Container images workflows are simple. Any developer or DevOps engineer can easily pull and run images from external repositories, such as Docker Hub. As a result, many organizations increasingly depend on external code, open-source images, and packages that are pulled from different sources.
These images are built by various, sometimes malicious, individuals who might exploit them to embed malware in innocent-looking images for example.
Prisma Cloud’s image scanning identifies vulnerabilities and compliance issues in container images during the development process and prior to their deployment to production. While image static scanning is essential for container security, some malicious behaviors can only be observed when an image runs as a container. In order to effectively defend cloud native applications, security and DevOps teams must assess the behavior of a container in runtime, before starting to use the image and deploy it to live environments.
We are happy to announce the Prisma Cloud Image Analysis Sandbox. With this newest enhancement, Prisma Cloud can dynamically run and scan container images in a sandbox virtual machine (VM). This allows you to see suspicious findings detected when the container is running, such as malware, cryptominers or port scanning, as well as a full profile of the runtime behavior of the container.
Assess the Risk of an Image
Once the sandbox analysis is initiated, the image analysis sandbox mechanism runs the image for a defined amount of time, and traces all the events occurring on the running container. Using advanced heuristics on the collected events, Prisma Cloud detects suspicious behavior of the container.
Possible suspicious findings could be a detection of malware, found by an integration with Palo Alto Networks WildFire which is one of the leading and most advanced malware detection tools. Other