Innovation demands uncompromising performance
 ASIC FE-400 chip
ASIC FE-400 chipAnd we make no sacrifices.
Performance
With Single-Pass Parallel Processing architecture (SP3), our ML-Powered Next-Generation Firewalls enable high-throughput, low-latency network security and allow high network speeds to be maintained while delivering unprecedented features and technology.
Expect powerful outcomes with flexible, scalable deployment that secures all locations and everything in between.
PA-7500





App-ID™ performance
Interface support
Networking processing cards
Layer 7 threat prevention throughput
Data processing cards
The PA-7500 chassis intelligently distributes processing demands across three subsystems, each with massive amounts of computing power and dedicated memory.
Provides the firewall with network connectivity.
Provides the firewall with additional processing power and capacity.
Provides the firewall with a management interface, first packet processing, logging interfaces, and inter-chassis HSCI ports. *Must be installed in slot 4.
Provides the firewall with network connectivity.



Provides the firewall with network connectivity.

Provides the firewall with additional processing power and capacity.

Provides the firewall with a management interface, first packet processing, logging interfaces and inter-chassis HSCI ports. Must be installed in slot 4.

Provides the firewall with network connectivity.
The world’s first Layer 7 firewall to exceed over 1.5 Tbps App-ID performance

Flexible, scalable design supporting up to seven data processing cards and/or networking cards for maximum throughput.

Flexible, scalable design supporting up to seven data processing cards and/or networking cards for maximum throughput.

The PA-7500 includes the new FE400 ASIC, custom silicon developed by Palo Alto Networks.

Our chassis intelligently distributes processing demands across subsystems, each with massive computing power and dedicated memory.



Quantum Optimized with 256 Cores of Compute and Hardware acceleration delivering 4X the performance

App-aware performance
Full Layer 7 threat performance
Concurrent Layer 7 session


The highest performing ML-Powered NGFW in a two rack unit (RU) design.

The PA-5580 delivers 4X threat performance and 2x higher session capacity compared to the previous generation PA-5545


App-ID performance
Threat performance
Concurrent sessions

The PA-455 provides optional redundant power for organizations looking for additional connectivity options.

The PA-455 provides optional redundant power for organizations looking for additional connectivity options.

Simplified deployment with Zero Touch Provisioning (ZTP)

Four SFP/SFP+ 1Gbps/10Gbps ports offer redundancy for remote offices


Full Layer 7 threat performance
Concurrent Layer 7 sessions
Extended operating temperatures


The fastest and most comprehensive ruggedized NGFW, offering over 2 Gbps of throughput and supporting over 200,000 concurrent sessions.

High performing ruggedized appliance in a 1U form factor that supports data pass-through in case of power failure
Integrated 5G modem and fiber connectivity in a compact, flexible package for securing remote offices.

Per port PoE power
Full Layer 7 threat performance
Concurrent Layer 7 sessions

Stop known and unknown threats in real time and decrypt branch traffic at high speed.

Stop known and unknown threats in real time and decrypt branch traffic at high speed.

Silent, fanless design with optional redundant power supply for branch and home offices.
Support high availability with active/active and active/passive modes.
Strata Cloud Manager™ enables you to easily manage your Palo Alto Networks Network Security infrastructure—including NGFWs and SASE environment—from the cloud, via one unified management interface.


