In the modern enterprise, we tell ourselves that visibility is the foundation of security. But for security leaders navigating the chaotic intersection of multicloud environments and rapid AI adoption, "visibility" has become a loaded term.
The reality is that true visibility remains elusive, so cybersecurity professionals are often forced to make assumptions. It’s not a sustainable approach. As your organization embraces digital transformation, you are tasked with protecting a perimeter that is no longer static — it is dynamic, decentralized, and increasingly autonomous. The pressure to adopt new cloud services and AI technologies at speed creates a constant tension with the imperative to maintain governance.
The risk goes beyond not being able to see everything; it is that traditional security measures struggle to keep pace, creating visibility gaps that leave organizations unaware of their actual risk exposure until it is too late. This is the "fog of cloud" — where you assume you are protected, but lack the data to prove it.
The Need for a Holistic View
Discovery is only the first step, because the real challenge for security executives is translating that awareness of actual threats into a quantifiable risk posture.
To bridge the gap between assumption and reality, Palo Alto Networks introduced the Cloud Networks and AI Risk Assessment. Unlike standard assessments that provide a single point-in-time snapshot, CLARA delivers a multi-faceted analysis — all at no cost or obligation. The service combines three distinct, complimentary assessments into a single engagement for AWS and Azure environments, allowing you to tackle risk from three critical angles.
Angle #1: Network Assessment - Exposing the Hidden Perimeter
The first narrative thread in any security story is "the unknown." Driven by agile methodologies and decentralized development, Shadow IT makes it nearly impossible to maintain a real-time inventory of all cloud assets.
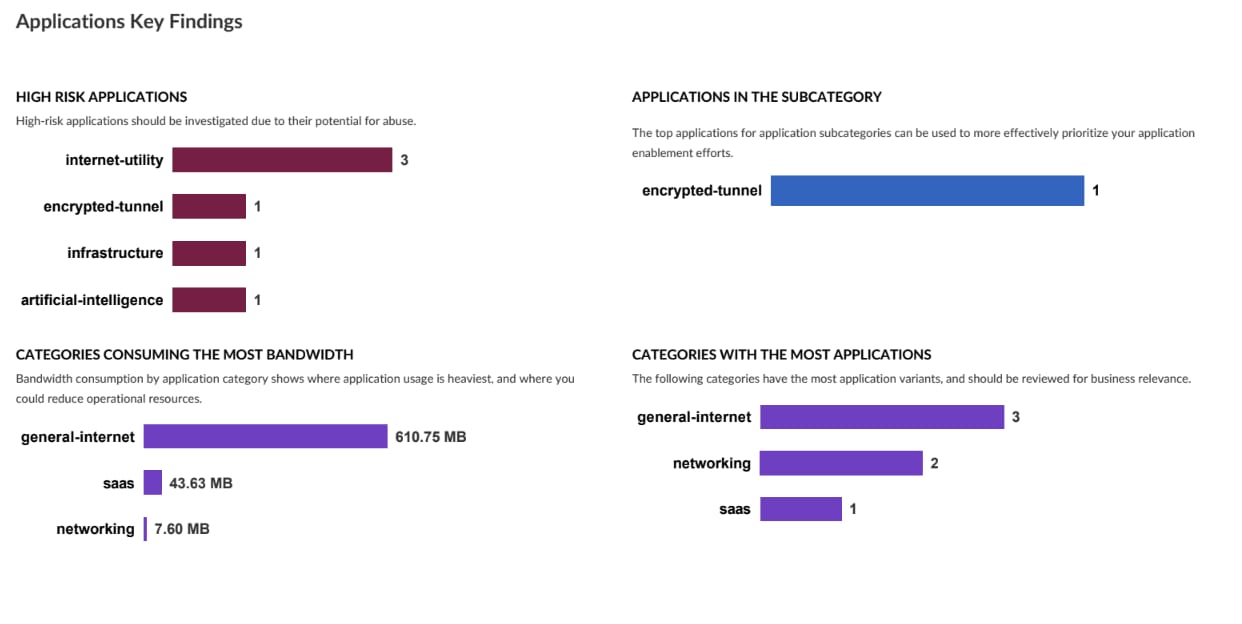
CLARA addresses this by automatically discovering workloads and applications to map your actual cloud perimeter and traffic patterns.
- The insight: You gain a complete, real-time inventory of all cloud workloads and AI apps, agents, and models.
- The outcome: This eliminates blind spots by identifying unknown or unsanctioned protocol usage and providing advanced threat analysis, allowing you to close the gaps attackers are most likely to exploit.
Angle #2: Firewall Benchmarking - The Reality Check
Once the perimeter is mapped, the narrative shifts to efficacy. Enterprises rightly question whether their existing cloud service provider (CSP) firewalls can stop sophisticated, modern threats. Are your controls actually working, or are you just assuming they are?
