manageable task, it compromises on speed and innovation. Therefore, as organizations increase their cloud footprint and reduce their on-premises presence, security professionals must ask themselves: What can we do to allow our organization to move at the speed of cloud while maintaining as much control over identities and permissions as we had in an on-premises environment? How can we unlock agility and innovation while maintaining security and fulfilling the principle of least privilege?
Main Characteristics of Cloud Environments
Innovation velocity or the data and compute sprawl? Cloud resources can be spun up and terminated with a few clicks. A new server can be up and running in minutes, and once you don’t need it, it can be gone in seconds. Pay-as-you-go subscription models enable organizations to save money and time by scaling up and down according to their specific needs, without the operational costs of building and maintaining an on-site data center. This also frees up development teams from the bureaucracies tied to receiving resources for their development process, which significantly improves efficiency and shortens the software development lifecycle.
Even though it increases flexibility and speed, the dynamic cloud environment presents a challenge. Your organization’s inventory becomes extremely dynamic, and the number of servers, virtual machines, databases and network assets can change by the minute. Each datastore, piece of code, or machine exposes your organization to a never-ending list of vulnerabilities and potential threats.
The speed at which resources can be added and redacted from your environment enables dynamic innovation – the ability to store as much data as you need or continuously scale servers running your applications. However, an ever-changing inventory of resources means an unlimited expansion of permissions leading to endless amounts of data that can be accessed and a never-ending number of users, VMs, functions and AI agents that can access them.
New Technologies Are Introduced Regularly
Cloud providers are innovating quickly. New services are released and updated regularly, enabling you to enjoy new, ever-improving technologies. You can customize your stack to the specific application you are developing and get the best fitting solutions for your storage, workload, AI and security needs. If your needs change, you can shift to another, better fitting technology from your provider's portfolio, without the cost or logistics of buying and replacing hardware.
Applications, AI agents and machine identities have also acquired many new capabilities in the cloud. These technologies are now essentially armed with the power to conduct human-like actions within a cloud environment, controlling other resources and sometimes even managing permissions. This means you have to keep up with all these innovations, stay up to date with new releases and improvements, and understand the risks that each technology presents.
Large Numbers of Identities and Devices
Since 2020, and particularly thanks to cloud advancements, remote work has become a far more common practice among companies. It is now significantly easier to connect to your organization's environment and gain access to all required resources from anywhere, reducing the need for employees to attend a physical office. Employees now use their work and personal laptops, phones, tablets and other personal devices to connect to your environment regularly.
Additionally, it has become much easier to connect external accounts to yours. But the rise of SaaS applications and their easy implementation have also made it more difficult to keep track of which external accounts your environment is exposed to and to analyze each account’s access.
This means that your organization is now being accessed from many locations and an unlimited number of devices and by more external organizations. While this opens up new employment and globalization opportunities, it also increases the volume and complexity of network traffic, making you vulnerable to common infiltration methods such as supply chain attacks and social engineering.
| Characteristic | On-premises | Cloud |
| Centralization | Centralized over resource management | Fragmented, dynamic resource management |
| Agility | Relatively slow-moving, significant changes in scale are predictable | Extremely dynamic with rapid changes, new technologies are introduced regularly |
| Number of identities | Controlled | Uncontrolled – large number of identities, devices, machine identities, third parties, and more |
| Access from the outside world | Heavily monitored | Easily granted, hard to keep track of |
| Number of permissions | Read, write and full access | Dozens of permissions per service, hundreds of different services, cloud-specific |
Table: the main differences between on-premises and cloud environments.
How Can You Regain Control over Your Overly Dynamic Environment?