findings are cryptocurrency miners, port scanning, suspicious ELF headers of a binary, unusual execution of files, and additional threats.
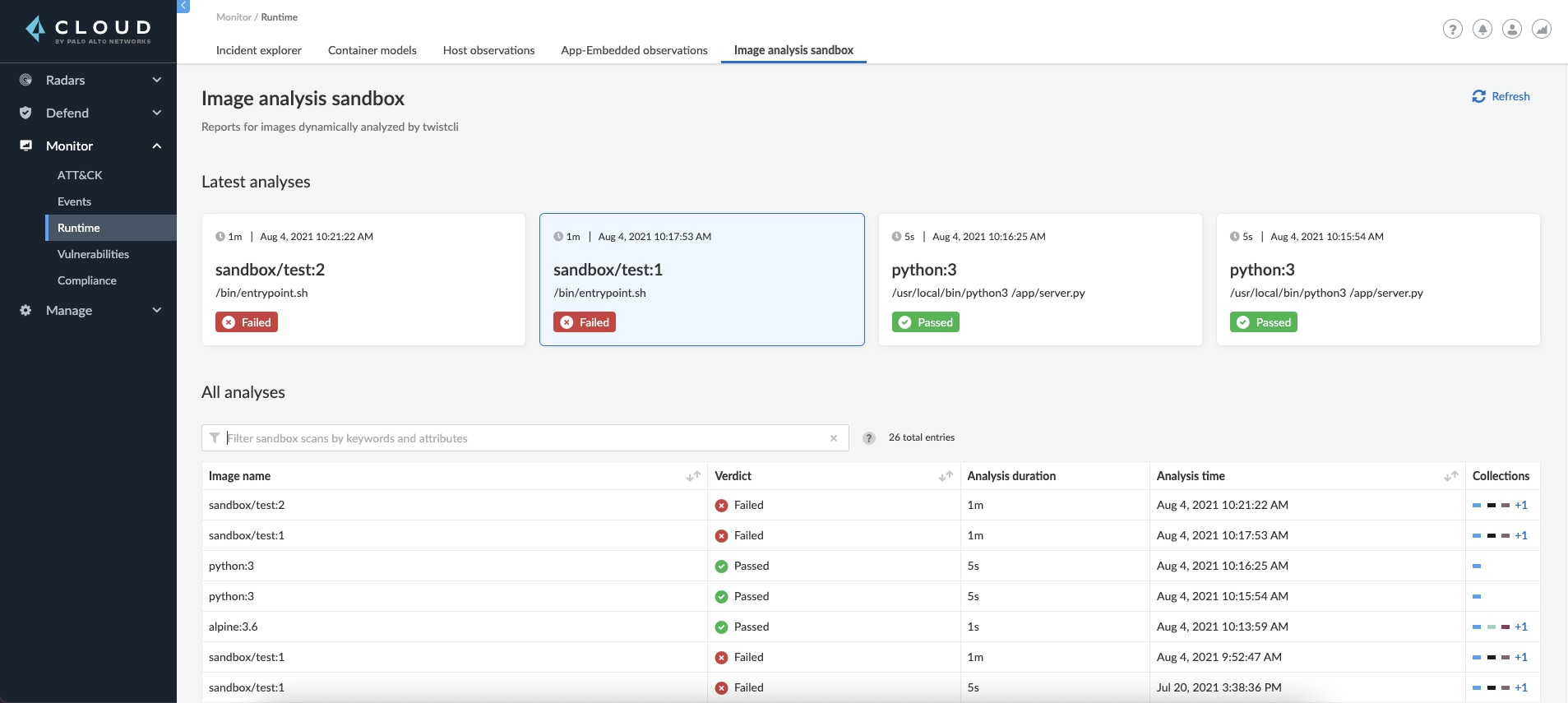
A suspicious finding is displayed to you with the appropriate severity and all its relevant details. Prisma Cloud determines the verdict of the image according to the findings to help you understand the potential risk level the image presents and decide if it is allowed to run in an open, networked environment.
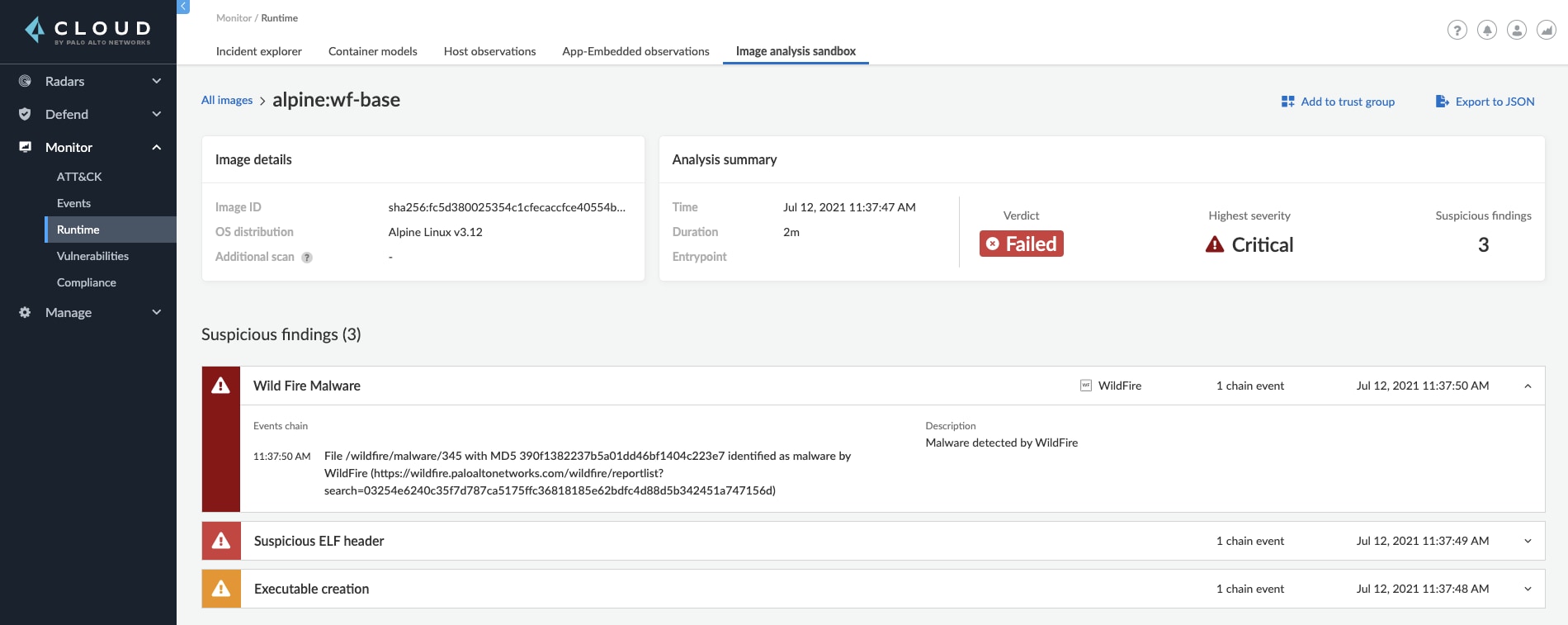
Get a Comprehensive Runtime Behavior Profile of the Image
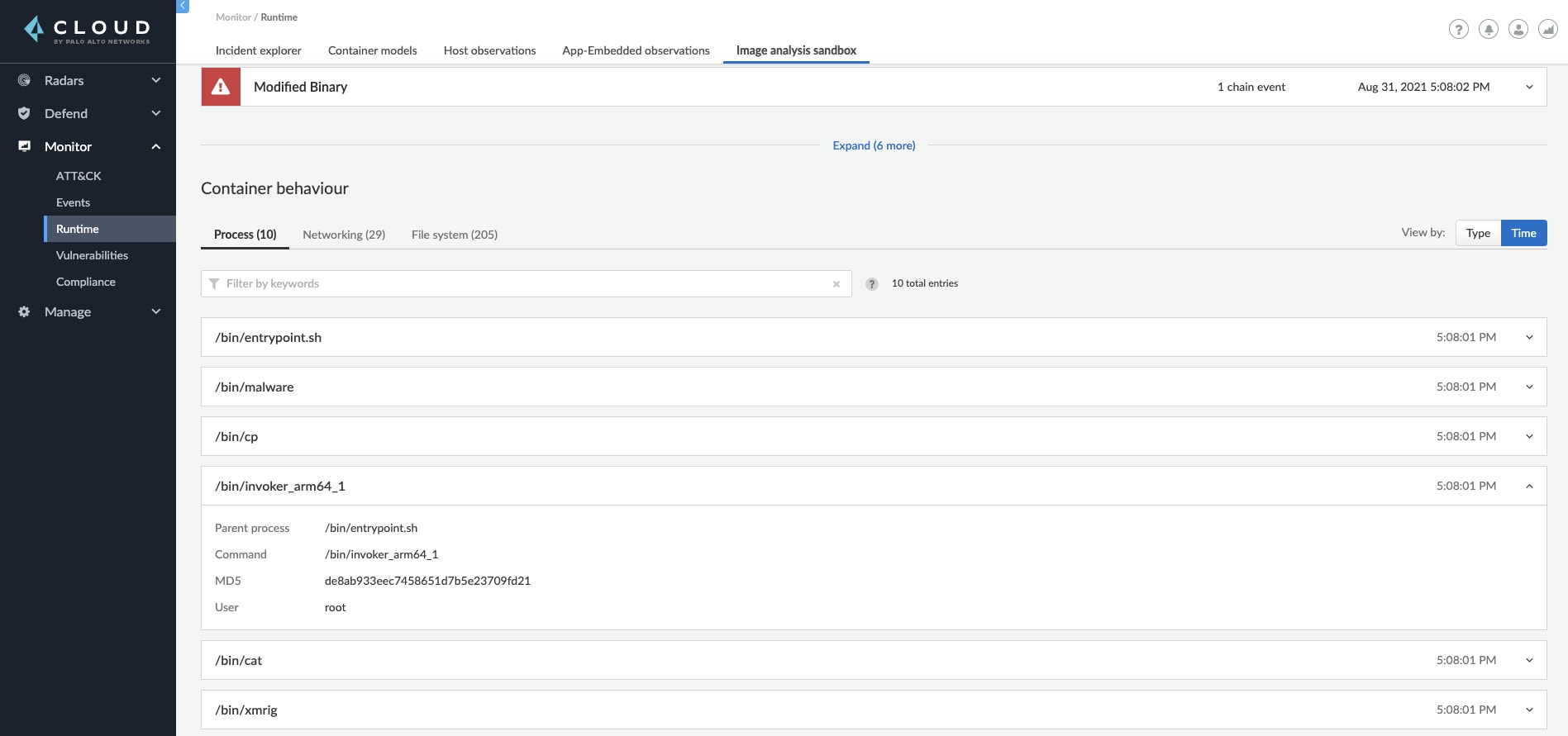
When analyzing an image using the Image Analysis Sandbox, you get the full picture of the container behavior. Prisma Cloud monitors and captures processes, network, and file system events that occurred while the container was running in the sandbox and shows them to you in a detailed overview.
