Originally published in the Economist under the title: “When IoT becomes the weak link in OT security”
In the past, the risk of a compromised Internet of Things (IoT) device would have been disregarded as highly unlikely for businesses, and hardly profitable for hackers. What could possibly be achieved from compromising a light switch or motion sensor?
But, such devices do not operate in isolation — they exist within sprawling systems that span information technology (IT), operational technology (OT), cloud infrastructure and storage. Exposing a single device to a hacker opens the door to the entire network, including the crown jewels of any organisation: its data, the lifeblood to business operations.
This is precisely what happened to a Las Vegas casino in 2017. A single IoT device — a smart thermostat in the lobby’s fish tank — was hacked and used as a stepping stone to exfiltrate the data of its high-roller customers.
With countless unsecured IoT devices in use, such breaches could become widespread. Businesses might not realise that cyber-criminals are already operating in their networks, using IoT devices as entry points to launch further attacks.
The OT Security Threat
So many IoT devices come with basic manufacturer credentials by default, passwords by default, insecure protocols and applications, and vulnerable or end-of-life software and legacy assets that are difficult to patch or keep up to date. They were built to be easily accessible at a low cost, with security as an afterthought. The bad guys can take advantage and exploit those vulnerabilities.
A lack of regulations and industry standards for IoT devices contributes to the already poor levels of security. Many IoT vendors work in niche markets and may prioritise power efficiency or connectivity over security, introducing vulnerabilities and leaving customers to deal with the fallout.
In the health care sector, cyber-security professionals are dealing with a range of concerns over Internet of Medical Things (IoMT) devices.
Such devices have a “low barrier to entry to the hospital network, making it easier for attackers to exploit vulnerabilities for ransomware and other malicious activity,” says Wendy Roodhooft, chief security officer of Belgian health care provider AZ Vesalius. “Although the devices were ostensibly protected by network access control, the endpoint security for IoMT devices remained a weak link.”
Powering Industry 4.0
IoT is at the heart of Industry 4.0 — the digital transformation of sectors like manufacturing, health care and transport. The general idea is to integrate an array of network-enabled “things”, which could include anything from a thermostat to a 20-tonne subway car, and enable them to gather data and perform tasks that expand the enterprise’s capabilities.
A facility may host tens of thousands of IoT devices — from cameras and heat sensors to sprinklers, robots and barcode scanners — powering automated quality assurance, crowd management, predictive maintenance and autonomous operations.
Global Industrial IoT Growth
IoT devices (known as Industrial IoT or IIoT) are often deployed by OT staff, who are also responsible for heavy industrial equipment. This includes decades-old “legacy OT” that has to be retrofitted to work with IoT connectivity.
Organisations with multiple facilities often lack full visibility of their IoT footprint as they have a variety of equipment across sites. Although IT oversees enterprise cyber-security, it has limited control over IoT assets managed by OT.
Managers may assume that legacy OT and air-gapped systems are secure. In reality, about 70% of industrial control assets have external connections, according to Palo Alto Networks. Any network link, no matter how isolated, is a potential attack vector.
It’s really surprising how many companies that I visit where they really do not have a management of the inventory or comprehensive visibility of the devices connected. There could be third parties or contractors involved. You can have so many devices in and out of the network, but they don’t have control or visibility.
In Europe, the NIS2 directive is tightening rules, requiring medium and large companies and their extended supply chains to uphold cyber-security standards in 18 critical sectors. The directive shortens incident reporting requirements from 72 to 24 hours and holds chief executives and board members personally liable, threatening fines or job losses for non-compliance.
Improving IoT visibility
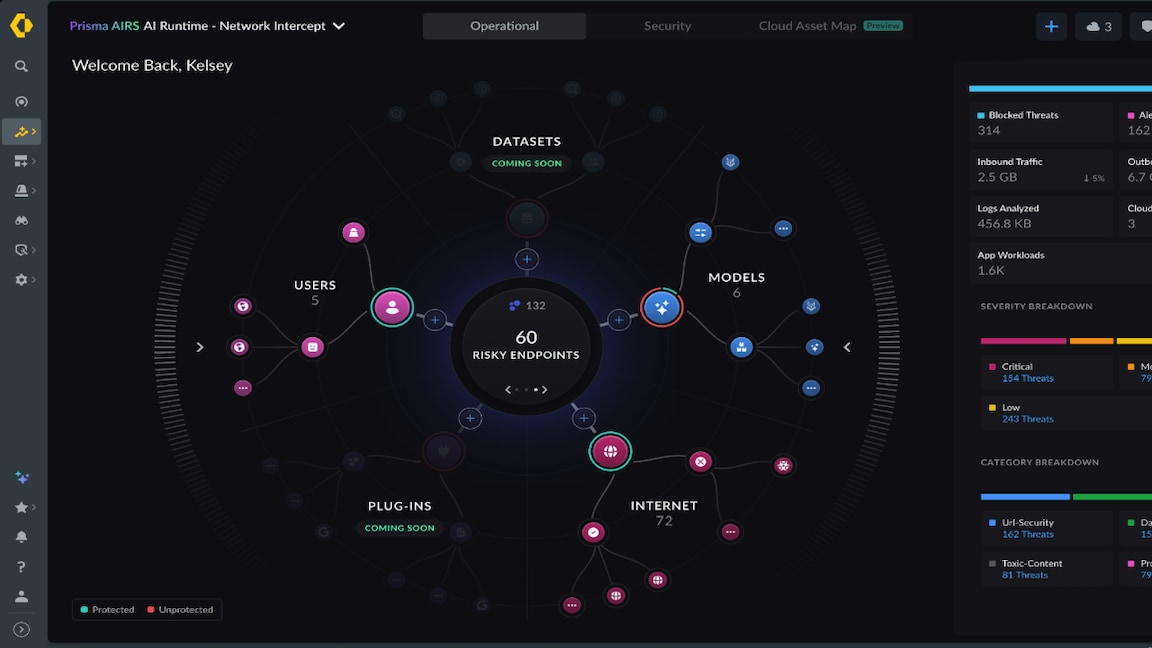
As well as conducting a census of connected assets, cyber-security executives must assess those assets’ security posture and implement appropriate policies. Effective IoT monitoring requires real-time, automated validation across enterprises and supply chains using artificial intelligence (AI) and advanced cyber-security. These demands will push manufacturers and others to adopt Zero Trust security.
If your crown jewels are based on industrial devices, it’s critical you protect and segment them effectively. I call it least privileged access, where there are only specific groups or specific people that can access those crown jewels.
When AZ Vesalius partnered with Palo Alto Networks, it gained full visibility into the constellation of IoT devices attached to the network, from someone attaching a device into a USB port to Shadow IT projects launched years ago.
“Within 24 hours of switching the service on, we could see all 3,000 medical and IoT devices connected to the network,” Ms Roodhooft says. “We identified vulnerable MRI scanners, cameras and other equipment that used standard passwords. We also discovered an old camera on the roof, used for birdwatching, that we didn’t even know existed!”
As for bridging the IT/OT divide, Dharminder Debisarun, Palo Alto Network’s smart industries cyber-security executive, says these groups will naturally need to work more closely together to secure IoT while avoiding OT disruptions.
“How do you make sure that the data is stored where it should be stored?” he asks. “How are you going to make sure that the device is not copying that data somewhere else, or being misused? With cyber-security, your end goal is to make sure that systems, networks, users and data are protected against unauthorized access, attacks, damage or theft.”