As 5G continues to gain market momentum and more and more enterprises embrace it for their wireless transport, an important question arises which must not be ignored. Who is responsible for making 5G secure? Security for 5G networks does not fall solely in the lap of the 5G radio and packet core vendors, nor does it fall solely in the lap of the enterprises embracing 5G. Rather, 5G security is a shared responsibility, much like the one AWS has made famous for its cloud services.
There are many facets of a 5G deployment that must be secured. So, it's not surprising that there isn’t a single tool that will solve all the security challenges of a 5G deployment. Before we can understand which tools we ought to use to secure 5G networks, perhaps we should start by looking at the components that already exist and who has the responsibility for securing them. There are many ways to group the security responsibilities. We will group them by the responsibilities outlined by 3GPP and by the customers who use the network functions defined by 3GPP.
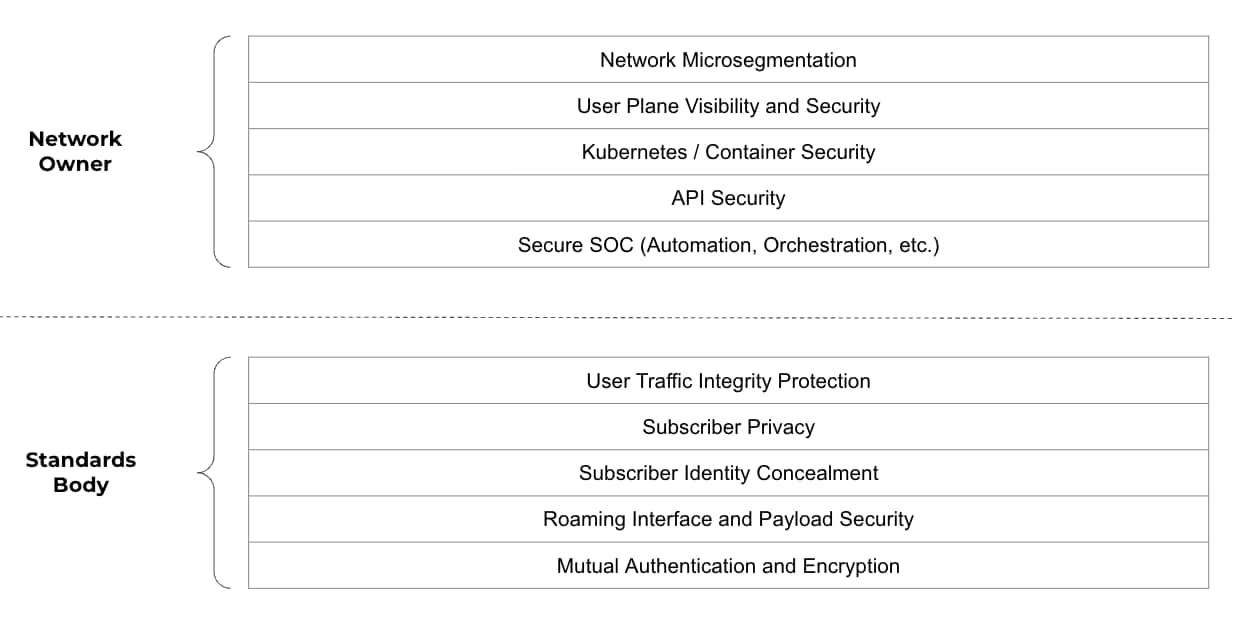
Let’s start by defining some of the security features 3GPP has built into 5G. The following are some of the features 3GPP offers in a 5G standalone network:
- User Traffic Integrity Protection
- Subscriber Privacy
- Subscriber Identity Concealment
- Roaming Interface and Payload Security
- Mutual Authentication and Encryption
Many of these features did not exist in 4G networks. So, it's worth noting that numerous important steps have been taken towards improved security for 5G wireless networks. However, there is more work that must be done. Below is a list of additional security considerations for 5G networks that go beyond what 3GPP has defined and fall squarely on the shoulders of the service providers and enterprises deploying 5G networks:
- Network Microsegmentation
- User Plane Visibility and Security
- Kubernetes / Container Security
- API Security
- Secure SOC (Automation, Orchestration, etc.)
