Critical operations must have a self-healing infrastructure built with 100% uptime and zero trust access controls.
Industries such as energy, emergency services and public safety require highly resilient, secure network communications across all sites, including remote and isolated ones. When traditional fixed-line services like fiber optic are unavailable or prohibitively expensive, organizations rely on radio and non-terrestrial backhaul networks, including LTE, 5G and satellite, for essential primary or backup connectivity. Crucially, these critical systems must remain air-gapped or blocked off from any external connectivity beyond what is strictly necessary.
These once-isolated control networks are very appealing targets for malicious actors. The convergence of operational technology (OT) and information technology (IT) is increasing the threat landscape for these assets. Even systems theoretically air-gapped from the public internet are vulnerable to threats like lateral movement from tangential networks, purposeful infiltration and sophisticated malware, while rendering them unable to leverage the dynamic threat protection and robust defenses offered by modern cloud-based security and connectivity services.
Nation-state actors, such as Volt Typhoon, have already demonstrated their ability to penetrate critical infrastructure, remaining hidden and poised for disruption. Furthermore, Russian-linked actors have shown they can manipulate physical systems, as evidenced by incidents like the overflow of water tanks in Texas, exploiting the inherent connection within modern control networks.
In this context, connectivity and security can no longer exist in separate silos. A remote substation, water-treatment node or compressor station needs not only deterministic transport, whether over fiber optic, 5G or satellite, but also a zero trust footprint capable of detecting and preventing malicious activity before it reaches the control plane. The two objectives are inextricably linked. There is no reliability without security. Critical infrastructure security is national security.
Forward-looking utilities and other organizations are addressing this challenge by converging highly resilient connectivity and a zero trust security footprint into a single intelligent platform that dynamically steers traffic while continuously enforcing zero trust security policy. This results in an intelligent, self-healing network that keeps critical operations running and shielded from malicious actors. In other words, zero trust availability.
In the following sections, we’ll explore how to converge a zero trust security posture with resilient, self-healing, deterministic connectivity and unified visibility at the edge to protect the most remote and vital parts of modern critical infrastructure, while leveraging remote networks such as 5G and satellite links.
Software-Defined Networks for Critical Air-Gapped Infrastructure: The Challenge
In remote and distributed environments, traditional WAN architectures quickly reach their limits. Fiber optic seldom extends to substations, compressor stations, or field controllers, and leased-line redundancy is often cost-prohibitive. In such cases, utilities are turning to pLTE/5G, fixed wireless, or satellite as their only viable transport options, which each brings their own challenges.
Cellular networks are often deployed behind carrier-grade NAT (CGNAT), making it difficult to establish or maintain site-to-site tunnels. Dynamic IP addressing and variable signal quality can interrupt VPNs, forcing manual intervention. Satellite links, whether geostationary or low Earth orbit (LEO), introduce latency and jitter that break conventional failover logic and impair real-time application performance such as SCADA polling. These links may also experience asymmetric bandwidth, where download and upload speeds differ drastically, complicating QoS and routing decisions.
Even when multiple links are available, legacy technology such as dynamic routing and IPsec VPN concentrators lack the intelligence to evaluate link performance or steer traffic dynamically. Traditional static failover approaches lead to unnecessary downtime or congestion.
Typically, LTE or 5G-enabled customer premises equipment (CPE) deployed at edge locations do not include mechanisms to sufficiently secure the environment. A strong zero trust security posture means preventing unwanted lateral movement by removing all implicit trust. This includes identifying applications beyond the ports, protocols or URLs they use - meaning actively scanning the behavior of the applications within the traffic payload at all times.
Additionally zero trust security needs to include proper segmentation of the network to only permit the applications, devices and users explicitly allowed to traverse boundaries. At the edge site, this can include separation based on network functions, such as defined in levels 0-2 (and beyond) of the Purdue model and to meet standards such as ISA/IEC62443, DNP3, IEC 60870-5-104, and ICCP, among others.
The separation of network and security results in having to own, deploy and operate multiple devices, likely from different vendors at each and every site, with a negative impact on costs and operational complexity. In addition, distributing the security functionality to an additional edge device compounds the issue of limited availability of space and power. If each site relies on separate hardware for firewalling and WAN management, the surface area and operational complexity grows, updates lag, and visibility fragments across hundreds of isolated nodes.