Users can dive into the processes that were running on the container, displayed either by the type as a processes profile of the container, or by time, with each one of the process execution instances. Furthermore, you can explore the container networking activity, including its listening ports, DNS queries and the outbound connections performed. The outbound connections are also displayed on a world map to allow you to easily understand if the container was trying to reach an unusual location.
Incorporate Dynamic Analysis in Your Workflow
The image analysis sandbox is triggered as a command in twistcli, the CLI tool for Prisma Cloud Compute. This allows you to simply perform an analysis on-demand for an image you want to assess or incorporate it into your CI pipeline as a security gate in addition to static scanning for vulnerabilities and compliance.
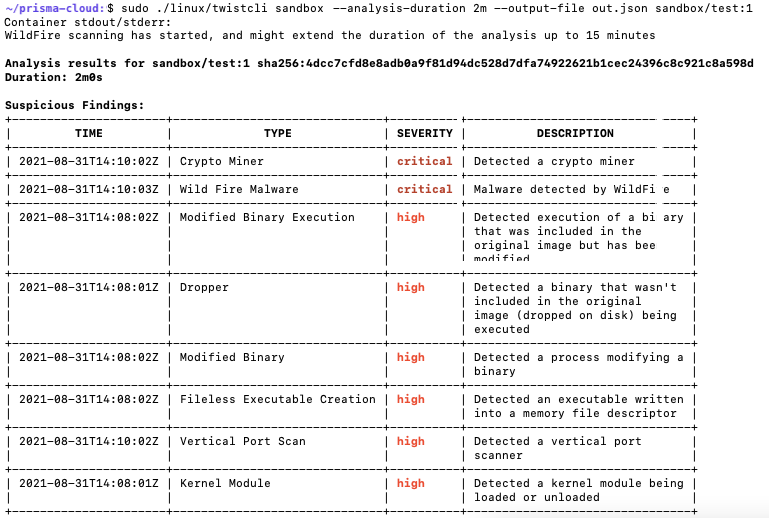
Image Analysis Sandbox in Action with an Example Image
Let's see an example of an image analysis sandbox in action. In our demo environment, we have triggered an analysis on an example image that ran for two minutes.
When the analysis was finished, the analysis report indicated 13 suspicious findings, one of them for the creation of a new executable on the disk /bin/invoker_prc.
