For CISOs at today’s large enterprises, the single greatest risk is not a novel threat but the fundamental uncertainty of what exists within their own environments. As organizations accelerate the adoption of multicloud architectures and generative AI, security leaders must now manage a complex "network of networks" that traditional tools cannot comprehend. As a result, visibility gaps occur that can create an unquantifiable attack surface and prevent the consistent enforcement of security policies.
To effectively reduce these risks and enable the business, teams can now adopt an architectural approach. This multicloud security fabric provides a complete, real-time map of all assets and their interconnections across every cloud.
Translate Invisibility into Quantifiable Business Risk
A lack of complete visibility is not just a technical inconvenience; it’s a direct contributor to executive-level business risk. When you cannot see your entire estate, you cannot effectively protect it, which can lead to specific, board-level concerns. Every unknown workload becomes an unmanaged attack surface, and every unmonitored network path is a potential entry point for adversaries. This makes it impossible to consistently enforce Zero Trust policies, creating weak points and unchecked risk of lateral movement.
Manual discovery processes also introduce operational friction, slowing application deployments and positioning security as a roadblock to innovation. Without a complete and verifiable map of all assets and data flows, proving compliance becomes an insurmountable challenge, guaranteeing audit difficulties.
Replace Fragmented Tools with a Single Multicloud Security Fabric
Many security teams are forced to assemble an incomplete security picture from a collection of siloed tools. While each cloud provider’s console offers a partial view, these tools fail to illuminate the critical intercloud connections and application dependencies where significant risks reside. This fragmented approach does not scale and leaves dangerous blind spots between environments.
The solution is not another point product but an architectural shift: establishing a multicloud security fabric. This foundational layer sits above individual cloud infrastructures to create a single, authoritative source of truth. This fabric provides a complete map of your environment, delivering:
- Comprehensive Asset Discovery: Full visibility into all assets, from virtual machines to container workloads and AI applications.
- Full Network Topology Mapping: A clear model of all cloud-native networking constructs and how they are interconnected across cloud providers.
- Application-Centric Context: The ability to understand not just infrastructure components but how applications communicate with each other across cloud boundaries.
Achieve Complete Visibility with an Automated, Step-by-Step Approach
