- What Is Cloud Native?
- What Is Threat Modeling?
- CSP-Built Security Vs. Cloud-Agnostic Security
- What Is CNAPP?
- What Are Microservices?
- What Is Cloud-Native Security?
- What Is CSPM? | Cloud Security Posture Management Explained
- What Is Cloud Network Security?
-
Core Tenets of a Cloud Native Security Platform (CNSP)
- What Is a Cloud Native Security Platform?
- CSPM Tools: How to Evaluate and Select the Best Option
- What is Platform as a Service (PaaS)?
-
What Is Serverless Security?
What Is Microsegmentation?
Microsegmentation is a security method of managing network access between workloads. With microsegmentation, administrators can manage security policies that limit traffic based on the principle of least privilege and Zero Trust. Organizations use microsegmentation to reduce the attack surface, improve breach containment and strengthen regulatory compliance.
Microsegmentation Explained
Microsegmentation refers to an approach to security that involves dividing a network into segments and applying security controls to each segment based on the segment’s requirements.
Microsegmentation software with network virtualization technology is used to create zones in cloud deployments. These granular secure zones isolate workloads, securing them individually with custom, workload-specific policies. Similarly, each virtual machine (VM) in a network can be protected, down to the application level, with exact security controls.
The granular security controls microsegmentation brings to workloads or applications is invaluable for the modern cloud environment with several applications running on the same server or virtual machine. Organizations can apply security controls to individual workloads and applications, rather than having a one security policy for the server.