Addressing these problems the right way decreases technical and operational complexity and reduces exposure to network and cybersecurity incidents.
Software Defined Networks for Critical Air-Gapped Infrastructure: Convergence
Palo Alto Networks Advanced SD-WAN is built directly into the PAN-OS. When deployed on a cellular-enabled Palo Alto Networks NGFW like the PA-450-5G it delivers Ethernet, satellite and mobile connectivity, edge segmentation, real-time traffic awareness, deterministic and dynamic path selection, with zero trust enforcement. Converged into a single device with no cloud dependency or the need for a dedicated SD-WAN controller, it is ideal for critical air-gapped or regulated environments.
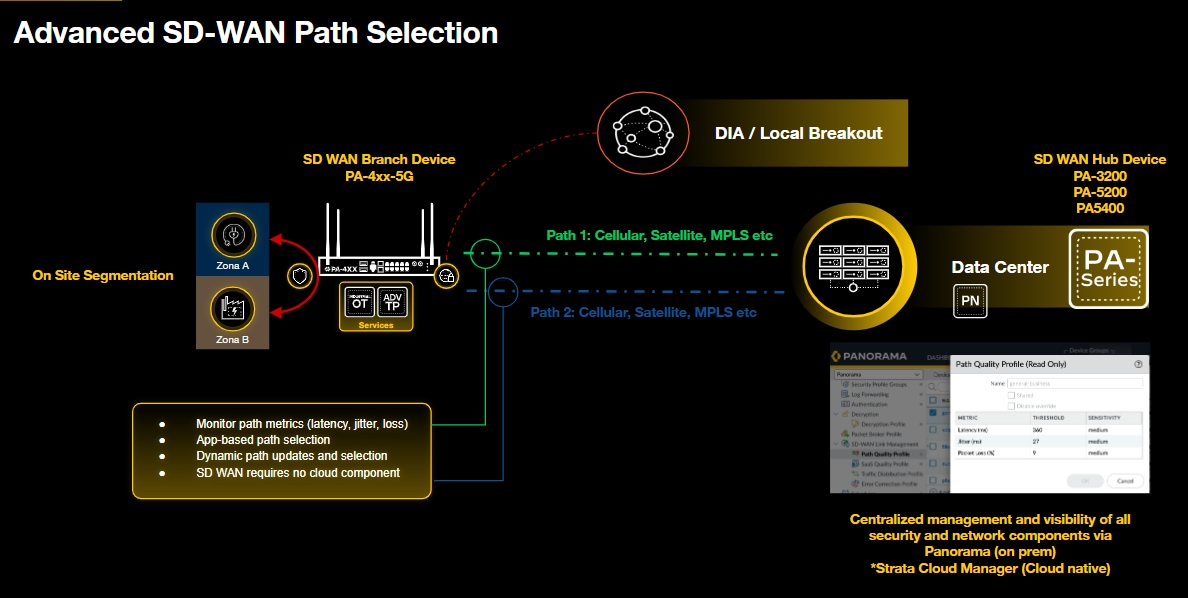
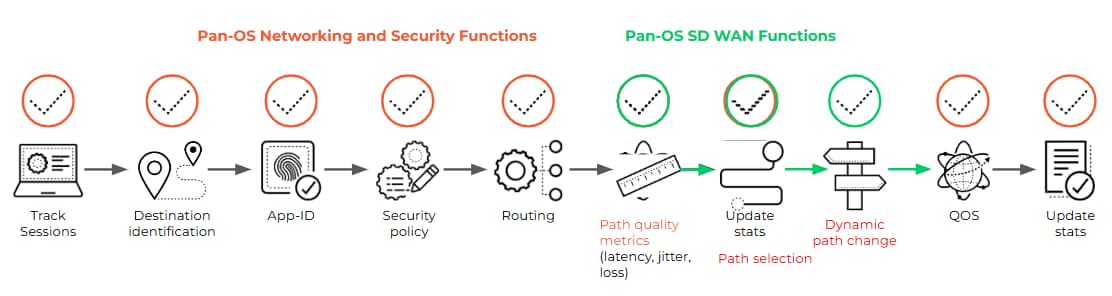
Palo Alto Networks firewalls, leveraging their powerful App-ID technology, identify traffic by its true application, not merely by port or protocol. This deep contextual awareness allows administrators to enforce granular zero trust security policies and apply customizable path quality and distribution profiles at the application-layer.
