Although much of the talk about 5G has focused on the benefits to consumers of faster connection speeds, serving the connectivity needs of the enterprise is what 5G was designed and built for. ARPU (Average Revenue per User) trends have been stagnating for some time. If service providers expect to increase revenue from 5G, it will have to come from creative offerings to enterprises and government entities.
These offerings will need to address each enterprise’s service level requirements, using automation to easily deploy offerings. As 5G-enabled solutions become more popular, such services and functions will attract more criminal activity. Accordingly, securing 5G networks through specific security policy enforcements at the enterprise level becomes more of an imperative.
For mobile service providers, delivering a ubiquitous “fast pipe” isn’t enough to substantially increase the bottom line. Driven by 5G’s promise for the enterprise, mobile service providers are building new value-add services on top of connectivity.
In short, 5G is driving transformation in new and somewhat unseen ways – for consumers and enterprises alike.
Often security around mobile networks was focused around perimeter security for radio access networks (RAN) and core. This entailed firewalls or, better yet, next-generation firewalls (NGFW), positioned in the interface (Gi LAN) at the internet connection or between the carrier and its roaming partners. Subsequent NGFW protection was added in the control plane of mobile 5G RAN and especially 5G core.
Here, whether with volumetric distributed denial-of-service (DDoS) or well-crafted protocol fuzzing attacks, stream control transmission protocol (SCTP)-based interfaces could be rendered useless to service and thus shutting down subscriber access to that mobile service. This blog will address why the user plane should also be statefully protected with the aid of NGFWs in order to prevent loss of service due to compromised user equipment (UE), which in turn could set up the kill chain that shuts down the mobile service.
GSMA and FS.37
5G service is built on the standards proposed by 3GPP, which in turn can rely on other standards bodies (e.g., IETF, IEE, O-RAN Alliance, etc.) These standards are the detailed foundation for the GSM Association (GSMA), which is an industry organization that represents the interests of mobile network operators (MNO) worldwide.
The GSMA represents its members via industry programs, working groups and industry advocacy initiatives. One of GSMA’s roles is to present the implementation of current 3GPP specifications to its members from an operational perspective. Similarly, the GSMA Security team’s purpose is to analyze the industry’s threat landscape and provide information that enables their members’ ability to protect the mobile ecosystem.
Among GSMA deliverables is FS.37 GTP-U Security, which addresses the attack vectors in the user plane and the corresponding features a provider would need to mitigate those threats. FS.37 provides recommendations for MNOs to detect and prevent attacks using General Packet Radio Service (GPRS) Tunneling Protocol for User (GTP-U) plane data on the network, services, and applications. FS.37 recommendations also recommend how to remediate the threat posed by malware or other suspect user traffic. GTP-U is the protocol that carries user data tunnels within the GPRS core network, and between the radio access network and core network. To illustrate these recommendations, FS.37 contains guidelines on how to logically deploy security capabilities on 3GPP interfaces which include the modes of deployment.
As mentioned above, mobile service providers are expanding from simple high speed connectivity to more value-added security-enabled services. This expansion of services will enable, at least, two key outcomes:
- Reduce financial, reputational and operational risks to the service provider and thus its customers.
- Enable enhanced “per enterprise” security controls that detect and prevent attacks enforcing each enterprise’s desired security posture in their GTP-U traffic plane.
GTP-U protection will be able to statefully detect and remediate in real-time malicious traffic the struggle to keep off their corporate networks. Examples of these threats seen on the network include:
- Denial of Service Attack: Disable service or access to it by volumetric overwhelming of a service-node
- Man-in-the-Middle Attack: Attacker gets between the two ends of an end-to-end communication flow. This allows them to passively (i.e. only listening) or actively (i.e. with modification of the original data) participate in the connection.
- Ransomware Attacks: Separate form of a DoS attack in which end systems are encrypted and decryption is offered against ransom payment.
- Privacy Violations: Unauthorized, stealth access to resting or dynamic data, e.g., smartphone location tracking or contact-stealing.
With today’s technology solutions, these threats could be identified and remediated before any service impacting incident. Under best case conditions, these threats could be stopped entirely.
User Plane Attack Vectors and Subsequent Requirements
Security attacks in mobile networks can come from these key four communication paths:
- Attacks against/from the telco infrastructure and its service
- Attacks against/from subscribers/users
- Attacks against/from telco partners and their services (e.g., roaming partners, regulatory services, etc.)