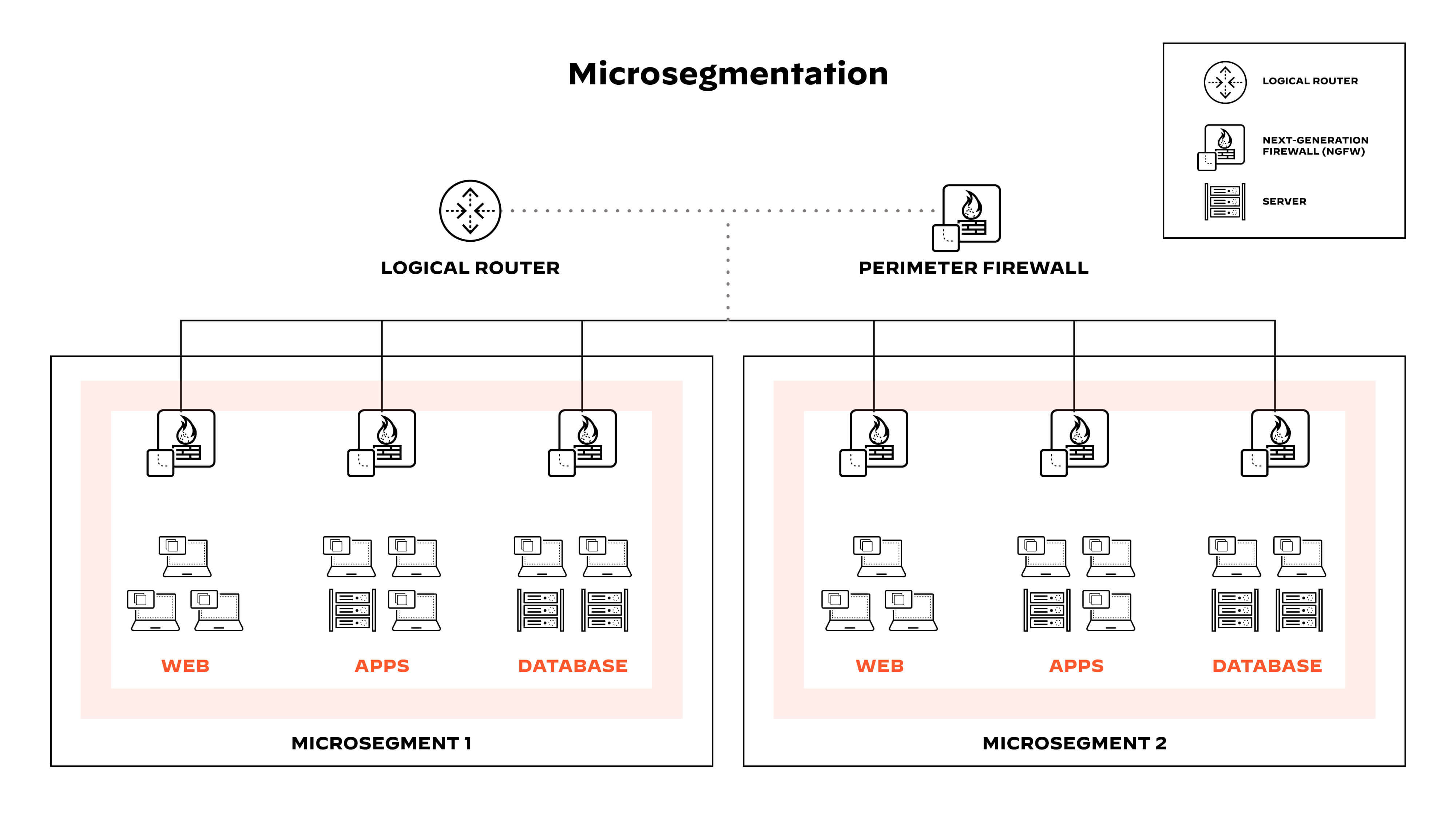
Figure 1: Microsegmentation divides networks into segments to limit traffic based on Zero Trust.
What Is a Workload?
A workload can be broadly defined as the resources and processes needed to run an application. Hosts, virtual machines and containers are a few examples of workloads.
Companies can run workloads across data centers, hybrid cloud and multicloud environments. Most organizations' applications are becoming increasingly distributed across different cloud-native compute architectures, based on business needs.
Beyond Perimeter Security
Perimeter security makes up a significant part of most organizations’ network security controls. Network security devices, such as network firewalls, inspect “north-south” (client to server) traffic that crosses the security perimeter and stop bad traffic. Assets within the perimeter are implicitly trusted, which means that “east-west” (workload to workload) traffic may go without inspection.
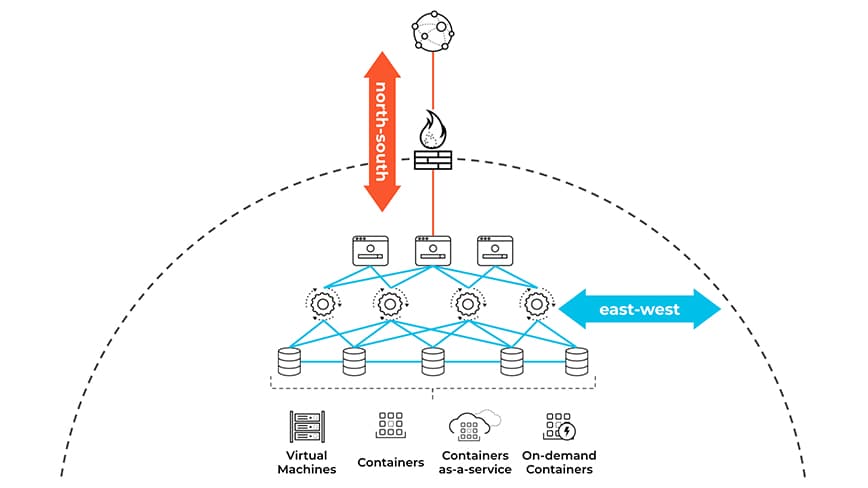
Figure 2: “North-south” (client to server) traffic vs. “east-west” (workload to workload)
For most organizations, east-west communications make up the majority of data center and cloud traffic patterns, and perimeter-focused defenses do not have visibility into east-west traffic. Given these factors, malicious actors use this as an opportunity to move laterally across workloads.
The network creates reliable pathways between workloads and determines whether or not two endpoints can access each other. Microsegmentation creates isolation and determines if two endpoints should access each other. Enforcing segmentation with least-privileged access reduces the scope of lateral movement and contains data breaches.