These profiles define acceptable thresholds for latency, jitter and loss. For mission-critical examples, such as a SCADA application using Modbus, this guarantees that protection and control traffic always takes the most stable path. Less critical traffic, however, can seamlessly load-share or failover across 5G, satellite or fiber optic connections. Furthermore, forward error correction (FEC) and jitter buffering are utilized to maintain stability even across high-latency or variable links, such as satellites.
Deployment and operations are streamlined through Auto-VPN, which automatically establishes secure IPsec tunnels between remote sites to the hub site(s), removing the need for manual provisioning, key management or controller intervention. This allows for fast, efficient and error-free deployment of Hub and Remote endpoints at scale.
Panorama, the centralized on-premises management system from Palo Alto Networks, provides unified management, policy control, lifecycle management and performance visibility across all nodes. Each node operates autonomously yet remains fully visible and manageable through secure, encrypted channels. Operators can monitor link health, application performance and threat posture from a single console, reducing complexity and accelerating troubleshooting.
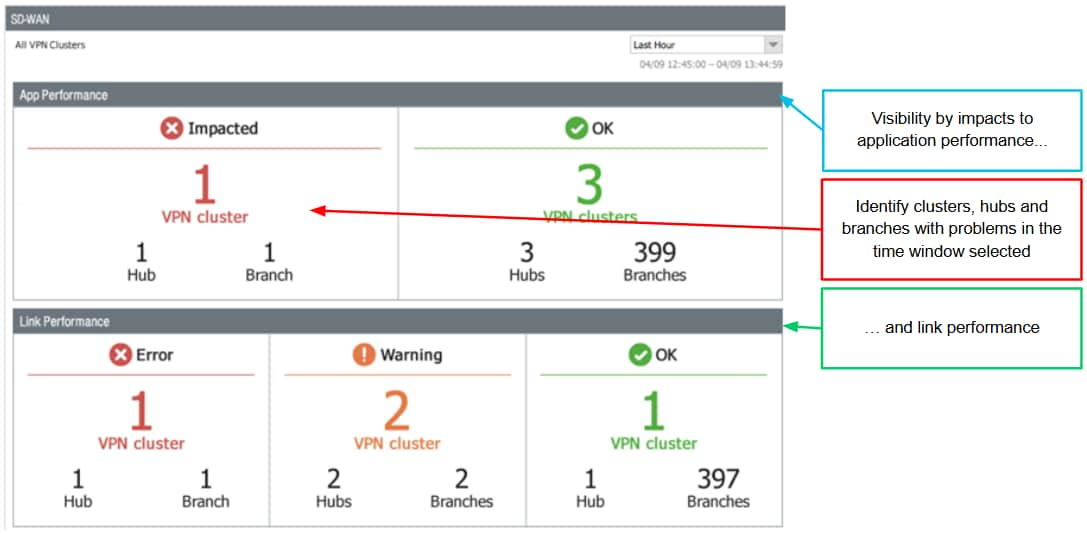
The result is a network that is both resilient and secure by design. An application-aware network that dynamically optimizes usage of LTE, 5G, satellite and fiber optic links while continuously enforcing a zero trust policy at every site. For critical infrastructure operators, this unification delivers fewer devices, simpler management and uninterrupted protection, even at the most remote edge of the grid.
Software Defined Networks for Critical Air-Gapped Infrastructure: Summary
Using the right secure edge products and unifying ASD-WAN intelligence with next-generation zero trust security in a single platform at the edge, PAN-OS ASD-WAN ensures every site stays online, protected and visible, even when connectivity relies on vulnerable transport mechanisms like mobile or non-terrestrial networks.
To learn how Palo Alto Networks helps utilities and critical infrastructure achieve deterministic performance with zero trust protection, visit /network-security/ASD-WAN-subscription or contact your Palo Alto Networks representative.
Further Reading
https://gca.isa.org/blog/common-ics-cybersecurity-myth-1-the-air-gap
/blog/2010/10/stuxnet-scada-malware/