Ahh the coffee shop: the aroma of freshly roasted coffee, friendly baristas who know your name and a third place to catch up with friends and colleagues. Now, with zero trust architectures, coffee shops are a place for remote workers to get things done without compromising on security.
CIOs and CISOs often wonder why they can’t build their offices like coffee shops to help reduce spending. The general perception is that the coffee shop model only provides minimal networking services, often perceived as enough for small remote locations.
Additionally, this model forces all network users to be treated as untrusted guests, eliminating any implicit trust gained by being on the network, a net security benefit. Employees access company resources securely through their remote access solution, just as they would from their home office. At the branch, all that is required is an authenticated Wi-Fi service and a terms and conditions splash page.
Spilling the Beans: Three Coffee Shop Network Model Shortcomings
The coffee shop model's perceived cost savings are alluring to CIOs and CISOs, but the viability of this approach quickly falls apart upon further inspection. Here are three ways the coffee shop network model falls short.
1. You still need a reliable and segmented network.
Shared office workspaces aside, every enterprise-managed location requires a network footprint—including SD-WAN, a firewall, router, switch and Wi-Fi access points—to provide reliable connectivity to branch users and devices. The edge network appliance terminates one or more WAN connections and provides isolation between network segments. Even our smallest customers operating userless locations, such as ATM locations, maintain these requirements.
With the coffee shop model, enterprise-level network requirements are too often ignored, and everything is treated like a home office or someone else's guest Wi-Fi: uncontrolled, unrestricted and unreliable.
2. You lose application visibility and traffic prioritization.
When moving to a coffee shop model, clients now build tunnels—including IPsec, SSL and DTLS—to the security service edge (SSE) to provide secure access to internal apps, SaaS apps and web browsing destinations. These tunnels obfuscate the underlying application, restricting the network edge's ability to provide effective application prioritization, connectivity and performance guarantees.
The network is unable to differentiate between low-priority traffic like OS updates, backups and social media, from critical revenue-generating traffic, like ERP data, point-of-sale system transactions, and your executive team's critical Zoom calls. In any enterprise, traffic types have differing business priorities, and your network design needs to reflect these priorities to ensure business continuity.
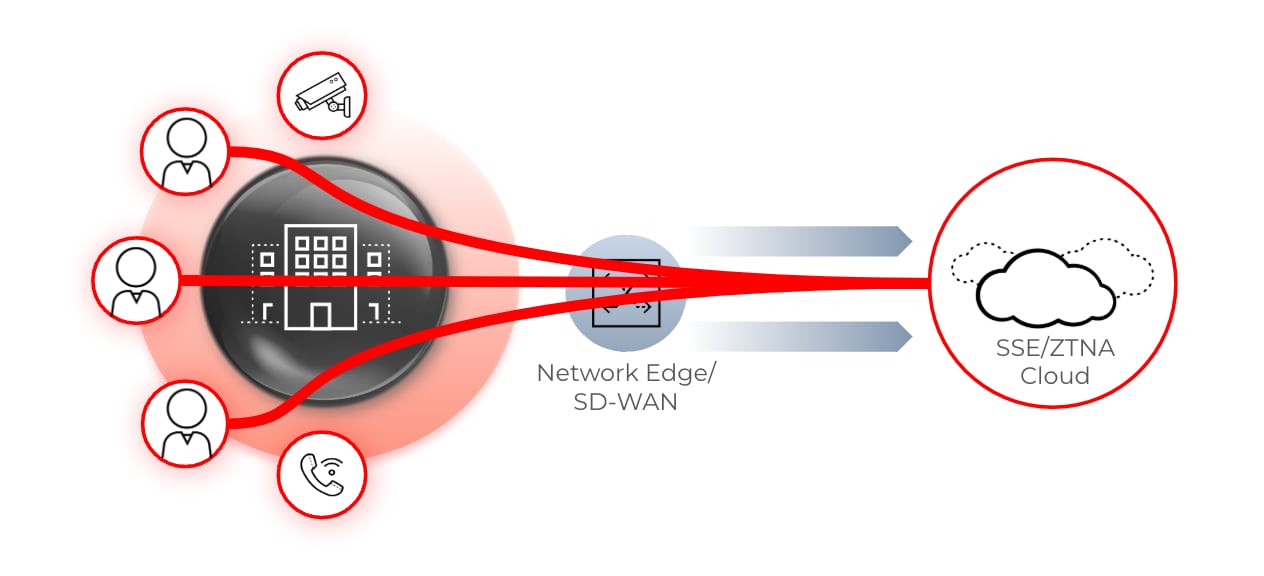
Figure 1: Client SSE tunnels obfuscate applications from the network.