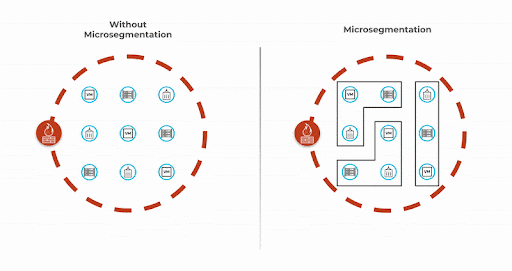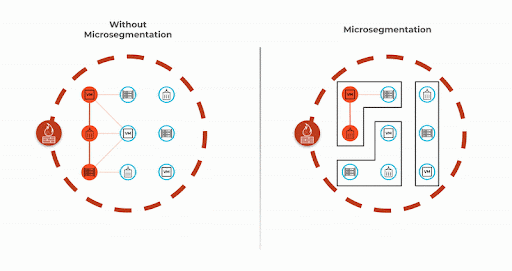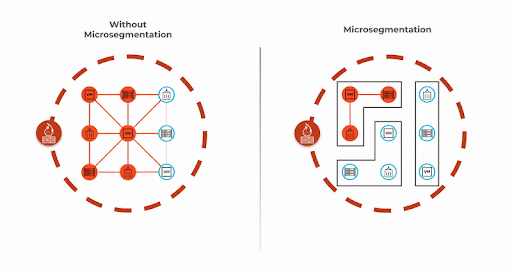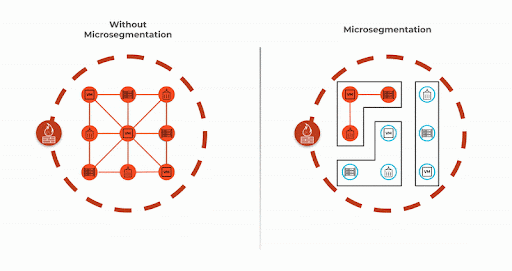
Figure 3: Microsegmentation can help you isolate the attack.
Network Segmentation Challenges
Network segmentation is an approach that divides a network into multiple smaller segments. This benefits performance and security:
- Performance: Subdividing the network into smaller subnets and VLANs reduces the scope of broadcast packets and improves network performance.
- Security: Network security teams can apply access control lists (ACLs) to VLANs and subnets to isolate machines on different network segments. In the event of a data breach, ACLs can prevent the threat from spreading to other network segments.
Leveraging network segmentation for security purposes comes with challenges. Segmentation needs don’t always match the network architecture. Re-architecting the networks or reconfiguring VLANs and subnets to meet segmentation requirements is difficult and time consuming.
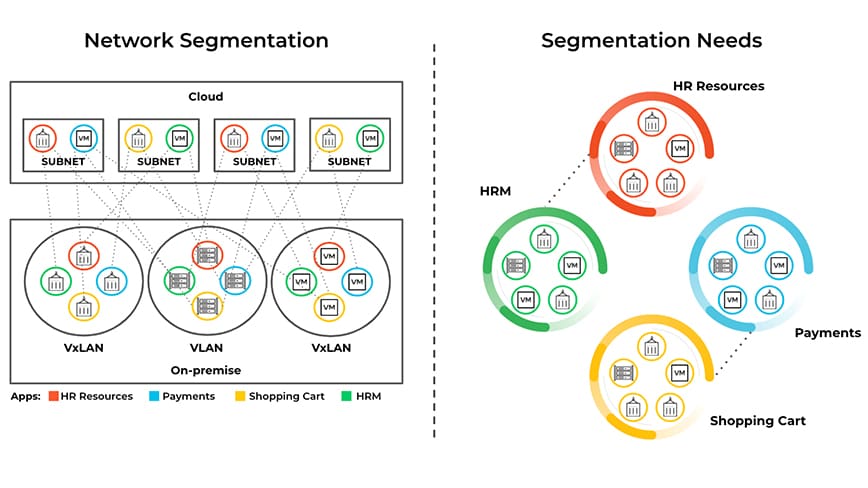
Figure 4: Network segmentation – using VLANs and subnets – is a method proven to deliver optimal network performance by breaking up network broadcast domains.
