Today, ransomware continues to be the most damaging form of cybercrime for organizations. Palo Alto Networks Unit42 threat research team found that demands ranged anywhere from $3,000 to $50M. This has even resulted in conversations of a “ransomware payment ban," which has caused a divide amongst the cybersecurity community. However, regardless of a ban or not, threat actors will continue to be resilient and find new and innovative ways to launch these attacks.
The three most popular methods for delivering ransomware were through emails, third-party applications and URLs and in 2021, Palo Alto Networks Unit42 team found that email attachments were the most popular. However, now in 2023, the team has discovered that URLs have emerged as the number one method for ransomware delivery, accounting for nearly 77% of attacks. This comes as no surprise given how much organizations rely on the web for day-to-day productivity, causing attackers to use it as their main vector for cybercrime.
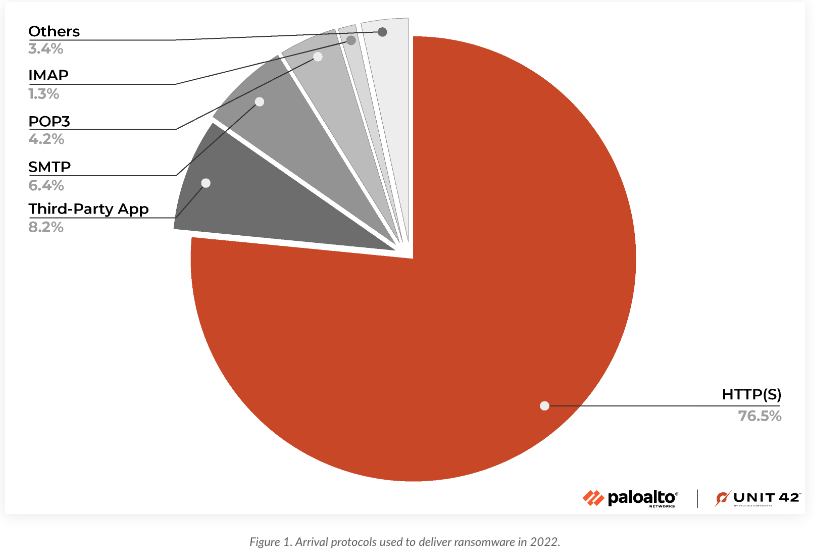
As threat actors continue to move to web-based ransomware attacks, there are two common techniques observed by Unit42. First, attackers quickly cycle through different URLs to host the same piece of ransomware. This aids them in avoiding detection by static web crawler databases. Additionally, they can use the same URL to deliver different ransomware variants, making their attacks more widespread. Unfortunately, attackers today have the ability to easily generate new URLs or take control of existing sites to use as hosting infrastructure for their ransomware payload, such as DNS hijacking, creating subdomains or paths under popular and legitimate social media and sharing services, and more. This has created a significant challenge for organizations with regards to preventing a ransomware attack.
With 66% of organizations affected by ransomware in 2023, it’s crucial that security vendors bolster their defenses to keep up with these advanced techniques used by attackers and protect their customers from a breach. To mitigate the sophistication of threat actors, Palo Alto Networks is continuously innovating on its Cloud-Delivered Security Services to help protect its customers from the latest and most advanced attacks, including ransomware. Our Advanced URL Filtering service leverages the power of AI to perform deep and real-time analysis of URLs, in addition to other critical web page attributes, i.e. page content, images, HTML code, etc., to detect and prevent unknown and highly-evasive web-based threats. To prevent web-based ransomware attacks, Advanced URL Filtering analyzes URLs in real time, identifying any words or blocks of text that frequently appear in malicious campaigns, or are reused by more recent active campaigns. In addition to using AI-powered models to analyze URLs, Advanced URL Filtering has recently released a “Ransomware Category” that helps customers better protect against websites known to host ransomware or malicious traffic involved in larger ransomware campaigns. With these innovations, Palo Alto Networks Advanced URL Filtering is the industry’s first web security engine to stop web-based ransomware attacks in real time.
To learn more about Palo Alto Networks research on web-based ransomware and the top campaigns and trends observed, read our Unit42 blog. Additionally, for more information on how Advanced URL Filtering can help ensure safe access to the web for your users and protect you from web-based threats like phishing and ransomware, visit PaloAltoNetworks.com and ask to be contacted by one of our experts.