This post is also available in: 繁體中文 (Chinese (Traditional)) Nederlands (Dutch) Deutsch (German) Italiano (Italian) 한국어 (Korean) Español (Spanish) Türkçe (Turkish)
In cybersecurity, one of the things people tend to focus on the least is defining what they’re trying to protect. The general consensus is that they want to protect against attacks, but the attacks are attacking something. What is that thing?
Over the years, we have been working diligently to reduce the attack surface, but unfortunately, it is a bit like the universe in that it is always expanding. With every new technology comes a new set of problems and vulnerabilities. Most notably, the internet of things has led to a massive increase in the attack surface. Newly revealed vulnerabilities such as those underlying the attacks on chip sets – Spectre and Meltdown – have added almost every modern computational system to the overall attack surface as well.
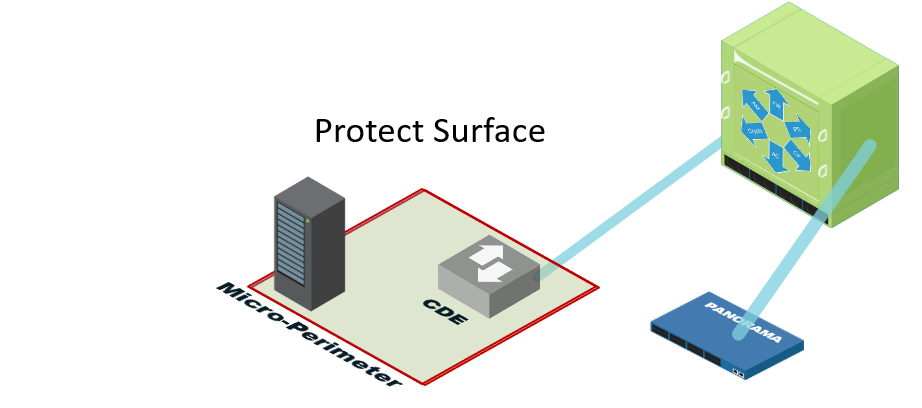
In Zero Trust, instead of focusing on the macro level of the attack surface, we determine what we need to protect: the smallest possible reduction of the attack surface, or the protect surface. Typically, a Zero Trust network defines a protect surface based upon at least one of these four things (remembered by the acronym DAAS):
- Data: What data needs to be protected?
- Applications: Which applications consume sensitive information?
- Assets: Which assets are most sensitive?
- Services: Which services, such as DNS, DHCP, and Active Directory, can be exploited to disrupt normal IT operations?
The awesome thing about the protect surface is that not only is it orders of magnitude smaller than the overall attack surface but it is always knowable. You may not know what it should be today, but you can always find out. Most organizations can’t really define the attack surface, which is why penetration testers always get inside. There are myriad ways to intrude upon an organization’s macro-perimeter. This is why the idea of a large perimeter-based security approach has demonstrated itself to be unsuccessful. In the old model, controls such as firewalls and intrusion prevention technologies were pushed to the edge of the perimeter, which is as far away from the protect surface as you can possibly get.
In Zero Trust, by defining a protect surface, we can move controls as close as possible to that protect surface to define a micro-perimeter. With our next-gen technology functioning as a segmentation gateway, we can segment networks in Layer 7 policy and granularly control what traffic moves in and out of the micro-perimeter. There is a very limited number of users or resources that actually need access to sensitive data or assets in an environment. By creating policy statements that are limited, precise, and understandable, we can limit the ability of our adversary to execute a successful cyberattack.