The internet of things, more commonly known as IoT, has arrived in the enterprise in a really big way. That should come as no surprise because the potential benefits are immense. Whether it’s the building sensors, surveillance cameras, point of sale systems, or conference room technology, IoT is on the network helping to enable digital transformation.
While IoT is on the network, in far too many cases, organizations aren’t aware of all the things that are running or the risks those things may represent. An unknown and unmonitored device on the corporate LAN represents a potential attack vector that can put an organization at risk.
Typically, enterprises want to support IoT devices on the network, but they also want to make sure that devices are secured in a way that doesn’t hinder productivity or add new burdens on IT security. It’s important to achieve both.
IoT Security by the Numbers
According to a Unit 42® IoT Threat Report, IoT accounts for more than 30% of all network-connected devices in the average enterprise. All those devices represent what Unit 42 refers to as a time bomb just waiting to explode. In fact, the research shows that 57% of IoT devices are vulnerable to medium- or high-severity attacks.Also, the Gartner Machina IoT Forecast database predicts there will be over 18 billion connected devices in enterprises by 2030. To put the numbers in perspective, by 2030, there will be four times the number of devices connecting to the network than the users in an enterprise.
Adding further insult to injury, 98% of all IoT traffic is unencrypted. Unencrypted traffic means that if an IoT device sends information over the network or the public internet, that information is sent “in the clear” meaning anyone can see it. Unencrypted data coming from unmanaged IoT devices could potentially lead to a data breach or a successful ransomware attack.
The 5 L’s of IoT Devices
When looking at the risks of IoT devices, there are what we refer to as the 5 L’s, which is a helpful way for a CXO to understand where the risks are:
- Large Quantity: There is a large and growing number of IoT devices.
- Large Variety: There is a large variety of protocols and technologies used in IoT.
- Lack of Self Protection: For the most part, IoT devices are exposed and do protect themselves.
- Larger Risks (as the attack surface is increased): Without encryption and with unprotected access, IoT expands the attack surface within organizations.
- Long Lifecycle: IoT devices often outlive the supported update cycle from a vendor, meaning there can be a lot of older, unsupported IoT devices on a network.
Removing the Burden and Risk of IoT Devices
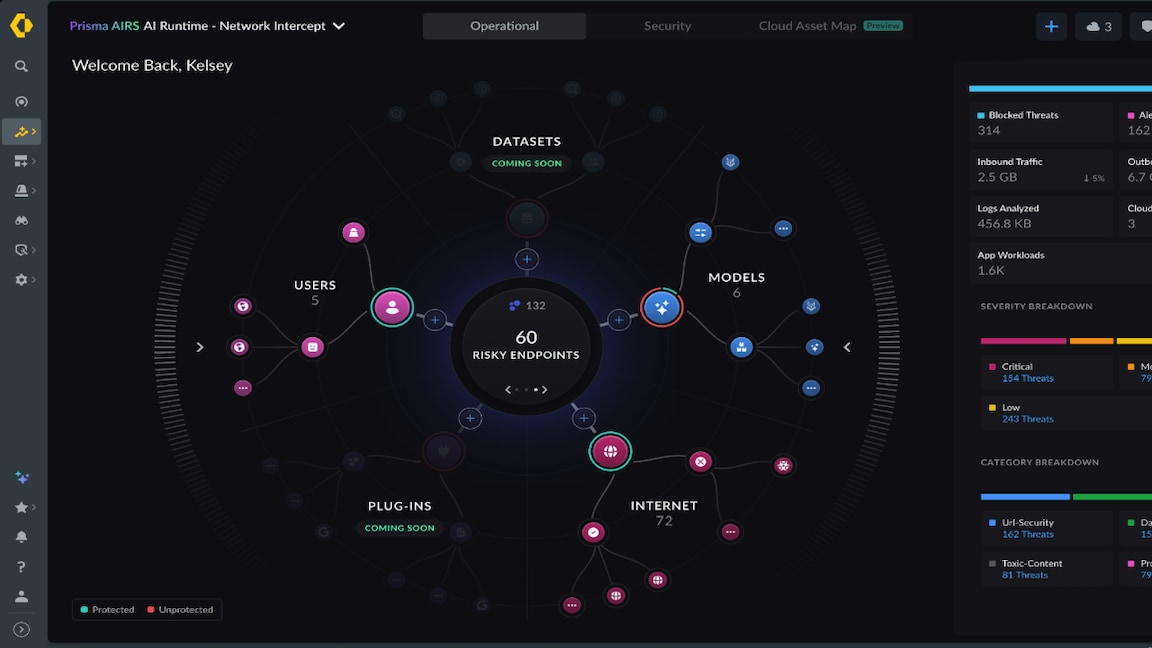
The first step in limiting the risk of unmanaged IoT is to get visibility into what’s on the network. After all, you can’t manage what you don’t know about.
Simply scanning the network hoping to find devices isn’t enough either as traditional network scanning techniques are typically limited to device identification of known asset types. Traditional network scanning also poses a risk as it can crash or even break mission-critical operational technology equipment. Given the large variety of IoT devices, the reality is that not all devices will be easily discovered or classified. That’s where there has been a real burden for IoT management. It’s not that IT staff don’t want to know what’s on the network. It’s that IoT devices don’t show up in the tools that network and security professionals are used to using.
With passive monitoring and machine learning, it’s possible to locate, then identify, the patterns associated with a given device. By monitoring not just what’s on the network but also the behavior of the devices on the network, a clearer picture can emerge. That can be used to inform an IoT security policy. The traditional approach of manual policy generation for what devices can or cannot do on a network is extremely cumbersome and error prone. It’s also not scalable to manually build a policy for a growing number of IoT devices.
Removing the burden of IoT risk mitigation is about removing manual processes. It’s about having full visibility into what is on the network and then using the power of machine learning to understand what is risky behavior and what is normal. Converting the findings about how devices behave into automated policies that secure IoT within the infrastructure can make successful IoT adoption less risky.
With a data-driven policy, informed by what IoT is actually doing on the network, the next step is to pair that policy with the full range of cloud and on-premises security services to block all the known and unknown threats that target your IoT device – that’s the end goal.
Don’t leave your IoT devices to the mercy of shadow IT, which is unmanaged. Take control, reduce risk, and let your organization benefit from IoT, without the burden of unmanaged security risk.