The risk of unmanaged devices connecting to an enterprise network remains one of the top challenges for IT and security teams. “Small organizations have deployed anywhere from 15-20 security tools. Medium-sized organizations deploy from 50-60. Large enterprise organizations like banks have deployed well over 150 tools.”[1]. Organizations rely on these systems to achieve comprehensive risk management across networks, apps, users, content and devices. But the risk management framework is not complete without factoring in IoT visibility.
Given that 30% of the devices on an enterprise network are unmanaged IoT devices, the potential of most of these cybersecurity solutions is not not fully realized as they are operating on partial information from the managed devices and endpoints. These gaps in visibility of IoT devices on the network are typically remediated through tactics that include manual steps and human interventions, which introduce risk, drain efficiency, and compromise the effectiveness of existing IT and security workflows. Here are some examples of common challenges security teams are experiencing as a result:
- Hidden vulnerabilities. Without IoT device visibility and context vulnerability management scans are incomplete, leading to compliance gaps and increased risk of undetected anomalies.
- Sub-optimal network segmentation. Network segmentation strategies, utilizing network access control (NAC) solutions, are less effective at preventing the lateral movement of threats posed by IoT devices when unmanaged devices are not automatically and accurately identified.
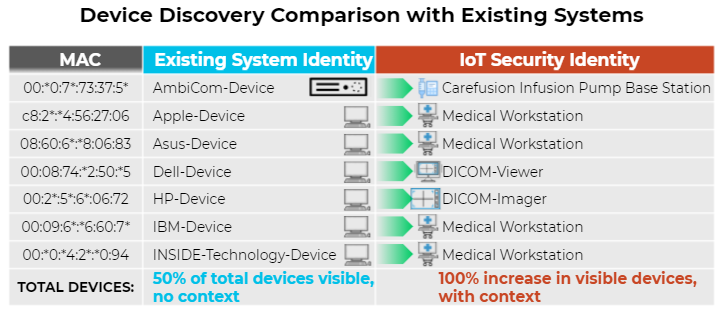
- Burdensome inventory updates. Enterprise asset management solutions’ asset inventory is less accurate and less efficient when all IoT devices aren’t visible in real time, resulting in costly and time-consuming manual database updates and increased risk of audit noncompliance.
Our built-in integrations take your IT and security workflows to the next level.
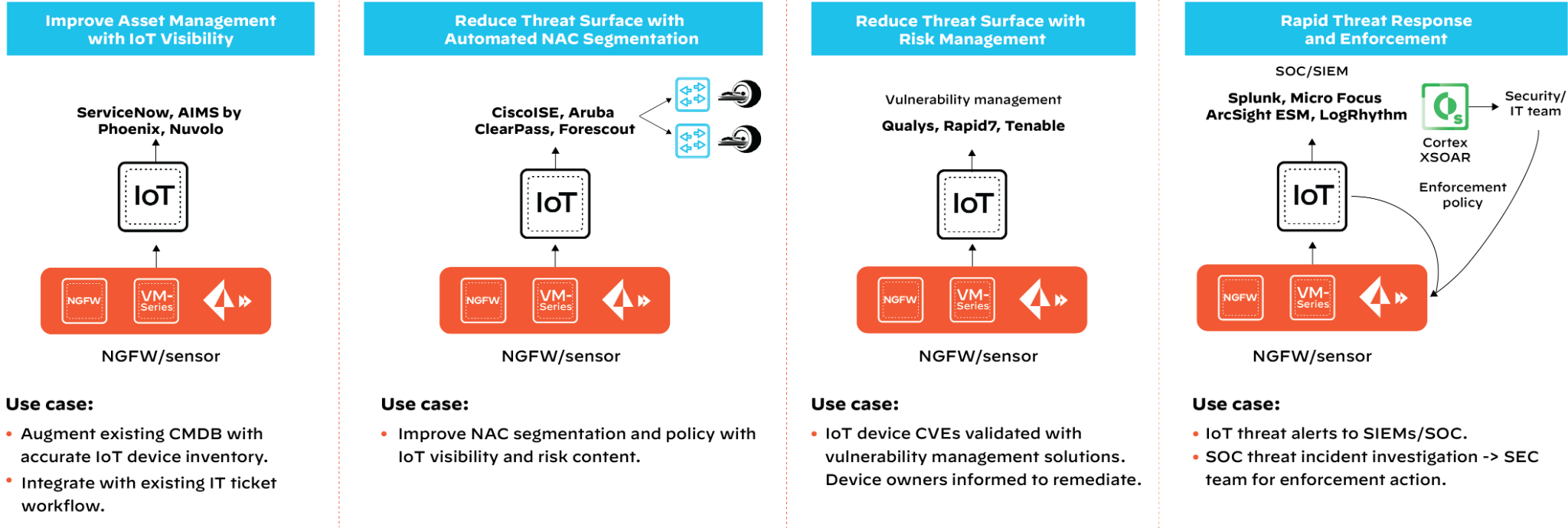
Palo Alto Networks IoT Security has introduced 15+ new integrations with market leading IT and security solutions to make existing workflows more effective and automated to secure unmanaged IT and IoT devices.
