The buzz around Zero Trust is amplifying across the higher education community as institutions look to fortify their cyber defenses against threats, like ransomware, and adopt processes to meet the security challenges of remote work. Your institution may be among those wondering how to make Zero Trust actionable, and how doing so can help you meet the data protection and security priorities outlined by EDUCAUSE in its 2022 Top 10 IT Issues list.
If you’re struggling to understand what Zero Trust is all about, you’re in good company. We’re getting a lot of questions from our customers in higher education, and across many other industries, about what Zero Trust means and what the Zero Trust journey entails. To help get your arms around Zero Trust, let’s start from the top.
What Is Zero Trust?
Zero Trust is a strategic approach to cybersecurity, not a single product, that secures an organization by eliminating implicit trust and continuously validating every stage of a digital interaction. It’s a way for higher education institutions to build resilience into their IT networks and environments.
The Zero Trust mantra is “trust nothing, validate everything.” By embracing a Zero Trust Model, your organization commits to moving away from inherently trusting whatever is inside your security perimeter – users, applications and infrastructure. You transition over time to continually authenticate, authorize and verify who and what can access your environment, granting “least-privilege” access all along the way. Authorization is based on who or what is requesting access, the context of the request and the risk level.
At Palo Alto Networks, we refer to users, applications and infrastructure as the three “pillars” of a Zero Trust Model. The figure below outlines the actions that must be taken consistently with these pillars: establishing identity by using the strongest authentication possible – verifying the device and workload, securing access and securing all transactions.
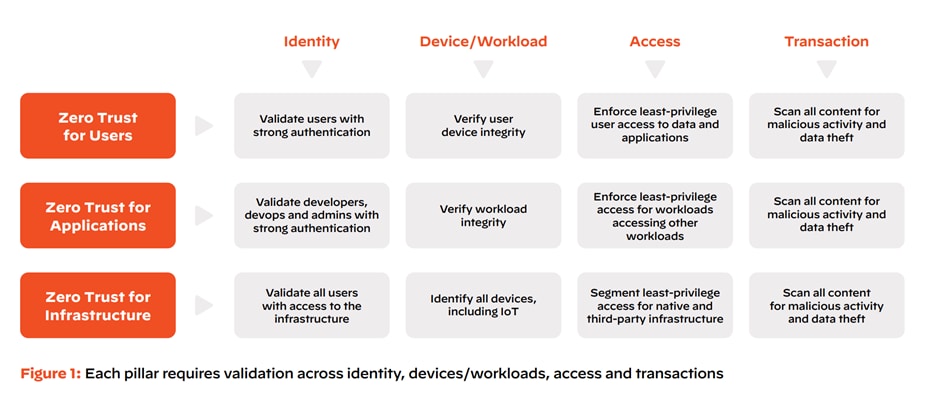
Zero Trust Is a Journey
It’s important for your higher education institution to understand that by implementing a Zero Trust approach, you’re adopting an iterative process, and your strategy will need to keep evolving as new threats, technology and ways of working change. Because Zero Trust is a methodology, it requires a mindset shift, which takes time to unfold and solidify.
Your organization can still make meaningful progress with Zero Trust in the near term; however, by determining where it can reduce acute risk and achieve resilience. There are some immediate actions to consider:
- Identifying Quick Wins – See where you can make the best use of existing resources. Conduct an audit of what controls you have in place today and optimize those products and solutions.
- Gaining Broad Visibility Into Securing Your Environment – Identify key assets and critical data; know who and where your users are and what devices are connected to your network.
- Determining Where You Currently Have the Most Control Over Data and Digital Interactions – Look at data center applications, power users and managed assets as these are some areas where you can likely make quick progress with reducing risk and implementing Zero Trust practices.
All of these measures will also help your organization move the needle on meeting the data protection priority outlined by EDUCAUSE in its 2022 list of top IT risks for higher education institutions.
A Zero Trust approach can also help your organization tackle number eight on the EDUCAUSE list “Weathering the Shift to the Cloud.” Many organizations in the public and private sectors today are applying Zero Trust principles so they can modernize their cloud native security strategy.
You Don’t Have to Make the Journey Alone
Zero Trust, when implemented properly, offers significant benefits to higher education institutions, including reduced risk, simplified operations and greater operational efficiency. While the Zero Trust journey can be challenging, the good news is that you don’t have to go at it alone. We have resources that can help you get started on making your Zero Trust journey actionable.
The Palo Alto Networks Professional Services team can help guide you in the right direction with a high-quality and integrated set of capabilities that can provide your higher education institution with holistic Zero Trust guidance. Our Professional Services team has years of experience and can help you accelerate your Zero Trust initiatives, achieving the best security outcomes, no matter where you are in your journey.
Your organization can also engage Palo Alto Networks Unit 42 team to conduct a proactive cybersecurity assessment. This exercise can give you the upper hand against adversaries by evaluating your controls, finding hidden vulnerabilities and testing your response capabilities to reduce the likelihood and impact of a breach. It provides a great starting point for evaluating where you are in your Zero Trust journey and determining the best way to move forward.
You can also contact the Palo Alto Networks higher education team.