If you’ve ever questioned the importance of vulnerability management, consider these facts:
- 26,447 vulnerabilities were disclosed in 2023—1,500 more than in 2022.
- Three new vulnerabilities are discovered every 3 hours.
- 7,000 vulnerabilities had proof of concept exploit code
To make matters worse, attackers are wasting no time in taking advantage of this wave, exploiting vulnerabilities within 15 minutes of publication.
Does your team have a plan to effectively manage vulnerabilities in the cloud?
Challenges of Vulnerability Management in the Cloud
Coordinating vulnerability management across diverse systems and applications, including cloud-based infrastructure and third-party software, is inherently complex and time-consuming. Traditional vulnerability management tools struggle to keep pace with the dynamic and ephemeral nature of cloud environments, leading to gaps in visibility and coverage. This is especially true when you consider the lack of integration between security tools and development pipelines, which often result in delays in patch management and an increased window of exposure.
These challenges can be overcome with four simple best practices:
- Gain visibility across the application lifecycle
- Identify the most impactful vulnerabilities
- Take action and remediate vulnerabilities
- Monitor and report risk burndown
This post will focus on the first two best practices. Let’s get started…
Vulnerability Best Practice #1: Gain Visibility Across the Application Lifecycle
Visibility is the most logical first step for most cybersecurity practices because it provides essential insights into an organization's digital environment. Understanding what assets exist and related vulnerabilities across the application’s lifecycle serves as the foundation for informed decision-making and proactive security measures.
Additionally, visibility into cloud vulnerabilities fosters transparency and accountability, enabling stakeholders to make informed decisions about risk management and mitigation strategies. It also enhances collaboration between security, development and other stakeholders by providing a common understanding of the vulnerability landscape.
By implementing robust scanning and assessment mechanisms, users can systematically identify vulnerabilities within their systems, ensuring that no workload is invisible or hidden from the program. This can be achieved with a myriad of techniques, such as agentless and agent-based scanning and ingesting data from 3rd party platforms.
An ideal solution should support both scanning methods, especially if you have cloud applications and workloads hosted on public and private cloud environments. Each approach offers benefits that, when combined, provide the most complete levels of security.
Agentless vulnerability management reduces the operational overhead associated with deploying and managing agents on numerous workloads, simplifying the management process. It also enables organizations to assess and monitor assets that cannot support traditional agents, such as legacy systems or network devices.
Agent-based scanning solutions provide continuous monitoring and real-time visibility into vulnerabilities and threats. They can also collect additional data and metrics from applications, enabling more accurate risk assessment and prioritization of vulnerabilities.
Prisma Cloud’s Approach to Identifying Vulnerabilities
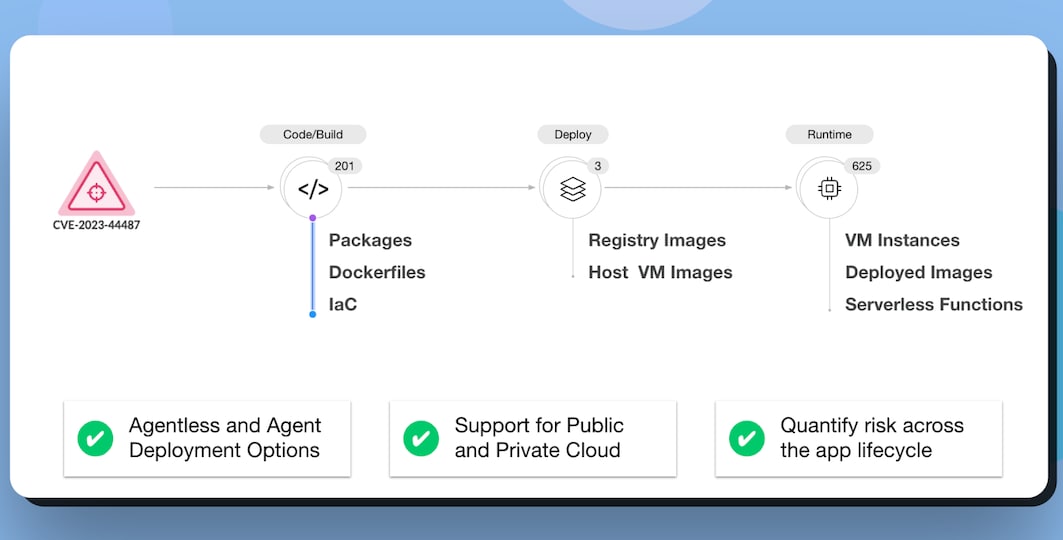
The Prisma Cloud Code to CloudTM platform enables users to gain visibility into how a vulnerability is affecting their entire application lifecycle. This view gives visibility into vulnerabilities from code to cloud.
