As organizations explore Zero Trust as a means to prevent successful cyberattacks, more vendors are using Zero Trust as a cybersecurity buzzword. If you walked through the halls of RSA this year, you will have noticed this to be true. Zero Trust was a part of dozens upon dozens of vendor booths, presentations, pamphlets, etc. in one fashion or another. This has resulted in misperceptions of what Zero Trust really is.
With the recent availability of “Zero Trust products,” the perception is that Zero Trust is all about identity or the belief that you have to rip and replace everything to achieve it. With so much noise and confusion, it’s no surprise that people believe that it’s a complex, costly and time-consuming initiative.
In truth, much of the complexity comes from the technology used to implement Zero Trust. John Kindervag, creator of Zero Trust and field CTA at Palo Alto Networks, explained in a recent webinar, “There are no Zero Trust products. There are products that work really well in Zero Trust environments, and there are products that don’t.”
When trying to implement Zero Trust, you don’t have to do everything right out the gate. It’s an iterative process that should start small and expand overtime as you gain familiarity and visibility into what is most critical to secure.
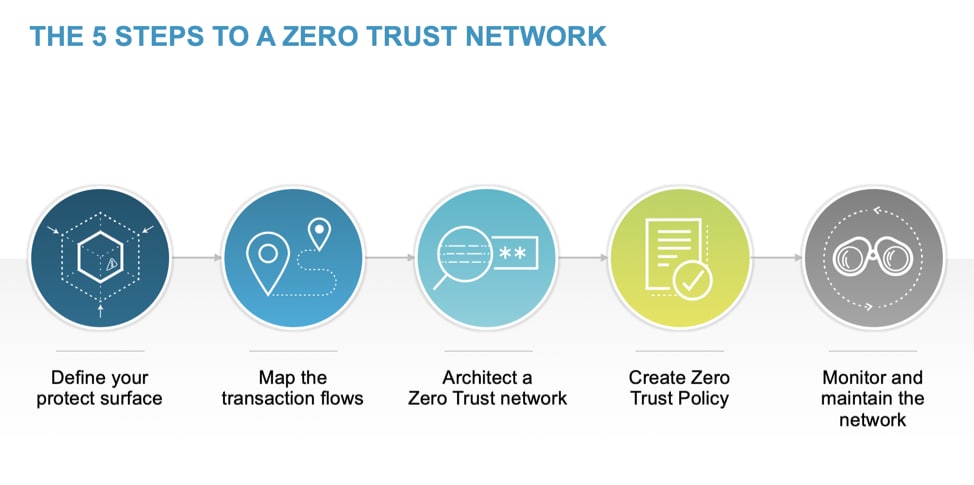
To better understand how to implement Zero Trust, there is a five-step methodology that simplifies the deployment of Zero Trust and, when followed, makes Zero Trust more than a buzzword, more like an achievable strategy that protects your most critical assets.
You can learn more about the five steps by reading the white paper, “Simplify Zero Trust Implementation Using a Five-Step Methodology.”