The pandemic changed the nature of work. An all-digital and remote work is becoming the new standard. We have seen years-long digital change has been compressed into weeks to adjust to the new normal as a result of COVID-19. It is clear that the future of work will be a mixture of virtual and in-person experiences.
The meeting solutions combine communications, co-operation, and content sharing to facilitate virtual meetings. The video conferencing gained a huge grip since the coronavirus outbreak occurred. The enterprises and government needed to act quickly to keep operations running. Therefore, video conferencing was the solution to connect employees and customers. Except taking the workforce operating remotely is not the same job as ensuring the assets needs to access have been properly secured. As a result, the necessity for excellent visibility and security accompanying granular application control is more important than ever before.
This type of application is employed in IoT devices across telemedicine and healthcare. For instance, Vuzix uses Zoom and Webex Connector Applications for Smart Glasses that are used for live-streaming surgery, in emergency rooms and ICUs to treat patients.
In November 2020, Palo Alto Networks was positioned in the Leaders quadrant of the Network Firewalls, as reported by Gartner. One of the strengths of our firewalls listed, was strong granular application controls that Gartner clients often highlighted as one of the primary reasons for shortlisting Palo Alto Networks firewalls.
In this article, we aim to leverage the robust security abilities of Palo Alto Networks App-ID to provide immeasurable visibility in the network security of organizations. We will illustrate how to take advantage of network traffic clarity for stopping attacks, data exfiltration, and remote control enforcement.
Network Traffic Visibility
Palo Alto Networks App-ID technology creates a foundation to reduce the attack surface. App-ID uses an application hierarchy that includes the base application and all its supporting functions. It allows administrators to safely enable applications through policies that allow or deny applications contextually for specific users or groups to keep the attack surface as small as possible.
App-ID enables visibility in video conferencing apps in your network. The App-ID concentrated on application identification and in-app features (e.g., meeting, messaging, desktop sharing, and remote access), along with file transfer capabilities such as download and upload. Administrators can block or control what they deem to be risky functions such as file transfer.
App-ID that already running on Palo Alto Networks Next-Generation Firewall (NGFW) is capable of providing users with extensive visibility on the following video conferencing applications:
- Zoom, Blue Jeans, GoToMeeting, Skype, Microsoft Teams, Amazon Chime, Google Meet, Slack, FreeConferenceCall, Webex, Zoho Meeting, UberConference, Fuze Meeting, Join.me, GoToWebinar, Adobe Connect, Avaya web.alive, BigBlueButton, Starleaf, Whereby, Free Conference, Tencent Meeting, GlobalMeet, VooV Meeting, My Own Conference, MegaMeeting, ReadyTalk, and Highfive.
Stopping Possible Attacks Scenarios
In this section, we'll introduce and discuss three scenarios for stopping possible attacks.
Cyber-attack chain using file transfer in video conference applications
In a cyber-attack chain, delivery is a phase where the attacker sends a malicious payload to the victim. For example, they could place a remote access Trojan inside a file that looks to have important information, share it in a meeting and attract users into downloading and running it. For instance, in Zoombombing incidents, a teleconferencing session is hijacked, and hackers joining a meeting without authorization can upload and distribute malicious contents into a video-conference call rooms/meeting. It is conceivable to infect participants' endpoints or mobile devices that are unwittingly downloading malicious files.
To minimize the chance of this threat, using App-ID features network security administrators might place a policy to granularity block file upload/download functions for users or groups. Nevertheless, it is suggested to block files known to carry threats or to have no real use case for upload/download. For policy rules that allow video conferencing applications, you can be strict with your file blocking because of the risk that users unknowingly download malicious files.
For this type of traffic, you may want to attach a more strict file blocking profile that also blocks portable executable (PE) files. You can define your custom File Blocking profiles, or choose one of the predefined profiles that are available with content release version 653 and later when applying file blocking to a Security policy rule.
