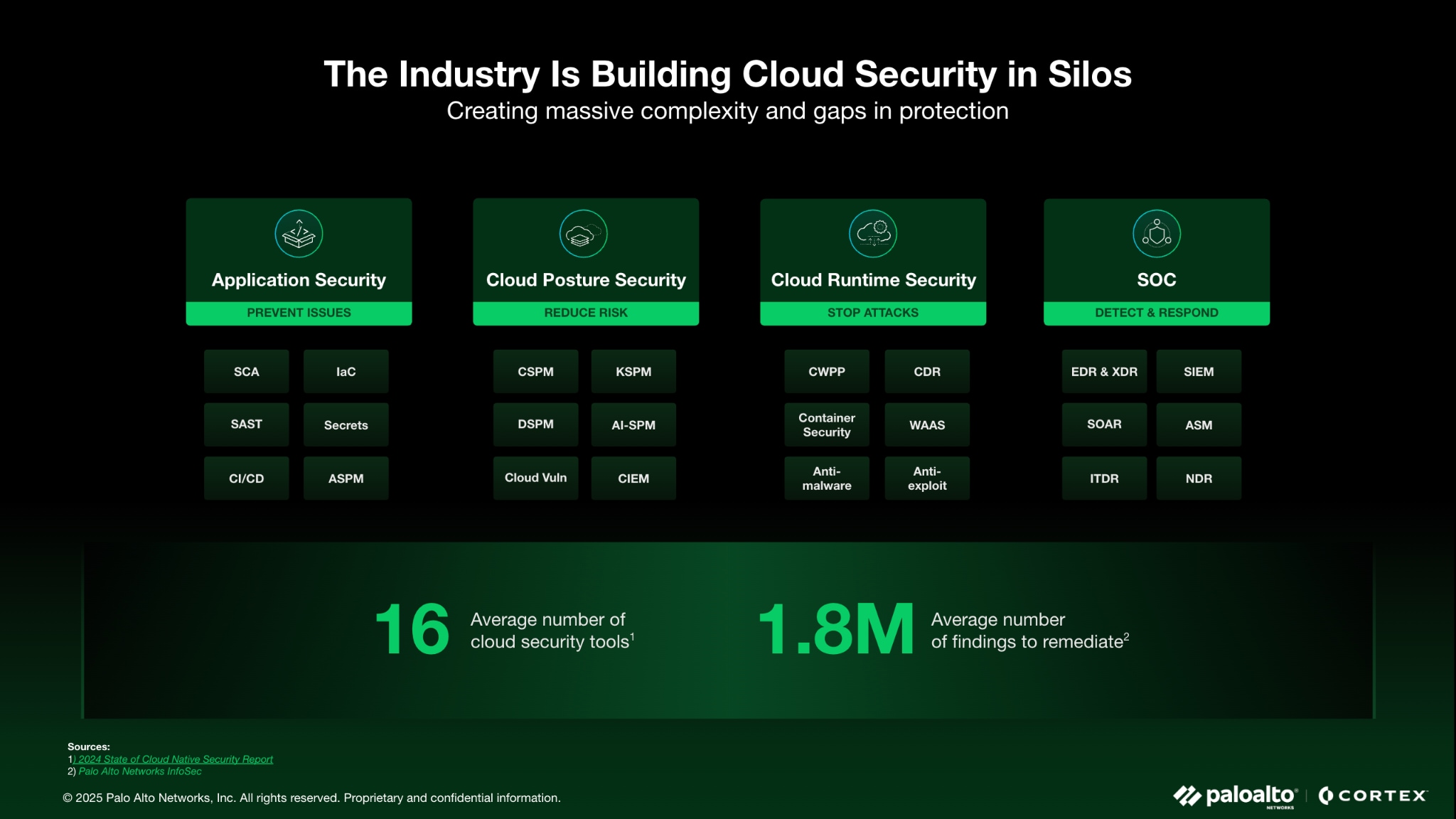
I’ve spent more than two decades in cybersecurity, and I see a paradox playing out in security organizations everywhere. Teams are managing an average of 16 different cloud security tools and are still missing critical vulnerabilities and breaches. Not that it isn't a failure of strategy. On the contrary, it's the inevitable result of confronting a rapidly evolving threat landscape with a patchwork of security products, each added to solve a specific, immediate threat.
Of course, the situation doesn't happen overnight. It's often the cumulative result of many individual decisions — a specific team choosing a best-in-class tool for their needs, or a new capability being added to solve an urgent problem. While each of these decisions may have been right at the time, the reactive approach has led to a fragmented security stack that creates dangerous visibility gaps, drives up costs, and ultimately weakens security posture.
