Prevent unintentional data leakage by employees
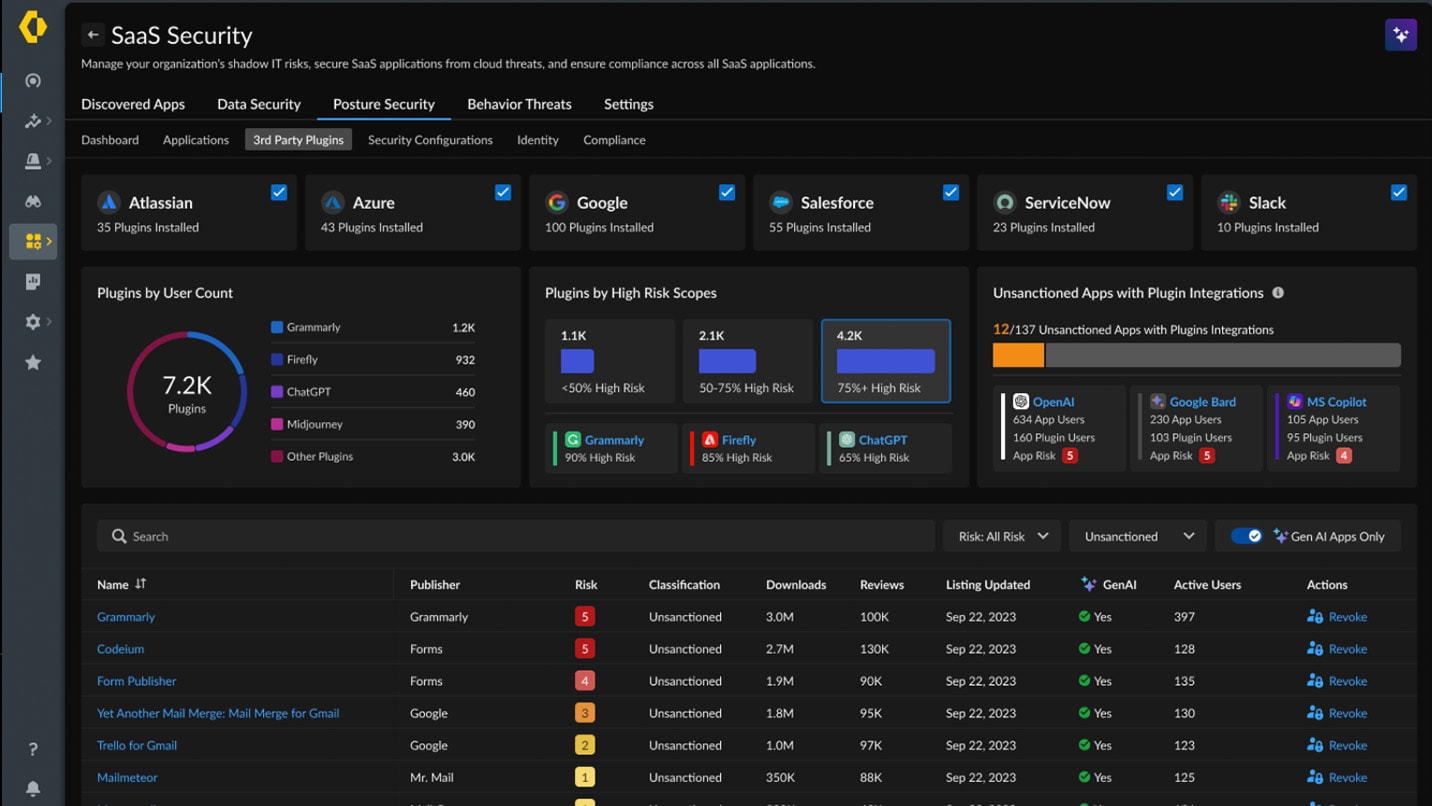
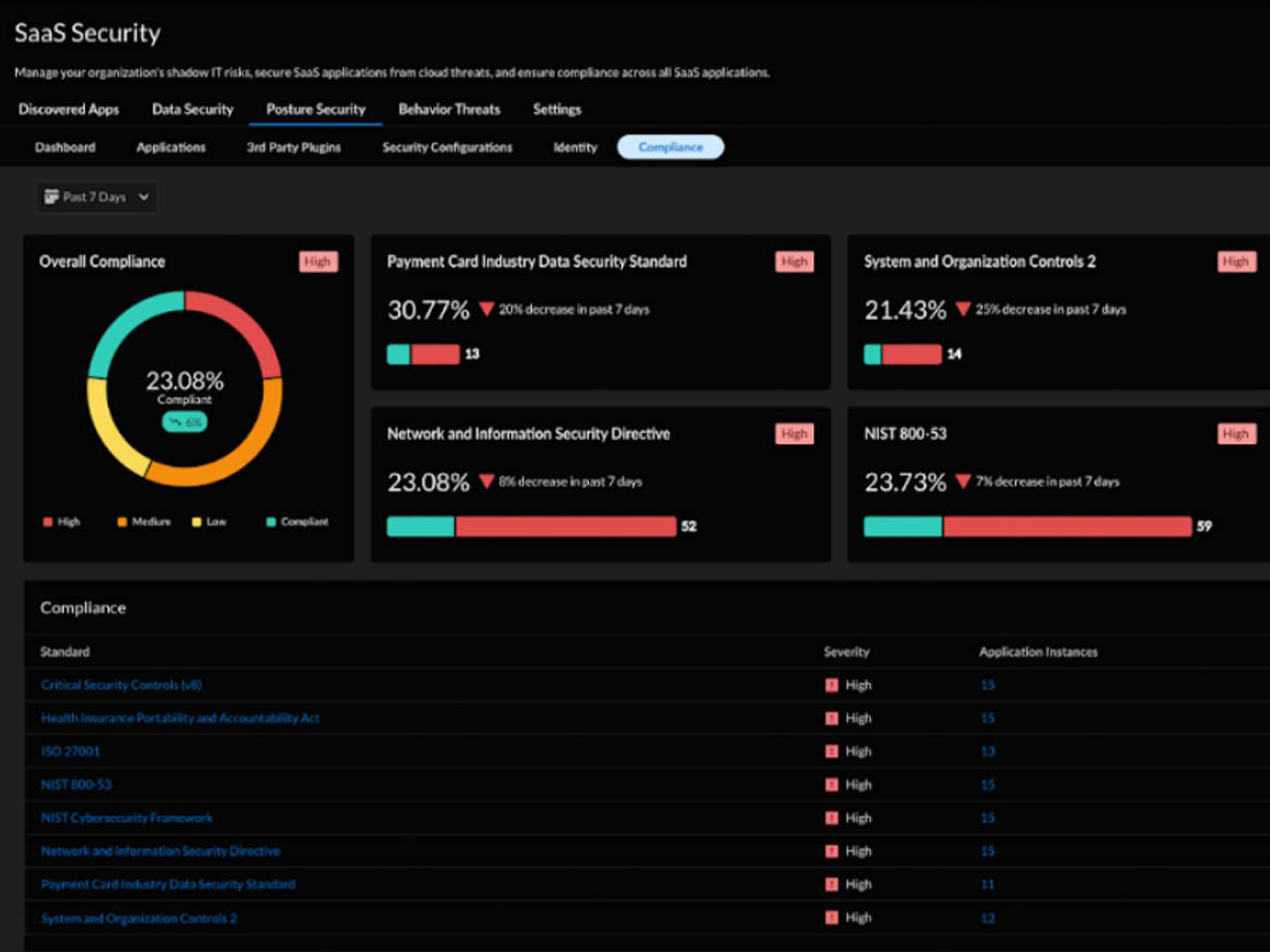
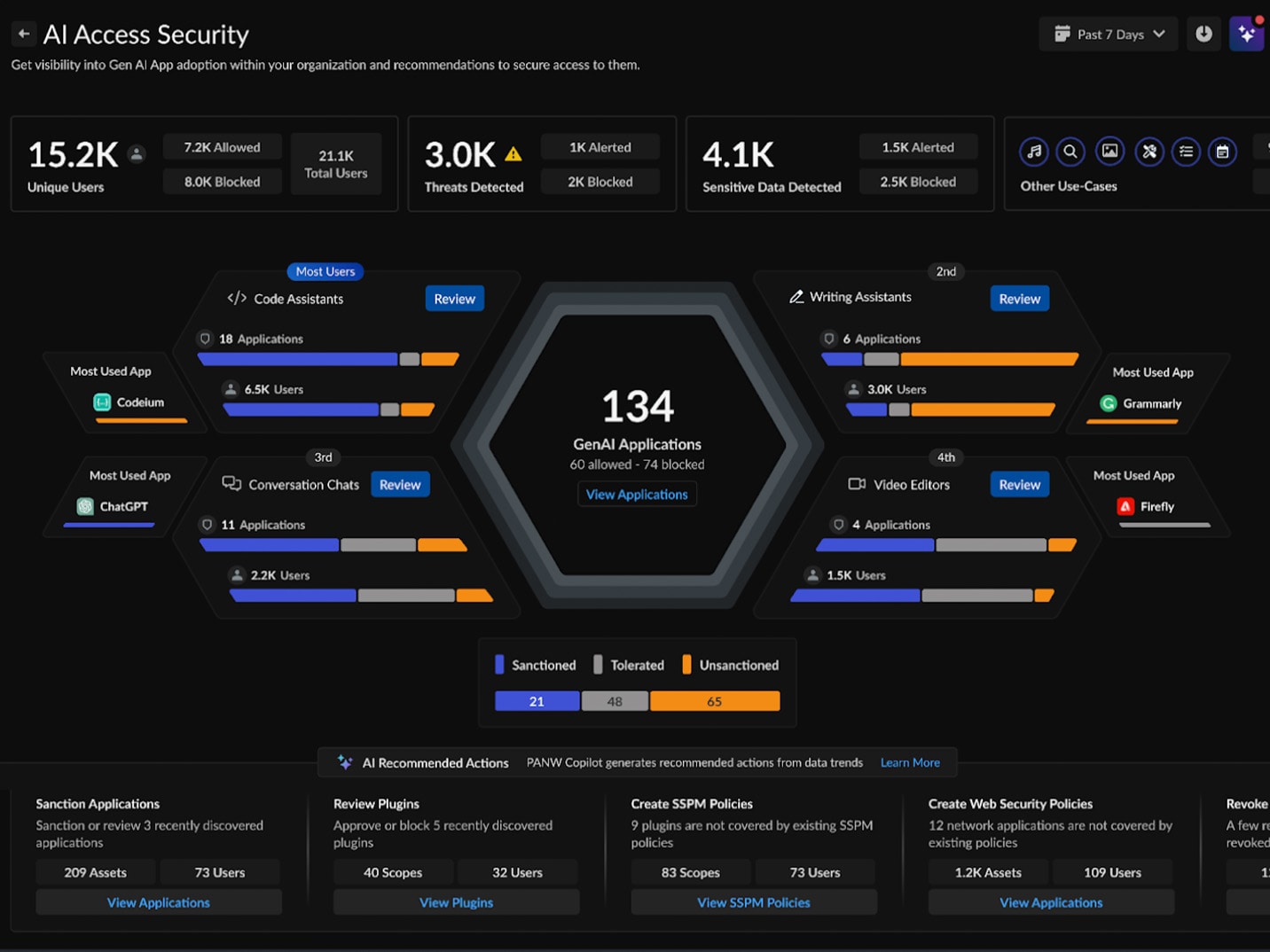
Human error is one of the leading causes of data breaches. Palo Alto Networks uses data monitoring and context-aware policies everywhere to prevent sensitive information from leaving the organization’s purview unintentionally.
With precise detection, real-time user coaching and adaptive response, you can significantly reduce the risk of accidental data loss without interrupting workflows.