- Attacks against/from the telco company’s back office (e.g., operations administration and maintenance access, logistics, customer portals, etc.)
The FS.37 focuses on the second path and documents how users and devices can get infected (or malicious users join the network). One should consider inbound roaming as also vulnerable local users who could be compromised and launch a botnet attack, as example, on the local mobile service provider.
Compromised mobile users can exfiltrate corporate data, initiate ransomware as well as attack network services (e.g., DDoS of Authentication Server Function [AUSF]) or compromise of operations systems (as seen in Figure 1).
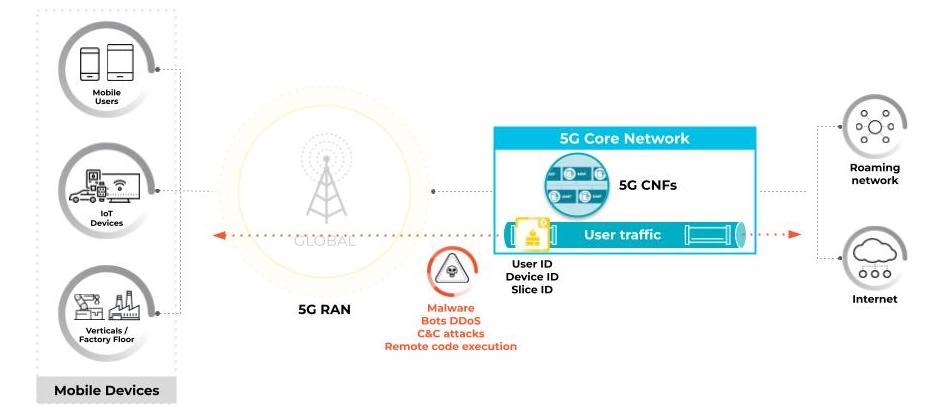
Granular visibility and policy control of the user plane can mitigate these breaches. Palo Alto Networks ML-Powered NGFW for 5G can be deployed at the N3 interface where it has full visibility of the user plane traffic. The firewall correlates user plane traffic in N3 with subscriber specific identifiers (user ID, device ID, slice ID) from the N4 interface (PFCP). The resulting granular visibility and control of the user plane traffic enables the mobile service provider to offer vertical or even customer-specific security policies.
Now each enterprise is, according to its security requirements and regulations, uniquely protecting its mobile-based infrastructure from UE-based threats through L7-based security intelligence. All Palo Alto Networks enterprise-grade security capabilities across App-ID and Cloud-Delivered Security Services (CDSS) – including DNS Security, Wildfire, Threat Prevention, URL Filtering, IoT Security, DLP – are available in any combination and configuration.
Palo Alto Networks offers the following key user plane security capabilities – available in virtual (VM-Series), container (CN-Series) and hardware-based (PA-Series) form factors:
- Visibility and policy control based on Subscriber ID, Equipment ID and Network Slice ID
- 5G Subscriber ID Security—incl. SUPI/IMSI
- 5G Equipment ID Security—incl. PEI/IMEI
- 5G Network Slice Security—incl. NSSAI
- GTP-U content inspection
- GTP-in-GTP
- GTP-U Protocol validation
- GTP-U tunnel endpoint identifier (TEID) validation
Now mobile service providers can protect their core services from both malicious attacks, whether acting alone or with the help of compromised UEs. These security mechanisms also can provide additional revenue from security-enhanced services which enterprise customers can shape to meet their ubiquitous wireless needs.
Security in 5G extends beyond internet, roaming or even control plane protection. Protecting UEs and the user plane traffic ensures not only the enterprise’s safety but also the provider’s service availability. And – effective protection of the user plane traffic can only be achieved with granular visibility and policy control, and enterprise-grade L7 security.
Ignoring security controls in 5G could result in severe public security breaches which, in turn, could place at risk key financial relationships with each vertical that the mobile service provider is serving.
Advancements that are inherent in 5G, including cloud-based scale, as well as slice ID delineated, will drive the mobile service provider to transition to new value-added services that will meet the security demands of their enterprise customers, especially those in government and defense. Security mechanisms will be spun along with the 5G RAN and core elements to ensure that the mobile services offered are highly available, robust and secure.