The Cloud Firewall Benchmarking component provides a data-driven answer by running targeted, real-world breach and attack simulations against your existing cloud firewalls in a controlled environment.
- The insight: You receive empirical, third-party validation of your CSP firewall's true security efficacy.
- The outcome: A Security Validation Report (SVR) details blocked versus allowed exploits, enabling you to make evidence-based decisions to validate the ROI of enterprise-grade threat prevention.
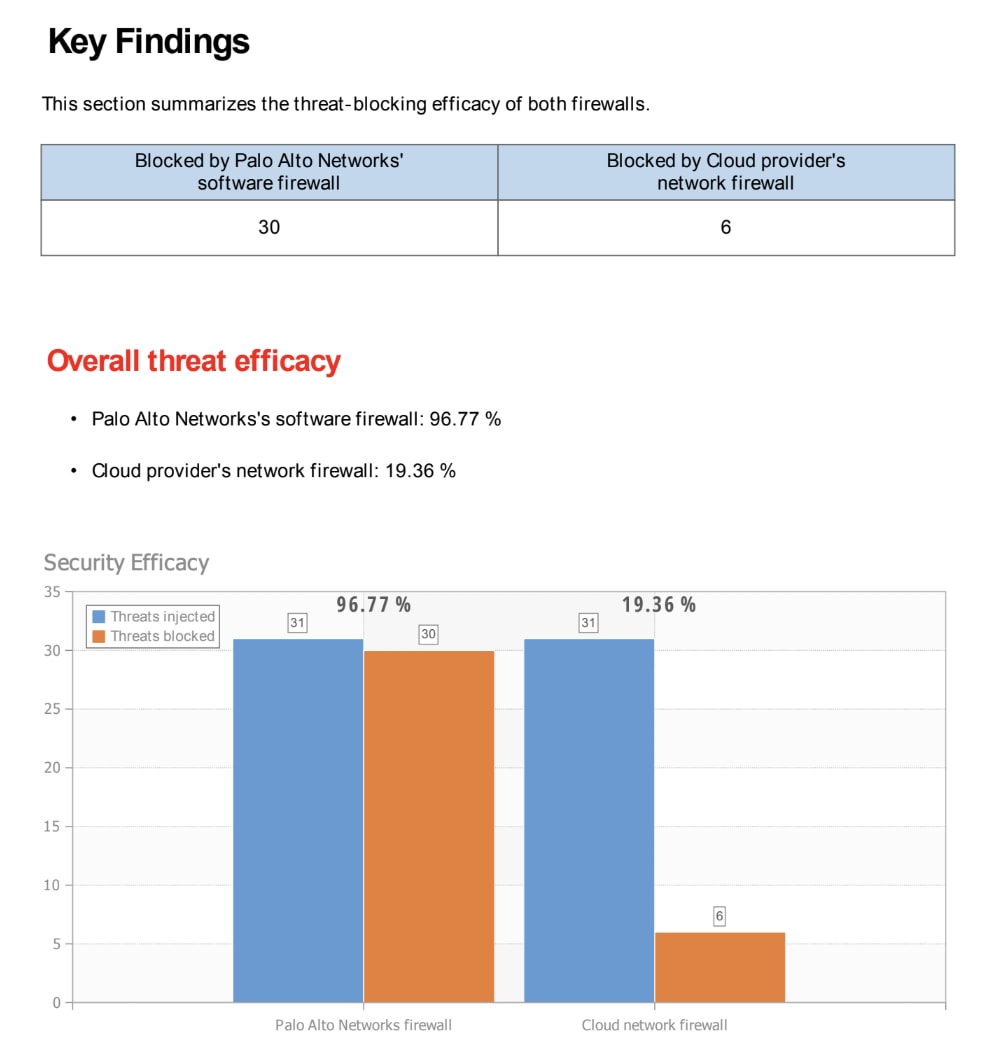
The Firewall Benchmarking Report comparing efficacy of blocked threats between cloud service providers and Palo Alto Networks Software Firewalls.
Angle #3: AI Risk Assessment - Securing the New Frontier
The final chapter in this saga turns to the most urgent security disruption: Artificial Intelligence. The "AI Black Box" conundrum — in which it is impossible to know how these systems reach their conclusions — presents two significant challenges. You need to secure the AI supply chain while protecting against runtime threats like prompt injections.
CLARA’s AI Risk Assessment scans models and datasets for malicious scripts or tampering to secure the supply chain and simultaneously performs Red Teaming exercises against live applications.
- The insight: You get an assessment of the complete AI ecosystem, from models and data to live applications.
- The outcome: By identifying vulnerabilities early — such as prompt injections or data tampering — you enable the organization to deploy new AI capabilities with confidence that your brand and data are protected.