These topics are important, so I will say a bit more on what each one entails, and some of the related threats.
Network Microsegmentation
This is a well understood security principle, which enables Zero Trust security and allows for the enforcement of least privilege access. It also reduces the “blast radius” if there is a breach in the network.
Suppose a network operator leaves an exposed endpoint, or one with a known vulnerability, access to the internet. Once that endpoint or server is compromised, Zero Trust security policies, if properly implemented, will prevent the attacker from pivoting to other critical hosts, such as Active Directory servers or source code repositories.
User Plane Visibility and Security
At Palo Alto Networks, we often say that you can’t secure what you can’t see. It's important to know all the applications and services running on your 5G network. Beyond that, it is important to ensure there are no threats present: Is the DNS query benign or malicious? Does the URL direct traffic to a phishing website? And, is that file being downloaded malware? If you see any threats or strange activity, it is important to identify the subscriber (SUPI) or equipment (PEI), so effective and timely action can be taken.
Imagine a warehouse with smart devices on the factory floor. In the event one of them is compromised via local access, any threat-related activity from that device, such as command and control query, will allow the enterprise or MSSP to rapidly detect which specific device is infected. This can only be done if the equipment ID (e.g. IMEI) is present in the threat log. With this high fidelity information, the SOC can act quickly and the mean time to remediation (MTTR) is greatly reduced.
Kubernetes / Container Security
Containers and virtualization are going to be a significant form factor for 5G networks. So, making sure they are secure before and while they are deployed is crucial. The ability to understand existing vulnerabilities in the libraries used in container images, as well as detecting anomalies as the container is running, are just a couple of the many features needed for Kubernetes/Container security.
Operators and enterprises who receive updated container images for their 4G and 5G core networks must ensure that there are no critical vulnerabilities in them before they are deployed. Since operators aren’t typically involved in the CI/CD pipeline of the companies building the network core software, they are often unable to “shift left” very far. The good news is they can still catch risky software images before they are deployed. Prisma Cloud can scan the images in the container registry and provide visibility into all the vulnerabilities per image. Using this feature, operators and enterprises can stop the deployment of a risky container before it happens.
API Security
The 5G Service Based Architecture will use numerous APIs for communication, both internally and externally, with elements, such as the Network Exposure Function. Additional APIs, such as those used for MEC and IOT, also need to be secured. Visibility and protection for APIs against DoS attacks, malformed requests and other attack vectors are a must for mobile networks.
5G will see an explosion of APIs, both internally and externally. The Camara Project is one such project that promises further use of APIs. Operators who implement these APIs will open up exciting new ways for their customers to interact with the network, such as getting device location information, request network quality, discover MEC platforms, etc. The APIs defined by the Camara Project will also open up numerous new attack vectors, which must be secured with API security, to prevent exploit attempts of those APIs, DoS attacks and other malicious API traffic.
Secure SOC
As threats are detected in a network, events are typically sent to a SOC for analysis. It's not uncommon for millions of events to hit a SOC each day. Prioritizing incoming incidents, removing false positives and allowing for rapid remediation are not easy tasks. Fortunately, tools like machine learning are perfect for helping here, along with automation, to leverage machines to reduce the noise, eliminate labor intensive repetitive tasks and speed remediation actions.
In 5G networks, the mean time to remediation (MTTR) can be critical, especially in networks supporting critical infrastructure. When alerts are triggered, numerous events should happen quickly to ensure a timely response. Tickets must be open, emails sent, API calls made, possibly even security policies updated, and all at machine speed. Humans will often just slow down the process and increase the MTTR, which is why automation and orchestration are so important.
The list of responsibilities above is certainly not comprehensive. Hopefully, this tally begins to highlight the different areas of security that enterprises and service providers will need to focus on as they deploy 5G. The standards have come a long way, and security is definitely better in 5G, but that is just the beginning, not the end of the journey.
The good news is that you do not have to take that journey alone. For more information on how to address the network owner’s security responsibilities discussed above, visit our 5G network security page for more insights.