Passwords, encryption keys, API tokens — protecting any confidential data that grants access to systems, applications, or data is paramount. All too commonly, though, access credentials are embedded in code or stored in plaintext files, leaving organizations vulnerable to security breaches. Given the extent of secrets sprawl and the mercurial landscape of cyberthreats, the need for comprehensive secrets detection is greater than ever.
While scanning for secrets hidden within IaC or code repos is a good start, secrets can still make their way into deployed workloads, potentially exposing the organization to unauthorized access and compromise of data confidentiality. Effective secrets scanning requires a holistic approach from code to cloud.
The Prisma Cloud team is happy to announce our release of agentless secrets scanning, a new layer of protection designed to ensure your cloud workloads remain free from unintentional secrets exposure.
The Need for Agentless
Agent-based solutions rely on partially effective methods for secrets detection. While they could uncover some secrets, these solutions are often too limited in scope and fail to provide complete coverage.
The primary issues with these traditional methods lie in their inability to efficiently scan for secrets across the entire filesystem due to the scan being resource intensive in nature, and the inability to scan non-running workloads. These two shortfalls leave organizations vulnerable to potential security breaches.
Not All Agentless Solutions Are Equal
Because a secrets scanning solution is agentless doesn’t mean it’s effective. Some agentless solutions rely on predefined directories or paths within the file system where secrets are traditionally expected to be stored. But this approach presents several issues:
- Organizations may remain unaware of secrets until a specific path is recognized as one that should be scanned.
- Exploits using a particular secrets path may exist in the wild before that path is included in the product.
- If an application changes its default path for storing secrets, it can take time to detect and incorporate this change into the security product.
- Users have the flexibility to use non-default paths for storing secrets.
A New Approach to Secrets Detection
Users can now find secrets in production environments without having to deploy agents. In fact, this powerful feature is available out of the box with Prisma Cloud.
With agentless scanning by Prisma Cloud, organizations can confidently search for secrets hidden in plain sight within running and non-running workloads across all major cloud service providers such as AWS, GCP, Azure and OCI.
Agentless secrets scanning doesn’t require additional configuration and is integrated seamlessly with the existing agentless scanning capabilities available within Prisma Cloud.
The Agentless Advantage
The key differentiator that sets agentless secrets scanning apart is its ability to operate in an offline manner — it doesn’t impact the performance of running instances. Unlike CPU and memory-intensive methods of scanning using agents and risking degradation of the production environment, this technology operates seamlessly without the need for resource-hungry agents. This means that organizations can conduct thorough secrets scans without compromising system performance or consuming excessive computing resources.
Unparalleled Coverage
Prisma Cloud agentless secrets scanning offers extensive coverage and adaptability. In contrast to many other cybersecurity products, Prisma Cloud's agentless secrets scanning doesn’t rely on predefined paths or directories within the filesystem where secrets are conventionally expected to be located.
Conducting searches for secrets throughout the entire filesystem, regardless of their potential hiding places helps increase coverage. This broader scope increases the effectiveness of detecting sensitive information and uncovering concealed vulnerabilities or latent security risks lurking within the system.
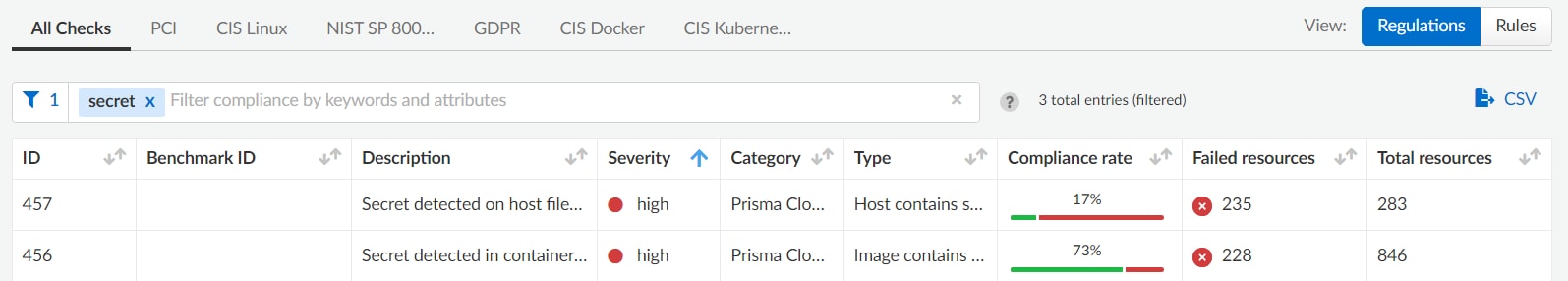
Additionally, the scanning capability supports detection of an unparalleled range of secret types, including application keys, private keys, passwords, API tokens, configuration files, cloud keys and credentials for all CSPs — AWS Secret and Access Keys, Azure Service Principals, and GCP Service Account Auth Keys, to name a few.
