What's New
in PAN-OS 8.1
A wealth of innovations to secure clouds, networks and organizations.
Keeping you a step ahead
Introducing PAN-OS® 8.1, the latest release of the software that powers our next-generation firewalls. The new features and innovations of PAN-OS 8.1 will help you accelerate your adoption of next-generation security and protect your organization from a wide range of threats.
Simplified application security
App-ID™ technology identifies the applications traversing your network so you can safely enable desired applications and block unwanted ones. With PAN-OS 8.1, it’s easier to move to and maintain an application-based security policy. New features include:
Application filter to allow new App-IDs – Temporarily allow new apps, so you can be sure newly released apps will not accidentally block traffic you intended to allow. That gives you time to perform a review of your policy and make updates.
Better tools to assess the effect of App-IDs – Get insight into newly categorized application activity and the effect of the new App-IDs on your traffic.
Rule usage tracker to eliminate security risks – Remove unused security rules by understanding when a rule was last hit, which eliminates holes that create security risks.
Controlling risk in SaaS applications
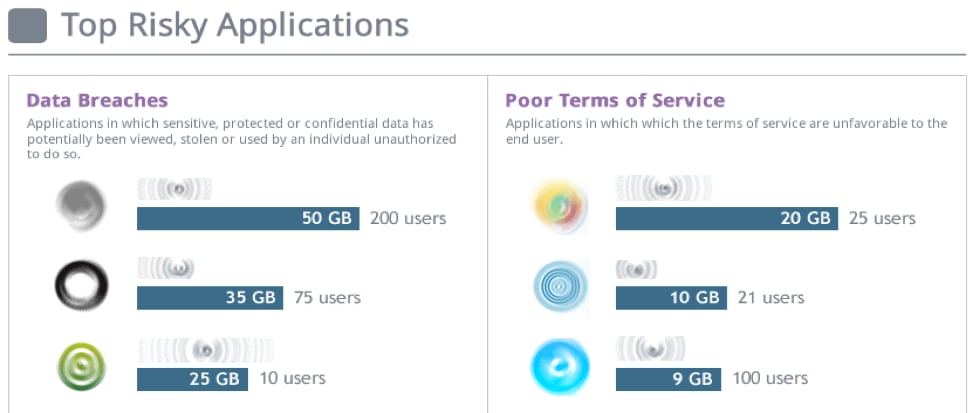
SaaS applications host sensitive data, and IT needs to ensure that data is stored in secure and compliant SaaS services. With the new SaaS application characteristics in App-ID, you can reduce risk based on hosting characteristics of SaaS applications. You can view detailed risk profile and usage statistics for the applications on your network; quickly identify and explore risky applications to determine which you should allow in your environment; and prevent future violations by enabling granular policy control.
Streamlined SSL decryption
Decryption Broker provides smarter, simpler decryption
The next-generation firewall Decryption Broker, an innovation introduced with PAN-OS 8.1, overcomes the challenges of supporting devices that complement next-generation firewalls. Now you can decrypt once and share decrypted traffic with other devices easily. All complementary devices are inline, enabling enforcement on each device and maximizing security. The Decryption Broker is a natural extension to decryption on the next-generation firewall, simplifying the management and troubleshooting of the solution.
Performance boost with new hardware systems
At the internet edge
The new PA-3200 Series appliances deliver up to 5x performance increase, up to 7x decryption performance increase, up to 20x decryption session capacity increase compared to existing hardware for the internet edge, and 1G/10G/40G interfaces for flexible connectivity options.
In harsh environments
The new PA-220R ruggedized next-generation firewall brings you the same PAN-OS features that protect your largest data centers; offers an extended temperature range; and is certified to IEEE 1613 and IEC 61850-3 standards for vibration, temperature and immunity to electromagnetic interference. It provides interactive visibility and control of industrial protocols and applications, such as Modbus, DNP3, IEC 60870-5-104, Siemens S7, OSIsoft PI® and more.
For high-performance data centers and mobile networks
The PA-5280, the latest addition to the PA-5200 Series appliances, prevents threats and safely enables applications in mobile network environments and large enterprise data centers. The PA-5280 offers security at throughput speeds of up to 68 Gbps and session capacity of up to 64 million.

Improved management efficiency and performance


Panorama™ management 8.1 includes new features that provide even greater efficiency for teams managing physical and virtual appliances running PAN-OS. Using variables in templates, you can now leverage common configurations across many devices while substituting device-specific values in place of IP addresses, IP ranges, FQDNs and more.
With device health monitoring, Panorama provides a deployment-wide view into the health and status of your next-generation firewalls. Trending of critical system resources up to 90 days helps you identify gradual changes in your environment. Proactive monitoring automatically creates alerts when substantial changes occur in the utilization of critical device resources, ensuring you’re the first to know. And new M-600 and M-200 appliances deliver high-performance management.
Panorama deployment flexibility
PAN-OS 8.1 enables you to deploy Panorama on public clouds. Its distributed architecture allows you to scale Panorama using the concept of modes, namely Panorama, Management Only or Log Collector. The choice of on-premise, private and public cloud environments provides maximum deployment flexibility. You can also use Panorama in conjunction with Palo Alto Networks® Strata Logging Service (formerly known as Cortex Data Lake).