3. Your IoT devices are incompatible with the coffee shop model.
IoT devices are pervasive across all enterprise-managed locations; security cameras, printers, badge readers and room sensors are needed even in the smallest of workspaces. Most IoT devices do not support SSE clients or proxy configurations, making them incompatible with the coffee shop model. Traditionally, IoT devices are segmented in isolated VLANs and their traffic is tunneled to the closest data center firewall, a traffic pattern that requires enterprise infrastructure to support.
Applying Coffee Shop Learnings to Design a Zero Trust Branch with SASE (SD-WAN + SSE)
When designing a zero-trust branch with learnings from the coffee shop model, the primary underlying goals are to reduce costs and risk. An evolved branch model and SASE can achieve these goals.
Traditional network designs stop at 802.1X/NAC authentication and do not provide the level of security required by today’s enterprises. Instead, zero-trust security controls must be installed between users' communication and internal and external applications. From there, continuous security inspection and continuous trust verification, including IoT protections, must be applied to minimize risks without adding complexity.
For most organizations, the solution is to adopt SASE as part of their zero-trust architecture, helping to reduce costs and eliminating implicit trust. The following are three design recommendations for modernizing your branch with SD-WAN and SASE.
1. Adopt SD-WAN and the thin branch model.
When deployed at the network edge, SD-WAN provides network resiliency across multiple WAN connections, autonomous connections to multiple SSE points of presence, and network and application segmentation between VLANs.
Prisma SD-WAN’s built-in zero touch provisioning makes your network easy to manage, regardless if you have ten sites or thousands of sites. Prisma SD-WAN enables enterprises to minimize their branch hardware footprint and simultaneously accelerate deployment with zero touch provisioning, increase visibility with analytic dashboards, and streamline operations with Autonomous Digital Experience Management. Full transparency of operation down to the application flow eliminates guesswork and fuels operational AI use cases with rich structured data. SD-WAN programmatically improves resilience, streamlines operations and provides consistent security.
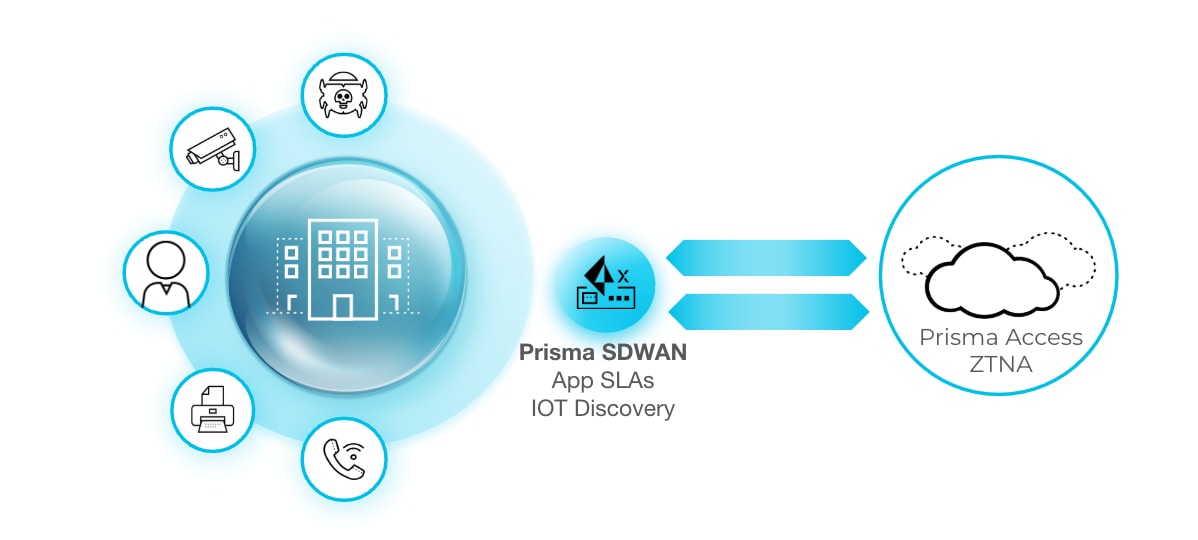
Figure 2: The Zero Trust Branch with Prisma SASE.
2. When on-premises, eliminate SSE client tunnels to maximize application resiliency while maintaining zero-trust client protections.
When clients are on-site, connectivity to the SSE layer is best handled by the SD-WAN and network layer, which has full control and visibility across all WAN connections. Clients can easily determine when they are connected to a trusted network using internal host detection, which enables user-ID authorization and continuous trust verification.
Because the branch leverages SASE, Prisma Access provides identity-based continuous security inspection. The network layer now has application visibility, so application SLAs are applied on all paths to maximize uptime and provide autonomous resilience to brownouts.
Prisma SD-WAN application SLAs identify, prioritize and monitor all applications to help ensure client-to-server application connectivity and performance. Prisma SASE App Acceleration reduces application latency and increases performance by up to five times, improving user experience.