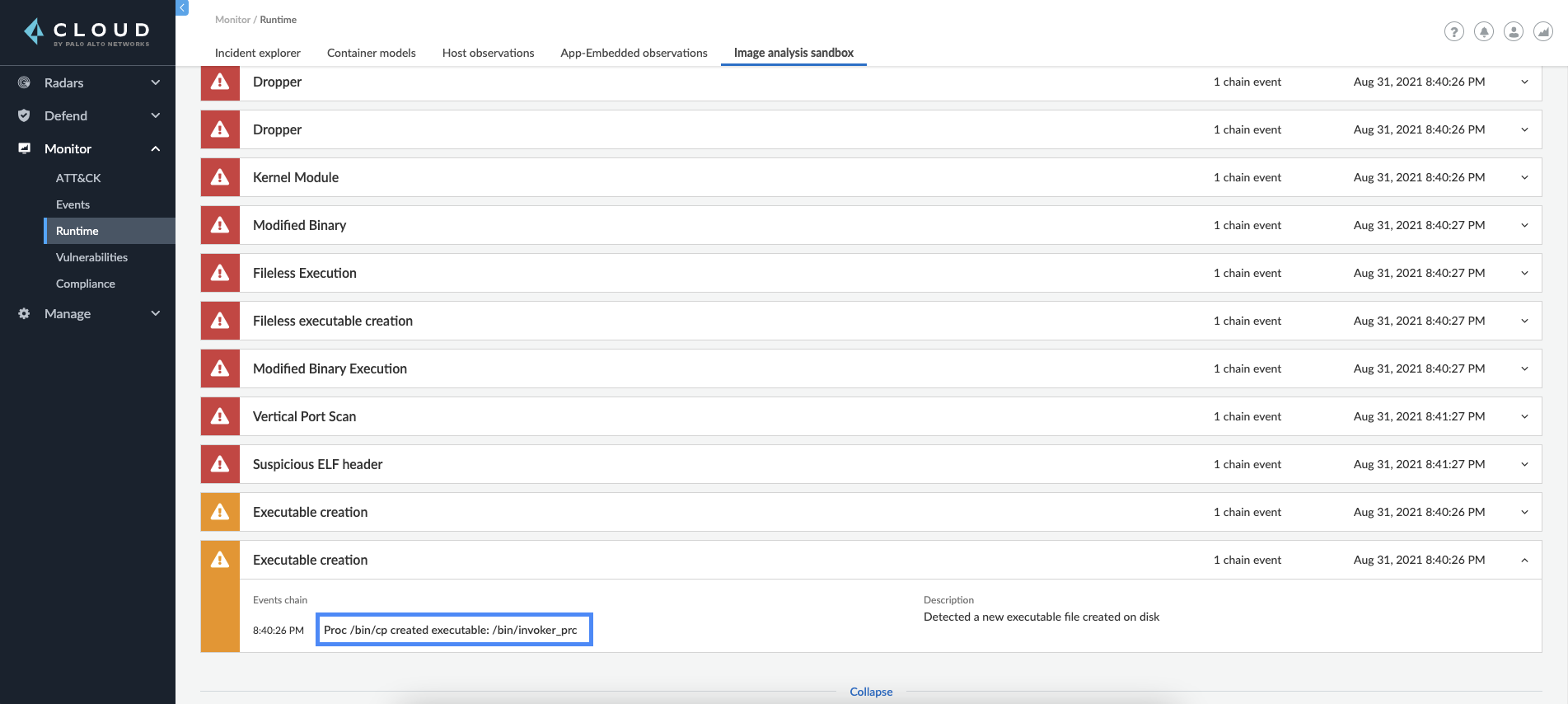
As we continue to review the results, we see a Dropper finding for the same process. Process /bin/invoker_prc, that didn’t exist in the original image, was also being executed.
