Search
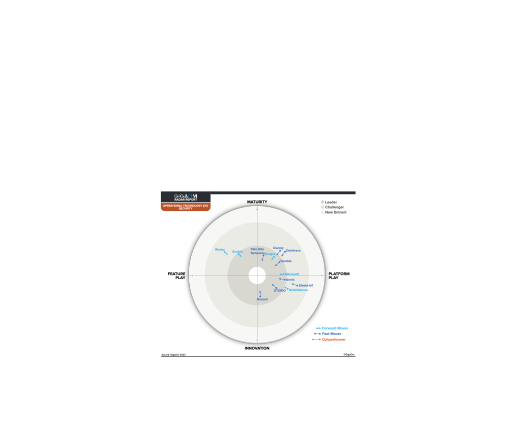
Forrester names
Palo Alto Networks
a Leader in OT security.
60-DAY FREE TRIALExperience security
Experience security
built for OT complexity.
Try our comprehensive industrial OT security solution, free.
RECOMMENDED
Increased ROI
Comprehensive Industrial OT Security lowers risk for OT environments and provides 351% ROI
- 95%
LOWER COMPLEXITY
- 15X
FASTER DEPLOYMENT
- 351%
RETURN ON INVESTMENT
Talk to us
Contact our Industrial OT security experts. We’ll help you protect your assets.
Get the latest news, invites to events, and threat alerts
Products and Services
- AI-Powered Network Security Platform
- Secure AI by Design
- Prisma AIRS
- AI Access Security
- Cloud Delivered Security Services
- Advanced Threat Prevention
- Advanced URL Filtering
- Advanced WildFire
- Advanced DNS Security
- Enterprise Data Loss Prevention
- Enterprise IoT Security
- Medical IoT Security
- Industrial OT Security
- SaaS Security
- Next-Generation Firewalls
- Hardware Firewalls
- Software Firewalls
- Strata Cloud Manager
- SD-WAN for NGFW
- PAN-OS
- Panorama
- Secure Access Service Edge
- Prisma SASE
- Application Acceleration
- Autonomous Digital Experience Management
- Enterprise DLP
- Prisma Access
- Prisma Access Browser
- Prisma SD-WAN
- Remote Browser Isolation
- SaaS Security