The recent addition of remote desktop control to Google Chrome sounds pretty cool – the casual, tech savvy user can now help their friend or family out if they are having problems with their PC. While remote access control features are indeed beneficial, in the hands of an unaware user, they have proven to be significant network security issues.
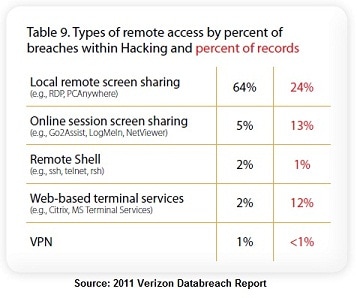
In the 2011 Verizon Databreach Report that analyzed 900 incidents worldwide, 320 of the initial penetrations could be tracked back to remote access errors.
Using our own research from the past two years of data collected and analyzed in the Application Usage and Risk Reports, the 5 most frequently used remote access tools have remained consistent. The frequency of use is based on finding the application at least once within an organizations network. In all cases, more than one remote access control tool was found.
The interesting trend seen is the growth in popularity of Teamviewer, an open source tool that, according to Wikipedia, supports nearly every client known to exist. So using Teamviewer, a support representative could conceivably help a customer using their Android-based phone. A very powerful business proposition. And therein lies the downfall. Since remote access control tool like Teamviewer may look like it is use by support or IT, there is a strong possibility that the use of these tools will punch an unnecessary hole (on a non-standard port) in the firewall (table 1).
Google Chrome is no different in terms of its ability to punch through the firewall – it allows a user to configure the port it should use. From the above
article: "If you have trouble connecting to the remote computer or it hangs when saying verifying access code, try allowing ports 443 and 5222 to have inbound and outbound rules in your windows firewall using both UDP and TCP."
Again, a very powerful feature that, in the hands of an unsuspecting user, can present the organization with significant network security challenges.
Recommendations to avoid becoming a security breach statistic:
- Learn which remote access tools are in use, who is using them and why.
- Establish a standard list of remote access tools for those who need them
- Establish a list of who should be allowed to use these tools.
- Document the usage guidelines, complete with ramifications of misuse and educate ALL users.
- Enforce the usage using traffic monitoring tools or better yet, a Palo Alto Networks next-generation firewall.
Users are smarter, more used to being online and expect to be able to use whatever application they desire. This is an understandable position, given the always online nature, but while at work, a balance must be achieved that protects the network, but enables the user.
The interesting trend seen is the growth in popularity of Teamviewer, an open source tool that, according to Wikipedia, supports nearly every client known to exist. So using Teamviewer, a support representative could conceivably help a customer using their Android-based phone. A very powerful business proposition. And therein lies the downfall. Since remote access control tool like Teamviewer may look like it is use by support or IT, there is a strong possibility that the use of these tools will punch an unnecessary hole (on a non-standard port) in the firewall (table 1).