In the code stage the system identifies all packages, dockerfiles and IaC templates. In the deploy stage it scans VM images and container images in registries. Then in runtime it identifies vulnerabilities in VM instances, deployed container images and serverless functions, giving organizations a complete picture of all vulnerabilities as well as how they’re connected.
Users have the flexibility to choose from both agentless and agent-based scanning methods, so they can customize their protection based on their specific needs.
Best Practice #2: Identify the Most Impactful Vulnerabilities
With comprehensive visibility across the application lifecycle established, it’s time to prioritize the issues that pose the biggest threat.
The reality is, not all vulnerabilities are created equal—some pose a significantly higher risk to our applications, systems and data than others. That being said, there's no single and absolute truth to vulnerability prioritization, since it’s affected by specific vulnerability, risk, business and environmental factors. This makes it imperative to prioritize remediation efforts based on the potential impact of a vulnerability on your unique environment.
Here are some key considerations:
- Severity: Critical and High Severity vulnerabilities should be prioritized over low severity vulnerabilities.
- Exploitability: Consider the likelihood that a vulnerability will be exploited. Vulnerabilities with known exploits readily available in the wild should be prioritized with urgency.
- Potential Damage: Workloads exposed to the Internet have a higher likelihood of being targeted for an attack and should be prioritized accordingly.
- Affected Assets: Assess the number of workloads affected by the vulnerability. Focus on fixing vulnerabilities that will have the greatest impact.
By focusing their attention where it matters the most, organizations can enhance their security posture and reduce the risk of cyber incidents.
But how can we implement this practice effectively within the context of our newfound visibility across the application lifecycle?
Prisma Cloud’s Approach to Prioritizing Vulnerabilities
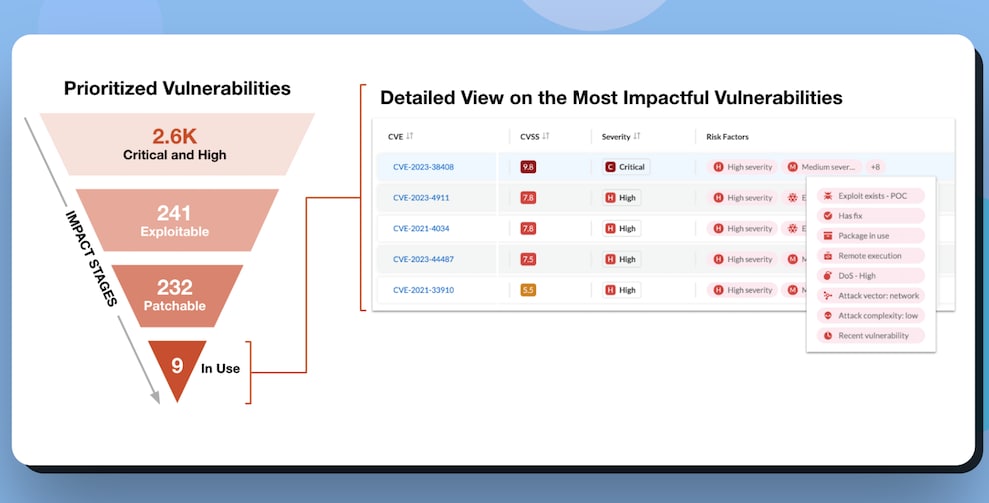
Prisma Cloud makes it easy to identify and prioritize the most critical vulnerabilities so that you can address the highest risks to your environment first.
The Code to Cloud platform provides a funnel view to help filter vulnerabilities into only the most critical CVEs. It then narrows it even further to only those that are exploitable. With insight into which ones can be exploited, it’s possible to identify those that can be patched or fixed by your team. The system also highlights the details of vulnerabilities that are actively being used by packages in your environment, including threat intelligence and known exploits, so you can start taking action.
Utilize the insights gained from comprehensive visibility to prioritize vulnerabilities based on their potential impact. It’s also important to collaborate closely with stakeholders, including security and development teams and business leaders, to align on prioritization criteria and ensure that remediation efforts are focused on addressing the most critical vulnerabilities first.
Learn More
Achieving comprehensive visibility and prioritization are just the first steps in building an effective foundation for vulnerability management.
To learn more about how Prisma Cloud can help your organization manage vulnerabilities from code to cloud, see how we can help you find and fix the XZ Utils vulnerability.