As cloud computing continues to increase in popularity, businesses should consider remaining vigilant in protecting their information. Enterprises are accelerating public and hybrid cloud initiatives and the release cycle for code deployment frequency is often exponentiating. Palo Alto Networks and Deloitte have expanded their strategic alliance with a new SSDL offering to reinforce their customers' cloud environments with enhanced security measures from code to cloud.
The expansion enables the customer to mitigate risks and promote a secure development and deployment lifecycle that adheres to their unique cloud security and compliance requirements. In the State of Cloud-Native Security 2023 survey from Palo Alto Networks, 55% of respondents indicated that they’re deploying code to production daily or multiple times a day. When the code release cycle increases, so does the risk of vulnerabilities and errors being included in the deployment.
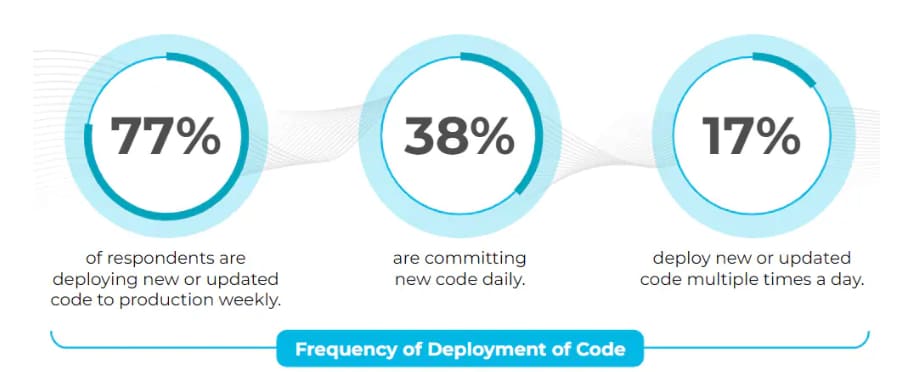
The expanded use of the cloud and open-source software, as well as the increased frequency of software deployment, create a complicated environment that increases risk to the enterprise. A developer may easily include a package that contains a vulnerability (Log4j, for example) exposing the cloud environment to intrusion, and potentially compromising customer data, code, as well as the uptime for the application.
Top Five Security Incidents
- Risk introduced early in application development
- Workload images with vulnerabilities or malware
- Vulnerable web applications and APIs
- Unrestricted network access between workloads
- Downtime due to misconfiguration
The security team must prevent this, but they are outnumbered by developers and must keep up with release cycles without causing delays.
Shifting Left in the Cloud
With the right strategies, enterprises could maintain a secure cloud environment while taking advantage of the benefits of cloud-based services. A leading strategy that businesses should consider is shifting left. Shift left security is a proactive approach that emphasizes the early detection and resolution of vulnerabilities and errors during the development cycle before they are deployed into production.
Top Challenges Providing Overarching Security
- Managing holistic security across teams
- Embedding security across the cloud-native development lifecycle
- Training IT/development/security staff to use security tools
- Lack of visibility into security vulnerabilities across cloud resources
- Finding the correct tools to address security requirements
The core concept of shift left security involves integrating security tools effectively within the DevOps lifecycle, allowing developers to work in their familiar environments while receiving alerts to potential issues.
Adopting a shift left security approach empowers development teams to take ownership of security and promotes a proactive security mindset. It allows developers to build secure and resilient applications from the outset. This minimizes the chances of vulnerabilities slipping through the cracks before it reaches production environments. By prioritizing security early in the development process, organizations can significantly reduce the potential impact of security incidents and establish that their applications are strong and secure from the ground up.
DevOps teams can conduct various security activities as part of the shift left approach — infrastructure-as-code scanning, container image scanning, secrets scanning and software composition analysis. But, implementing these processes in a complex multicloud environment can prove challenging.
Streamlining Cloud Security
Safeguarding your cloud environments requires a standardized approach to ensure your cloud environments are resilient, compliant and secure. You can achieve this by streamlining account provisioning, facilitating secure build and deployment practices, implementing strong logging and monitoring mechanisms, enforcing custom guardrails and automate remediations.
When effectively executed, SSDL incorporates shift left security into the DevSecOps pipeline, scanning code early in the process to identify vulnerabilities and other issues. This fosters a culture of secure-by-design and promotes transparency of security vulnerabilities. With the early identification of issues, this encourages tight collaboration between the dev, ops and security teams, and it drives agility and automation. The primary cybersecurity goal of the SSDL model is to reduce or remove manual controls that have historically impeded business and IT teams, such as cycle time issues, false positives and inefficient output.
These challenges have also contributed to the problem of identifying defects later in the development cycle when they’re more costly and difficult to remediate. SSDL utilizes cutting-edge technologies, such as Prisma Cloud, Cortex XSOAR, proprietary custom code and integrated workflows to help you effectively address your distinctive requirements.
Whether you’re implementing a design strategy, tactically building, deploying or need ongoing observability through assessments, SSDL can be effectively integrated as part of the overall solution. Or, it can be integrated within an existing cloud security and compliance ecosystem. Moreover, SSDL is designed to be highly scalable, accommodating diverse multicloud platforms regardless of your cloud journey.