- Vulnerability management. With IoT Security, security teams will be able to detect behavioral anomalies unique to IoT devices, and enhance existing vulnerability management solutions by identifying scan coverage gaps, confirm vulnerabilities on discovered IoT devices with rich contextual information, and proactively take remediation actions with automated workflows.
Available built-in integrations: Qualys, Rapid7, Tenable
- Network Access Control (NAC). Built-in integrations with NAC solutions allow IT and security teams to quickly fill their segmentation policies’ IoT device visibility gaps. Furthermore, network and security teams can also leverage the rich device communication pattern, segmentation, and risk context from our IoT Security to define prescriptive micro-segmentation policy, such as downloadable ACL(dACL), Security Group Tags (SGT), or a quarantine policy for risky devices. These prescriptive policies can be shared from the IoT Security dashboard to the existing NAC solutions to enforce via the network infrastructure.
Available built-in integrations: Forescout, Cisco ISE (with PxGrid), Aruba ClearPass
- Detection and Response. Incident and threat detection and response solutions often rely on agent-based approaches and lack context for unmanaged IoT devices, which makes it challenging to triage alerts when they do not have visibility into which device creates them. IoT Security identifies and prevents threats specific to IoT Devices and allows security analysts to investigate with context and automate enforcement, this reduces risks and enhances threat incident response solutions, such as Security Information Event Management (SIEM) with details (such as device make and model, network location, risk context, etc.) to quickly take actions.
Available built-in integrations: Splunk, Micro Focus ArcSight ESM, LogRhythm
- IT network management. Network infrastructure technology integration has proven very useful for IT, security, and device management teams to pinpoint device location and get granular information on the IoT devices. This further helps the IT and security teams to:
- Quickly locate and remediate IoT device misconfiguration and anomalies.
- Plan for zero trust segmentation by visualizing network segmentation topology mapped to the devices and policies.
- Discover and get the network location of the non-IP Bluetooth and BLE devices connected to the network.
Available built-in integrations: Cisco DNA Center, Cisco Prime Infrastructure, Cisco Wireless LAN Controller (WLC), Aruba WLC, SNMP Servers
- IT Asset Management. The native integrations with the configuration management database (CMDB) and computerized maintenance management system (CMMS) solutions make static asset inventory dynamic with automatically updated IoT device visibility and context such as device make, model, operating system, network location, applications, and more. Palo Alto Networks IoT Security creates an IT ticketing workflow for the security team to investigate and remediate risky or compromised unmanaged devices. Healthcare organizations can track medical device utilization and automatic work orders to better manage over or under utilization of medical equipment and devices.
Available built-in integrations: ServiceNow, AIMS by Phoenix Data Systems, Nuvolo
Top IoT Security Use Cases
Request a product demo today to learn more on how our most comprehensive IoT Security protects every single unmanaged device in your network while making single-purpose sensors a thing of the past.
========================END==============================
- /blog/2018/03/cso-security-platform-monopoly/ ↑