 A legacy security information and event management (SIEM) system at an oil and gas company was overwhelming the SOC with alerts. The SIEM system could only ingest a limited number of data sources, which reduced visibility into potential security threats. By replacing its SIEM with Palo Alto Networks Cortex XSIAM, the company saw rapid, meaningful change across its SOC.
A legacy security information and event management (SIEM) system at an oil and gas company was overwhelming the SOC with alerts. The SIEM system could only ingest a limited number of data sources, which reduced visibility into potential security threats. By replacing its SIEM with Palo Alto Networks Cortex XSIAM, the company saw rapid, meaningful change across its SOC.
Too many alerts put security analysts on edge
For the last two decades, SIEM solutions provided a robust foundation for cybersecurity threat detection. But SIEM tools weren’t designed to defend against aggressive, automated attacks launched by modern adversaries.
A US-based oil and gas company found this out the hard way, as a legacy SIEM bombarded its SOC with alerts. Overwhelmed, the team brought in a managed security service provider (MSSP) to help mitigate the overload— but because the SIEM had a 90% false positive rate, the service offered little relief.
“The rule is, you investigate every alert,” one of the company’s security leaders explains. “Which created a very inefficient process.”
Alert overload wasn’t the only shortcoming of its SIEM. Onboarding new data sources into the system was a cumbersome and resource-intensive process, which ultimately limited the number of key security data sources being ingested. This left a visibility gap into potential risks and extended investigation times. After an incident occurred, analysts had to manually correlate events using data siloed across disparate product dashboards. Without a significant change, the company was on a potential path to security analyst burnout.
"Ingesting data into our prior SIEM required a lot of work—which could easily go off track if complex configuration wasn’t done correctly.”"
IT security operations supervisor
An evolving threat landscape requires an AI-driven SOC
As the company grew, it needed to uplevel its threat intelligence with more visibility into attacks. It also wanted to empower security analysts to do what they do best and free them up from spending hours investigating false positives.
Incremental updates wouldn’t be enough. The company needed a transformational approach that met these requirements:
- The ability to ingest more data sources faster and more easily for expanded visibility.
- A solution that didn’t inundate its SOC with false positive alerts.
- A single platform experience that allowed them to progress toward a best-in-class SOC with advanced customization, automation, threat intelligence, and more.
In order to meet these requirements, security teams use the full capabilities of artificial intelligence (AI) to augment and complement their efforts. Advanced analytics and AI can significantly reduce the time teams spend processing massive amounts of data and developing critical security insights.
SOC transformation doesn’t have to be painful
Security veterans are well-versed in the difficulty of transitioning to a new platform. As the company’s security leaders evaluated Palo Alto Networks Cortex XSIAM for extended security intelligence and automation management, they also considered keeping and upgrading their existing SIEM, thinking it might be less disruptive. When they learned the upgrade process would take extensive time and effort, that was no longer an option.
Not only did Cortex XSIAM meet the company’s requirements for data sources, ingestion capabilities, and ease of use, but its small security team was able to get it up and running—fast.
The security operations supervisor and one other employee made the initial transition themselves. “We switched our SOC to Cortex XSIAM over a single weekend during Christmas break,” he recalls.
