This post is also available in: 日本語 (Japanese)
Last year was besieged with unprecedented events. From the massive shift of work-from-home mandates, to the extensive impacts from supply chain attacks (like SolarWinds), our global network infrastructure has never seemed more vulnerable. To that end, your SOC teams need all the support they can get to successfully defend and protect against today’s attacks. This can be obtained in four simple steps toward SOC transformation.
Step 1: Auditing Your Environment Helps Reduce Security Risks Associated with Tool Sprawl
Leonardo da Vinci once said, “Simplicity is the ultimate sophistication.” Due to acquisitions, mergers and a lack of standardization for similar security products, many organizations are burdened with a disparate swath of tools across their security stack. To put it simply, they have too many tools that result in too many issues. With resources both in cloud environments and on-prem, security IT teams are challenged with having complete visibility of their attack surface.
For some teams, tool sprawl can begin by deploying a point solution to fix a specific issue. Unfortunately, this piecemeal approach, combined with managing numerous agents, can ironically leave networks even more vulnerable, exposing gaps due to issues from a lack of interoperability and improper configurations.
Auditing identifies as many risks as possible, whether they’re software or physical assets. Your organization can better prioritize whether to protect high-value or high-risk data.
As reported by ESG (Enterprise Strategy Group) in a 2019 survey of 406 IT and cybersecurity professionals (U.S. and Canada), 42% of respondents used between 10 and 25 security tools; another 26% used between 26 and 50 security tools.
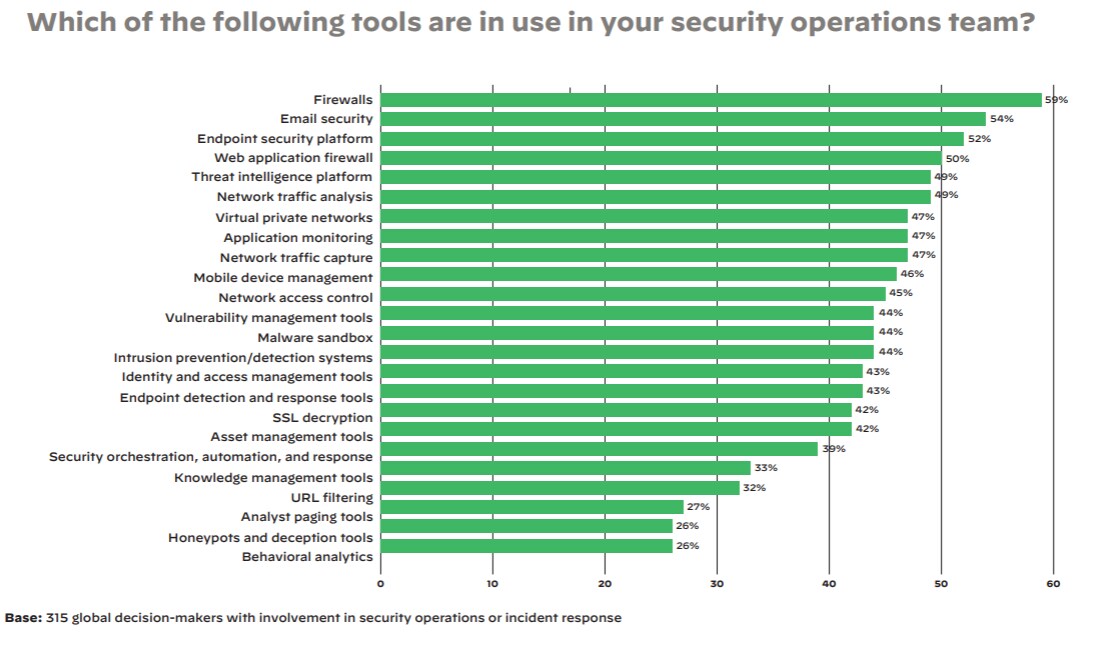
Step 2: Automate Workflows
As a security leader, you must consider whether tools require a human to configure or run them. Should an expert interpret or triage the result? Are people needed to test things? Security leaders can identify repeatable, low-level tasks that can work with human decision-making to help accelerate incident investigations. While advancements in machine learning and artificial intelligence hold great promise, retaining the human element for knowledge transfer in either direction is imperative to achieve optimal outcomes for a smooth SOC transformation.