The business case for consolidation is undeniable, yet many leaders find themselves trapped by the same solutions they bought to protect the business.
The resistance to change is especially pronounced in cloud-native application security, where development, DevOps, cloud security and SOC teams must collaborate across an increasingly complex landscape. The core problem is that the barriers to true security transformation aren't just technical. To build a defense that can match the speed of modern attackers, we must first understand the organizational inertia that holds us back.
The Technical Reality: Why Consolidation Matters
Before diving into the challenges, let's establish why this matters technically. Having spent over two decades watching the cybersecurity landscape evolve, I've witnessed firsthand how tool sprawl creates exponentially growing challenges:
Visibility gaps: When security data lives in disparate systems, critical context is lost. An infrastructure vulnerability reported in one tool may directly relate to an application weakness flagged in another, but without consolidation, this correlation remains invisible.
Alert fatigue: The average SOC analyst now processes over 11,000 alerts per day across multiple dashboards. Meanwhile, cloud security teams often have to deal with thousands of security findings. It’s clear that beyond a certain threshold, attention degrades dramatically, regardless of skill level or experience.
Integration overhead: Each tool requires maintenance, updates and custom integrations. During the past few years, I’ve talked with organizations where security teams spent roughly 60% of their time managing tools rather than addressing risks.
Cloud complexity multiplication: Modern cloud architectures introduce ephemeral resources, microservices, containers and serverless functions that traditional security models struggle to track. When multiple tools attempt to monitor these dynamic environments independently, gaps inevitably form at the seams.
Mean Time to Remediation (MTTR) extension: When a critical vulnerability is detected, the clock starts ticking. Consolidated platforms can reduce MTTR dramatically by eliminating context-switching and providing direct remediation workflows.
For cloud-native applications specifically, the problem complicates further. Kubernetes environments alone introduce dozens of configurable security parameters across nodes, pods, containers and network policies. When monitored through separate tools for vulnerability management, CSPM, CWPP, CIEM, KSPM and API security, critical relationships between these elements become obscured.
Five Barriers to Consolidation
Despite these clear technical imperatives, resistance may persist. After leading many security transformation initiatives, I've identified five core barriers that transcend industry, company size and technical maturity:
1. Loss Aversion and the Sunk Cost Fallacy
Security teams feel the pain of giving up existing tools far more intensely than they appreciate gaining new capabilities — a cognitive bias known as loss aversion. It typically surfaces in statements like, 'We've invested years customizing Tool X. Yes, it only covers 30% of our needs, but we've perfected that 30%.’
I witnessed this firsthand at a major financial institution where a decade-old SIEM deployment had accumulated thousands of custom rules. Despite covering less than 40% of their modern cloud environment, the perceived value of these customizations created powerful resistance to change.
The challenge is often intensified by a familiar dilemma: “We've already invested in these tools, so we should keep using them.” Although future value should drive decisions, it’s hard to disregard the weight of past investments.
2. Identity and Expertise Attachment
Security professionals often build deep expertise in specific tools — technologies that become closely tied to their professional identity. As a result, discussions around consolidation can sometimes be perceived as a challenge to that hard-earned expertise.
I’ve seen seasoned security architects, whose careers were closely aligned with particular technologies, emerge as strong voices of caution. While their concerns often raised valid technical considerations, there also seemed to be a deeper, unspoken concern: How would their role and value evolve within a newly consolidated security environment?
3. Control and Autonomy Issues
Different security teams value their autonomy. DevSecOps teams want flexibility to integrate security into CI/CD pipelines. SOC teams need predictable, stable alert workflows. Cloud security teams require infrastructure-as-code integration capabilities.
Each team fears that consolidation will force them to compromise on their specific requirements, potentially breaking carefully constructed workflows. The fear manifests as: "A platform that works for everyone won't work well for anyone."
4. Status Quo Bias and Uncertainty Aversion
People have a remarkable ability to normalize their current situation, however inefficient. The known pain of managing 16 different security tools feels safer than the unknown challenges of consolidation.
This uncertainty aversion is particularly pronounced in cybersecurity, where professionals are trained to identify and mitigate risks and where failures can have catastrophic consequences. The thought process becomes: "Our current approach is inefficient but predictable. A new approach introduces unknown risks."
5. Distributed Decision Authority
Cloud-native applications distribute security responsibility across multiple teams. More often than not, this creates tension. While everyone would benefit from consolidation, no individual team has sufficient authority or incentive to drive the change.