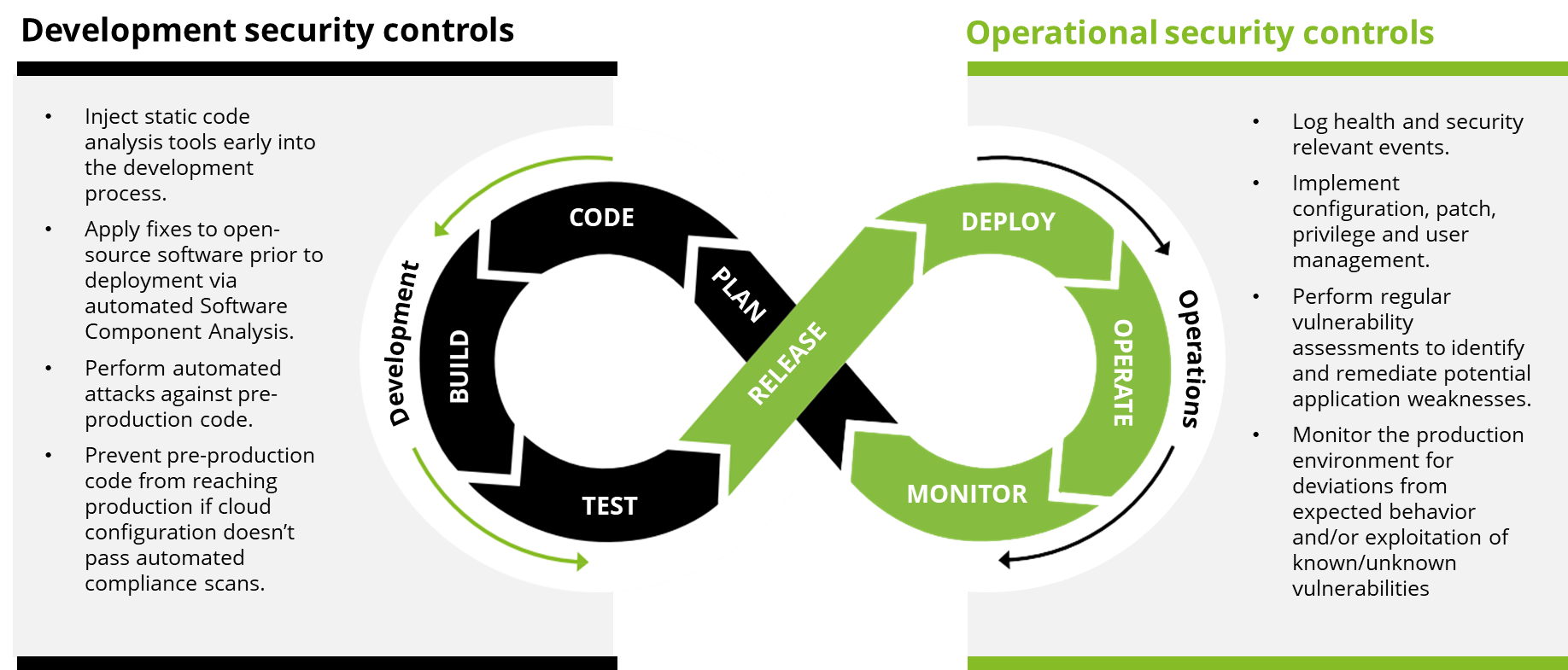
SSDL enforces security at every stage: code and build, deploy and run. The SSDL accelerators facilitate faster delivery of thoroughly assessed and securely configured infrastructure and applications into your cloud environments. This means you can continuously monitor deployed infrastructure for configuration drift while also enforcing automated, actionable workflows to ensure ongoing security and compliance. By integrating security into the development process from the beginning, you can effectively address vulnerabilities and risks, facilitating secure and efficient multicloud operations.
When building SSDL, Deloitte chose to collaborate with Palo Alto Networks as they provide market leading technology that provides the recognized outcomes for our clients. Transitioning to an SSDL empowered by Prisma Cloud and Cortex XSOAR is a strategic and iterative approach that yields manifold benefits. These potential benefits include enhanced security measures, heightened operational efficiency, improved product quality, alignment with industry standards, fostered collaboration among teams, cost reduction, and strides toward achieving a strong and future-proof security posture.
– Jane Chung, Managing Director, Deloitte & Touche LLP
Leveraging a shift left security approach and proactively monitoring for potential threats keeps critical data secure while still taking full advantage of the benefits offered by cloud services. With SSDL, potential issues may be identified early and resolved before serious damage occurs. In addition, it helps clients keep their team focused on other important tasks. If you're looking for ways to improve your cloud strategy, considering shift left and managed cloud security may be worth exploring.
Learn more about Deloitte and SSDL and what Prisma Cloud can do for you.
This blog contains general information only and Deloitte and Palo Alto Networks are not, by means of this blog, rendering accounting, business, financial, investment, legal, tax, or other professional advice or services. This blog is not a substitute for such professional advice or services, nor should it be used as a basis for any decision or action that may affect your business. Before making any decision or taking any action that may affect your business, you should consult a qualified professional advisor.
Deloitte and Palo Alto Networks shall not be responsible for any loss sustained by any person who relies on this blog.
As used in this blog, “Deloitte” means Deloitte & Touche LLP, a subsidiary of Deloitte LLP. Please see www.deloitte.com/us/about for a detailed description of our legal structure. Certain services may not be available to attest clients under the rules and regulations of public accounting.