There are too many manual processes involved in security operations and incident response (IR), including numerous threat feeds to monitor. Investing in automation capabilities (such as those in a SOAR solution) can help orchestrate actions across the product stack for faster and more scalable IR.
Manual Alert Investigations Plague Teams
One area that is a continued sticking point for SOC teams is managing the number of alerts. Deploying solutions that can automate a range of tasks, decisions and workflow associated with alert triage (alert prioritization/ranking, causal event correlation and enrichment) can help streamline investigations.
Even after deploying a SIEM or other solutions for better security insights and visibility, SOC teams are often flooded with low-fidelity alerts generated by their security controls. A 2019 survey of CISOs reported that “over 41% see more than 10,000 and that some claim to see more than 500,000 alerts daily.
As one would expect, these types of numbers are not sustainable. The overwhelming number of false positives creating “noise” is often a result of a combination of poorly tuned algorithms, legacy detection tools and/or configuration errors.
These issues, combined with a lack of correlation from disparate tools and operations, are often done in silos and don’t always enable consolidation of event data. Even the use of SIEM or log management tools require tuning or customization to accurately correlate alerts. What further muddies the waters is that even though tools may trigger alerts, they are not necessarily malicious. As such, many low-fidelity alerts go ignored.
Step 3: Augment People with ML-Driven Intelligence
A key component in a modern SOC transformation is to ensure that security teams are leveraging machine learning to its full potential to augment and complement humans in security. By automatically detecting anomalous patterns across multiple data sources and automatically providing alerts with context, machine learning today can deliver on its promise of speeding investigations and removing blind spots in the enterprise.
This works by training machine-learning models, using them to detect patterns among and across the data, and then testing and refining the processes. ML techniques can gather, integrate and analyze data to interrogate the data and reduce the amount of time and knowledge needed for a human to perform these tasks. This also minimizes the challenge for a SOC team trying to find threat context and evidence across multiple layers of security that are embedded in data.
Supervised machine learning techniques can be used to fingerprint devices, such as desktop computers, mail servers or file servers, and then learn the behavior of different types of devices and detect anomalous behavior. The promise of machine learning is having the ability to determine causal inferences around what is happening in an environment and letting the software direct next steps instead of relying on human interaction. For instance, the software can flag “bad” actions based purely on behavior and interactions within the joined datasets to then propagate a decision to the rest of the network with explicit instructions (such as, instructing an agent to contain it or a firewall not to communicate with it.)
High-level, machine-learning capabilities can:
- Integrate – Enable the data to tell a story about what is happening.
- Analyze – Extract insights about the problem space and make predictions.
- Automate – Accelerate human decision making, automate system-level action, workflows and decision making.
Step 4: Optimize Security Teams
Beyond security solution and tool investments, the most important factor in any successful SOC will remain the human element. While machine learning and automation will undoubtedly improve outcomes like response times, accuracy and remediation overall—especially for low-level, repetitive tasks—attracting, training and retaining security personnel (including engineers, analysts and architects) needs to be baked into any cohesive SOC transformation strategy.
According to the Bureau of Labor Statistics, the number of individuals employed within the cybersecurity sector is slated to grow by 31% between 2019 and 2029. Additionally, the National Center for Education Statistics (NCES) shows the number of new cybersecurity programs has increased by 33% while cybersecurity job postings have grown by 94% in the past six years.
SOCs Can Come in Many Flavors
At Palo Alto Networks, our SOC story is highly optimized in that we actively choose to break away from the traditional four-tier SOC approach. Taking more of a hybrid approach, the Palo Alto Network SOC team follows this general philosophy:
- Staff the SOC with 80% of people who have previous SOC experience.
- Cross-train the SOC team in all domains, including alert triage, incident response, threat hunting and others.
- Provide a well-funded annual training budget for all analysts.
Our rationale is that we can:
- Maintain a nimble team, able to pivot between responsibilities (and tiers).
- Support business continuity.
- Provide a more engaging atmosphere and reduce staff burnout.
- Promote an environment of continuous learning.
- Provide greater coverage with less staff by relying on the right technology to get the job done.
Start transforming your SOC by checking out our playbook, How to Plan Tomorrow’s SOC, Today