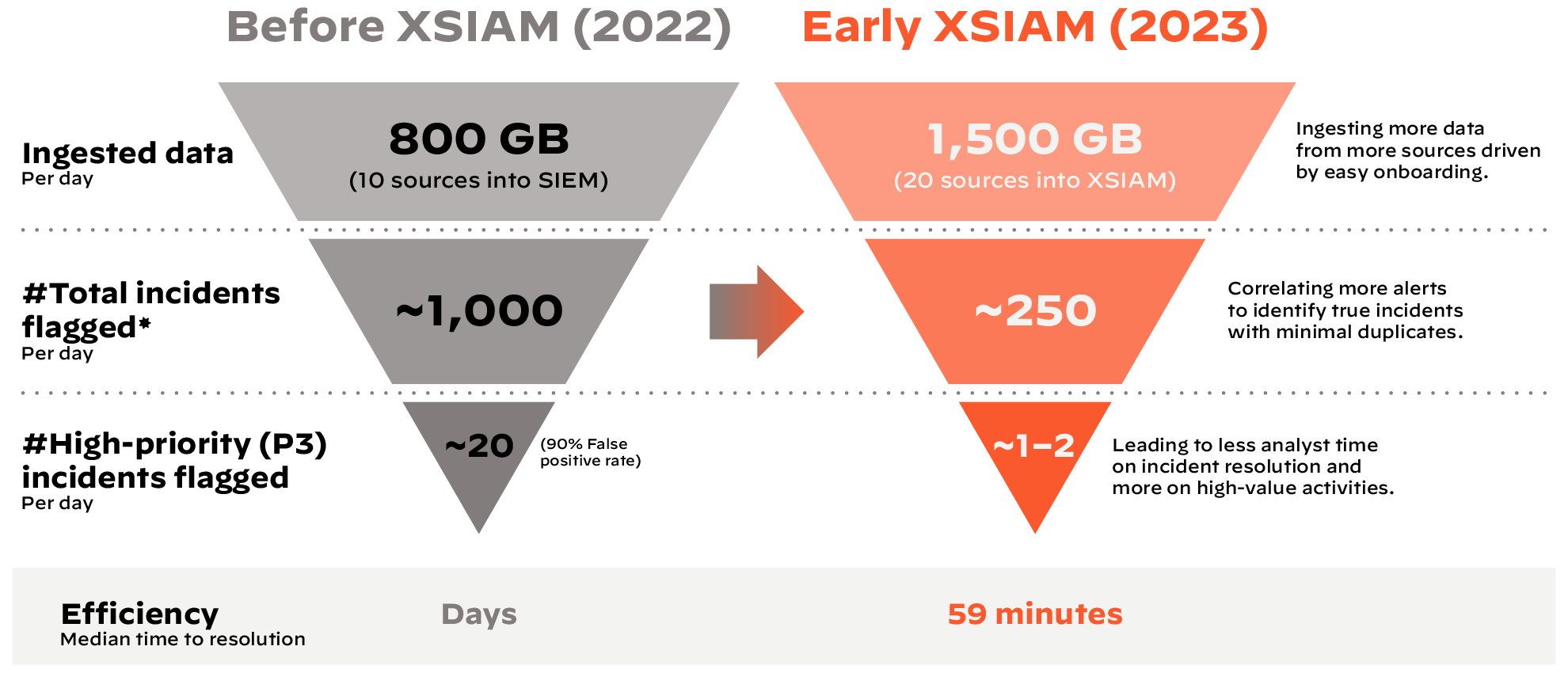
*Incidents flagged = potential security events flagged that require automated or manual investigation. Real-time investigations Closure = incidents remediated in less than 60 minutes after detection.
Analyzing more data, with fewer headaches
The team was able to configure new data sources—such as playbooks, correlations, and dashboards—in a few clicks with the XSIAM onboarding process.
“[For the prior SIEM], I had to go through their 3-day data admin training,” the security leader says. “For Cortex XSIAM, you just need to download the marketplace add-on. You don’t have to worry about anything.”
 The company did not run any automation playbooks with its legacy SIEM, but now runs multiple playbooks with XSIAM to reduce analyst workload and improve security outcomes. Plus its ingestion capabilities doubled right out of the gate, from 10 sources to 20. XSIAM can ingest data well beyond traditional security logs from network and cloud, along with data from containers, commercial off-the-shelf software (COTS) and non-COTS applications, system configurations, and more.
The company did not run any automation playbooks with its legacy SIEM, but now runs multiple playbooks with XSIAM to reduce analyst workload and improve security outcomes. Plus its ingestion capabilities doubled right out of the gate, from 10 sources to 20. XSIAM can ingest data well beyond traditional security logs from network and cloud, along with data from containers, commercial off-the-shelf software (COTS) and non-COTS applications, system configurations, and more.
