Gaining a continuous understanding of the state of cloud security, for most organizations, is downright painful. Security teams feel constantly behind the eight ball. Why? Because cloud service providers (CSPs) and cloud environments are in a greater state of flux than on-premises or private clouds.
This rapid pace of change presents an obstacle for any business. But it is a unique challenge for organizations seeking compliance with Federal Risk and Authorization Management Program (FedRAMP) authority to operate (ATO).
Given that Gartner found 81% of enterprises have a multi-cloud strategy, addressing this challenge requires a combination of tools and processes that are specifically designed for highly dynamic cloud environments. Here I present potential solutions tailored for FedRAMP seekers, but still applicable to any business
The Shift to FedRAMP Continuous Monitoring Requirements
As early as 2010, the Office of Management and Budget (OMB) had allowed static, point-in-time security assessments. But after an in-depth review, OMB changed course and required a move to “Ongoing Assessment and Authorization throughout the system development lifecycle.”
This radical shift was a wise first step toward acknowledging that security works best when it’s organically embedded into the entire application lifecycle. Without knowing it, this was an early nod toward components of what we now call DevSecOps. FedRAMP quickly followed suit and developed a continuous monitoring framework based on the National Institute of Standards and Technology (NIST) special publication 800-137. This framework is what CSPs must follow and regularly report on to maintain their authorization for a service.
High Velocity Plus Scale = Challenging FedRAMP ATOs
The high velocity of change in cloud computing environments makes achieving and maintaining FedRAMP ATOs challenging. To put things in perspective, research indicates that the average lifespan of a cloud resource is 127 minutes. Compare that with a legacy application that could have a lifespan of years. The problem is then further amplified in large cloud computing environments with thousands of resources. The end result is weak security and compliance postures across public cloud computing environments.
A Four-Step Approach
Building on NIST 800-137, we’ve developed a simplified four-step approach that could be helpful in achieving a multi-cloud ATO.
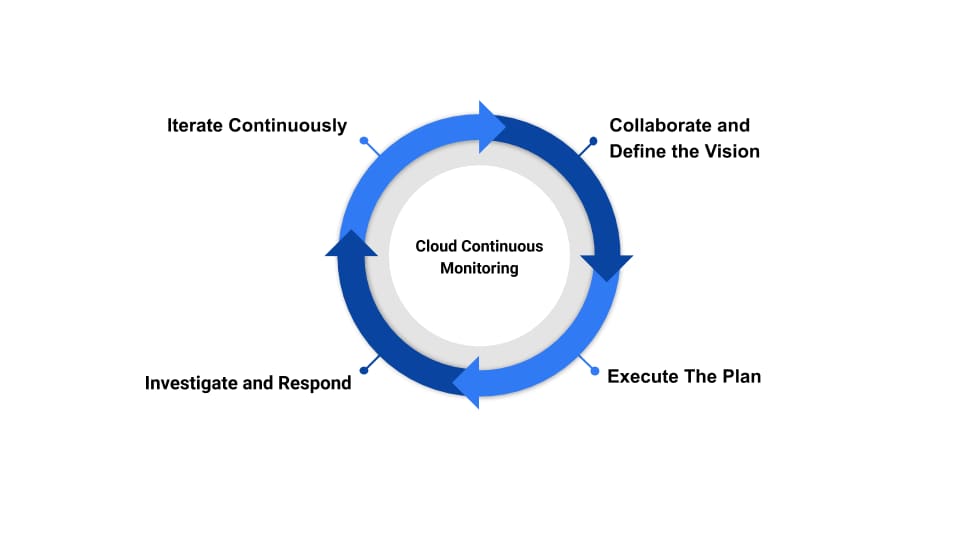
1. Collaborate and define the vision![Cloud continuous monitoring (including the monitoring needed to meet FedRAMP continuous monitoring requirements) involves a cycle of steps, shown here, including: 1) Collaborate and define the vision, 2) Execute the plan, 3) Investigate and respond, and 4) Iterate continuously]()
It is easy to jump directly into the technology side of security without first considering what your organization and leadership are trying to achieve. Step back and look at the bigger picture. In this first step, you’ll work across your organization to understand requirements from the likes of development teams, as well as FedRAMP. Many teams will need to be involved to make this a success so remember to work broadly. The clearest path to an ATO is a well-defined strategy that includes vision, goals, milestones and resources.
Organizations need to keep in mind that FedRAMP requires evidence of a continuous monitoring program collected, at a minimum, monthly, annually, every three years and on an as-needed basis after an ATO is granted. Make sure your strategy encapsulates all cloud accounts and systems in scope for the FedRAMP ATO.
2. Execute the plan
You’ve created the vision, discussed it amongst your peers and the organization is aligned behind it. Now it's game time. In this critical step, you’ll likely get down to the nuts and bolts of how your organization is going to carry out the FedRAMP continuous monitoring requirement.
A typical decision made in this step will include the mountain of tools that can be utilized to carry out the automated monitoring requirement. Engineers love to build, and when it comes to cloud security, some DevOps teams try to cobble together their own solution from a combination of cloud-provided and disparate open source products.
Before your team spends too much time and too many resources on a DIY security project, be sure to factor in cost, time, long-term support and maintenance, and multi-cloud support. Be realistic about your continuous monitoring goals. Cloud service providers offer an appealing menu of services that can, with enough time and resources, be woven together into a fairly comprehensive security solution. But does your organization have the time, expertise and desire to essentially create and sustain your own multi-cloud security tool?
3. Investigate and respond
The good thing about continuous monitoring programs is that, if done correctly, they will unearth security issues you were likely completely unaware of. This is why, as part of your strategy, you must have a well-defined process for investigating and responding to bugs found as part of your continuous monitoring program.
Organizations looking to minimize manual efforts will want to investigate security orchestration, automation and response (SOAR) platforms. These platforms take much of the burden off security operations centers (SOC). They can help automatically remediate issues where possible by acting as the intermediary between security controls, both third party and CSP-provided. They can also act as the workflow monitor between different teams that each may have partial ownership in resolving a security issue.
4. Iterate continuously
The systems that are in scope for your FedRAMP ATO will no doubt change over time – and so should your continuous monitoring program. CSPs will add new functionality, and your development teams will want to take advantage of them. Depending upon the scale of your cloud usage, your organization should consider a regular review process of any continuous monitoring program. Review the attack surface of the in-scope systems and make the determination if what’s being monitored still meets FedRAMP requirements. Discovering what’s running in a multi-cloud environment can be challenging, but thanks to cloud native security platforms that leverage cloud provider APIs as well as their embedded security tools, this is not as challenging as it used to be.
What Versus How
Organizations contemplating their FedRAMP certification need to strongly consider their continuous monitoring approach, including people, process and technology. Although FedRAMP requirements are clear, how this is actually carried out will largely be dependent upon your organization and your third party assessor (3PAO).
Prisma Cloud is a comprehensive cloud-native security platform with broad security and compliance coverage throughout the development lifecycle and across multi- and hybrid cloud deployments. The Prisma Cloud integrated approach enables security operations and DevOps teams to stay agile, collaborate effectively and accelerate secure, cloud native application development and deployment.
Prisma Cloud also helps simplify compliance for organizations by utilizing a comprehensive library of industry compliance standards and policies, including NIST 800-53, ISO 27000, SOC 2, NIST CSF and many others. To learn more about how Prisma Cloud can support your journey toward FedRAMP ATO, view our page on comprehensive cloud native security.