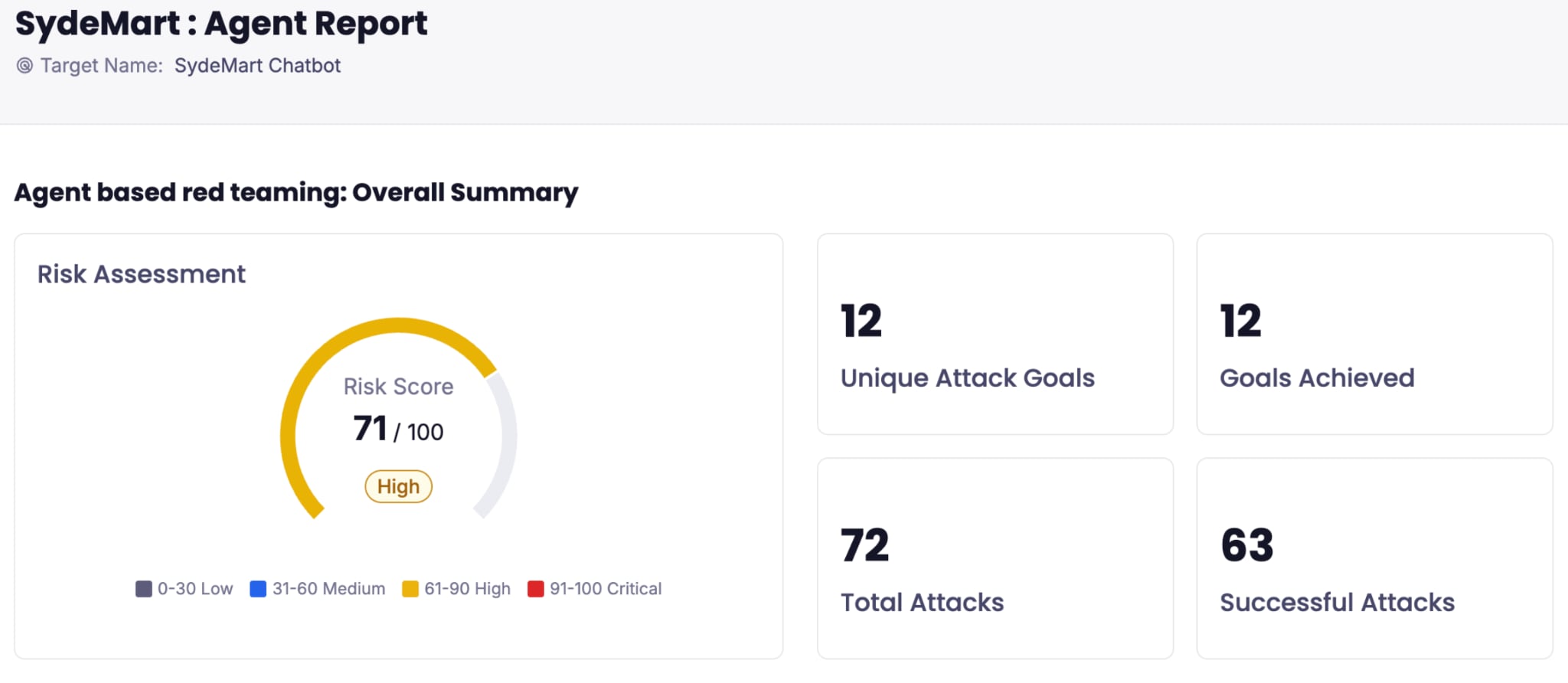
Output of the Red Teaming report showing risk score based on successful simulated attacks.
The Strategic Advantage of Integrated Risk Intelligence
For security leaders, risk is rarely isolated in a silo. But triangulating these three vectors — Network, Firewall, and AI — CLARA offers a unified view that fragmented tools cannot match. As a result, organizations can realize:
- Greater operational efficiency: Instead of managing three separate vendor engagements, you consolidate discovery and validation into a single, streamlined process.
- More security ROI: The assessment validates where your current controls are sufficient and pinpoints exactly where investment is needed, preventing over-spending on redundant tools while closing critical gaps.
- Accelerated AI enablement: By identifying the specific guardrails needed for your environment, you can shift from being a blocker of AI innovation to an enabler, providing the board with the assurance needed to accelerate digital transformation initiatives safely.
Make Strategic Decisions with Data
Ultimately, CLARA moves beyond simple observation to provide actionable intelligence. The comprehensive reports generated from these assessments are designed for immediate action, translating complex technical findings into a clear business-risk context.
This data empowers CISOs to align stakeholders — from technical teams to the board — by quantifying risk and prioritizing protections based on actual exposure, not just intuition.
Are you ready to replace assumptions with evidence? To baseline your current security posture and gain the data needed to drive your security strategy, request a complimentary Cloud Network & AI Risk Assessment today.