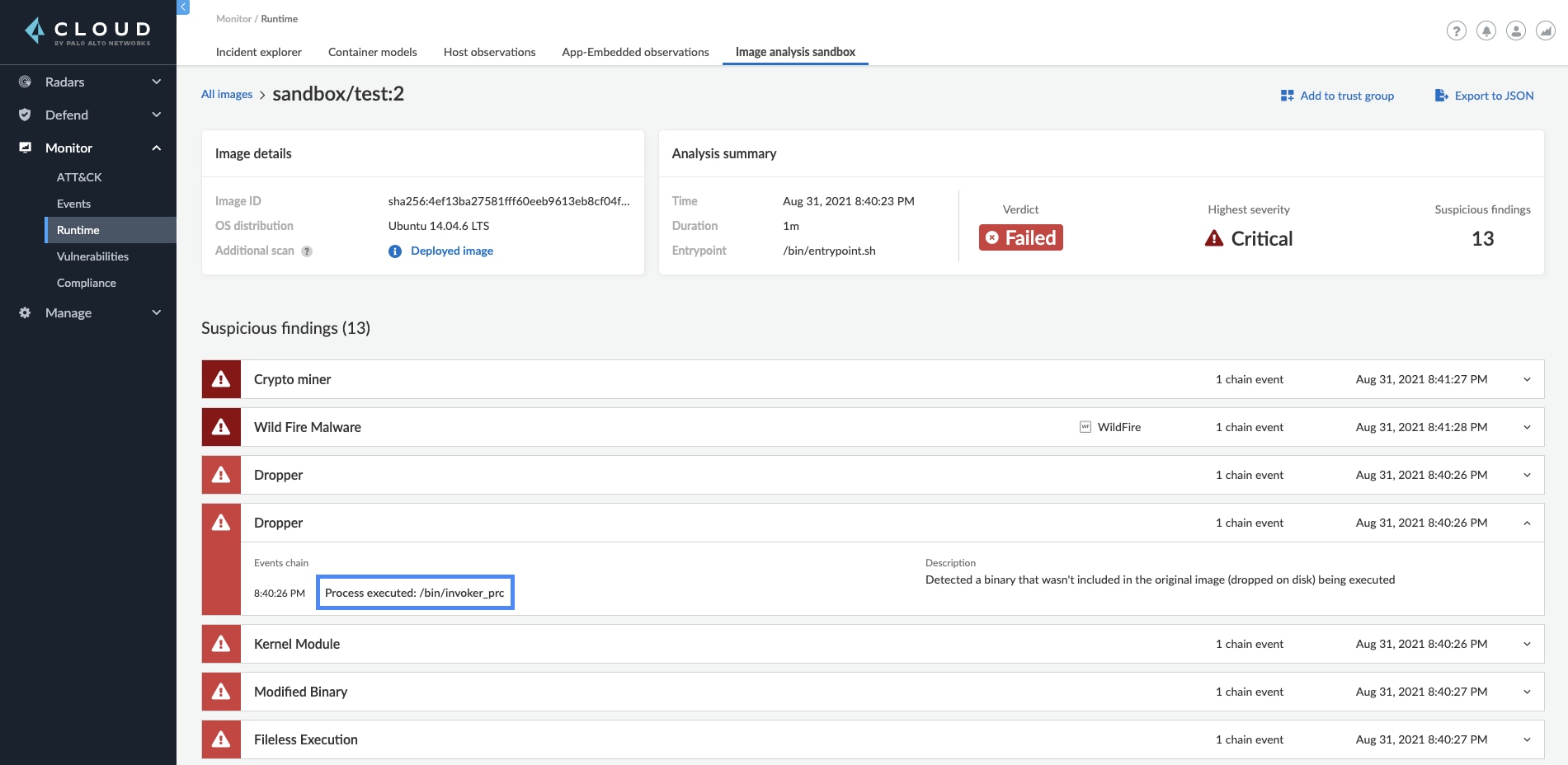
This alone lets us understand that this might be a malicious image. Further investigation into the container behavior section shows indications that the suspicious process tried to reach out to several outbound IPs and touched multiple files on the disk.
