Only a few years ago, the world was buzzing with the term “4G.” While many mobile network operators (MNOs) are still rolling out their 4G infrastructures, the world is already buzzing about “5G.” Year 2020 is the suggested timeline for when MNOs are predicting to be ready for 5G. Development is already in the works with IETF, 3GPP, 5G-PPP, ETSI and NGMN, to name a few. Many government bodies, such as the European Union, are funding 5G rollouts pre-2020 using pre-standard technologies.
But what’s in it for an average user to be hyper-excited about hyper-connected 5G? How do MNOs view 5G? What are the security challenges that MNOs will need to face with a 5G rollout?
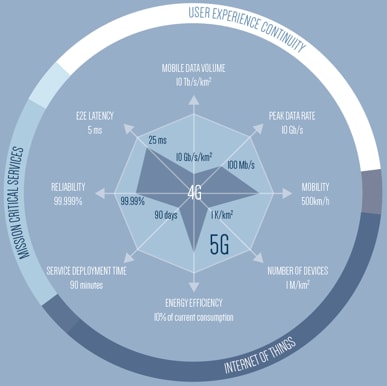
From an average user’s perspective, 5G will bring ultra-low latency, high speeds reaching up to 10Gb/s per user equipment and richness of services on-demand, as well as ultra-high availability, reliability, and interconnectivity with everyone and everything through connected devices, nowadays commonly referred to as the internet of things (IoT).
Source: 5G Vision, 5G-PPP
For MNOs, 5G implies the introduction of new service models; deep technical modifications in radio and optical technologies; network infrastructures transformations to software-defined networks (SDNs) and network functions virtualization (NFV); and unprecedented demand for preventive security.
Nowadays, MNOs are quickly realizing large gaps in their security posture, even within their 4G infrastructures – no longer can security be treated as an afterthought. Security needs to be part of overall infrastructure design from its outset; instead of asking, “How much would it cost to have security?” we need to ask, “How much will it cost if there is inadequate security?”
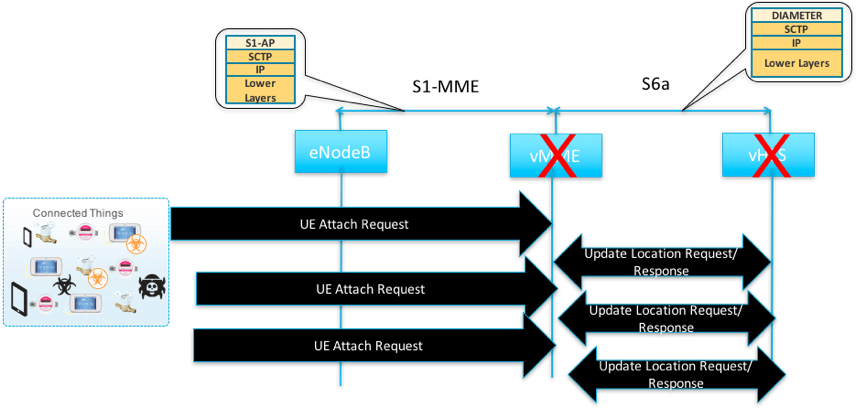
Think of the recent massive WanaCrypt0r ransomware attack (You can read about Palo Alto Networks protections against WanaCrypt0r, and see a detailed breakdown by our Unit 42 threat research team). The attack hit many organizations globally, including quite a few MNOs. What is the price tag to bridge that security gap? Could the attack have been prevented? Think further … what is the price tag associated with signaling attacks, such as S1-AP paging floods, Diameter 3GPP Update Location Request (ULR) and Authentication Information Request (AIR) floods, or GTP Control plane floods? Just imagine billions of zombie devices requesting to be attached at the same time, as instructed.
MMEs/vMMEs and HSSs/vHSSs simply cannot sustain such “misbehavior,” and die. That forces MNOs to overprovision their 4G – and soon 5G – infrastructures. What is the price associated with that? In addition to “killing” a few core elements, zombie IoT devices’ batteries won’t last long, breaking the desired IoT protocol’s behavior, targeting to preserve device battery life … well, as more infected devices get robotized, killing battery life becomes an extra bonus of the hacking exercise, doesn’t it?
One might think that positioning crypto on S1-MME and S6a interfaces would be good enough to provide signaling plane protection on those interfaces. Is it really? IPsec is the right approach to deploy for transport security. One of the interesting side-effects of IPsec is that it ensures everything is sent securely, including malware, signaling storms and other “interesting” things.
Sure enough, 5G’s hope is to deploy SDN- and NFV-based technologies, where MNOs will be striving to reduce their CAPEX. Using the example of signaling storms, we need to question how easy will it be for MNOs to achieve that goal if proper security measurements are not implemented. Taking control of IoT, connected cars, compromised e-health and compromised infrastructures will result in zero connectivity to the “hyper-connected” world.
Stay tuned for more! In the next blog, I’ll address preventive measures for hyper-connected 5G world to remain connected. For more imformation, download the white paper, The Need for a Network-Based Platform Approach in Mobile Networks.