Figure 1 illustrates a sample of how to block Microsoft Team file transfer. We can simply go to Palo Alto Networks Firewall, “POLICIES” tab and create a Drop rule for Microsoft Team uploading and downloading for the function of upload/download.
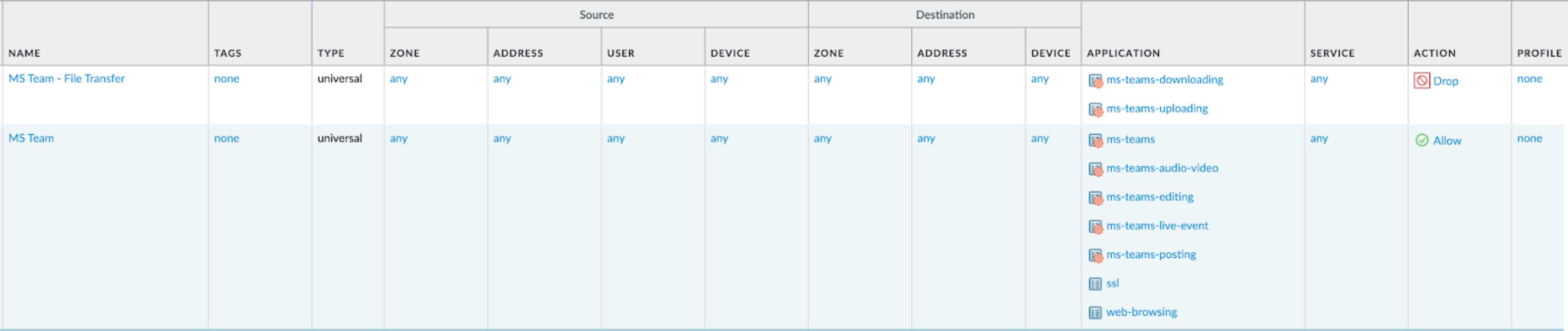
Figure 1. A sample of how to block Microsoft Team file transfer.
Data Exfiltration
Keeping sensitive information inaccessible to unauthorized individuals is an essential function of network security. Data exfiltration happens when an authorized party extracts data from the secured systems where it belongs or moves it to insecure systems. It can happen due to the actions of malicious or compromised parties, or even accidentally. To minimize the risk of these types of threats, organizations must integrate security awareness and regularly assess the risks of every interaction with computer networks, devices, and applications.
Uploading sensitive data to a third-party through unmonitored software (application) is dangerous and costly. In addition, the network traffic for the application could be innocuous-seeming like a meeting solution application. This type of data exfiltration typically arises from malicious insiders. By utilizing App-ID, the risk of this kind of incident can decrease. By using policy restrictions on upload files in video conferencing applications, it protects organizations against transferring sensitive data to vulnerable and unapproved systems.
Figure 2 illustrates a sample of how to block Cisco Webex upload file transfer in the meeting. Administrators can go to Palo Alto Networks Firewall, “POLICIES” tab and create a rule with the action of Drop for Cisco Webex uploading function.
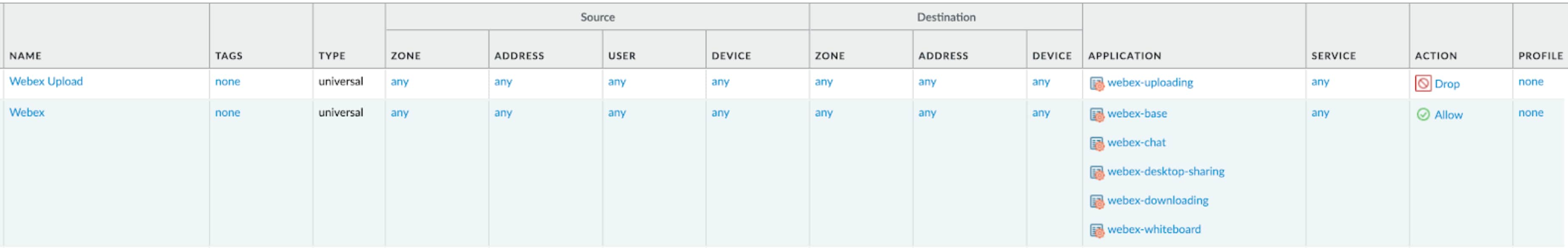
Figure 2. A sample of how to block Cisco Webex file uploading.