The team can detect, prevent, and respond to more potential threats in less time thanks to the greater insight and expanded visibility provided by XSIAM. AI within XSIAM normalizes data and stitches together many points of view from the same event into a single enriched log line for a cohesive, holistic view.
Better alert quality helps analysts identify true threats faster

Cortex XSIAM reduced the company’s false positive rate from ~90% in the prior SIEM to virtually none, allowing analysts to correlate more alerts with actual incidents
While their legacy SIEM provided some customization, XSIAM equipped the security team with meaningful custom detections right out of the box. They’re now able to customize alerts on all endpoint and network data.
That came in handy when one of the company’s vendors got breached and began sending phishing emails. The SOC was able to detect the breach within minutes and prevent an attack on its systems.
“We knew about the breach before they did, because we were ingesting the log source into XSIAM and had tuned the alert,” the company’s security analyst recalls. “We wouldn’t have been able to do that without XSIAM.”
The team is able to identify, respond to, and resolve legitimate threats faster than ever before by eliminating data silos and consolidating:
- Endpoint detection and response (EDR)
- Security orchestration, automation, and response (SOAR)
- Attack surface management (ASM)
- Identity threat detection and response (ITDR)
- Threat intelligence platform (TIP)
- SIEM
Better analytics, driven by AI, allow analysts to focus on higher-value activities
Cortex XSIAM leverages machine learning (ML) and artificial intelligence to automate activities that previously mired analysts in repetitive tasks, allowing them to focus on more strategic and higher-impact needs. Analysts no longer spend hours sifting through trivial data or piecing together an incident timeline.
“XSIAM is excellent with stitching,” the company’s security leader explains. “You can see the entire causality chain for an incident in one place. Before, I’d have to go to different sources for that.”
Machine learning in XSIAM provides:
- Behavioral analysis: XSIAM uses AI and ML algorithms to analyze endpoint behavior and detect anomalies that may indicate the presence of a threat.
- Threat intelligence: The platform applies ML algorithms to analyze large volumes of threat intelligence data and identify patterns and trends that may indicate an emerging threat.
- Automated response: XSIAM uses AI-powered automation to respond to threats in real time, without the need for human intervention.
- Predictive analytics: The platform leverages ML algorithms to analyze historical data and predict potential threats, helping organizations proactively protect against future attacks.
- Continuous learning: XSIAM’s ML algorithms continuously learn from new data and adjust their models, improving the platform’s accuracy and effectiveness over time.
Ultimately, Cortex XSIAM empowers teams to be more productive and deliver better security outcomes across the board.
"We used to have thousands of garbage alerts. Now we have five events a week we really need to investigate. That’s how good the systems are working. It’s very easy to investigate.”"
IT security leader
On the path to a best-in-class SOC
Today, with the help of Cortex XSIAM, the company has transformed its SOC to meet the demands of modern threats. As it refines its XSIAM implementation, its SOC is well on the way to becoming best-in-class. Among the benefits it has achieved thus far:
- Nearly doubling its data ingestion from 800 GB per day to 1,500 GB per day, with an additional ~960 GB per day of endpoint data analyzed in line with other data sources.
- Doubling its data sources from 10 to 20.
- Massively decreasing its false positives from ~90% to virtually none.
- Shortening median time to resolution from days to 59 minutes.
- Reducing dashboard overload from 6–10 sources or dashboards for investigations to only 1 or 2.
- Eliminating disparate vendors and tools while broadening its coverage and capabilities. It’s a compelling story that allows security teams to achieve meaningful outcomes and demonstrate success.

The company took a thoughtful approach to implementing Cortex XSIAM, investing heavily in its easy data onboarding capabilities to capture a tremendous amount of security data in one place. With more customization and automation, it has materially better analytics and a minimal false positive rate—a significant improvement over its previous SIEM.
Now the company has a highly mature, modern SOC with an automation-first platform. Its security analysts have the assurance that they’re seeing the whole picture and have the solutions and insights they need to quickly identify and resolve issues. Cortex XSIAM delivers the security posture that allows them to meet the modern threat landscape with confidence.
Learn more about Palo Alto Networks Cortex XSIAM here.