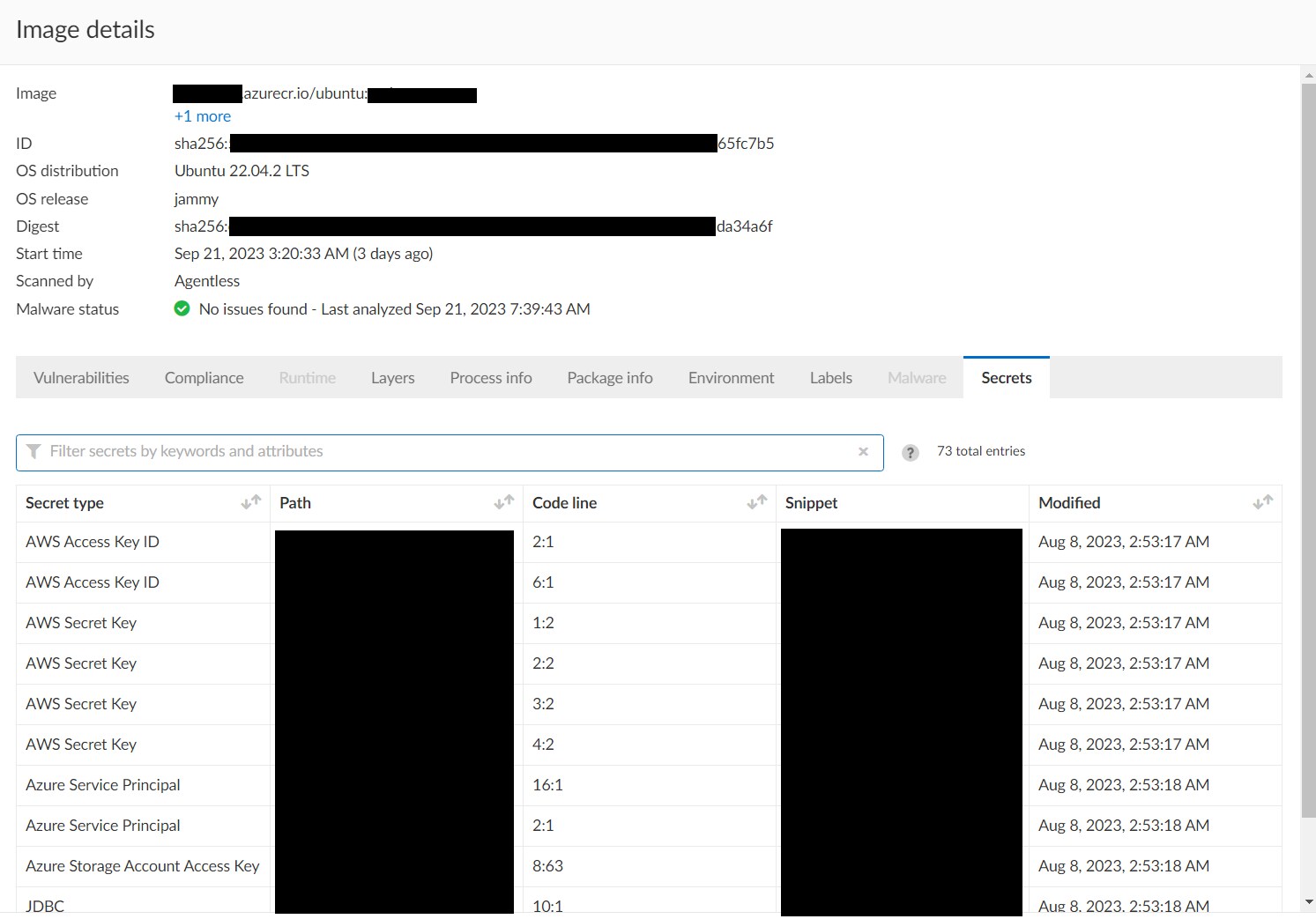
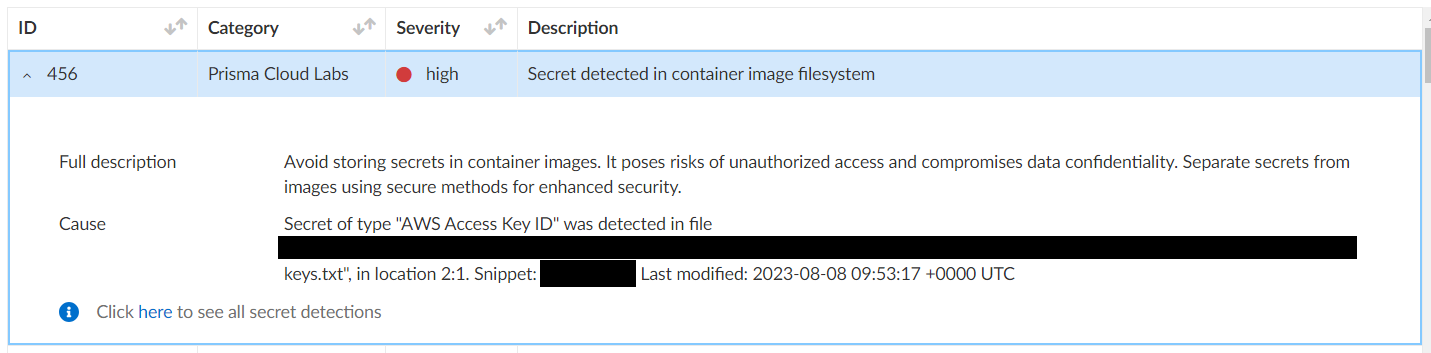
By offering comprehensive coverage and cross-cloud compatibility, agentless secrets scanning represents a robust and adaptable approach to cybersecurity that addresses the evolving needs of modern organizations.
Code-to-Cloud Secrets Scanning
In the era of DevSecOps, with security integrated into the development process, agentless secrets scanning aligns perfectly with essential practices. Prisma Cloud offers a code-to-cloud approach, enabling teams to detect secrets throughout the development lifecycle — and resolve secrets vulnerabilities before they’re exploited.
Prisma Cloud’s agentless secrets scanning represents a significant leap forward in secrets detection technology. And it’s available for both SaaS and Compute Editions, making sure that organizations of all sizes can take advantage of this cutting-edge security feature.
Learn More and Equip Your Team with Actionable Insights
Learn how to effectively eliminate exposed credentials, safeguard your cloud-native stack, and implement a comprehensive secrets management strategy with 6 Secret Security Tips for Cloud-Native Stacks.