Nevertheless, policy restrictions do not eliminate all the risks of this nature, such as screenshots or copied text being uploaded or posted on the Internet. However, Palo Alto Networks App-ID covers over 3,000 applications that contain categories among the high-risk applications that could be a target for data exfiltration. The full list of applications and protocols covered by App-ID can be found here. Researchers at Palo Alto networks are constantly working to increase the coverage of applications and protocols.
Remote Control Compliance
Remote access to an organization could provide an attacker the ability to manipulate and subvert the organization systems from outside the physical security perimeter. Unauthorized remote connections via video conferencing applications should be restricted by establishing and enforcing policies. By allowing remote control functionality in meeting solution applications, it exposes users to possible remote access attacks, which employees are not usually aware of. It may put the organization at a severe security disadvantage by allowing attackers the opportunity to remotely gain access to a system. Once the attackers are inside the system, they may upload malicious code, exfiltrate sensitive data, and use the compromised machine to target and attack other workstations or networks within the same environment.
The best way to prevent remote access attacks is to stop remote access ability for the application that possesses a remote access option, but not needed to be active in the network. The majority of the meeting solution applications come with remote access capability. By using App-ID you can inspect remote connections that are part of the video conference sessions, and set and enforce policies to prevent remote access options and mitigate these types of threats.
In Figure 3, an example of how we can limit remote access for users is provided. As shown in the example, we can limit the users from using Adobe Connect Remote access capability that allows screen-sharing and collaborative remote control. Go to your firewall in the “POLICIES” tab, create a policy that restricts the “adobe-meeting-remote-control”. If you want to allow the other Adobe Connect features to be used by users, you can create a second rule.
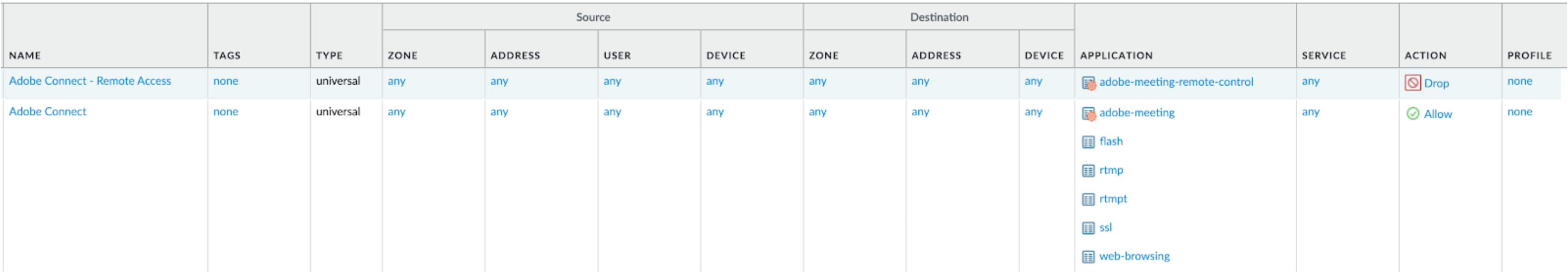
Figure 3. Limiting the users from using Adobe Connect remote access capability.
Conclusion
The growing dependence on video conferences in today's digital world demands security teams to recognize potential threats and adjust their organization security policies, respectively. Palo Alto Networks NGFW is equipped with App-ID control that has extensive detection capabilities. It is used to provide exceptional network security visibility to its customers to secure organizations from attackers and protect employees and their data.