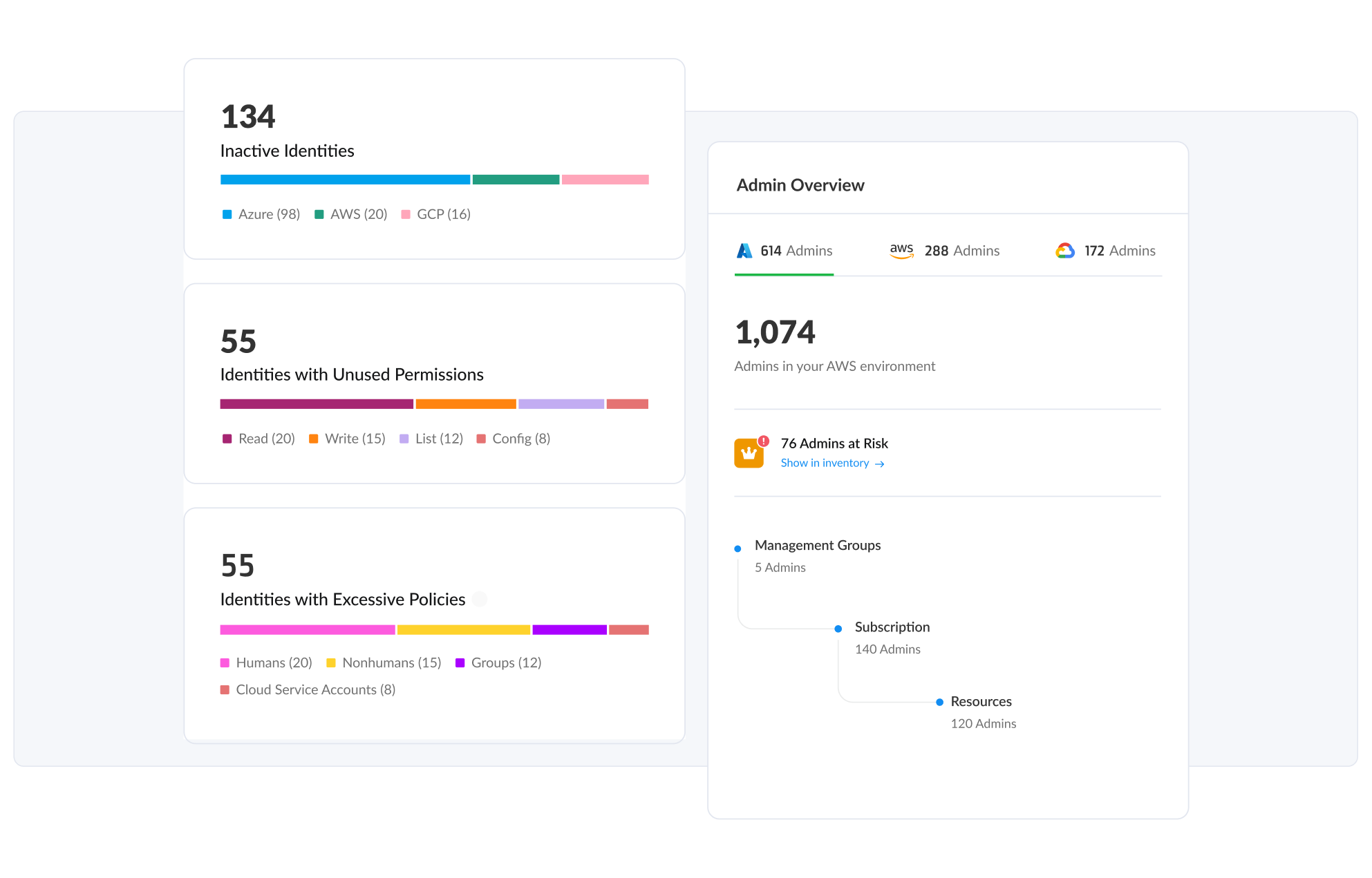
A changing inventory of servers requires a constantly updated inventory list of assets. Good cloud-native application protection platforms (CNAPPs), which secure various cloud aspects, create a list of all your cloud assets and always scan your environment to update it.
Similarly, a complete identity solution for the cloud continuously scans your cloud environment to detect human and nonhuman identities, AI agents, service accounts, groups and policies. It will then provide an updated view of your organization's identity inventory. You can utilize the solution to detect dormant or vulnerable identities in your environment, a publicly accessible EC2 instance or a user with an unused, unrotated access key.
