This post is also available in: 日本語 (Japanese)
Mastering ZTNA 2.0 for Optimal Access Security
COVID launched a cybersecurity headache for many companies as remote use of applications exploded. There’s an expectation that employees will be granted access to business applications without increasing the organization’s attack surface. As part of a security strategy, validating remote workforces accelerated a need for Zero Trust Network Access (ZTNA) security policies.
But, the first iteration of ZTNA (ZTNA 1.0) exhibited some limitations, like inadequately instituting the critical principle of least privilege – simply stated, “Trust no one.” Enter, ZTNA 2.0.
Prisma Access uses ZTNA 2.0 principles for all mobile users and remote networks, raising the level of security for your total enterprise. And when you want to ensure optimal access security, our education services help you get the most out of your Prisma Access deployment.
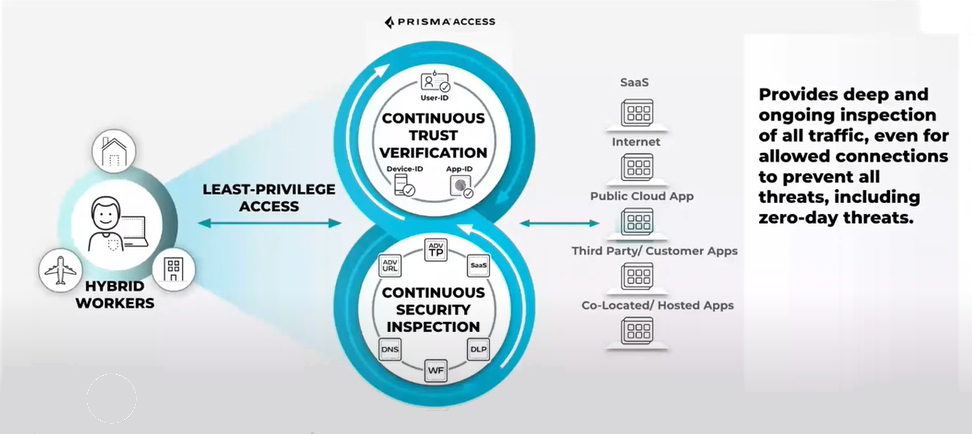
ZTNA 2.0 Goodness
The principles of ZTNA 2.0 work through Palo Alto Networks Prisma Access and are essential to validating application access and users working from home or in remote offices. ZTNA 2.0 uses five tenets to assure the highest level of access and validation:
- Least Privilege Access – Delivers the most stringent trust enforcement, providing access control from the network layer (OSI layer 3) to the application layer (OSI layer 7) independent of network constructs like IP and port numbers.
- Continuous Trust Verification – Trust is continually assessed based on changes in device posture, user behavior and app behavior, providing the ability to react in real time to any and all changes.
- Continuous Security Inspection – Provides deep and ongoing inspection of all traffic, including allowed connections, to prevent all threats and threat vectors, like zero-day threats.
- Protection of All Data – Protects application data across any application used in the enterprise, including private apps and Software as a Service (SaaS) with a single Data Loss Prevention (DLP) policy.
- Security for All Apps – Safeguards all applications used across the enterprise, including modern cloud-native apps, legacy private apps, SaaS apps, apps that use dynamic ports and apps that leverage server-initiated connections.
Even with all this goodness, things happen that require changes to your Prisma Access or ZTNA 2.0 environment. Platform updates, software upgrades, adding additional products, onboarding new users, scaling globally and so on can impact the environment. New functionality may need to be configured and provisioned, security policy decisions may need to change, etc.. These changes could leave a security gap, and criminal minds are always hard at work trying to find a security hole. Once initial deployment happens, your team now has the responsibility of securing access controls. Keeping your staff skilled in the rich features of Prisma Access and ZTNA 2.0 is how you can ensure that you do it right.
Upskilling Your First Line of Defense
It’s not difficult to master Prisma Access, an advanced Secure Access Service Edge (SASE) implementation, or ZTNA 2.0. But, it takes an ongoing commitment to stay current with changes in your environment and software. How do you achieve internal subject matter expertise?
You either hire them or train them. Given there’s over 3.5 million open cybersecurity jobs, we suggest education and training as your first line of defense. Much like the ongoing investment in working out to stay healthy, investing in education and training keeps your Prisma Access deployments using a ZTNA 2.0 approach healthy, eliminating security gaps and ensuring an optimal security posture.
Palo Alto Networks education, instructor-led training, free self-paced learning and certifications encourage mastery in Prisma Access, ensuring ZTNA 2.0 tenets are implemented across your environment and securing access no matter what location.
Don’t wait, create an account in Palo Alto Networks Beacon Learning System to get started. All that is required to take our fundamentals of cybersecurity courses is an email address.
Free, self-paced Prisma Access digital learning courses and industry-leading micro-credentials for remote user administrators and remote network security administrators ensure that you and your practitioners have the necessary skills and expertise to leverage ZTNA 2.0 with Prisma Access.
Develop knowledge and skills in the following Prisma Access and ZTNA 2.0 actions:
- Plan and design environments
- Activate and configure tenets
- Configure service infrastructure, API scripts used to retrieve IP addresses, IPSec VPN tunnels and service connections
- Setup service connections and accurately read traffic logs
- Enable GlobalProtect and explicit proxy for mobile users
- Onboard mobile users
- Configure security policies and profiles
- Setup authentication, cloud identity engine and identity redistribution
- Define web-access policies
Hone your Prisma Access expertise with instructor-led training. Students get hands-on experiences putting ZTNA 2.0 scenarios into practice. Fine tune your skills:
- User management
- User identity validation
- Application data structures and people
Like a good workout routine, ongoing education and training requires commitment and effort, an investment in knowledge that keeps you in front of access-related security incidents.
Learn more about our cybersecurity courses.