A multicloud security fabric provides unified visibility through a logical, automated process.
Step 1: Discover All Assets Automatically
The security fabric integrates cloud-native APIs to discover the entire multicloud estate. This includes traditional workloads, cloud-native gateways, Kubernetes clusters and the full AI stack, including large language models (LLMs) and their associated datasets.
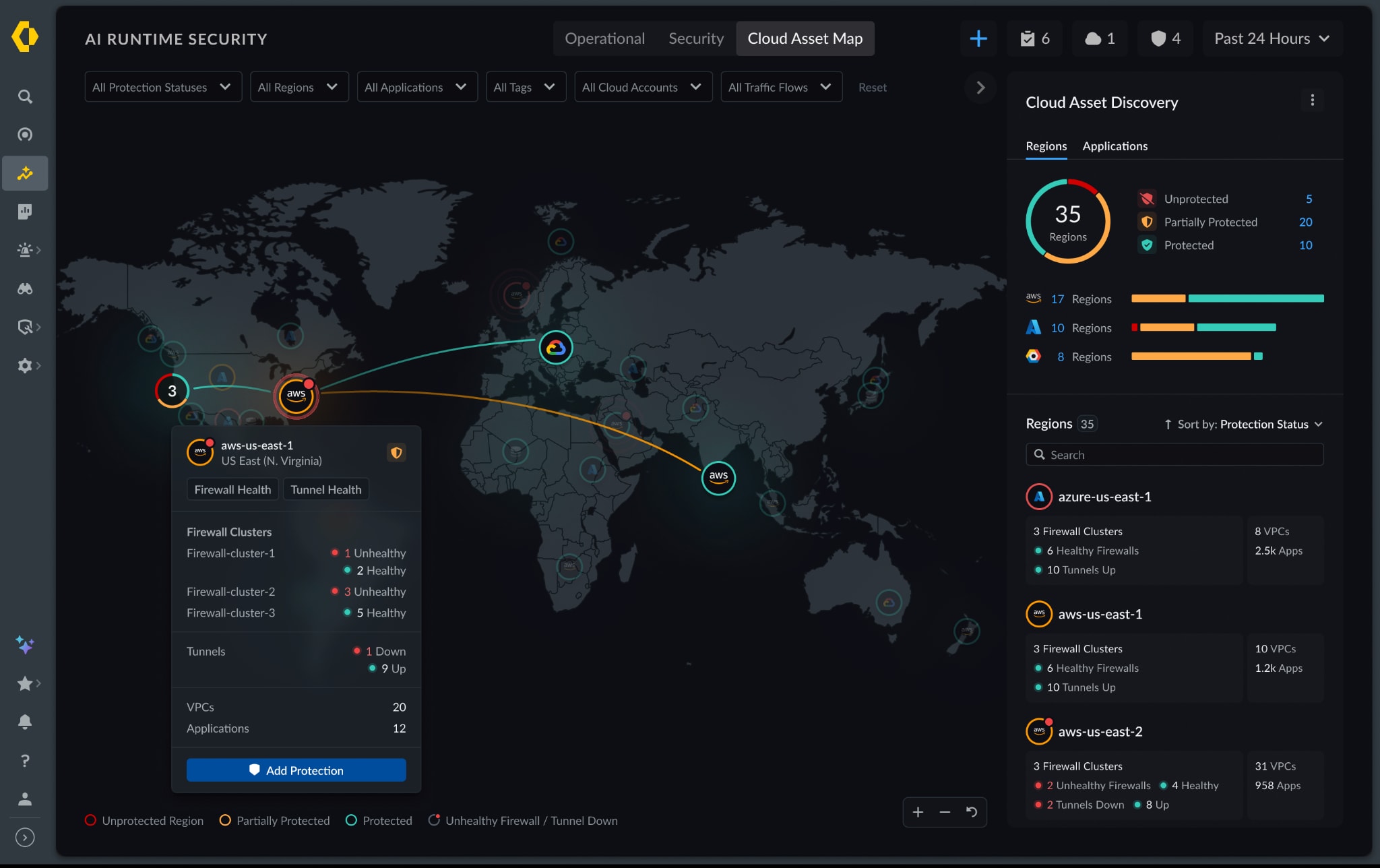
Complete discovery of the entire multicloud estate including workloads, gateways, containers and AI assets.
Step 2: Map Topology Dynamically
The security fabric moves beyond a simple asset inventory to map the dynamic relationships among assets and visualizes the end-to-end network topology, showing exactly how traffic is routed through constructs such as transit gateways and VPCs/VNETs across different providers.
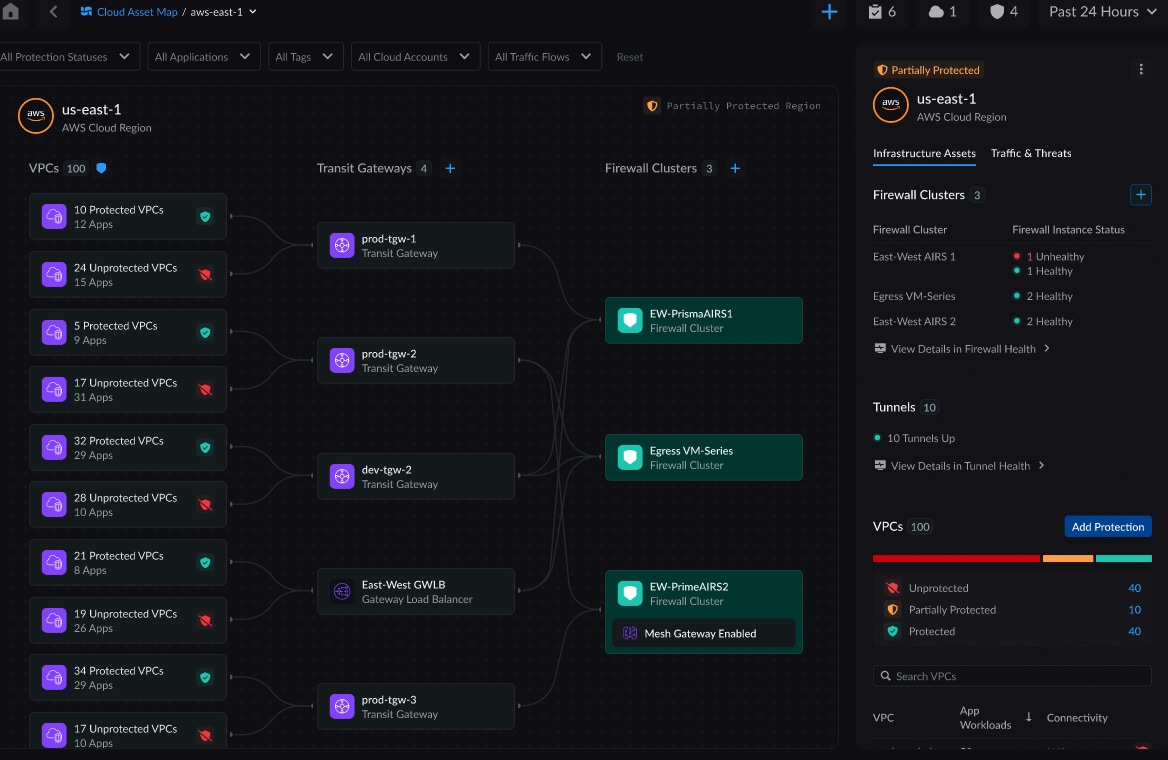
Dynamic relationship mapping among assets to visualize the end-to-end network topology beyond simple inventory.
Step 3: Identify Security Gaps
Discovery becomes actionable by highlighting both protected and unprotected assets. This unified visibility provides an immediate, risk-prioritized view of workloads and applications that lack required security controls, showing you precisely where to focus your efforts.
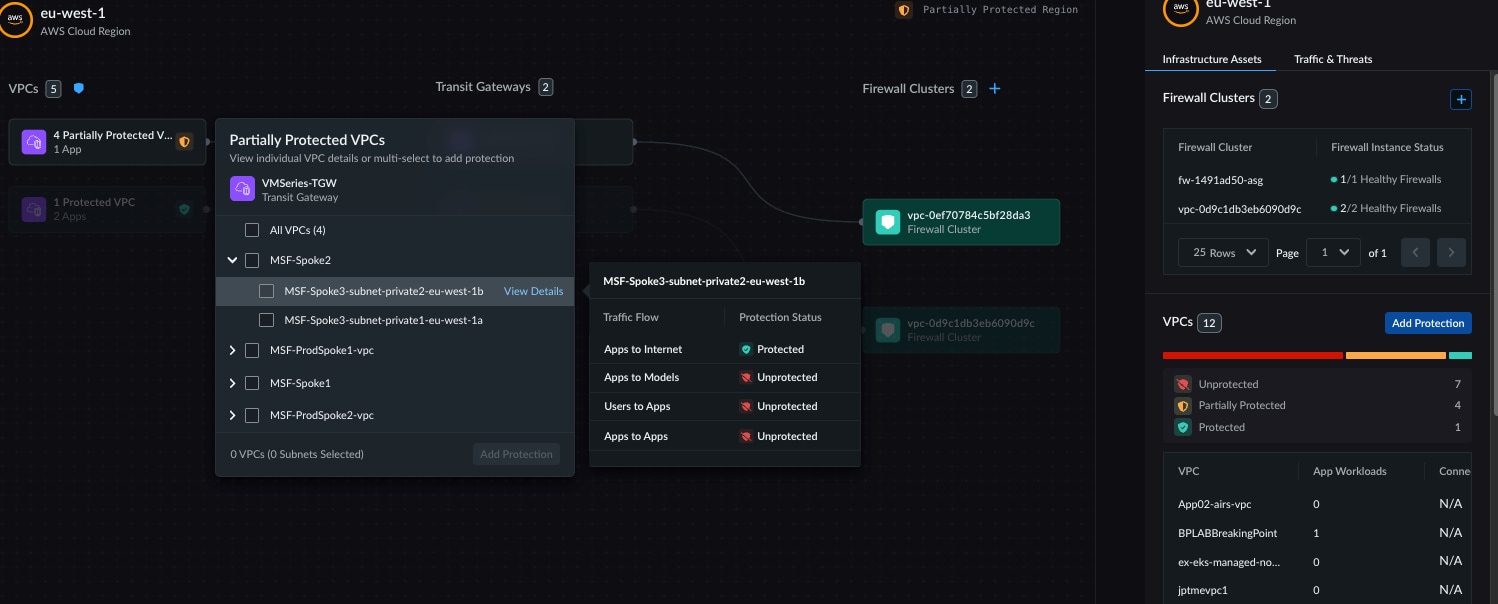
Actionable, risk-prioritized view of workloads and applications that lack required security controls.