Your identity solution should also be able to accurately calculate effective permissions to help you understand who can do what and where, as well as identify administrative or overly permissive identities in your environment. Finally, it should help you analyze your organization's exposure to “the outside” such as external accounts and applications.
The combination of live inventory, configuration assessment and effective permissions calculation provides a solid foundation for controlling which identities exist in your organization and which permissions each identity holds.
Addressing the Massive Numbers of Permissions
The wide variety of cloud services along with the need for more granular permissions management has driven cloud providers to develop service-specific actions. Each service can have dozens of different permissions, enabling you to pinpoint the specific actions each identity should be able to conduct. For example, the Amazon AWS S3 service has different permissions for listing all objects under a bucket, listing access points, reading objects, getting the bucket’s policy, or seeing a bucket's tags.
Like your environment, your permissions can also be extremely dynamic. With the use of name-pattern-based, tag-based or attribute-based resource permissions, you can dictate who can access which resources not only in the present, but also in the future. A misuse of these concepts, on the other hand, can create a permissions gap where identities are granted access to resources they don’t use or to which they shouldn’t have access. The permissions gap is a real-world problem, as nearly all cloud entities are overpermissioned. In fact, 99% of cloud identities are granted permissions that go unused for 60 days or more, exposing organizations to unnecessary risk.
While having a detailed understanding of one's identity landscape is crucial for security, the concept of a highly dynamic environment in combination with a complex permissions model makes it difficult to map who is able to do what and where.
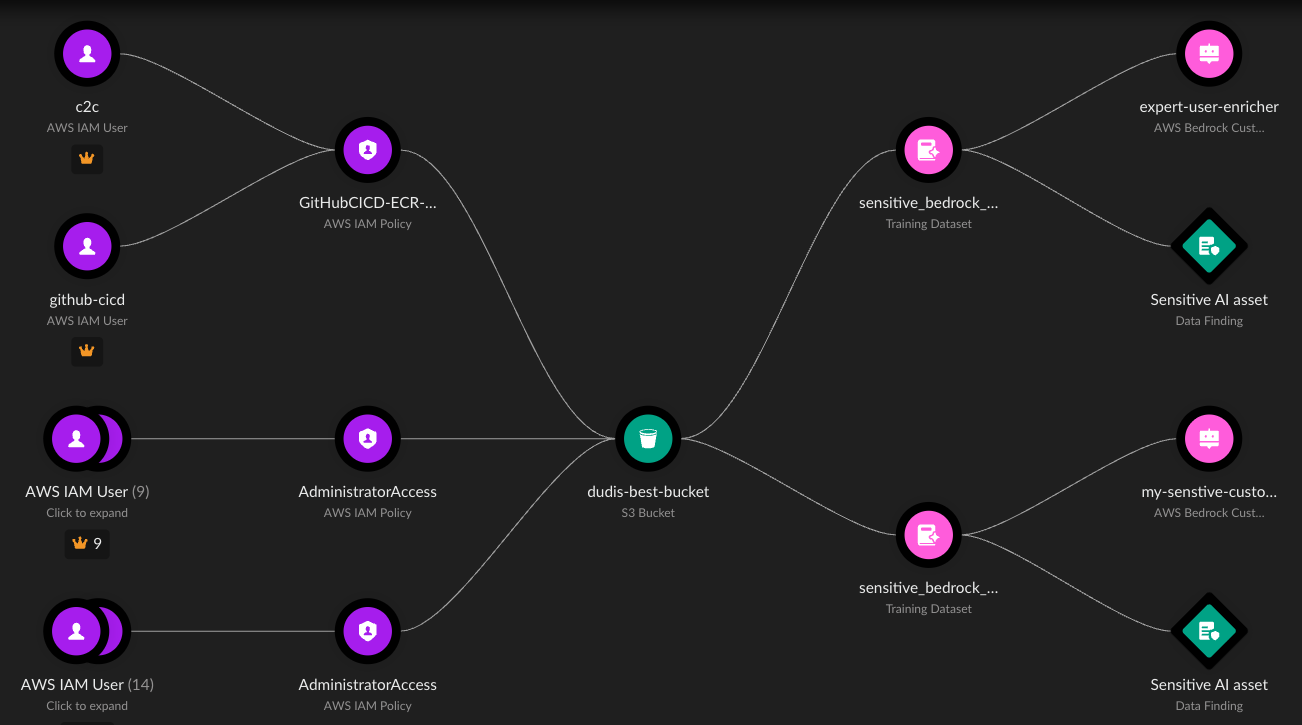
Understanding the Meaning Behind Permissions?