Each team optimizes for their local requirements, resulting in overlapping tools and duplicated capabilities. When consolidation is proposed, resistance comes not from a single source but emerges as distributed opposition across organizational boundaries.
Common Signs of Security Fragmentation:
- Alert fatigue across multiple dashboards
- Increasing mean time to remediation
- Visibility gaps between tools
- Duplication of effort across teams
- Rising licensing costs with diminishing returns
- Inability to correlate events across tools
How many can you check off in your organization?
Breaking Through: Strategies for Overcoming Resistance
Having identified these barriers, how do we overcome them? Here are proven strategies I've employed across organizations ranging from startups to Fortune 500 enterprises:
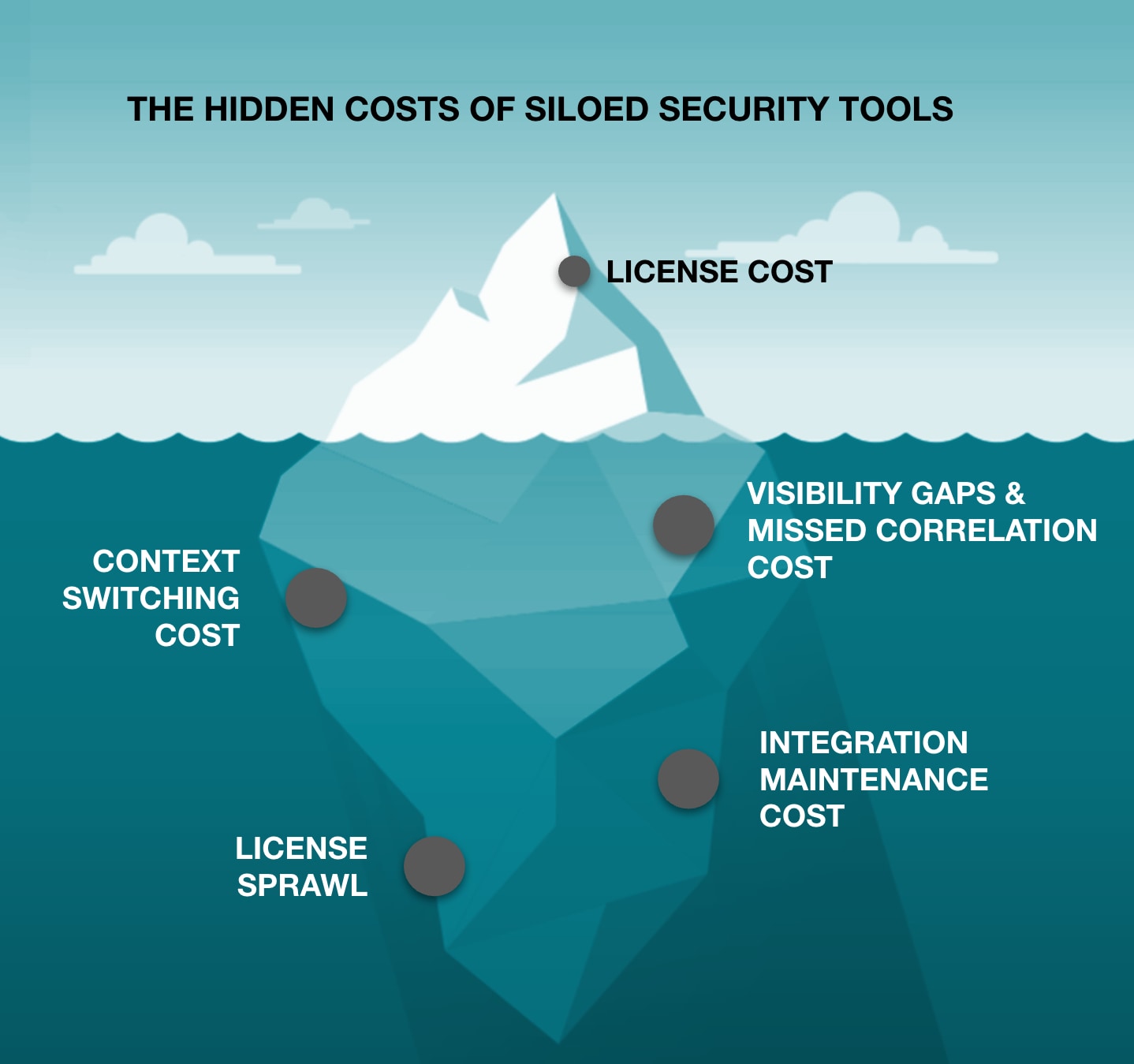
1. Quantify the Hidden Costs of Security Fragmentation
Make the invisible visible by documenting:
Time spent context-switching: Have analysts log time spent moving between tools over a two-week period. The results are often shocking.