Step 4: Monitor Continuously
Visibility is an ongoing need, not a one-time event. The security fabric continuously monitors for configuration drift and provides tools like a hop-by-hop cloud tracer for troubleshooting, ensuring the security posture remains intact.
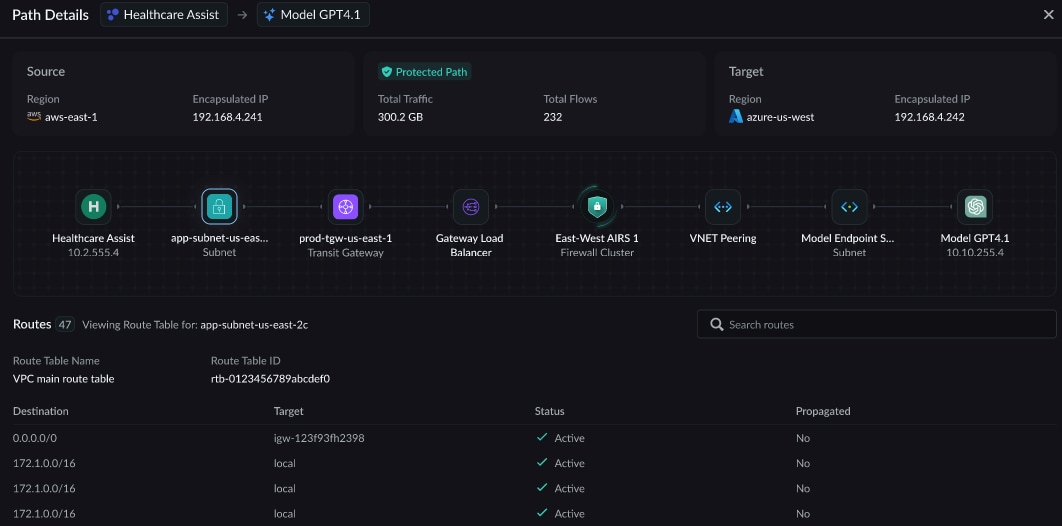
Continuous monitoring for configuration drift to ensure the security posture remains intact over time.
Drive Strategic Business Outcomes with Complete Visibility
Eliminating security blind spots translates directly into quantifiable risk reduction and strategic business advantages. By shrinking the unknown attack surface, you can consistently apply Zero Trust policies, significantly reducing the likelihood of a major breach. A complete, real-time map of your environment provides a single source of truth that transforms audit preparation into a routine reporting activity.
Operationally, discovery automation frees security teams from manual, error-prone tasks and allows them to secure new applications in minutes, not weeks. This efficiency, delivered through solutions like the Palo Alto Networks multicloud security fabric (MSF), transforms the security team from a barrier to innovation into a key business enabler. As a core element of our software firewalls, MSF allows your organization to adopt new technologies like generative AI with confidence and speed.
A Multicloud Security Fabric Helps Move from Foundational Visibility to Automated Action
A multicloud security fabric enables automated actions to help you achieve complete, real-time visibility to secure complex multicloud environments. With complete visibility of your entire estate, you can build the foundation needed to programmatically deploy security controls, ensuring that protection always keeps pace with development.
To understand the visibility gaps in your own multicloud environment, request a complimentary Cloud Network and AI Risk Assessment (CLARA). Our experts will help you identify your unprotected assets and map a strategy for achieving total visibility.