Predict and Prevent Network Disruptions
See how network health issues may be impacting your users, and jump directly to any incident to investigate.
Strengthen Security in Real Time
See what portion of your traffic is flowing over rules that adhere to best practices, including ones you’ve added to fit your needs. You can also compare adjustments to see which will have the most impact.
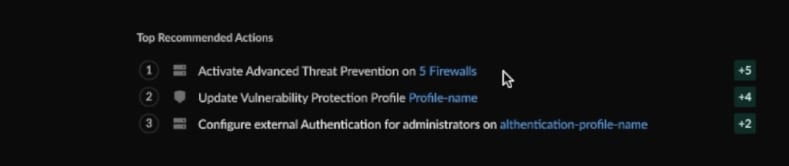
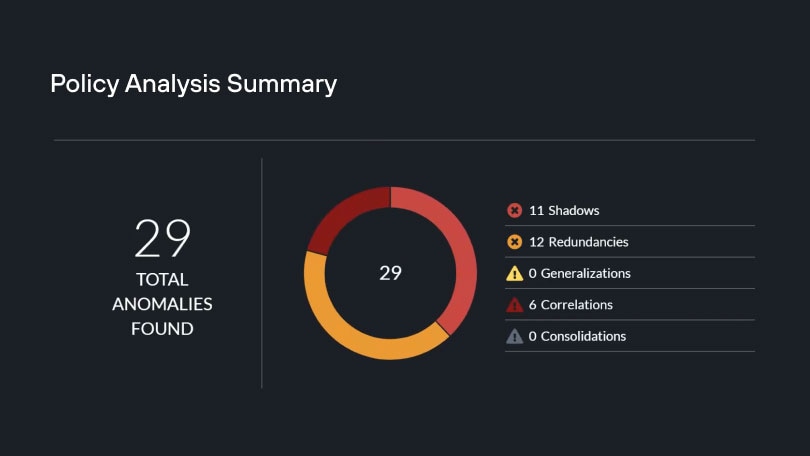
Use the policy analyzer to gauge the impact of new policy changes before they are pushed to your NGFWs.
Comprehensive Management for all Deployments
Oversee all your assets, users, applications and devices — including IoT — from the summary view. From here, you can see how your network is being accessed and secured while also being able to click deeper into areas of interest.
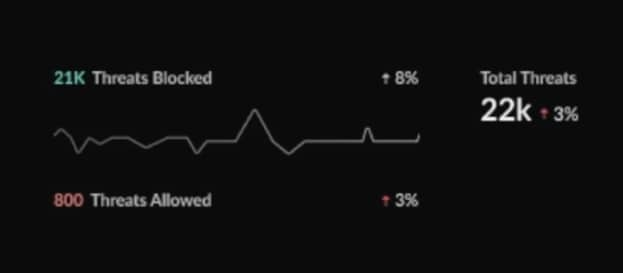
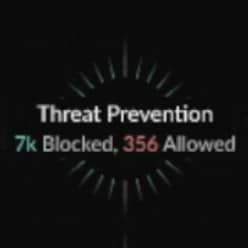
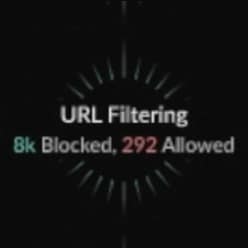
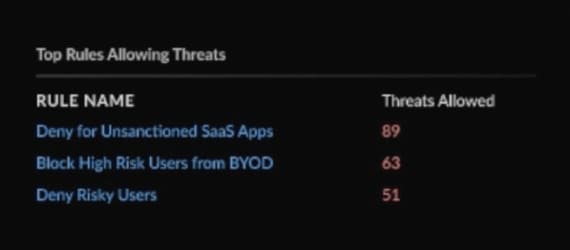
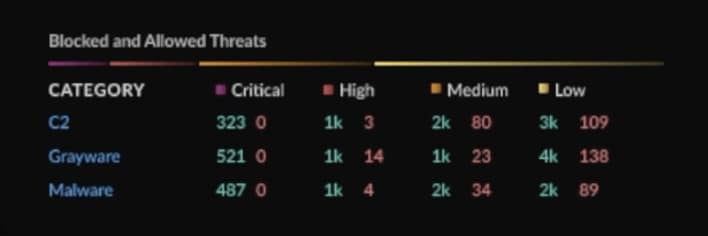
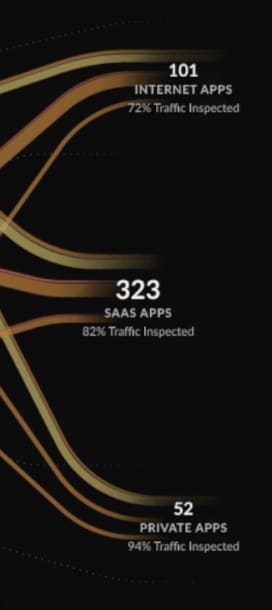
With Strata Cloud Manager, you have a comprehensive view of what’s going on and how to configure your security services to create the best outcomes. You can view apps that have the highest volume of threats, identify where policies might be lax and track how your security services are performing over time.


WEBPAGE
Secure whatever, whenever, wherever, from the latest threats — with less complexity





