Missed correlations: Conduct red-team exercises that deliberately exploit visibility gaps between tools, demonstrating real-world risk.
Integration maintenance: Calculate staff hours dedicated to maintaining custom integrations and API connections between disparate systems.
License sprawl: Create a comprehensive cost model including not just licensing but implementation, integration and maintenance costs.
As an example, this exercise may reveal that a $2M security stack might in reality cost ±$6M annually when accounting for hidden costs.
2. Support the Evolution of Expertise
Successful consolidation depends on leveraging the deep knowledge security teams have built over time. Rather than replacing that expertise, the goal is to extend it into new platforms.
- Recognize existing skills by publicly acknowledging the value of current tool-specific expertise.
- Define transition roles that make use of institutional knowledge during and after the migration.
- Establish clear growth paths that align evolving skill sets with the consolidated environment.
- Provide early access to training and certifications on the new platform to ensure readiness and confidence ahead of migration.
By aligning career development with platform changes, organizations can reduce disruption and retain key talent throughout the transformation.
3. Implement Progressive Consolidation with Demonstrable Wins
Rather than attempting a "big bang" migration, create a phased approach with clear victories at each stage:
- Begin with integration and visibility layers that don't replace existing tools but connect them.
- Identify the most painful workflows across teams and prioritize consolidating those first.
- Create immediate feedback loops showing time saved and risks remediated.
- Use technical proofs-of-concept for specific use cases before full commitment.
For cloud-native environments specifically, container security often provides an excellent consolidation starting point as it intersects with multiple domains (vulnerability management, compliance, runtime protection) but is recent enough that deep tool attachments haven't formed.
4. Develop and Communicate a Consolidated Technical Vision
Create a technical architecture showing how a consolidated platform will:
- Preserve necessary team autonomy through role-based access controls and custom workflows
- Enhance rather than restrict capabilities through comprehensive APIs and integration points
- Address team-specific requirements through configurable modules rather than one-size-fits-all approaches
- Provide migration paths that maintain existing capabilities while enabling new ones
Your vision must be developed collaboratively with input from all stakeholder teams, not imposed from above.
5. Align Organizational Incentives with Consolidation Goals
Address the distributed authority problem by:
- Creating cross-functional security steering committees with decision authority
- Developing shared KPIs that measure end-to-end security effectiveness, not just team-specific metrics
- Establishing executive sponsorship that can resolve cross-team conflicts
- Implementing budget models that reward consolidation rather than protecting siloed tool investments
The 4-Phase Path to Security Consolidation Success
Having led numerous consolidation initiatives, I've developed this framework for successful transformation:
Phase 1: Assessment and Vision
- Document current tool capabilities and gaps
- Map workflows across security teams
- Quantify current state inefficiencies and costs
- Develop consolidation vision and roadmap
- Identify key stakeholders and potential resistance points
Phase 2: Proof and Preparation
- Select 2-3 high-impact use cases for initial consolidation
- Implement technical proof-of-concept projects
- Develop training and transition plans for affected teams
- Create a detailed migration timeline with clear success metrics
- Establish governance model for consolidated platform
Phase 3: Progressive Implementation
- Begin with an integration layer connecting existing tools
- Implement first consolidated use cases
- Measure and communicate early wins
- Gradually expand scope based on success and feedback
- Maintain parallel systems during transition
Phase 4: Optimization and Evolution
- Fine-tune workflows based on user feedback
- Progressively decommission redundant tools
- Develop centers of excellence for consolidated platform
- Implement continuous improvement processes
- Regularly reassess security posture and platform effectiveness
Throughout this process, technical excellence must be balanced with awareness. Each phase should include explicit activities addressing all aspects of change, not just the technical requirements.
How Cortex Cloud Enables Successful Security Consolidation
Having outlined the barriers and strategic approaches to security consolidation, let's examine how a purpose-built platform like Cortex Cloud addresses these challenges directly.
