Infrastructure as Code (IaC) templates, such as Terraform and CloudFormation, provide a way to provision and modify infrastructure using code. This improves the speed, change failure rate and collaboration around provisioning infrastructure, but it doesn’t solve the security problem. When 63% of open source IaC templates are insecure, infrastructure provisioned by IaC can be just as insecure as brownfield deployments.
The goal of shift-left security is to empower developers to address these security issues in code before they get deployed in applications and infrastructure. Tools like Prisma Cloud bring visibility into the posture of IaC templates prior to deployment, reducing the time to remediation. Additionally, for many misconfigurations identified, we provide fix suggestions that developers can easily implement as automated pull requests and commits to secure their code. However, not all misconfigurations have a single fix available. For example, load balancers should have TLS enabled, but there are multiple encryption libraries available.
For these misconfigurations, determining which solution meets internal compliance requirements can take time and slow down the time to remediation. However, if an expert has resolved an issue enough times, it becomes muscle memory to fix or even avoid that issue in the future. The problem is that this institutional knowledge can be siloed with the individual who has built up that expertise.
That’s why we’re excited to announce Smart Fixes available as part of Prisma Cloud Infrastructure as Code Security and Bridgecrew. By providing fix suggestions based on teams’ past secure coding behavior, this feature democratizes institutional knowledge for fixing cloud misconfigurations within IaC templates. The result is a faster time to remediation and a higher remediation rate before deployment, leading to reduced risk and faster time to market.
How Smart Fixes Work
Smart Fixes work automatically once a version control system (VCS) is onboarded to the Prisma Cloud platform. Prisma Cloud will track the code in repositories that pass a policy check, whether that’s previously committed code that passed the policy from the beginning or a previous fix to the code that failed a policy check. If the same code is used for passing a policy check multiple times, that code will be surfaced in the future as a Smart Fix against the policy. For the earlier example, if the same encryption library is used multiple times, then the next time someone forgets to add encryption to their IaC resource block that creates a load balancer, Prisma Cloud can suggest that library.
Additionally, there may be multiple correct fixes for failing policies. For some applications, one standard may be appropriate, and for others, it may be another. Smart Fixes will track the frequency and rate at which code passes policies and suggest multiple ranked options, reducing the fallacy of choice that comes with too many options.
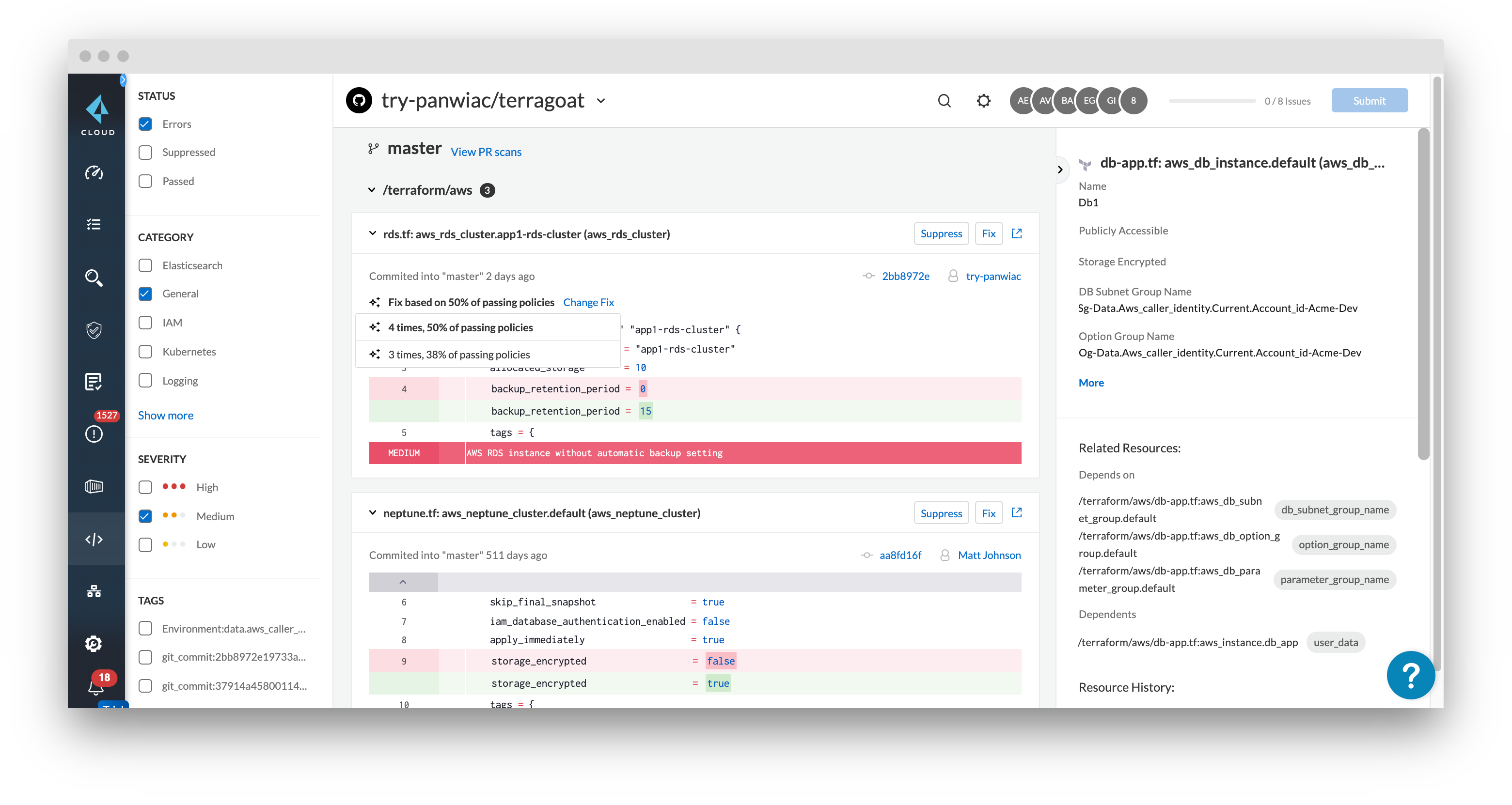
Once a Smart Fix is applied, Prisma Cloud will open a pull request with the code changes back to the repository. That IaC template will then be deployed into runtime infrastructure with the security fix already applied, creating secure infrastructure from the start.
Approaching Full Fix Suggestion Coverage
When development teams are moving at a rapid rate, any friction caused by security guardrails reduces the likelihood that developers will secure their code. Instead of digging through forums or past code, developers using Prisma Cloud now have quick fixes for nearly all policies right at their fingertips. This makes securing code and cloud infrastructure just a few clicks away.
Smart Fixes are now available on the Code page, and we’ll be adding them to our other integrations.
Try it out by requesting a free trial or register for one of the IaC security demo sessions.