3. Leverage SSE to secure ALL branch traffic, including headless IoT.
Given the inherent security risks associated with IoT, protections are applied in two steps. First, headless IoT devices are isolated into their own VLANs based on device type and risk profile. Second, IoT traffic is routed through Prisma Access, where it can be further secured.
IoT devices are inventoried, posture checked, and assessed for risk against device-specific CVEs using the Enterprise IoT subscription and additional telemetry from Prisma SD-WAN. IoT traffic is continuously inspected for noncompliant behavior with device-specific behavioral analysis. Bidirectional traffic flows of all types are secured using the zero trust policy in Prisma Access that uses User-ID, App-ID and Device-ID constructs.
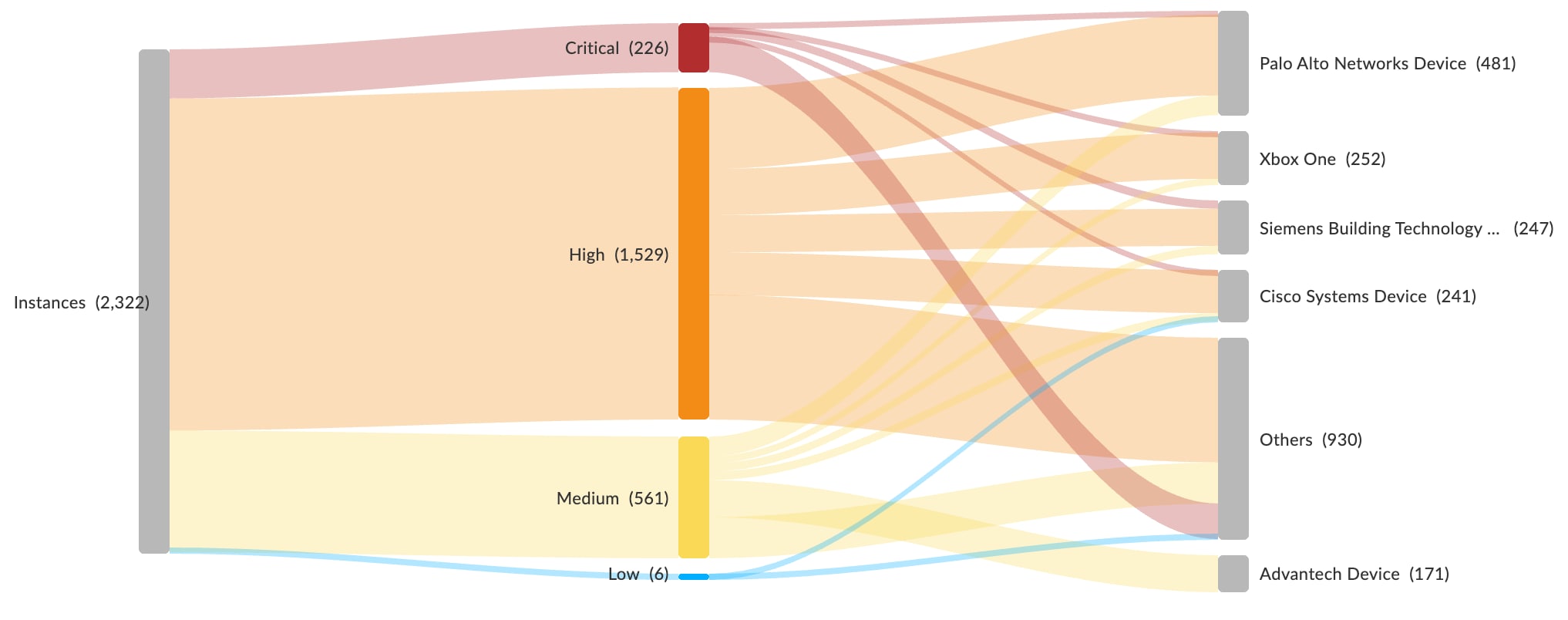
Figure 3: Identify IoT vulnerabilities and block threats with integrated Internet of Things (IoT) security.
Build Your Office as a Zero Trust Branch, Not a Coffee Shop
Conceptually, the coffee shop model is alluring, but does not meet enterprise standards for even the smallest of branches. Security, business continuity and supportability remain critical needs, and these needs can be met at scale through proven solutions.
Adopting a zero-trust branch architecture using Prisma SASE offers organizations a cost-effective, secure and future-proof solution to branch modernization without the pitfalls and oversights of a coffee shop design.
As I finish this blog post, I’m working in a coffee shop where the espresso machine is deafening, my table is uncomfortable to sit at for more than 15 minutes, and the constant stream of customers offers little privacy. Also, my guest Wi-Fi connection has been unreliable at best. Maybe coffee shops aren’t the best place to get work done after all?
Contact us today to learn more.