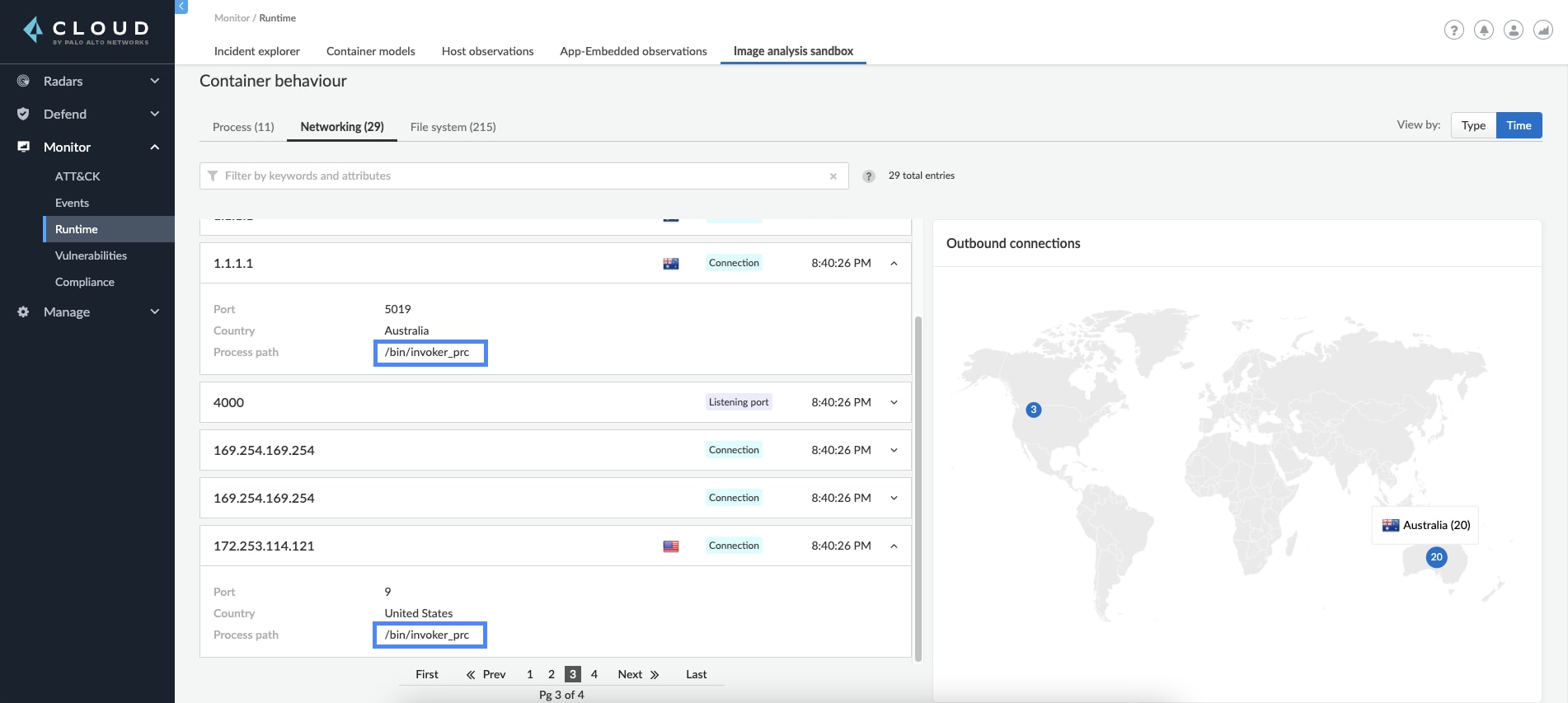
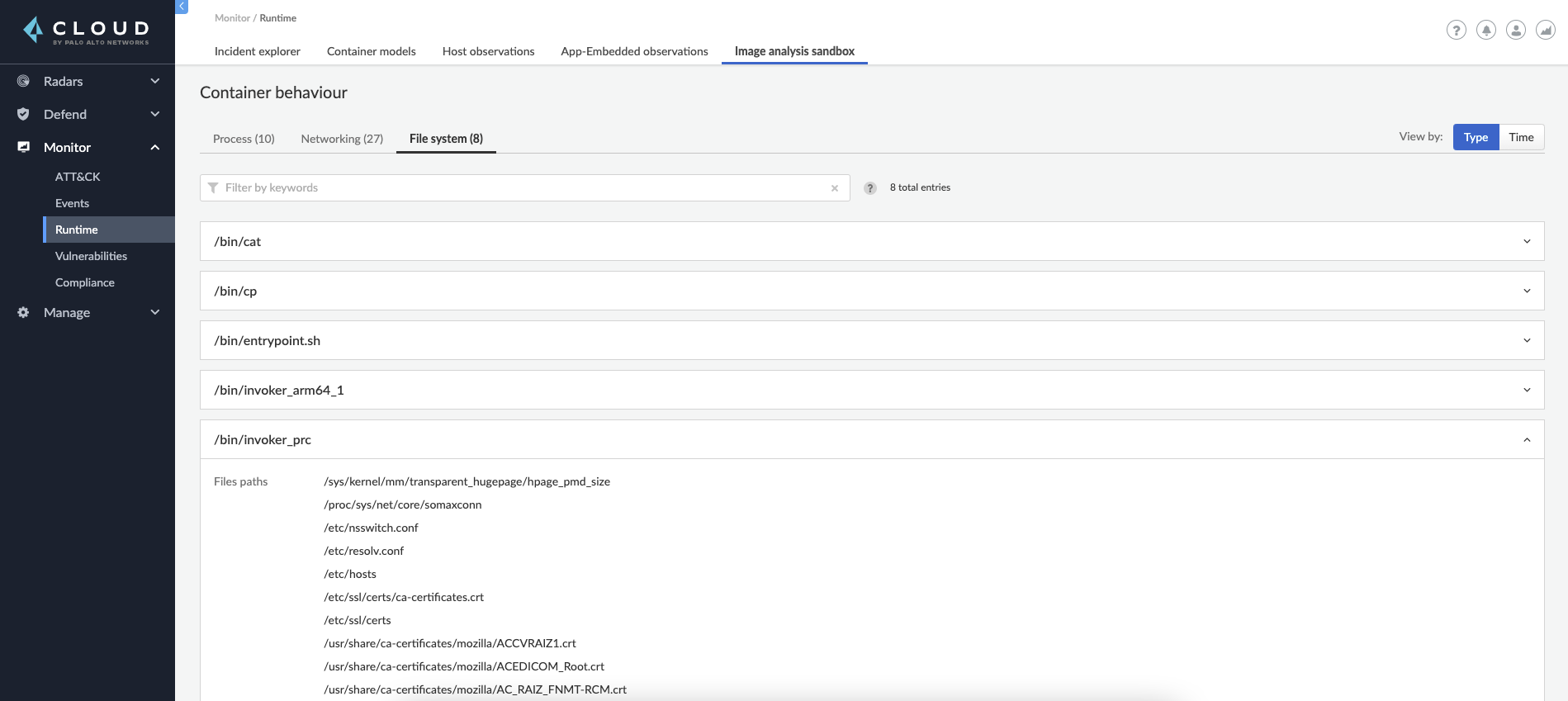
Reviewing the results for our example image leads us to understand that this is a malicious image that should not be used. Discovering it on the sandbox machine helped secure the environment by preventing us from running this image in production.
Get Started with the Image Analysis Sandbox
The Image Analysis Sandbox discovers hidden malware and suspicious behaviours in container images that would otherwise be discovered only if the image was already running in the environment. It also creates and displays a full profile of the container behavior at runtime. Understanding how an image will operate in runtime helps security teams decide whether the image is safe to use in live environments and shifts-left your organization’s security in the cloud.
Learn More About Containers
Whether you’re new to containers or a cloud-native veteran, The 2024 Definitive Guide to Container Security is your essential resource for understanding, implementing and mastering security in a containerized environment. This book-length guide lays out in-depth insights and practical advice to empower developers, DevOps, cloud teams and security professionals to effectively protect their cloud-native applications.