Unified Visibility Without Sacrifice
Cortex Cloud was designed specifically to overcome the fragmentation challenges plaguing modern cloud-native security teams. Unlike point solutions that excel in narrow domains, Cortex Cloud provides a unified security data lake that ingests, normalizes and correlates telemetry signals from across your entire cloud-native stack:
- Container security: Deep inspection across image vulnerabilities, runtime behavior and Kubernetes configuration risks
- Cloud infrastructure: CSPM capabilities spanning multiple public cloud vendors such as AWS, Azure and GCP with contextual understanding of resource relationships
- Application security: Integration with CI/CD workflows for shifting security left while maintaining runtime protection
- Identity security: Cloud-native CIEM that identifies excessive permissions and privilege escalation paths
- API security: Automated discovery and protection of both internal and external APIs
- Data security: Automated sensitive data discovery and classification with continuous monitoring for exfiltration attempts and unauthorized access across cloud storage, databases and endpoints
- AI-SPM: AI Security Posture Management that secures your AI ecosystem by discovering all AI applications and models, identifying vulnerabilities in the AI supply chain, preventing model compromise and monitoring sensitive data used for training or inference
The unified approach directly addresses the visibility gaps that plague fragmented security architectures while preserving the depth that specialist tools provide.
Respecting Team Expertise and Autonomy
What separates Cortex Cloud from mere technical consolidation is how it can address the barriers we've discussed:
Overcoming loss aversion: Cortex Cloud offers a progressive adoption model. Instead of forcing teams to abandon existing workflows, they can begin by integrating their current tools and transition gradually as the benefits become clear.
Preserving expertise value: Cortex Cloud provides role-based interfaces that respect team specializations. DevOps engineers interact with security through familiar CI/CD integrations, while SOC analysts use detection and response workflows tailored to their requirements. The approach validates rather than threatens existing expertise. In addition, Cortex Cloud uses role-based access control (RBAC) to manage roles with specific permissions for controlling user access. RBAC helps manage access to Cortex Cloud components and Cortex Query Language (XQL) datasets, so that users, based on their roles, are granted minimal access required to accomplish their tasks.
Maintaining autonomy: The platform's architecture and customization capabilities ensure that teams maintain control over their specific processes.
Reducing Uncertainty, One Win at a Time
By applying a phased implementation methodology, Cortex Cloud can help address status quo bias by demonstrating concrete wins at each stage of adoption, creating a predictable path to value that reduces perceived risk.
The platform solves the distributed authority challenge through consolidated dashboards with role-based views, creating a single source of truth while still allowing teams to maintain their operational independence. Quite effectively, this resolves the governance challenge that fragmented tools create.
Operational and Measurable Gains
The power of Cortex Cloud in enabling consolidation becomes evident through the measurable benefits it can provide:
Quantifiable Efficiency Gains
Organizations implementing a unified platform like Cortex Cloud can expect:
- Significant reduction in the overall security toolset
- Decreased alert volume through contextual deduplication
- Improved remediation time for critical vulnerabilities
- Streamlined compliance processes without sacrificing security effectiveness

Operational Improvements
From an operational perspective, the consolidation enabled by Cortex Cloud delivers:
- Unified vulnerability management, compliance and runtime protection workflows
- Customized dashboards for different stakeholders drawing from the same underlying data
- Automation of security findings through direct integration with CI/CD pipelines
- Accelerated security review cycles
Designed for Human Transformation
The technical foundation that makes Cortex Cloud particularly effective for overcoming consolidation resistance is its architecture specifically designed to address the human challenges:
Modular adoption: Teams can begin with the components most relevant to their immediate needs, expanding adoption as value is demonstrated.
Multilevel integrations: From APIs, CLI tools to CI/CD integrations, Cortex Cloud meets teams where they’re rather than forcing workflow changes.
Collaborative workflows: Built-in capabilities for cross-team collaboration on security findings, with clear ownership and accountability tracking.
Knowledge preservation: Teams can easily migrate existing security rules and custom detections, preserving the intellectual property they built over the years.
Outcome-based metrics: Dashboards that focus on security outcomes (reduced attack surface, faster remediation) rather than tool-specific metrics, aligning incentives across teams.
By addressing the barriers mentioned above, Cortex Cloud provides not just a security platform but a transformation enabler — one that acknowledges the human elements of security consolidation are as important as the technical ones.
Learn More
Security consolidation in cloud-native environments isn’t merely a technical challenge but a deeply human one. By understanding and addressing the barriers to change, security leaders can transform resistance into partnership and fragmentation into cohesion.
By approaching transformation as both a technical initiative and a team-driven effort, leaders can build stronger defenses, as well as more aligned, resilient security teams ready to meet the demands of our cloud-native future.
If you’d like to see Cortex Cloud in action, allow us to give you a personalized demo.