An effective cloud identity solution provides relevant context to your permissions estate. It should be able to categorize permissions into high-level access classes that offer the simplicity of on-premises permissions without losing the granularity of the cloud, whether you deploy a single- or multicloud architecture. This should help give you an understanding of what the different actions mean and what identities can do in your environment when given certain permissions.
Your identity solution should also provide security-aware insights into your permissions estate. A strong solution doesn't only tell you what you have but also provides an expert-driven posture view of it. Your solution should help you answer the following questions:
- Are there any overly permissive identities in your environment?
- Are you granting any unused permissions?
- Are you granting permission combinations that open up the possibility of lateral movements or identity-based attack paths?
- Do you know which external organizations have access to your environment?
- Are you allowing for the possibility of role chaining or unintended cross-account access in your environment?
- Can an identity move laterally from a compromised workload to a critical data resource?
The sensitivity of cloud permissions as well as cloud and service variations require a deep understanding of the risks that come with granting different permissions. Your identity solution should provide posture insights that help you not only understand what you have but also assess how secure your environment is, and more importantly, which actions you should take to improve it.
What Can You Do to Get Ahead of Your Permissions?
Identity security posture solutions—such as cloud infrastructure entitlement management (CIEM), identity security posture management (ISPM), and identity visibility and intelligence platforms (IVIP)— were created to help you handle the identity and access-related risks in the cloud. And they maintain a few capabilities that help you stay ahead of your environment.
- Keeping an inventory of your identities: Such solutions help you keep track of exactly what you have in your environment – which human and nonhuman identities, groups, service accounts and policies exist and receive or grant permissions.
- Understanding your environment: CIEM solutions carry out effective permissions calculation, painting a precise map of who can do what and where they can do it.
- Listing security gaps: Compare your environment against a set of security framework and detect all your identity security gaps, which can include misconfigurations, dormant accounts, unused permissions or overprivileged identities. A well prioritized list of gaps is a good start for creating an identity security improvement program.
- Leveraging context-aware insights: When insights are enriched with context from across your environment—such as data, AI, code, workload and cloud applications—your identity solution becomes significantly more powerful. It can go beyond static findings to deliver a business-aware, prioritized list of risks, helping you focus on the issues that matter most and address the root causes efficiently.
- Solving your problems: Identifying gaps is only part of the solution. A good identity posture solution should help you take active steps in your environment to achieve least privilege without slowing down business.
- Staying compliant with any standard or framework: Identity security posture solutions help you plan and maintain your identity estate in a way that is compliant with any standard to which your organization is subject. They usually also help you produce relevant reports to prove that you are indeed compliant with any required standard.
- Achieving least privilege: Most identity-focused security teams work hard toward achieving least privilege – granting access only to those who need it, and specifically, where they need it. Identifying and removing unused permissions, downsizing excessive permissions and providing data-aware context are some of the tools these solutions provide to help you take significant steps toward least privilege.
Palo Alto Networks Cortex Cloud includes a strong, security-centric and business-aware identity security solution. We unify identity security posture management (ISPM) with threat intelligence, data security, code, application security, and more to give you the context required to secure your identity estate. Let our experts guide you through the process of understanding your current state, helping you to prioritize and fix identity security issues and achieve least privilege at the speed of cloud.
Ready to secure identities at the speed of cloud? Book your demo today.