PA-SERIES
MILLION BENEFITS REALIZED
BREACH REDUCTION
MILLION END-USER PRODUCTIVITY GAIN
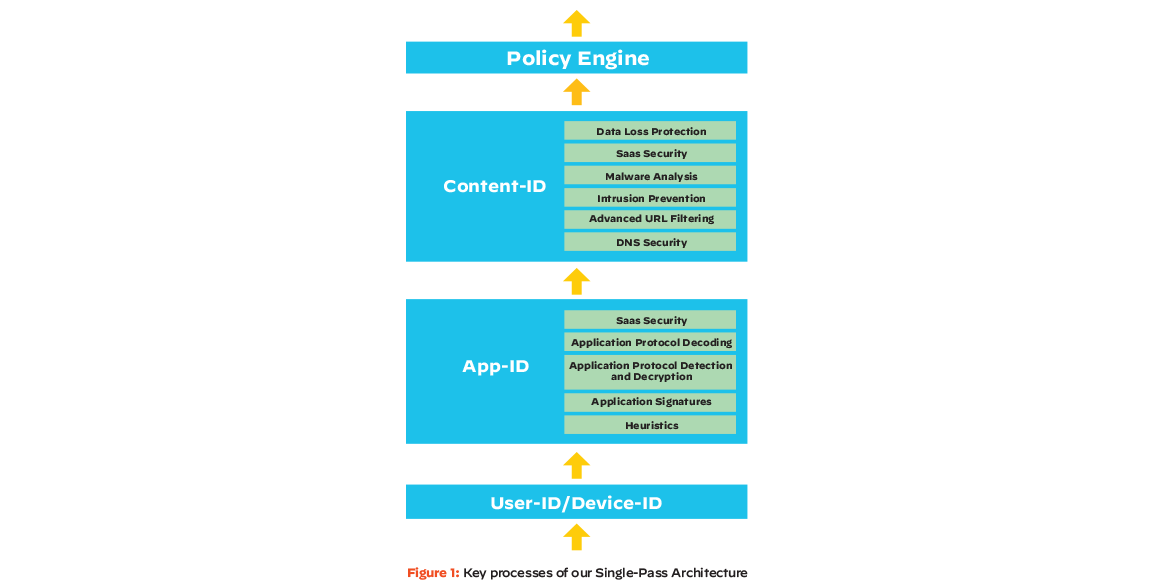
Palo Alto Networks single-pass architecture employs a unique single-pass approach to packet processing, delivering better performance and security.
A comprehensive approach to Layer 7 security starts by identifying your applications regardless of port, protocol, evasive techniques or encryption (TLS/SSL).
Our Palo Alto Networks firewalls classify network traffic by the application’s identity in order to grant access to users and provide visibility and control of all types of applications to admins, including web applications, software-as-a-service (SaaS) applications and legacy applications. Our approach uses the application, not the port, as the basis for all your safe enablement policy decisions so you can allow, deny, schedule, inspect and apply traffic-shaping. When needed, you can create custom App-ID™ tags for proprietary applications or request App-ID development for new applications.
Attackers frequently bypass traditional signature-based security, modifying existing threats that then show up as unknown signatures. This leaves security professionals struggling to keep up since manually adding signatures cannot be done fast enough to prevent attacks in real time. Plus, using solutions that pull files offline for inspection creates bottlenecks, hinders productivity and can’t scale.
Our ML-Powered NGFWs use embedded ML algorithms to enable line-speed classification, inspecting files at download and blocking malicious files before they can cause harm. With inline prevention, the PA-Series automatically prevents initial infections from never-before-seen threats without requiring cloud-based or offline analysis for the majority of malware variant threats, reducing the time between visibility and prevention to near zero.
Our inline deep learning system analyzes live traffic, detecting and preventing today’s most sophisticated attacks, including portable executables, phishing, malicious JavaScript and fileless attacks. Finely tuned models avoid false positives, and a unique feedback loop ensures fast and accurate threat prevention as attacks happen – all without sacrificing performance.
Identity is a critical component of a Zero Trust approach to network security. With enterprises increasingly migrating from on-premises to cloud identity providers, and users connecting from anywhere, it is difficult to keep security and identity information connected and in sync across the network. Networks are designed for a single source of identity, and this can lead to inconsistent security between data centers, campus networks, public clouds and hybrid environments.
Palo Alto Networks Cloud Identity Engine is a cloud-based architecture for identity-based security that can consistently authenticate and authorize your users, regardless of location and where user identity stores live – on-premises, in the cloud, or hybrid. As a result, security teams can effortlessly allow all users access to applications and data everywhere and quickly move toward a Zero Trust security posture.
Cloud Identity Engine saves you time and hassle in deploying and managing identity-based controls on your network security infrastructure, using a point-and-click configuration with real-time identity synchronization.
5G is a vital component of the digital backbone of tomorrow’s economy. From consumers to enterprises, governments and critical industries, society will depend on 5G. For this reason, organizations transitioning to 5G infrastructures must adopt security that can withstand sophisticated and evasive attacks as the speed and scale of threats on 5G networks rise.
Palo Alto Networks 5G-Native Security allows service providers to safeguard their networks, users and clouds as well as back their customers with enterprise-grade security they need for tomorrow’s 5G economy. 5G-Native Security allows organizations to extend Zero Trust to their 5G environments to help protect their business-critical 5G users, devices and applications. 5G-Native Security offers a comprehensive approach to protecting all facets of 5G networks.
Service providers can deploy a Zero Trust architecture for their 5G network infrastructure and the business-critical enterprise, government and consumer traffic it carries. Enterprises and organizations can protect their 5G users, applications and infrastructure with the same Zero Trust approach they use in their other network segments.
Over the past two decades, web proxies have become a security mainstay for organizations. As corporate networks expand, the demand for consistent, location-independent security is growing. This means many organizations are adopting converged, cloud-centric architectures. However, many organizations migrating from on-premises to cloud struggle with large structural changes that can hinder business productivity and services.
We simplify security for those who use an on-premises proxy by introducing web proxy support for next-generation firewalls. This allows users to modernize their network security without instituting large changes to existing infrastructures.
Now, both proxy and firewall admins can leverage a single UI to deploy, manage and operate their firewall, allowing them to provide consistent security and policies across all deployments. We make it simple for organizations to move away from their legacy solutions that can't scale, and give them a way to modernize their proxy architecture and deliver best-in-class security everywhere, all while maintaining interim support for their proxy.
Through this platform, organizations can:
Contact our team of NGFW experts today. We want to meet with you to help keep your network secure.