In this blog series, I’ve been giving sufficient commentary on Zero Trust in order to dispel much of the mythology that has started to surround the topic recently. I talked about the fundamental issues with the failed trust model and how trust is a vulnerability. Then, I provided clarity as to what Zero Trust is (and isn’t). And most recently, I reviewed the concept of a “protect surface”. Now, I want to talk about the concept of a Segmentation Gateway (SG) – the technology that protects the protect surface.
Years ago, before the advent of the Next-Generation Firewall, I wrote about the concept of an SG when I was at Forrester Research. I foresaw the need for a segmentation gateway that collapses all network security technologies into a single gateway for the purpose of segmenting networks based upon users, applications, or data. Today, an SG can be delivered either physically (PSG) or virtually (VSG), and can granularly control what traffic moves in and out of a micro-perimeter in a Zero Trust network.
Network segmentation is top of mind in organizations around the world. I have found that when customers ask for segmentation, what they really mean is that they NEED a Zero Trust network. This isn’t surprising, as a fundamental struggle in the cybersecurity industry is the tendency to think tactically and not strategically. Network segmentation is a tactic and a tool, not a strategy for building secure networks. This is where Zero Trust comes in. Adopting a Zero Trust architecture provides business resonance, defines the business use of segmentation, and provides a methodology for building a segmented network.
How to Segment a Network Properly
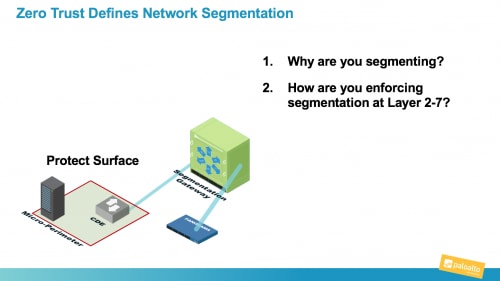
As I work with customers, I show them how applying Zero Trust principles provides two very important answers around how to segment a network properly:
- Zero Trust answers why you are segmenting. Segmentation should be done from the inside out. You first determine what you are protecting. This is typically data, applications, assets, or services that are sensitive, regulated, or in other ways, important to your company. This defines the protect surface, which is the smallest possible outcome of our mandate to reduce the attack surface.
- Zero Trust answers how you are enforcing the segmentation all the way up to Layer 7. Every attacker worth their salt knows how to get past Layer 3 controls. Network segments must be secured at Layer 7. This should be non-negotiable and intuitive.
When I work on Zero Trust network designs, I use a Next-Generation Firewall either in a physical or virtual form factor to function as the SG in a Zero Trust environment. This is imperative as policy must be enforced at Layer 7. Most attackers know how to bypass Layer 3/4 technologies, which is why NGFWs had to be developed in the first place.
By having access to the Layer 7 traffic, we can now create more effective and granular policy controls enforced in real time by the SG. As I noted in my last post, there is a very limited number of users or resources that actually need access to sensitive data or assets in an environment. In an SG, by creating policy statements that are limited, precise, and understandable, you limit the ability of the adversary to execute a successful cyberattack. You just need a Zero Trust architecture as the starting point to achieve this. In my next post, I’ll discuss how Zero Trust enables a new way to create Layer 7 policy.