How Microsegmentation Works
Microsegmentation, also referred to as Zero Trust or identity-based segmentation, delivers on segmentation requirements without the need to re-architect. Security teams can isolate workloads in a network to limit the effect of malicious lateral movement. Microsegmentation controls can be assimilated into three categories:
- Agent-based solutions use a software agent on the workload and enforce granular isolation to individual hosts and containers. Agent-based solutions may leverage the built-in host-based firewall or derive isolation abilities based on workload identity or attributes.
- Network-based segmentation controls rely on the network infrastructure. This style leverages physical and virtual devices, such as load-balancers, switches, software-defined networks (SDN), and overlay networks to enforce policy.
- Native cloud controls leverage capabilities embedded in the cloud service provider (e.g., Amazon security group, Azure firewall, or Google Cloud firewall).
Microsegmentation helps provide consistent security across private and public clouds alike by virtue of three key principles: visibility, granular security and dynamic adaptation.
A microsegmentation solution should deliver visibility into all network traffic inside and across data centers and clouds. While there are many ways to monitor traffic, the most effective measure is to see traffic coupled with workload context (e.g., cloud, application, orchestrators), as opposed to logs containing only IP addresses and ports.
Granular security means network administrators can strengthen and pinpoint security by creating specific policies for critical applications. The goal is to prevent lateral movement of threats with policies that precisely control traffic in and out of specific workloads, such as weekly payroll runs or updates to human resource databases.
Microsegmentation offers protection for dynamic environments. For instance, cloud-native architectures like containers and Kubernetes can spin up and down in a matter of seconds. The IP addresses assigned to cloud workloads are ephemeral, rendering IP-based rule management impossible. With microsegmentation, security policies are expressed in terms of identities or attributes (env=prod, app=hrm, etc.) rather than network constructs (e.g., 10.100.0.10 tcp/80). Changes to the application or infrastructure trigger automatic revisions to security policies in real time, requiring no human intervention.
Types of Microsegmentation
Microsegmentation offers protection for dynamic environments. For instance, cloud-native architectures like containers and Kubernetes can spin up and down in a matter of seconds. The IP addresses assigned to cloud workloads are ephemeral, rendering IP-based rule management impossible. With microsegmentation, security policies are expressed in terms of identities or attributes (env=prod, app=hrm, etc.) rather than network constructs (e.g., 10.100.0.10 tcp/80). Changes to the application or infrastructure trigger automatic revisions to security policies in real time, requiring no human intervention.
Container Segmentation
Container segmentation involves isolating containers from each other and the host system to improve security and reduce the attack surface. Containerization is a widely used technology that allows multiple applications or services to run in separate containers on a single host system. Without proper segmentation, though, containers can potentially access each other's data and configuration files, which can result in security vulnerabilities.
Container Segmentation Best Practices
- Container isolation: Each container should be isolated from other containers running on the same host system to prevent unauthorized access. Isolation can be achieved using container technologies like Docker and Kubernetes, which provide built-in isolation mechanisms.
- Network segmentation: Containers can be segmented from each other using network segmentation techniques. Creating separate networks for each container and configuring firewall rules to allow or deny traffic between containers can achieve this.
- Role-based access control: Role-based access control (RBAC) can be used to define access policies for different containers based on user roles and permissions, which can help to ensure that containers are accessed only by authorized users and processes.
- Image signing: Container images can be digitally signed to ensure that only trusted images are deployed in production. This can help to prevent container images from being tampered with or altered. Proper artifact integrity validation can reduce the risk of security vulnerabilities.
- Runtime protection: Runtime protection tools can be used to monitor container activity and detect anomalies that may indicate a security breach. These tools can help to detect and prevent attacks in real time, improving the security posture of containerized environments.
Container segmentation helps to ensure the security of containerized applications and services. By isolating containers and applying access control policies, organizations can reduce the attack surface and prevent unauthorized access to sensitive data and resources. Container segmentation should be implemented as part of an overall security strategy that includes network security, access control, and runtime protection.
User Segmentation in Cloud Security
User segmentation in cloud security involves dividing user access based on different roles and responsibilities within an organization to ensure that users have access to only the resources they need to perform their job functions. User segmentation reduces the attack surface by limiting the exposure of sensitive data and resources to only authorized users.
Because cloud environments are dynamic and change rapidly, user segmentation is a critical component of a comprehensive cloud security strategy. Here are some key considerations for user segmentation in cloud security:
- Role-based access control (RBAC): RBAC involves creating and defining permissions for roles, and then assigning users to the appropriate roles according to job functions. This approach ensures that users have access only to the resources they need to perform their job functions, reducing the risk of accidental or intentional data breaches.
- Multi-factor authentication (MFA): MFA requires users to provide more than one form of authentication — a password, a security token, biometric data — to access a resource. MFA is an effective way to prevent unauthorized access to cloud resources, particularly when combined with RBAC.
- Continuous monitoring: Continuous monitoring of user activity is critical for detecting and responding to security incidents in real-time. This involves analyzing log data and user behavior to identify threats and vulnerabilities.
- Separation of duties: Separation of duties involves dividing responsibilities among multiple users to prevent any one user from having too much control over a system or process. Access management reduces the risk of fraud or errors and ensures that sensitive operations are performed by multiple users.
- Regular access reviews: Regular access reviews involve routinely reviewing user access rights and permissions to ensure they’re still essential. Access reviews can help to identify and remove unnecessary access rights, reducing the risk of unauthorized access.
By implementing RBAC, MFA, continuous monitoring, separation of duties, and regular access reviews, organizations can enhance their cloud security posture and protect against evolving threats, reduce the attack surface and prevent unauthorized access to sensitive data and resources.
Benefits of Microsegmentation
Organizations that adopt microsegmentation realize tangible benefits. More specifically:
- Reduced attack surface: Microsegmentation provides visibility into the complete network environment without slowing development or innovation. Application developers can integrate security policy definition early in the development cycle and ensure that neither application deployments nor updates create new attack vectors. This is particularly important in the fast-moving world of DevOps.
- Improved breach containment: Microsegmentation gives security teams the ability to monitor network traffic against predefined policies as well as shorten the time to respond to and remediate data breaches.
- Stronger regulatory compliance: Using microsegmentation, regulatory officers can create policies that isolate systems subject to regulations from the rest of the infrastructure. Granular control of communications with regulated systems reduces the risk of noncompliant usage.
- Simplified policy management: Moving to a microsegmented network or Zero Trust security model provides an opportunity to simplify policy management. Some microsegmentation solutions offer automated application discovery and policy suggestions based on learned application behavior.
Microsegmentation Use Cases
The range of use cases for microsegmentation is vast and growing. Here are some representative examples:
- Development and production systems: In the best case scenario, organizations carefully separate development and test environments from production systems. However, these measures may not prevent careless activity, such as developers taking customer information from production databases for testing. Microsegmentation can enforce a more disciplined separation by granularly limiting connections between the two environments.
- Security for soft assets: Companies have a huge financial and reputational incentive to protect “soft” assets, such as confidential customer and employee information, intellectual property, and company financial data. Microsegmentation adds another level of security to guard against exfiltration and other malicious actions that can cause downtime and interfere with business operations.
- Hybrid cloud management: Microsegmentation can provide seamless protection for applications that span multiple clouds and implement uniform security policies across hybrid environments composed of multiple data centers and cloud service providers.
- Incident response: As noted earlier, microsegmentation limits lateral movement of threats and the impact of breaches. In addition, microsegmentation solutions provide log information to help incident response teams better understand attack tactics and telemetry to help pinpoint policy violations to specific applications.
Microsegmentation FAQs
Microsegmentation, on the other hand, focuses on east-west traffic and is typically implemented using software-based security solutions, such as hypervisor-based firewalls or endpoint protection platforms (EPPs). Microsegmentation applies security policies at the individual workload or application level, rather than at the network level.